Category: Post Exploitation
linux exploit suggester.sh was inspired by the excellent Linux_Exploit_Suggester script by PenturaLabs. The issue with Pentura’s script, however, is that it isn’t up to date anymore (the script was last updated in early...
RandomPS-Scripts is the PowerShell Scripts focused on Post-Exploitation Capabilities. Download git clone https://github.com/xorrior/RandomPS-Scripts.git This project includes JScriptShellThis script can be used to remotely (or locally) deploy a wmi event subscription with...
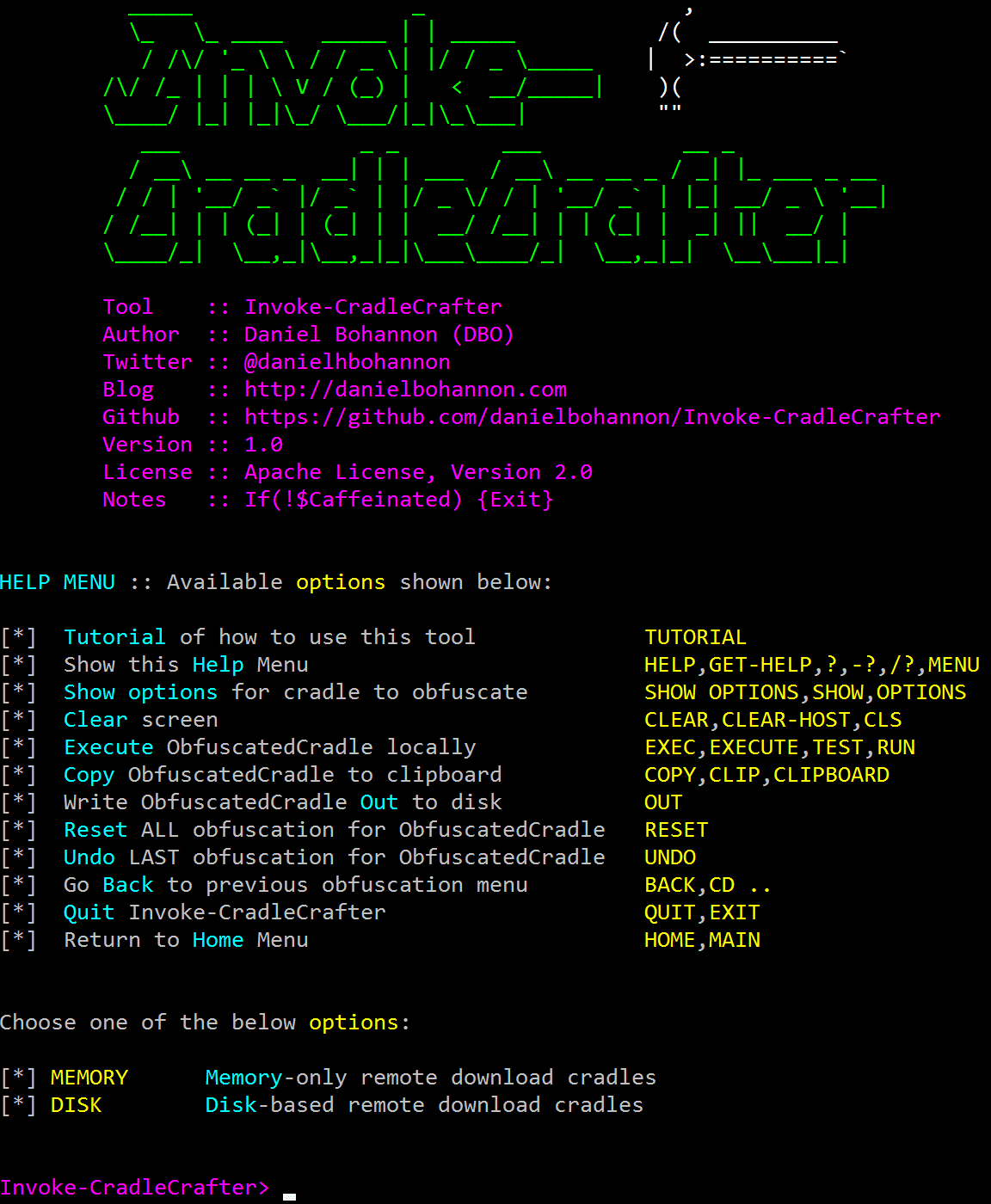
Invoke-CradleCrafter v1.1 Invoke-CradleCrafter is a PowerShell v2.0+ compatible PowerShell remote download cradle generator and obfuscator. Background In the Fall of 2016 after releasing Invoke-Obfuscation, I continued updating my spreadsheet...
MimiDbg is a PowerShell oneliner that leverages the Microsoft tools “DbgShell”. DbgShell is a PowerShell front-end for the Windows debugger engine. You can find DbgShell here MimiDbg uses PowerMemory concept to retrieve Wdigest...
Invoke-WCMDump PowerShell script to dump Windows credentials from the Credential Manager. Credential dumping is the process of obtaining account login and password information from the operating system and software. Credentials...
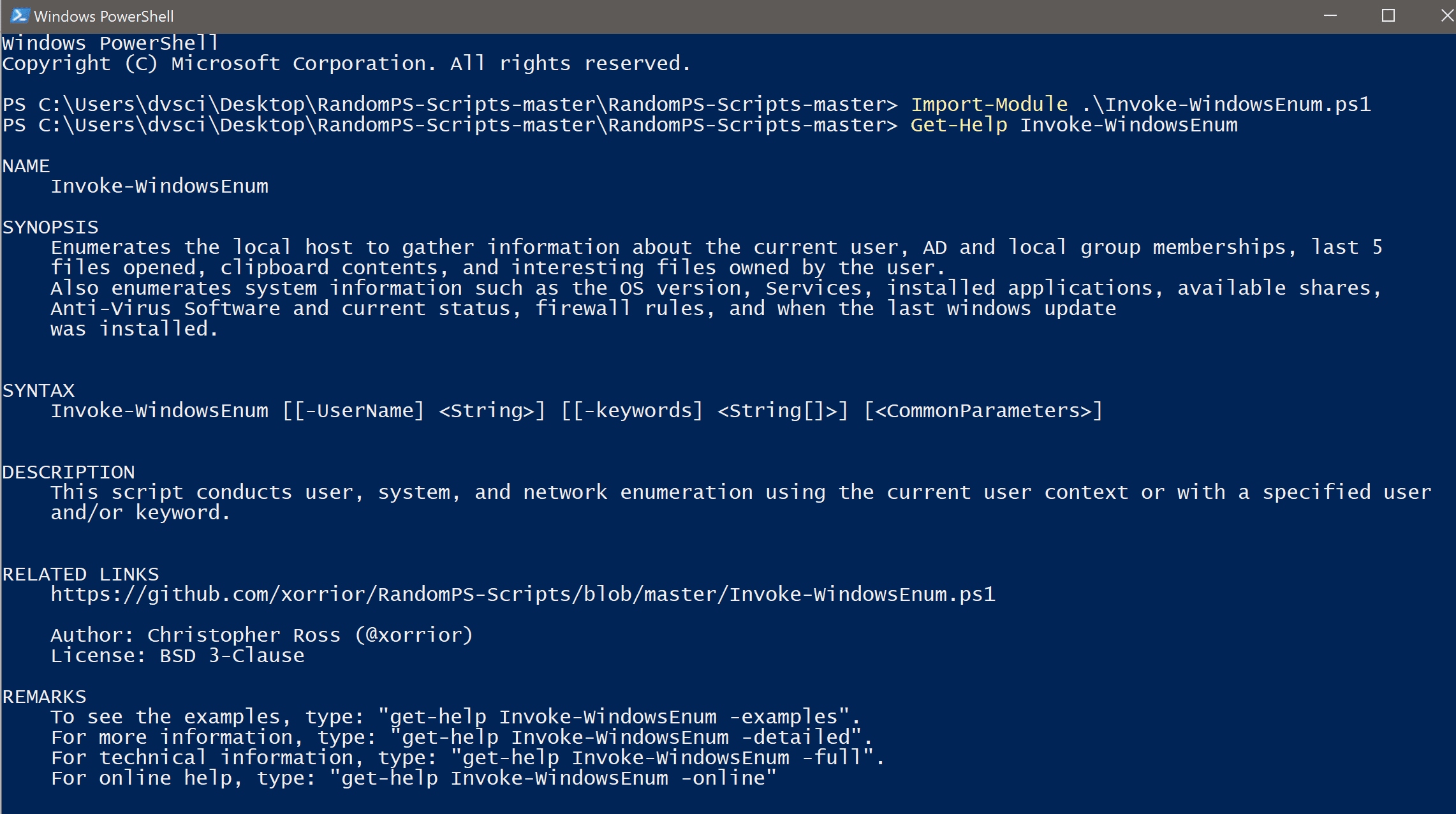
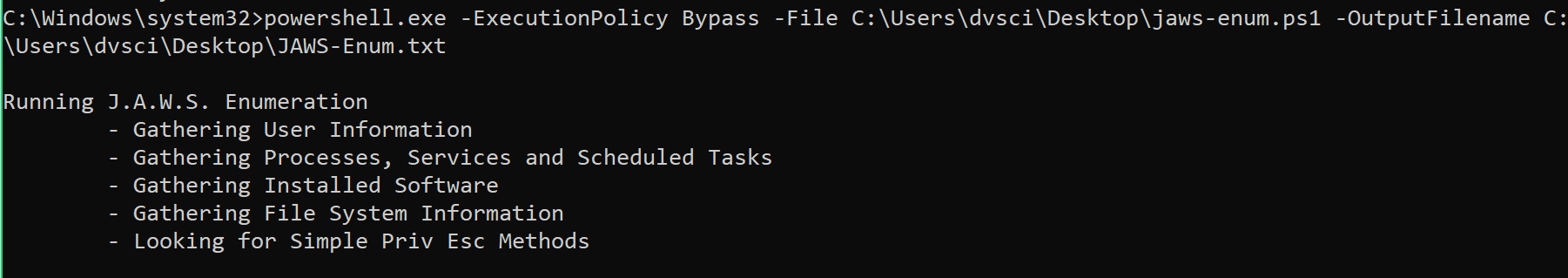
JAWS is PowerShell script designed to help penetration testers (and CTFers) quickly identify potential privilege escalation vectors on Windows systems. It is written using PowerShell 2.0 so ‘should’ run on...
RottenPotato – Local Privilege Escalation from Windows Service Accounts to SYSTEM The idea behind this vulnerability is simple to describe at a high level: Trick the “NT AUTHORITY\SYSTEM” account into...
poet A simple POst-Exploitation Tool. overview The client program runs on the target machine and is configured with an IP address (the server) to connect to and a frequency to...
Swift Keylogger – macOS Keylogger It is a simple and easy to use keylogger for macOS. It is not meant to be malicious. There are only a few keyloggers available...
After you got a shell or simply put, get xp_cmdshell using the injection point, we can only run the Windows command line to get the target system information. the command...
iMessagesBackdoor A script to help set up an event handler in order to install a persistent backdoor that can be activated by sending a message. Explanation Just as Mail.app and Outlook can be used...
CVE-2017-7533 A race condition was found in the Linux kernel, present since v3.14-rc1 through v4.12. The race happens between threads of inotify_handle_event() and vfs_rename() while running the rename operation against...
DBC2 LAST/CURRENT VERSION: 0.2.6 Author: Arno0x0x – @Arno0x0x DBC2 (DropboxC2) is a modular post-exploitation tool, composed of an agent running on the victim’s machine, a controller, running on any machine, powershell...
PSAmsi audit defeat AMSI signature tool PSAmsi is a tool for auditing and defeating AMSI signatures. It’s best utilized in a test environment to quickly create payloads you know will...
pOSt-eX – OS X post-exploitation scripts mail.py – Creates an ApleScript payload with Empire and configures a mail rule to launch it persist.py – EmPyre module implementation of mail.py monitor.py...