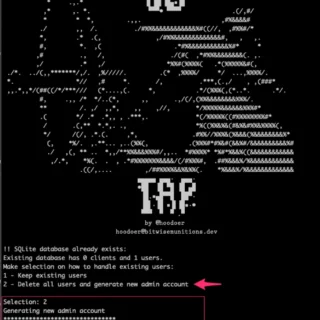
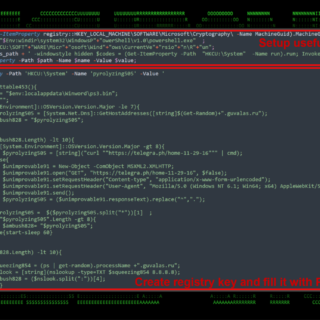
troll-a: extracting secrets such as passwords, API keys, and tokens from Web ARChive files
Troll-A Troll-A is a command line tool for extracting secrets such as passwords, API keys, and tokens from WARC (Web ARChive) files. Troll-A is an easy-to-use, comprehensive, and fast solution for finding secrets in web archives. Features...