Category: Maintaining Access
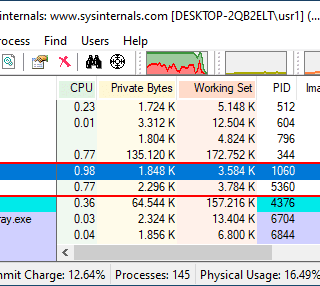
r77 Rootkit Ring 3 rootkit r77 is a ring 3 Rootkit that hides the following entities from all processes: Files, directories, named pipes, scheduled tasks Processes CPU usage Registry keys & values TCP &...
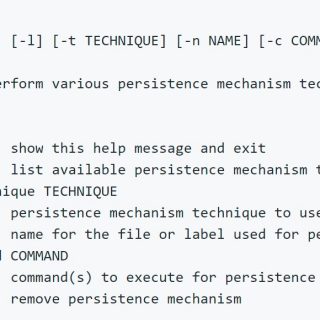
PoisonApple Command-line tool to perform various persistence mechanism techniques on macOS. This tool was designed to be used by threat hunters for cyber threat emulation purposes. Changelog v0.2.3 Formatted code using black, bump license for...
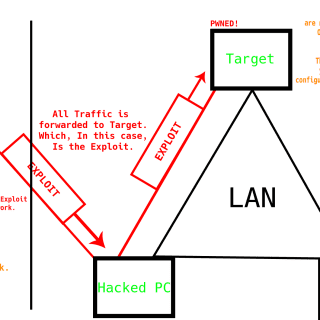
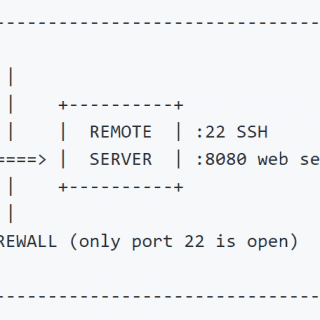
Boomerang Boomerang is a tool to expose multiple internal servers to the web/cloud using HTTP+TCP Tunneling. The Server will expose 2 ports on the Cloud. One will be where tools like proxychains can connect...
Apollo Apollo is a Windows agent written in C# using the 4.0 .NET Framework designed to be used in SpecterOps training offerings. Apollo lacks some evasive tradecraft provided by other commercial and open-source tools,...
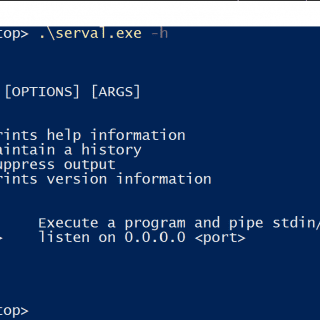
serval Serval is a lightweight, easy-to-use, binary for spawning reverse and bind shells for pentests or pentesting exercises. It is cross-platform and can be compiled for both Windows 32 & 64-bit and Linux 32...
Maalik Network Pivoting and Post Exploitation Framework. Features Console Features Desktop notification on new sessions. Kill Online sessions easily. Build Maalik Client, Fhdawn easily. Configurable values in settings.ini Root shell. Multithreaded, Get multiple sessions. Maalik...
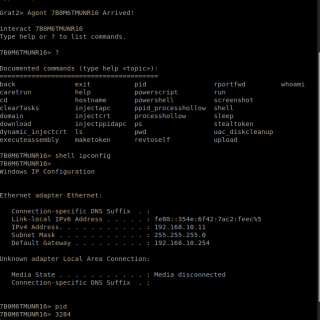
GRAT2 GRAT2 is a Command and Control (C2) tool written in python3 and the client in .NET 4.0. The main idea came from Georgios Koumettou who initiated the project. Current Features: Evasion Techniques: Sandbox (Check whether...
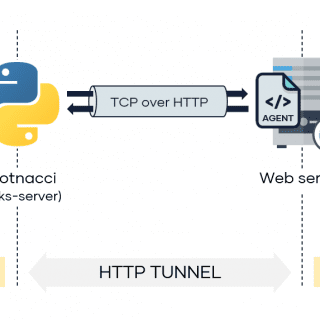
pivotnacci Pivot into the internal network by deploying HTTP agents. Pivotnacci allows you to create a socks server that communicates with HTTP agents. The architecture looks like the following: This tool was inspired by the...
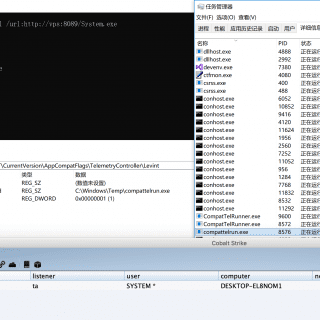
TELEMETRY TELEMETRY is a C# For Windows PERSISTENCE Today we’re going to talk about a persistence method that takes advantage of some of the wonderful telemetry that Microsoft has included in Windows versions for the...
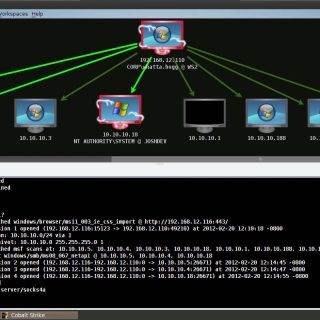
Socks Over RDP This tool adds the capability of a SOCKS proxy to Terminal Services (or Remote Desktop Services). It uses Dynamic Virtual Channel that enables us to communicate over an open RDP connection...
gTunnel A TCP tunneling suite built with golang and gRPC. gTunnel can manage multiple forward and reverse tunnels that are all carried over a single TCP/HTTP2 connection. I wanted to learn a new language,...
Ligolo: Reverse Tunneling made easy for pentesters, by pentesters Ligolo is a simple and lightweight tool for establishing SOCKS5 or TCP tunnels from a reverse connection in complete safety (TLS certificate with the elliptical curve). It is comparable to Meterpreter with Autoroute + Socks4a but more...
StayKit – Cobalt Strike persistence kit StayKit is an extension for Cobalt Strike persistence by leveraging the execute_assembly function with the SharpStay .NET assembly. The aggressor script handles payload creation by reading the template...
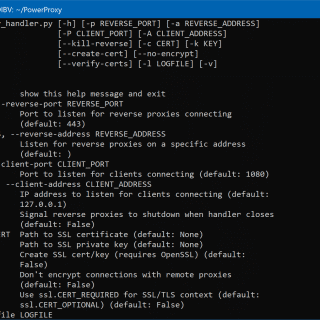
PowerProxy PowerShell SOCKS proxy with reverse proxy capabilities. PowerProxy is written with penetration testers in mind. Reverse proxy functionality is a priority, for traversing networks that block inbound connections. Reverse proxy connections are encrypted...
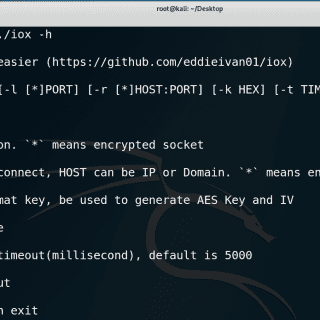
iox Tool for port forward & intranet proxy, just like lcx/ew, but better Why write? lcx and ew are awesome but can be improved. when I first used them, I can’t remember these complicated parameters for...