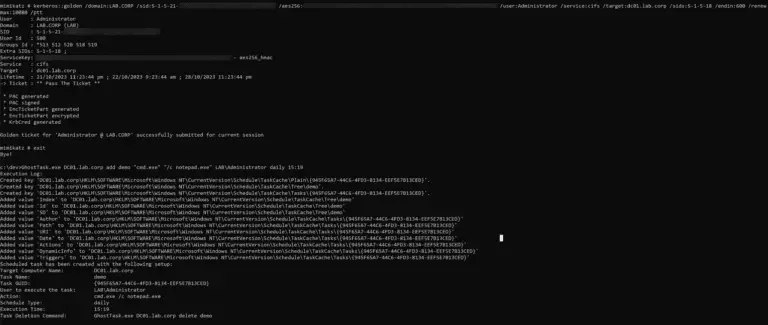
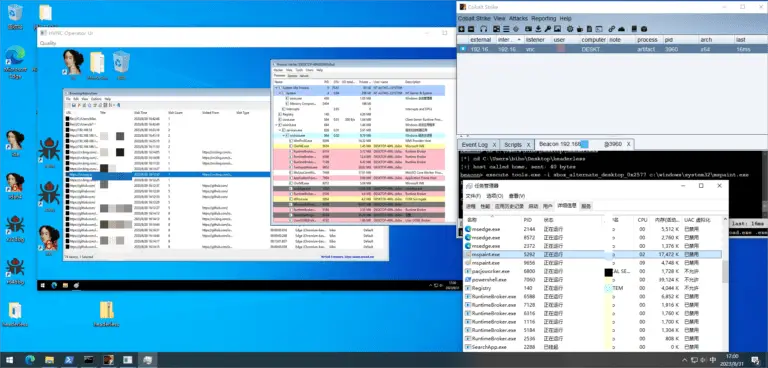
Ghost Scheduled Task While using scheduled tasks as a means of persistence is not a novel approach,...
Network PenTest
Nemesis Nemesis is an offensive data enrichment pipeline and operator support system. Built on Kubernetes with scale...
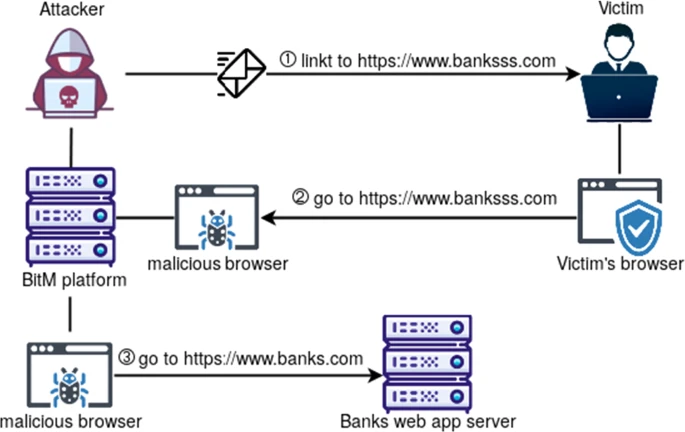
CuddlePhish Weaponized multi-user browser-in-the-middle (BitM) for penetration testers. This attack can be used to bypass multi-factor authentication...
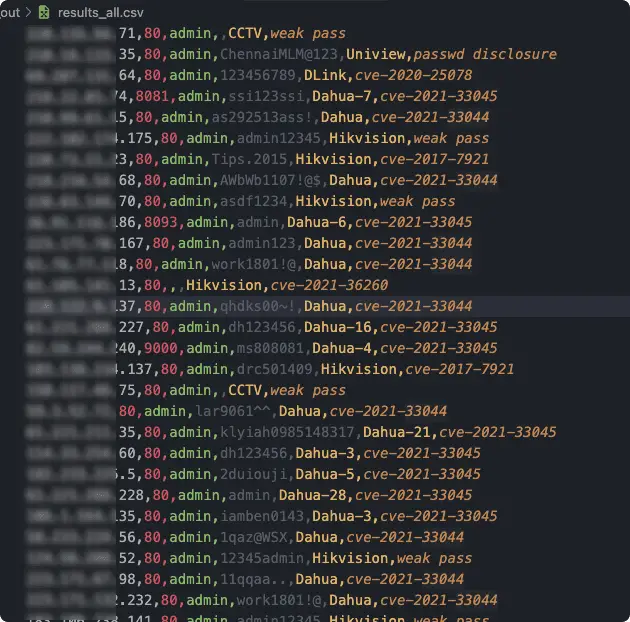
Ingram This is a webcam device vulnerability scanning tool, that already supports Hikvision, Dahua, and other devices....
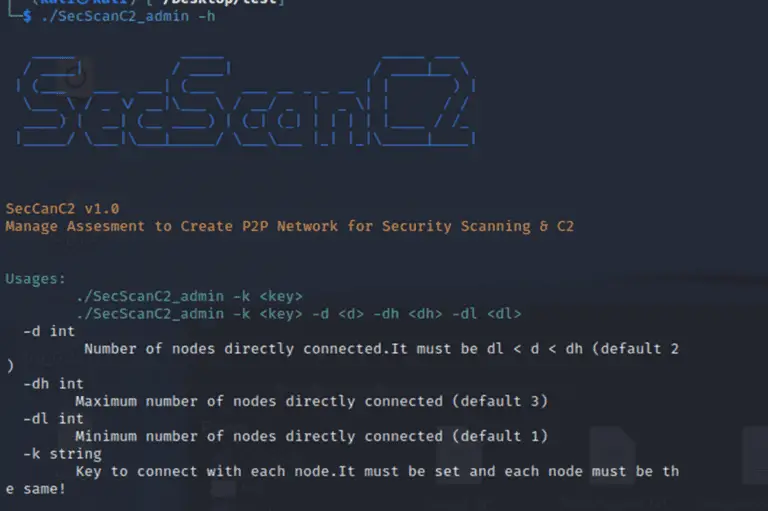
SecScanC2 SecScanC2 can manage assessment to create a P2P network for security scanning & C2. The tool...
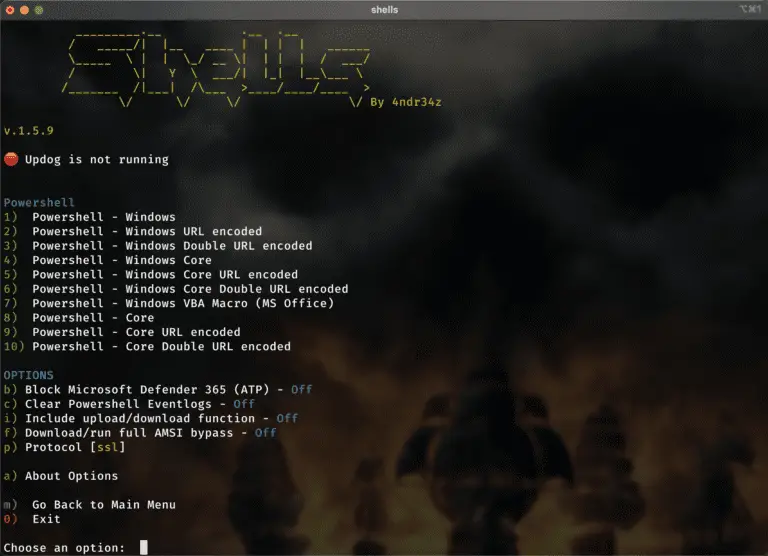
Shellz A script for generating common reverse shells fast and easy. Especially nice when in need of...
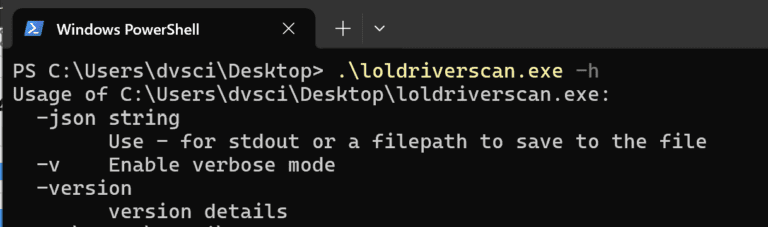
LolDriverScan LolDriverScan is a golang tool that allows users to discover vulnerable drivers on their system. This...
HeaderLessPE HeaderLessPE is a memory PE loading technique used by the Icedid Trojan. Based on this technology,...
ADMiner ADMiner is an Active Directory audit tool that leverages cypher queries to crunch data from the BloodHound graph...
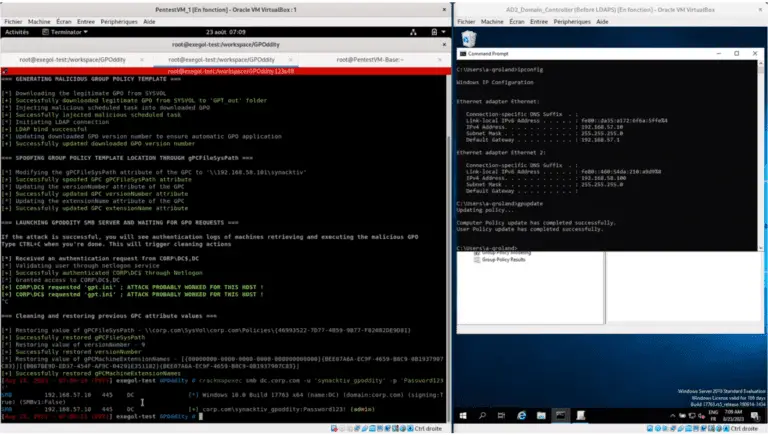
GPOddity The GPOddity project aims at automating GPO attack vectors through NTLM relaying (and more). For more...
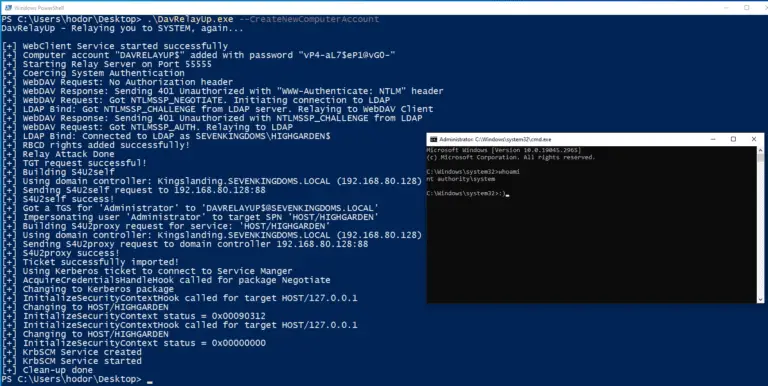
DavRelayUp A quick and dirty port of KrbRelayUp with modifications to allow for NTLM relay from webdav to LDAP...
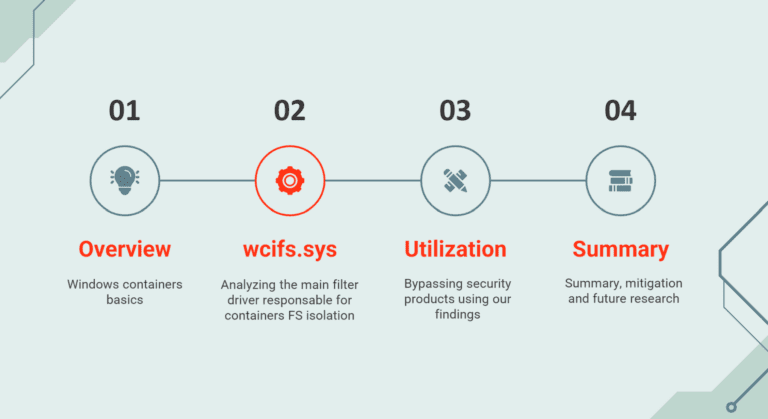
ContainYourself A PoC of the ContainYourself research, presented on DEFCON 31. This tool abuses the Windows containers framework...
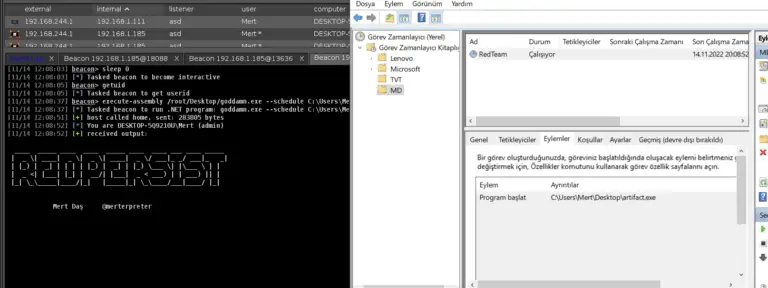
RedPersist RedPersist is a Windows Persistence tool written in C# Usage You can use it with execute-assembly...
TeamsPhisher TeamsPhisher is a Python3 program that facilitates the delivery of phishing messages and attachments to Microsoft...
EternalHush Framework EternalHush Framework is a new open-source project that is an advanced C&C framework. Designed specifically...