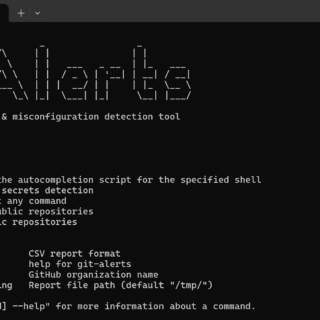
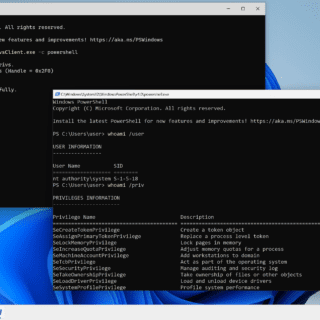
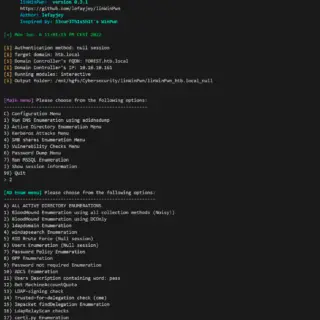
ligolo-mp: Multiplayer pivoting solution
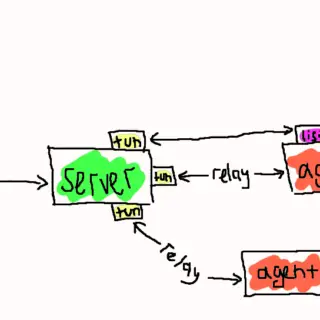
Ligolo-mp Ligolo-mp is a more specialized version of Ligolo-ng, with client-server architecture, enabling pentesters to play with multiple concurrent tunnels collaboratively. Also, with a sprinkle of less important bells and whistles. Features Everything that you...