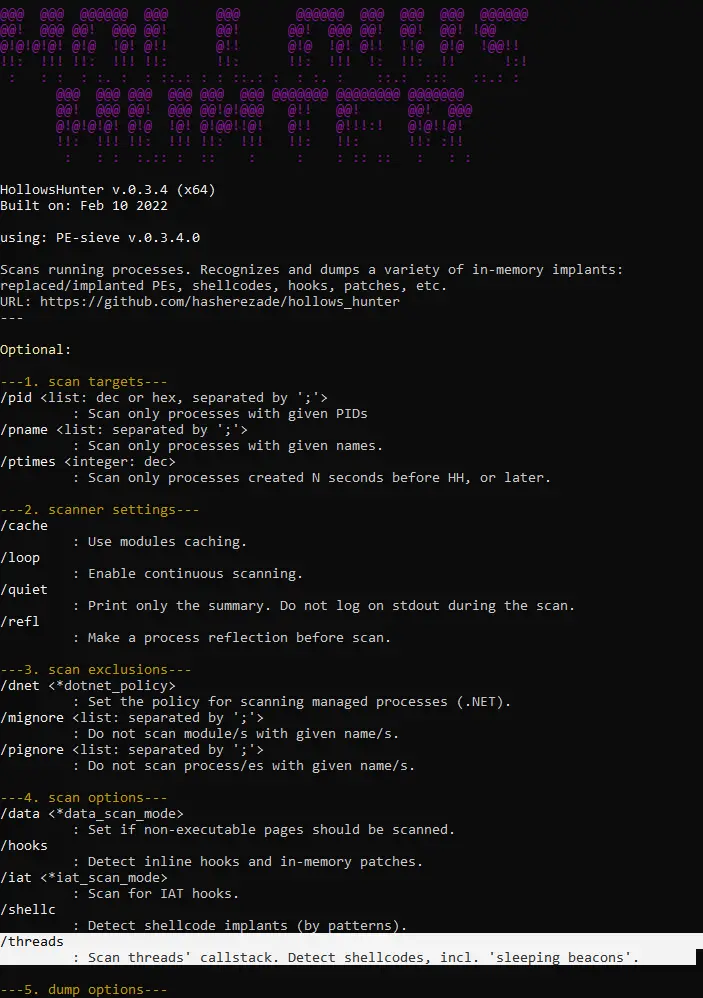
hollows_hunter Scans all running processes. Recognizes and dumps a variety of potentially malicious implants (replaced/implanted PEs, shellcodes,...
Malware Analysis
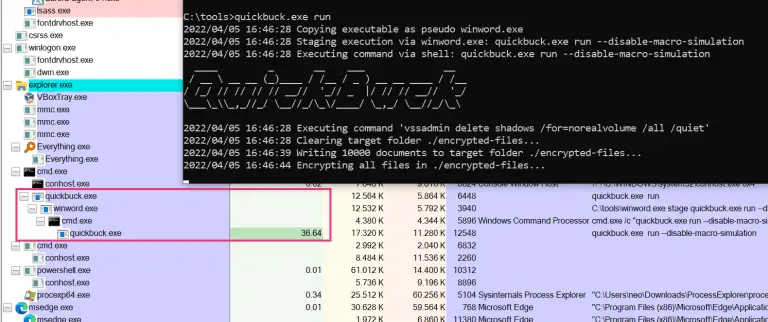
Ransomware Simulator The goal of this repository is to provide a simple, harmless way to check your...
DroidDetective DroidDetective is a Python tool for analysing Android applications (APKs) for potential malware-related behaviour and configurations....
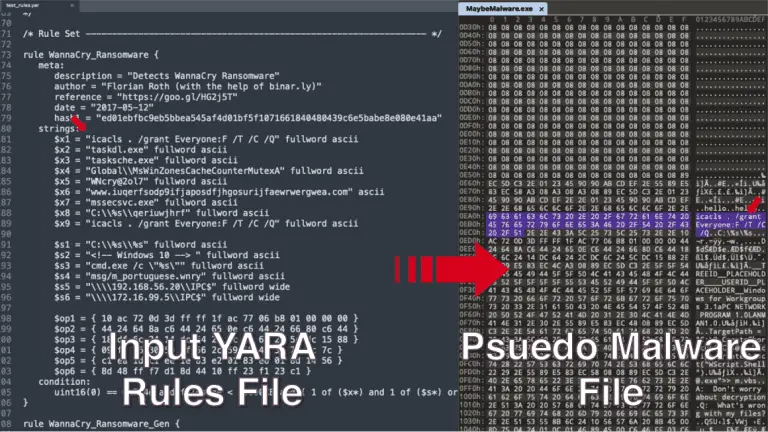
Arya – The Reverse YARA Arya is a unique tool that produces pseudo-malicious files meant to trigger...
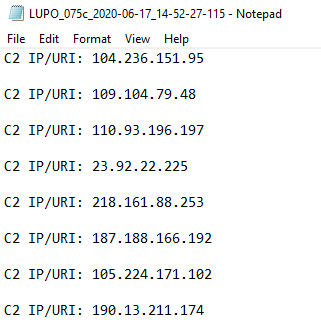
Lupo — Malware IOC Extractor Debugging module for Malware Analysis Automation Introduction Working on security incidents that...
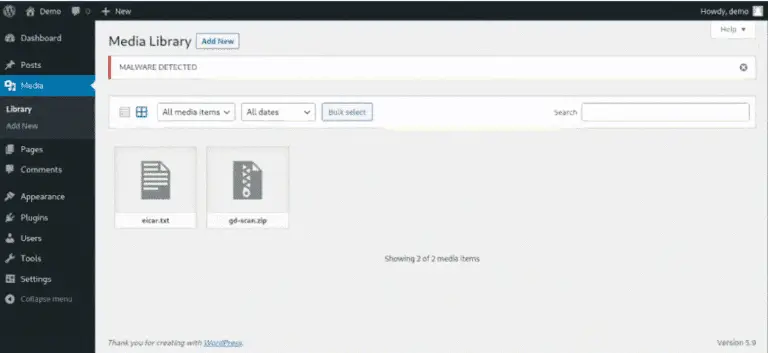
Verdict-as-a-Service Verdict-as-a-Service (VaaS) is a service that provides a platform for scanning files for malware and other threats....
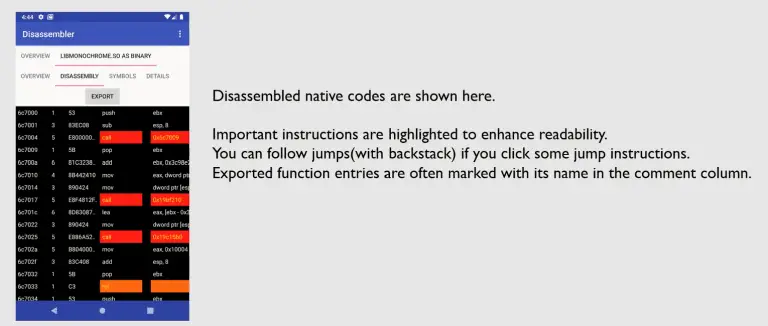
Android Disassembler Analyze malicious app on your phone Android Disassembler is an application that is able to...
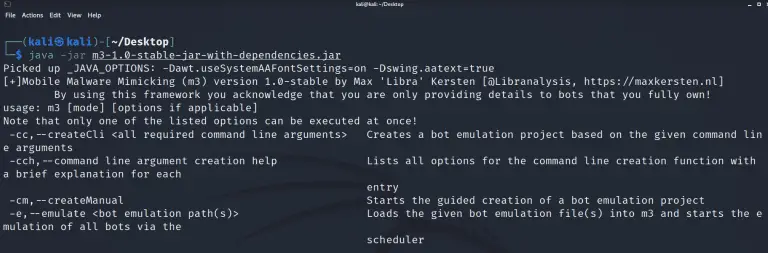
Mobile Malware Mimicking Framework The Mobile Malware Mimicking framework, or m3 in short, is built to easily and scalable...
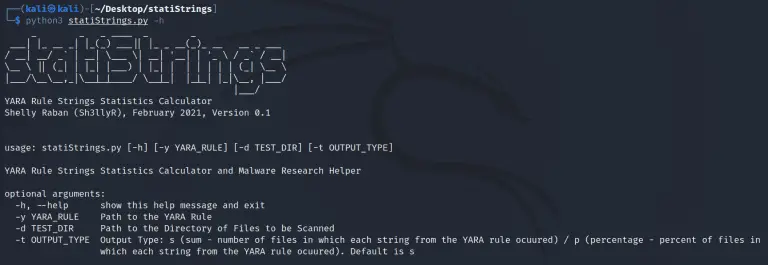
statiStrings statiStrings is a strings statistics calculator for YARA rules. The goal is to aid malware research...
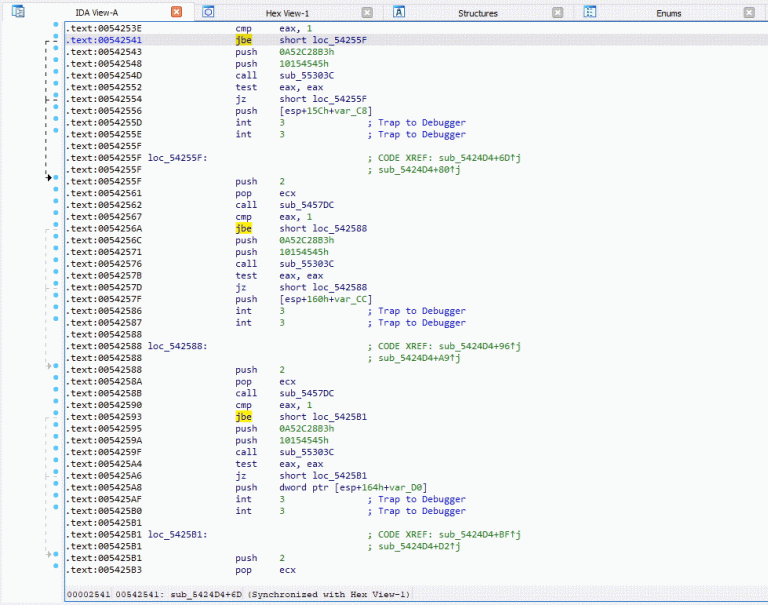
AlphaGolang AlphaGolang is a collection of IDAPython scripts to help malware reverse engineers master Go binaries. The...
PMAT-labs – The labs for Practical Malware Analysis & Triage This repository contains live malware samples for...
HashDB IDA Plugin Malware string hash lookup plugin for IDA Pro. This plugin connects to the OALABS HashDB...
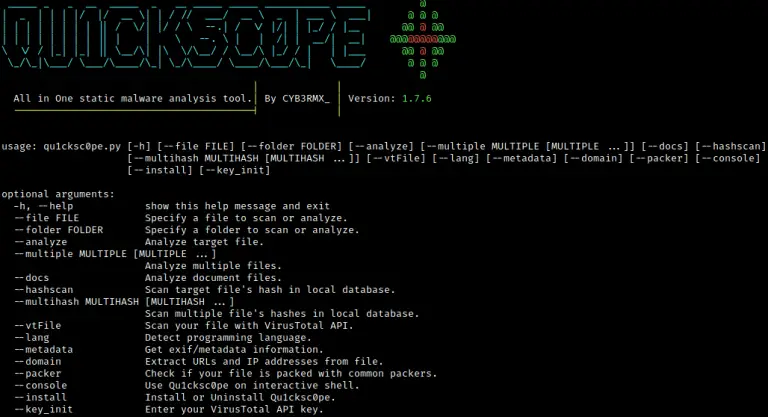
Qu1cksc0pe This tool allows statically analysis Windows, Linux, osx, executables, and also APK files. You can get:...
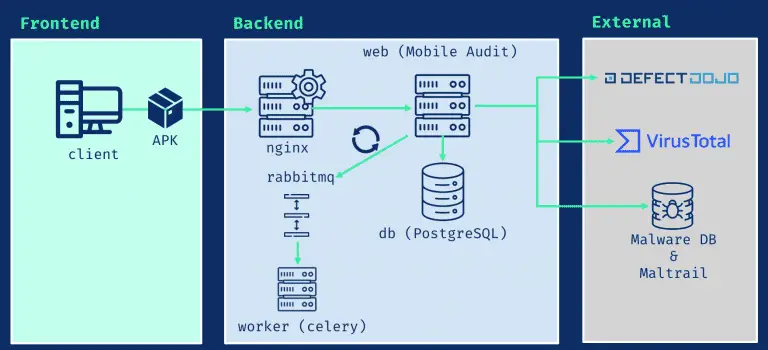
Mobile Audit MobileAudit – SAST and Malware Analysis for Android Mobile APKs Django Web application for performing Static...
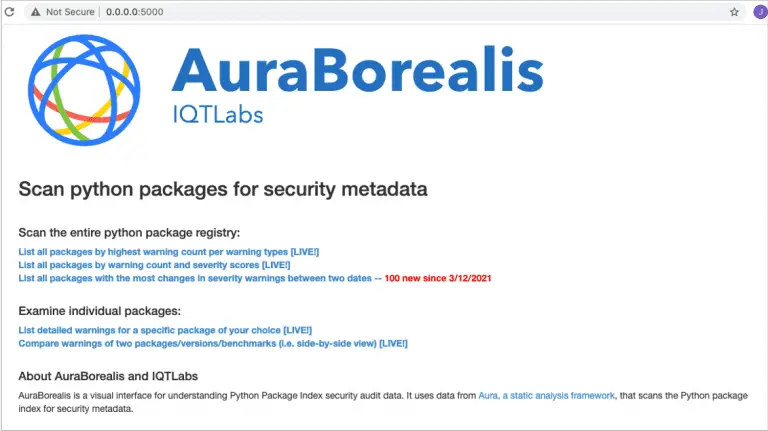
AuraBorealis: Do You Know What’s In Your Python Packages? AuraBorealis is a web application for visualizing anomalous...