Category: Information Gathering
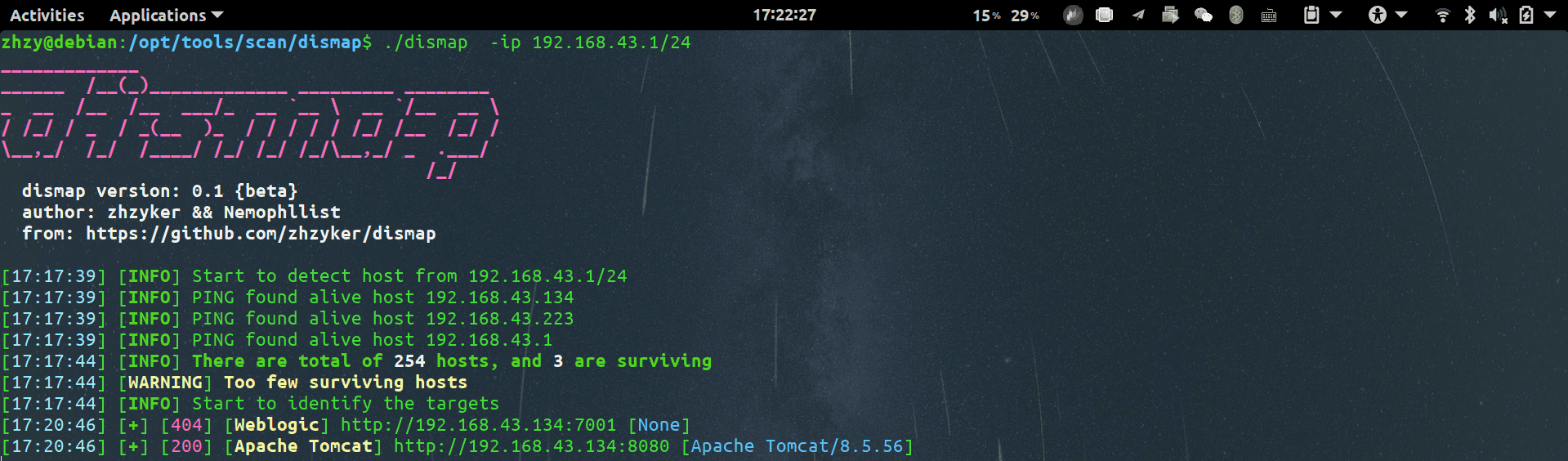
Dismap – Asset discovery and identification tool Dismap positioning is an asset discovery and identification tool; its characteristic function is to quickly identify Web fingerprint information and locate asset types....
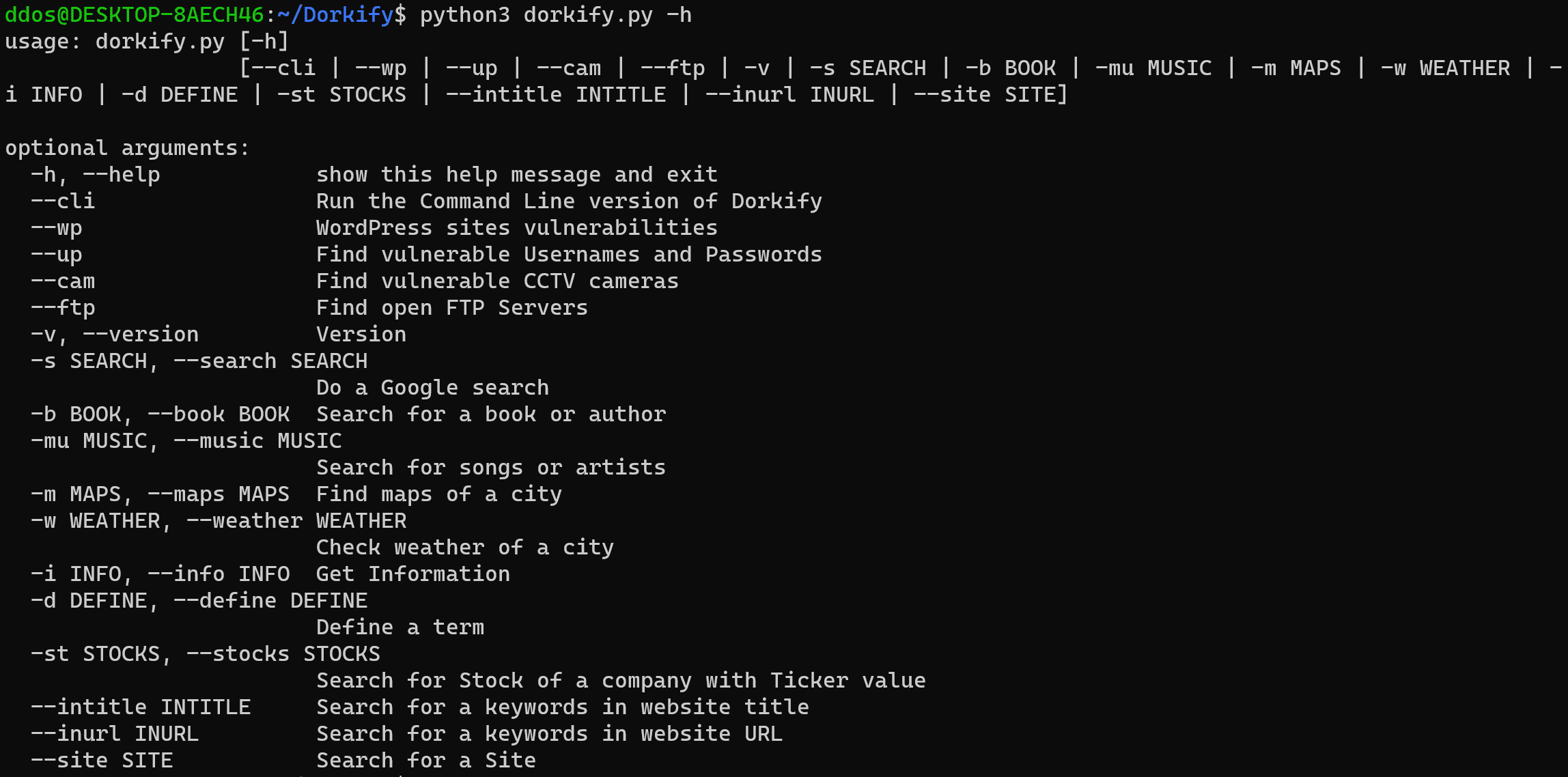
Perform Google Dork search with Dorkify Google dorking is a hacker technique that uses Google Search to find security holes in the configuration and computer code that websites use. Google Dorking...
KnockOutlook KnockOutlook is a C# project that interacts with Outlook’s COM object in order to perform a number of operations useful in red team engagements. Operations checkEnumerates the Outlook installation...
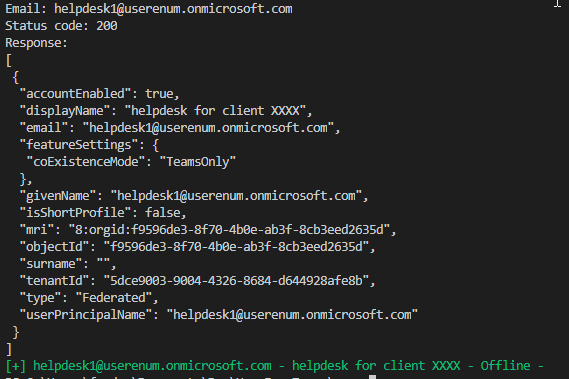
UserEnumTeams User enumeration is a security weakness that allows an attacker to determine whether a specific username is valid. The most common form of user enumeration manifests within the authentication...
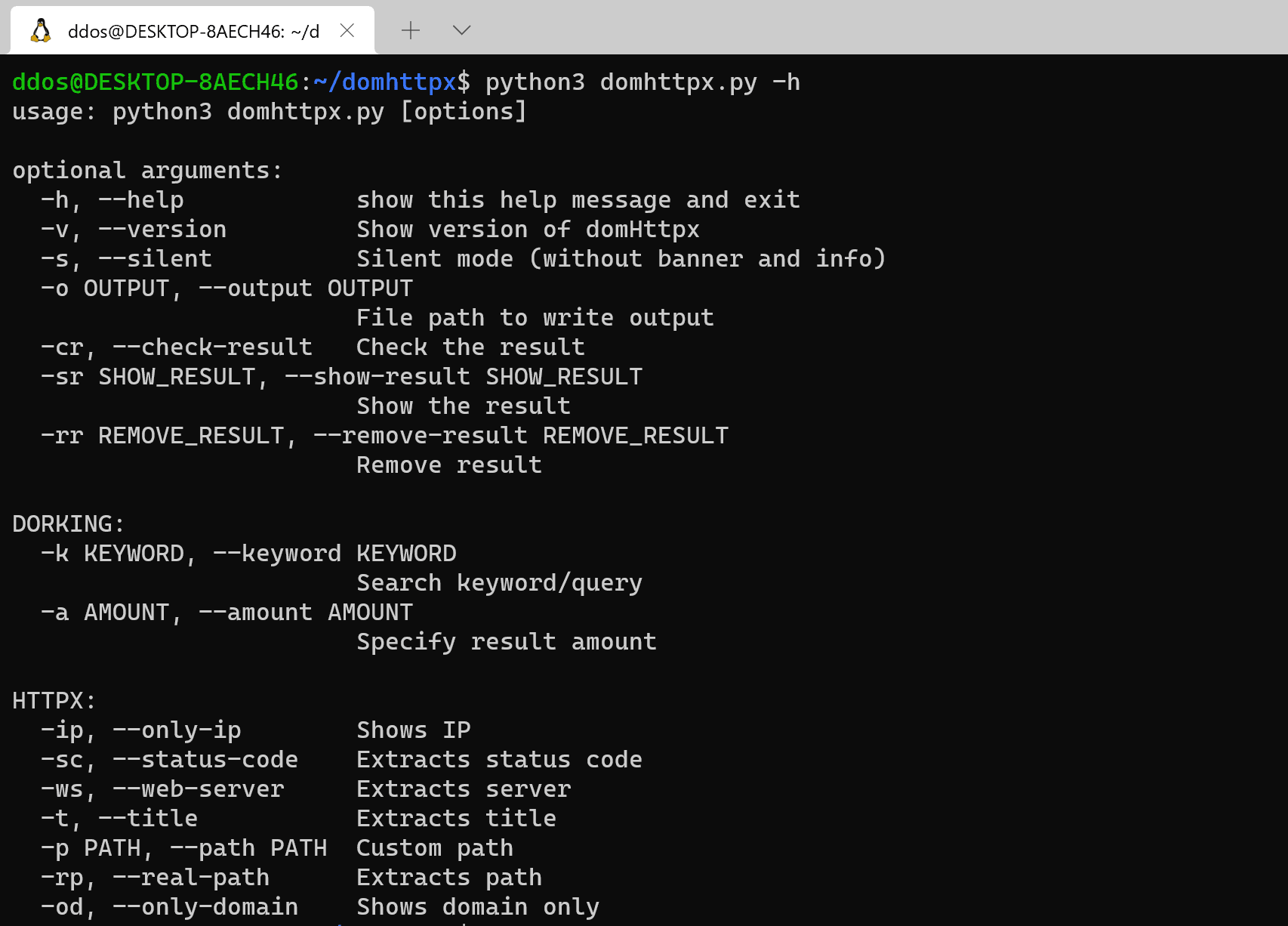
domhttpx domhttpx is a google search engine dorker with an HTTP toolkit built with python, which can make it easier for you to find many URLs/IPs at once in a fast...
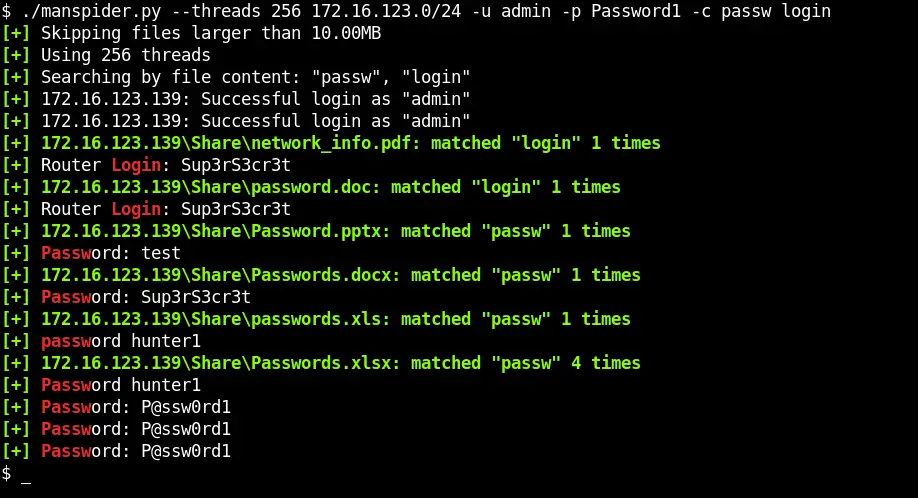
MAN-SPIDER Crawl SMB shares for juicy information. File content searching + regex is supported! File types supported: PDF DOCX XLSX PPTX any text-based format and many more!! MAN-SPIDER will crawl...
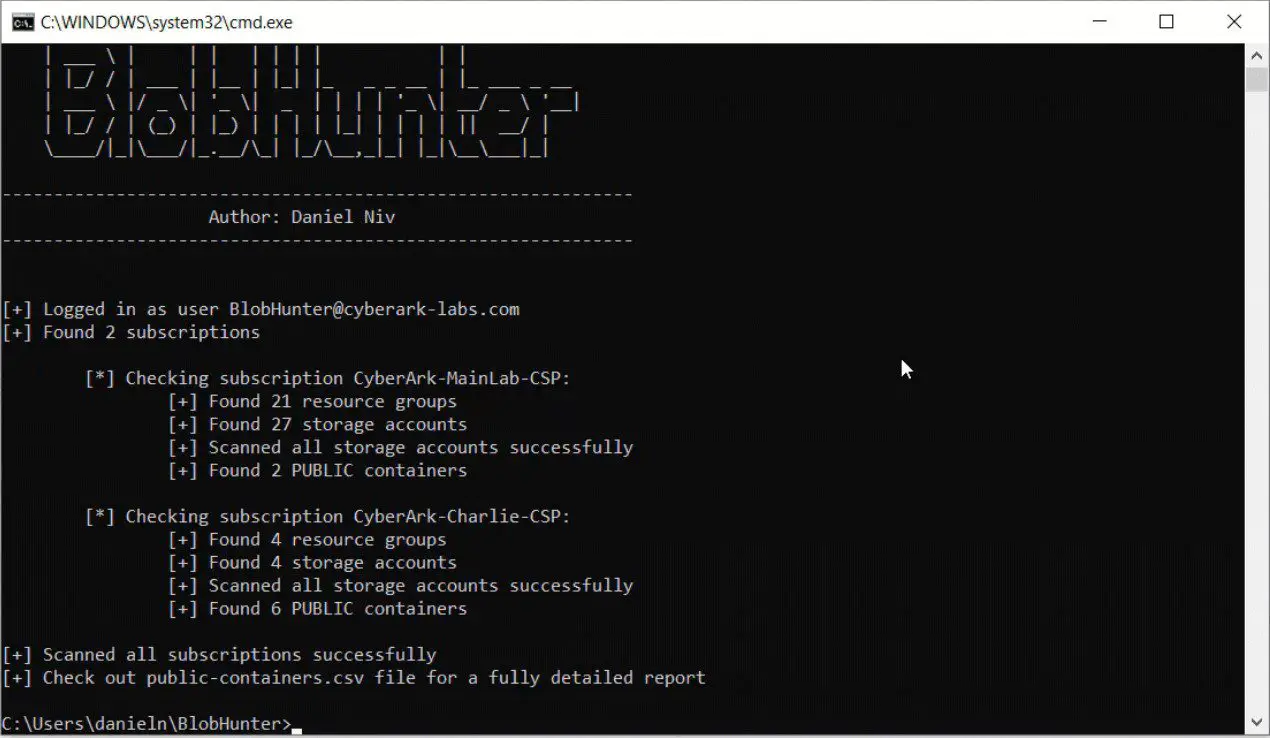
BlobHunter An opensource tool for scanning Azure blob storage accounts for publicly opened blobs. BlobHunter is a part of “Hunting Azure Blobs Exposes Millions of Sensitive Files” research. Overview BlobHunter...
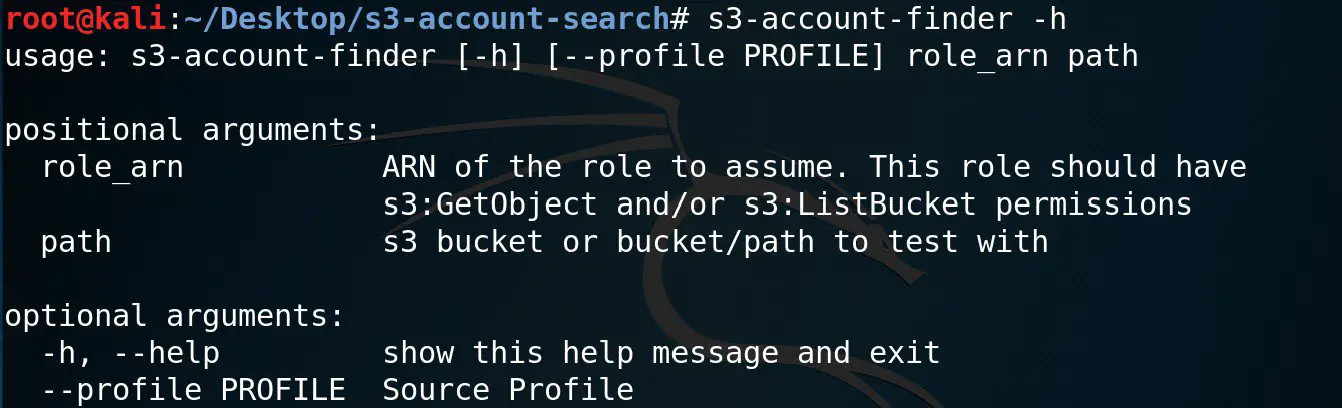
S3 Account Search This tool lets you find the account id an S3 bucket belongs to. For this to work you need to have at least one of these permissions:...
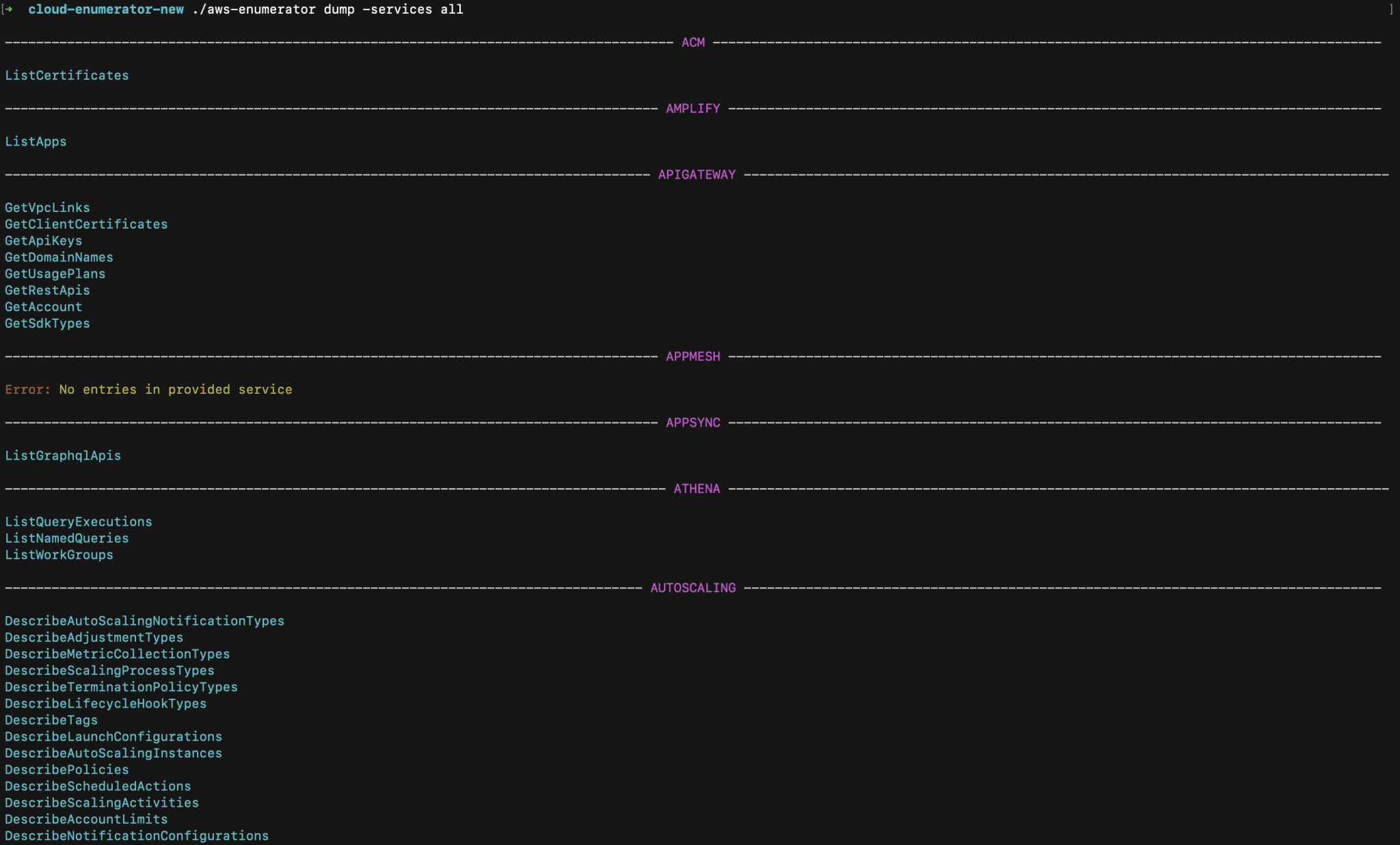
AWS Service Enumeration The AWS Enumerator was created for service enumeration and info-dumping for investigations of penetration testers during Black-Box testing. The tool is intended to speed up the process...
DivideAndScan DivideAndScan is used to efficiently automate the port scanning routine by splitting it into 3 phases: Discover open ports for a bunch of targets. Run Nmap individually for each...
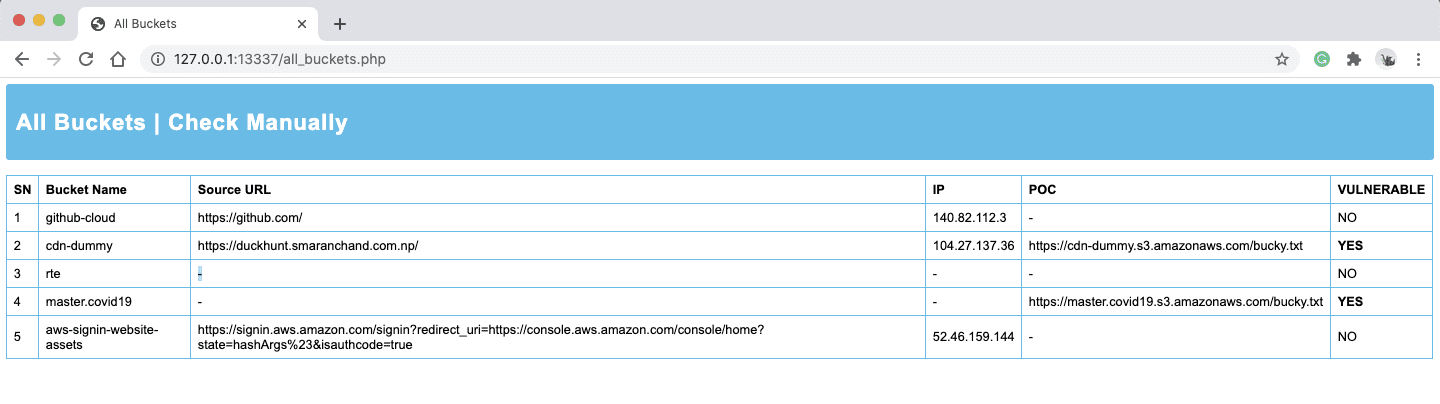
Bucky Bucky is an automatic tool designed to discover S3 bucket misconfiguration, Bucky consists up of two modules Bucky firefox addon and Bucky backend engine. Bucky addon reads the source...
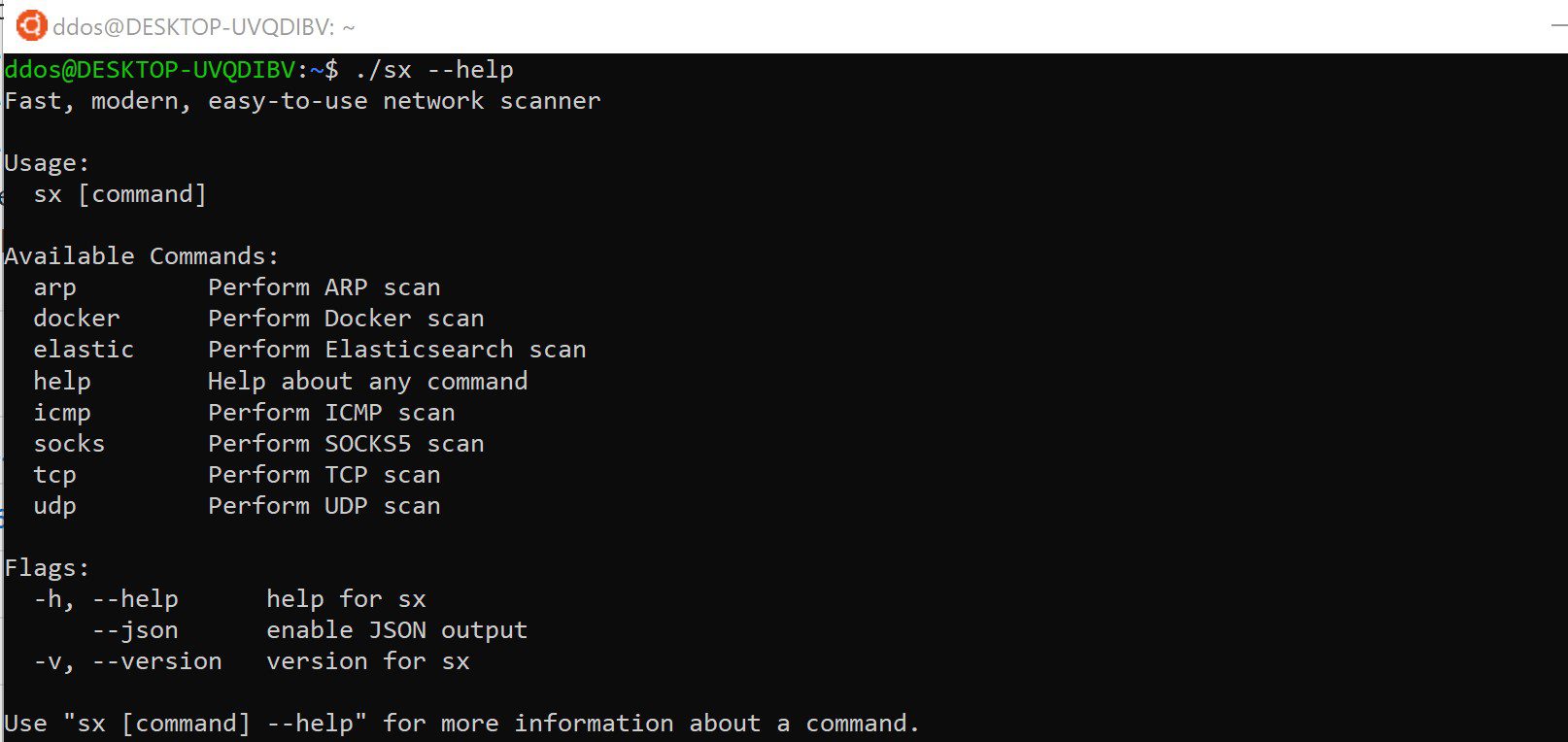
sx is the command-line network scanner designed to follow the UNIX philosophy. The goal of this project is to create the fastest network scanner with clean and simple code. ✨ Features ⚡ 30x...
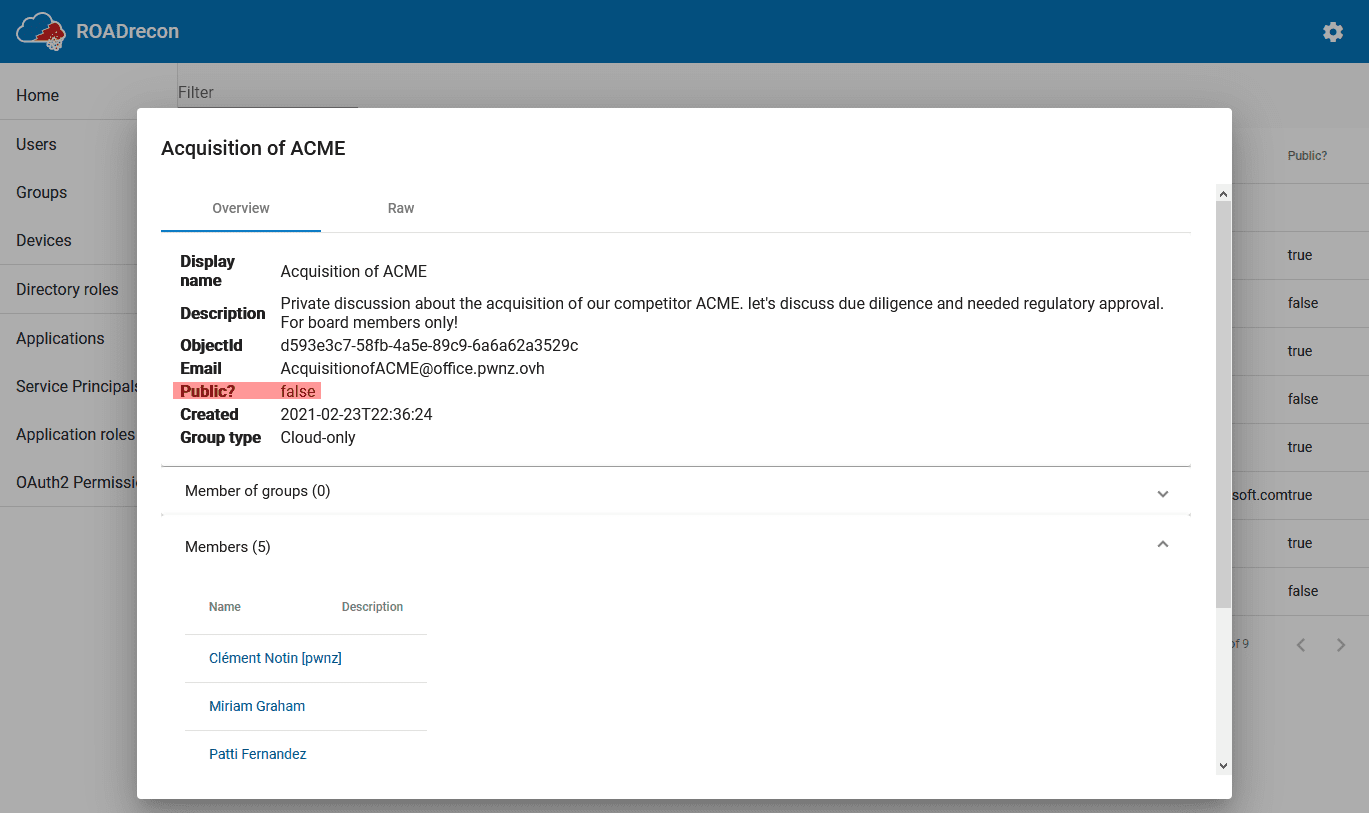
Enumerate Microsoft 365 Groups in a tenant with their metadata The all_groups.py script allows to enumerate all Microsoft 365 Groups in an Azure AD tenant with their metadata: name visibility:...
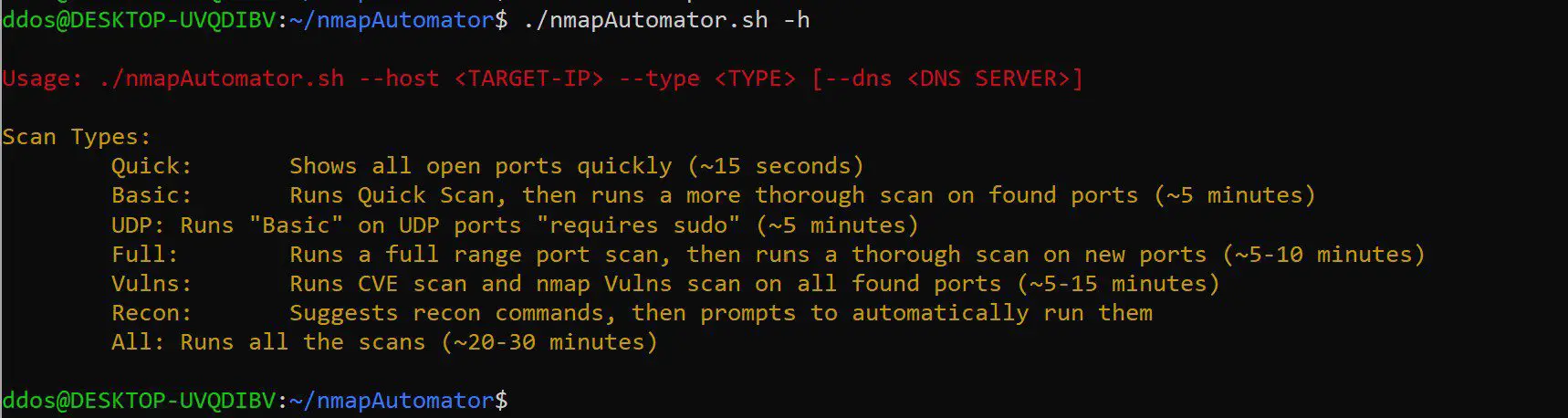
nmapAutomator A script that you can run in the background! Summary The main goal for the nmapAutomator script is to automate all of the processes of recon/enumeration that are run...
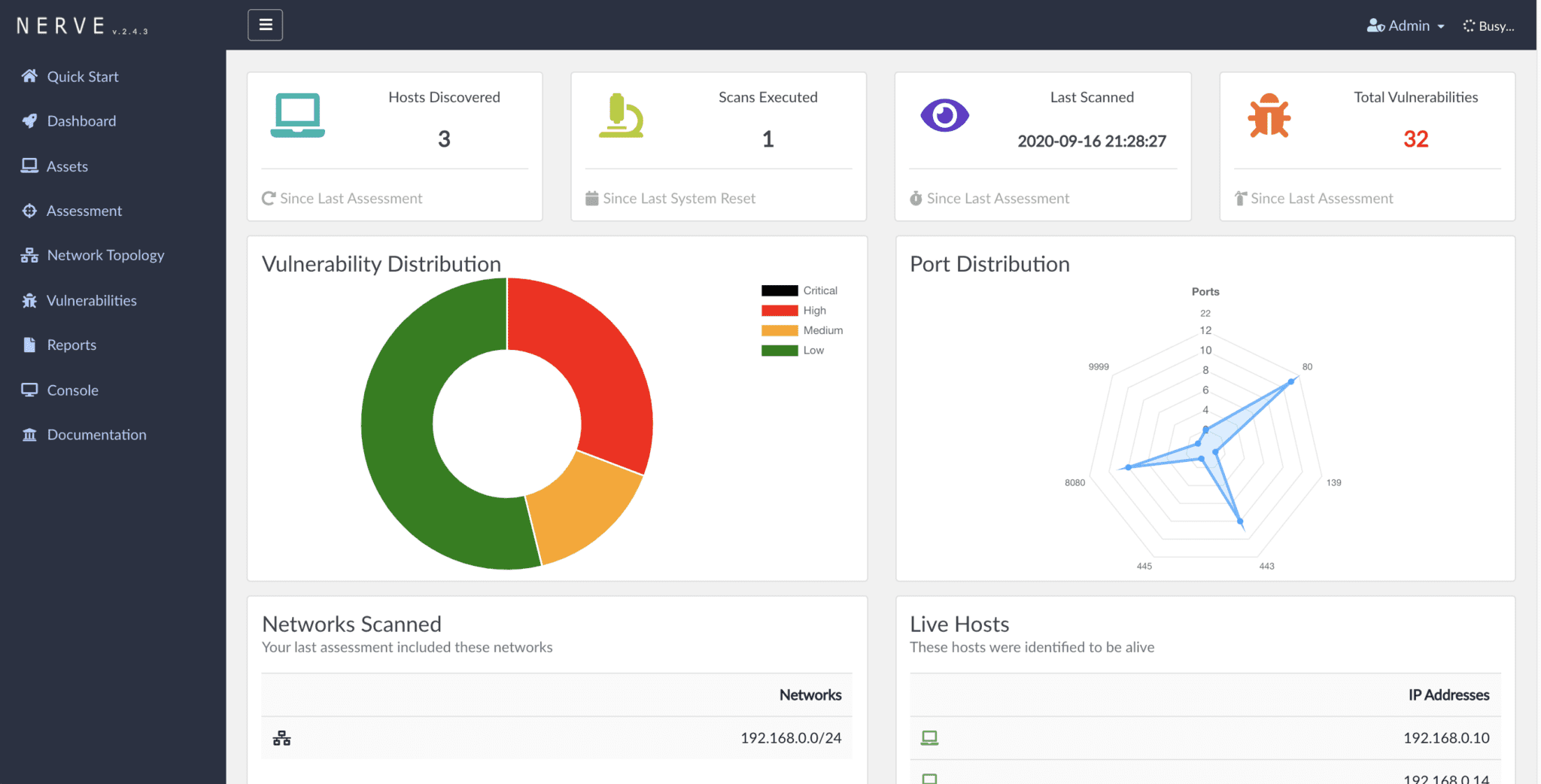
Network Exploitation, Reconnaissance & Vulnerability Engine (N.E.R.V.E) We believe security scanning should be done continuously. Not daily, weekly, monthly, or quarterly. The benefit of running security scanning continuously can be...