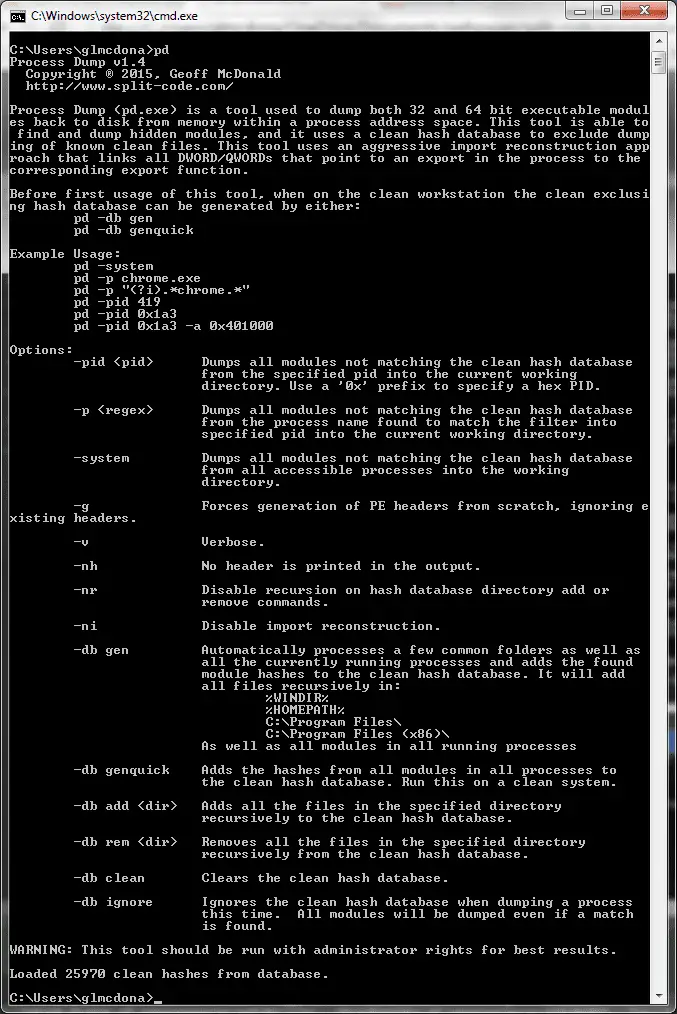
Process Dump Process Dump is a Windows reverse-engineering command-line tool to dump malware memory components back to...
Malware Analysis
TwiTi TwiTi, a tool for extracting IOCs from tweets, can collect a large number of fresh, accurate...
Passive Security Tools Fingerprinting Framework Have you ever wanted a simple, easy, and stealth bypass for multiple...
medusa Medusa is an extensible framework for Android applications which automates processes and techniques practised during the dynamic analysis of a malware...
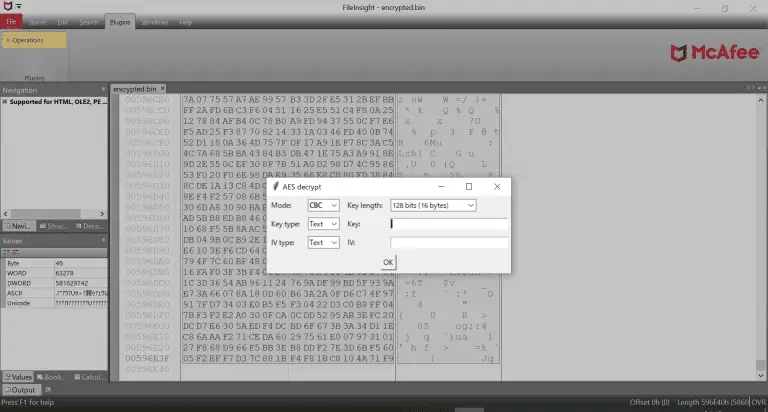
FileInsight-plugins: decoding toolbox of McAfee FileInsight hex editor for malware analysis FileInsight-plugins is a large set of...
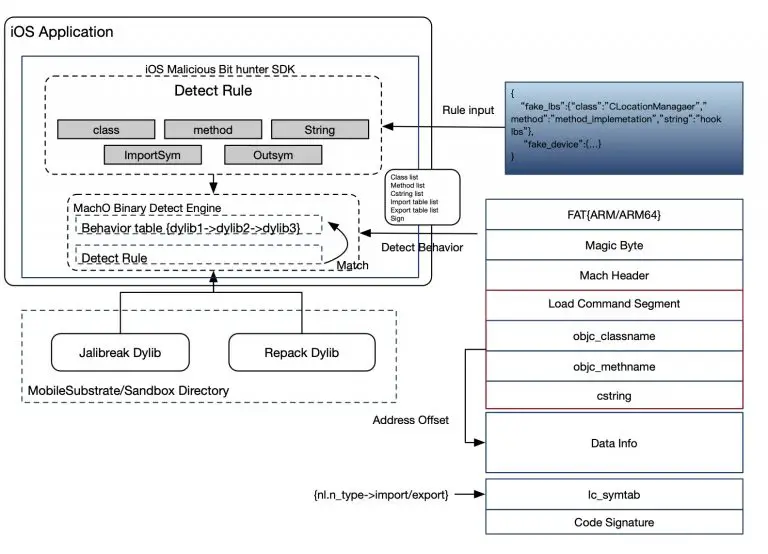
iOS Malicious Bit Hunter iOS Malicious Bit Hunter is a malicious plug-in detection engine for iOS applications....
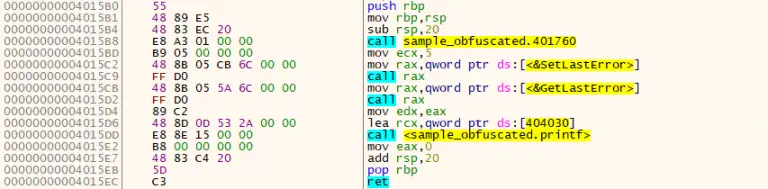
CallObfuscator Obfuscate (hide) the PE imports from static/dynamic analysis tools. Theory This’s pretty forward, let’s say I’ve...
Strafer Elasticsearch infections are rising exponentially. The adversaries are exploiting open and exposed Elasticsearch interfaces to trigger...
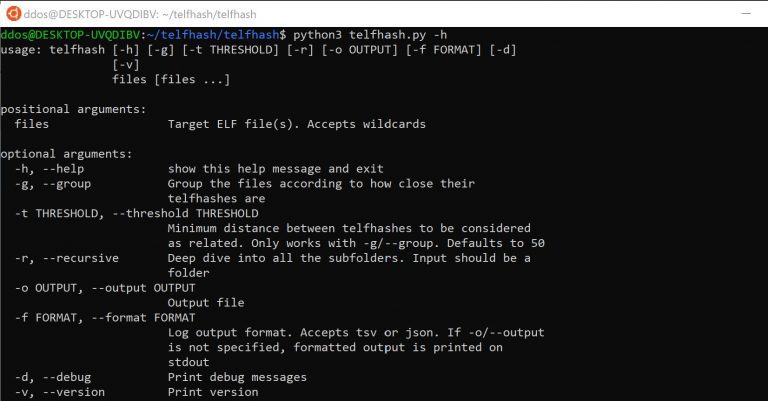
Trend Micro ELF Hash (telfhash) telfhash is a symbol hash for ELF files, just like imphash is...
Uchihash Uchihash is a small utility that can save malware analysts the time of dealing with embedded...
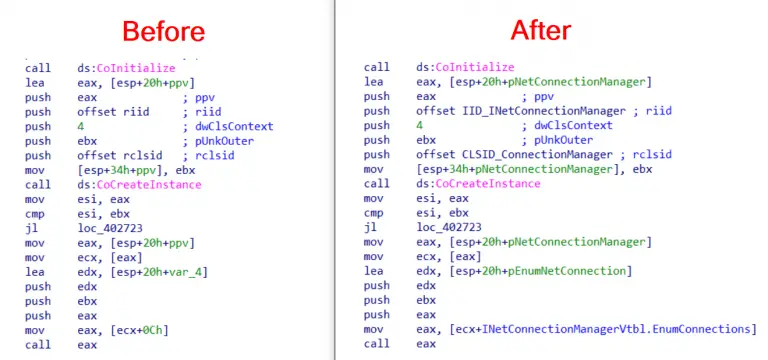
COM-Code-Helper Two IDAPython Scripts help you to reconstruct Microsoft COM (Component Object Model) Code Especially malware reversers...
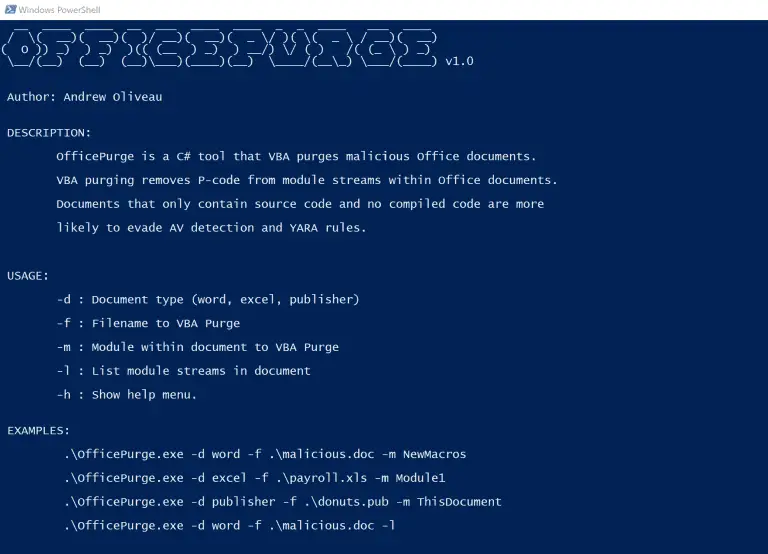
OfficePurge VBA purge your Office documents with OfficePurge. VBA purging removes P-code from module streams within Office...
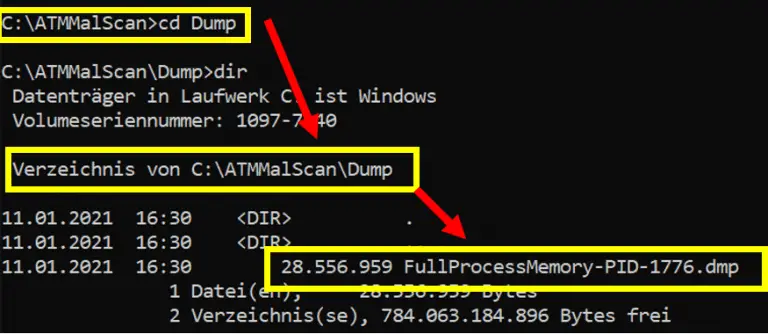
ATMMalScan ATMMalScan is a commandline tool for Windows operating systems version 7 and higher, which helps to...
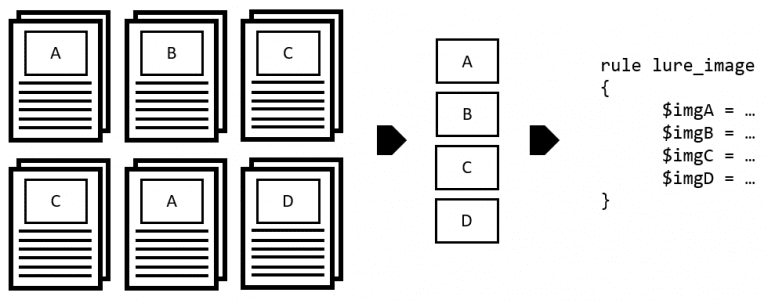
Halogen Halogen is a tool to automate the creation of yara rules against image files embedded within...
Malduck Malduck is your ducky companion in malware analysis journeys. It is mostly based on the Roach project,...