Category: Reverse Engineering
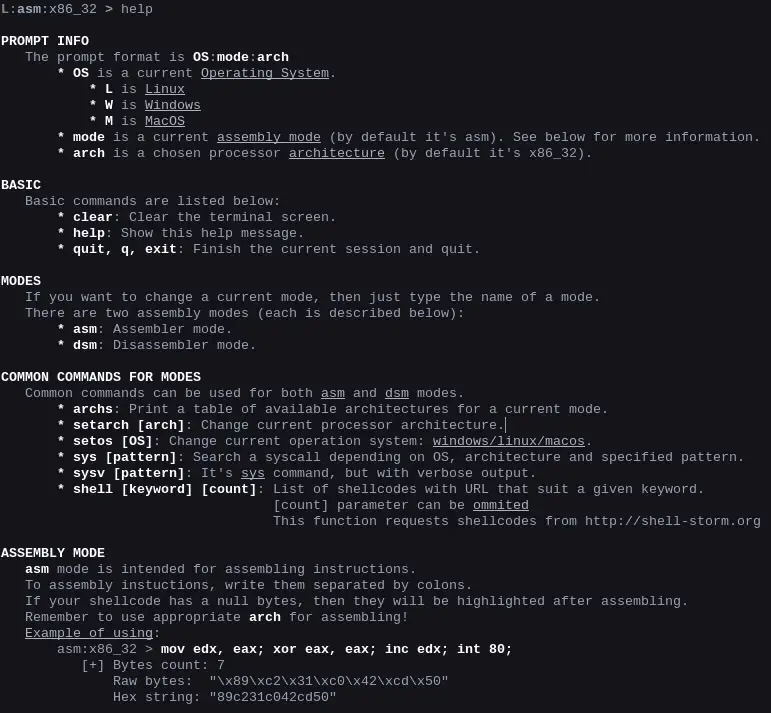
Shellen Shellen is an interactive shellcoding environment. If you want a handy tool to write shellcodes, then shellen may be your friend. Also, it can be used just as assembly/disassembly...
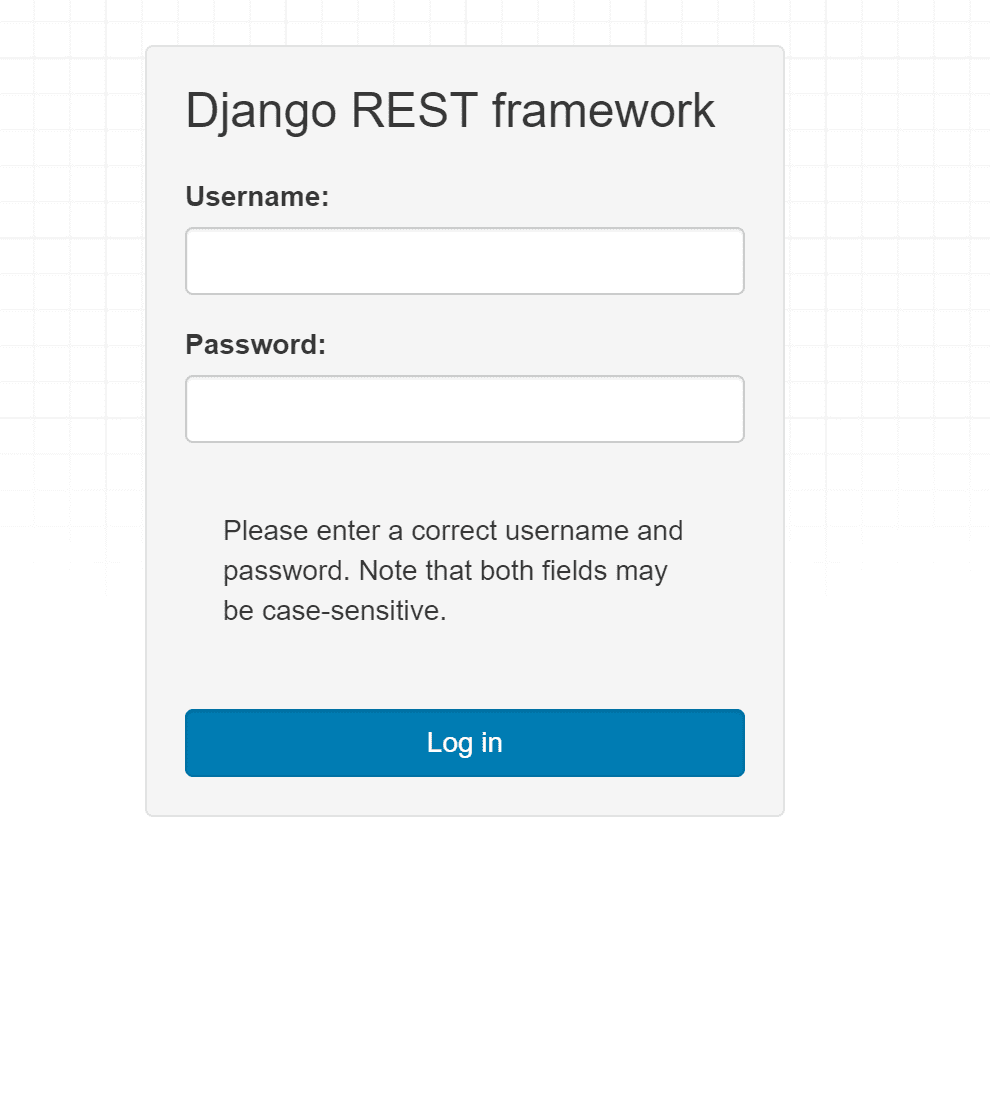
djangoctf v1.1 A platform for jeopardy CTF (capture-the-flag) competitions written in Django. CTF cybersecurity competitions have become an increasingly popular form of challenges for aspiring cybersecurity students. After the success...
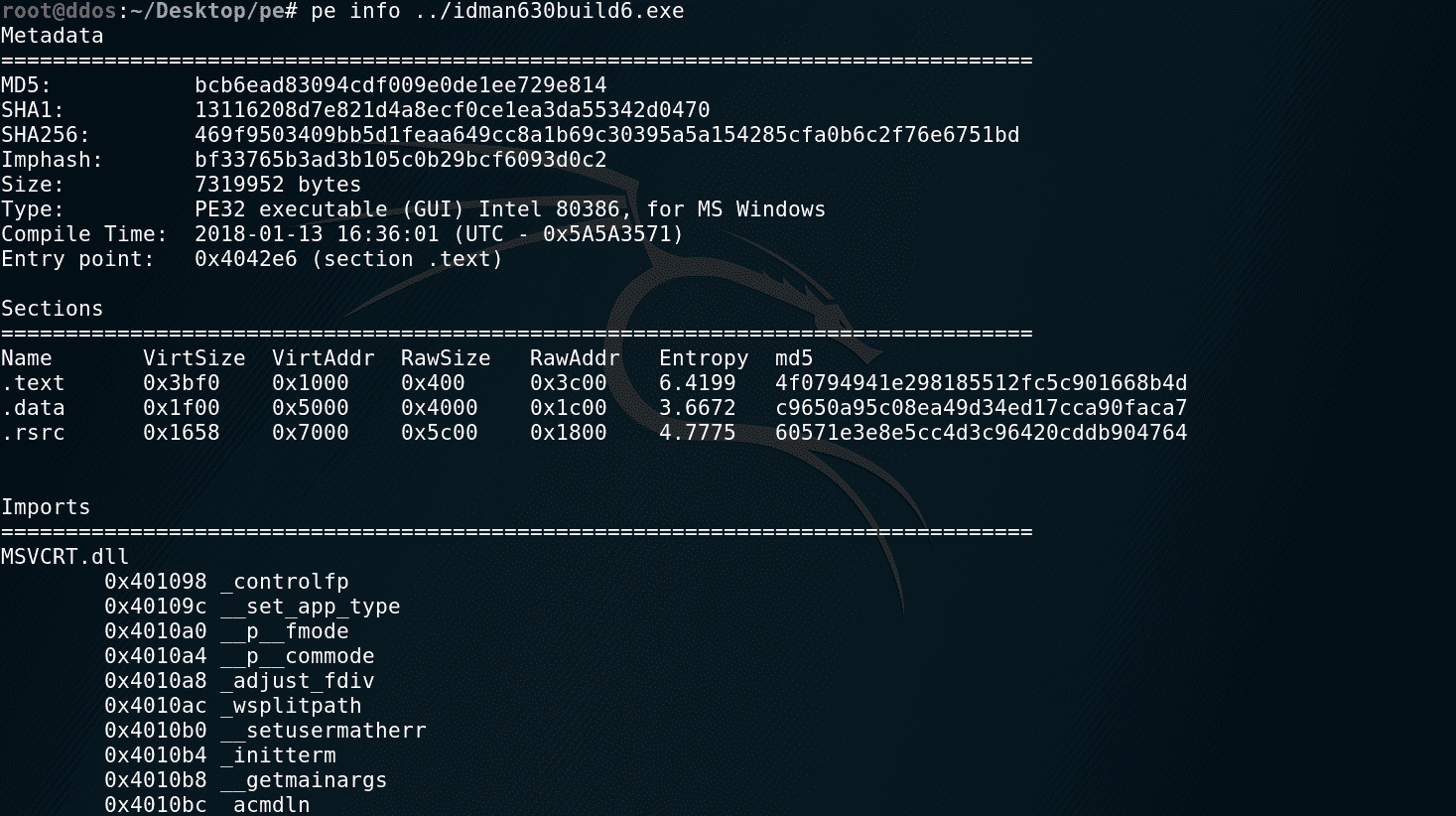
PE Tool to analyze PE files in python 3. Current features : Show information about the file (import, exports, resources) Search for interesting information in the file (abnormal resources, peid…)...
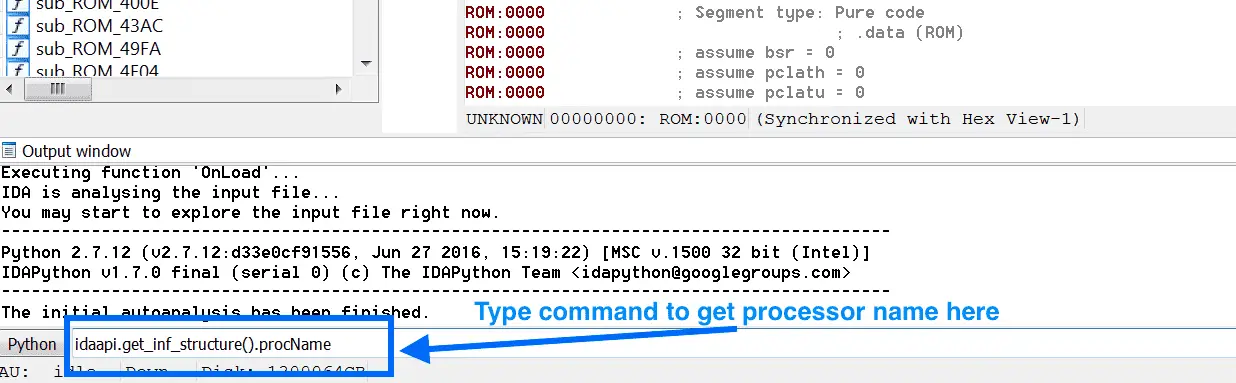
IDAPython Embedded Toolkit The IDAPython Embedded Toolkit is a set of script to automate many of the steps associated with statically analyzing, or reverse engineering, the firmware of embedded devices...
Shellcode Factory tool A tool to print and test shellcodes from assembly code. It supports both Gas and Intel syntax (.s and .asm extensions respectively), as well as x86 and x64 architectures. Download...
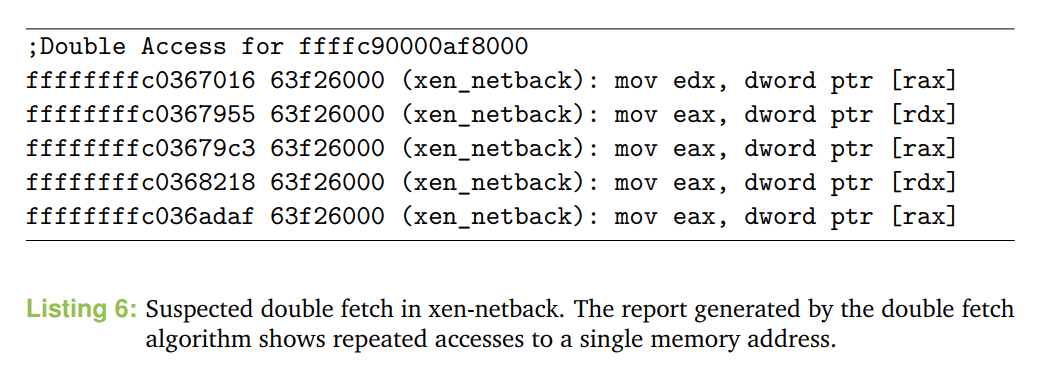
Xenpwn is a toolkit for memory access tracing using hardware-assisted virtualization. It runs as a normal user space application inside the management domain (dom0) of a Xen hypervisor and can...
TitanHide is a driver intended to hide debuggers from certain processes. The driver hooks various Nt* kernel functions (using SSDT table hooks) and modifies the return values of the original...
CTF Works Tools and scripts for CTF exploit/pwnable challenge development. Challenge Organization Each challenge goes in its own directory in challenges/${challenge} Each challenge must be packaged as a docker container and must have a Dockerfile...
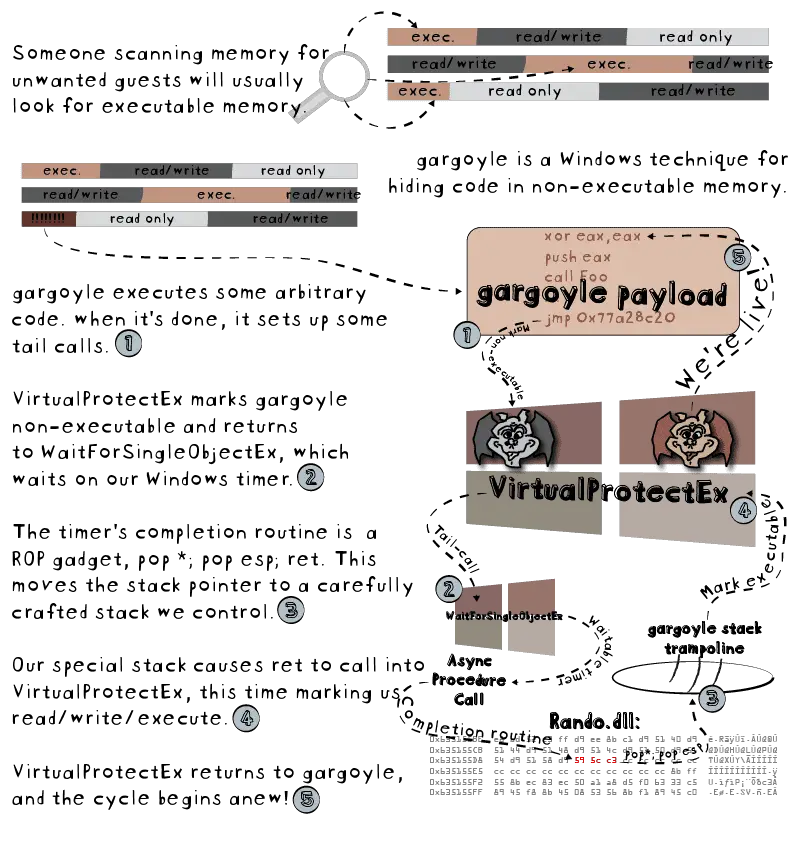
Building gargoyle gargoyle is only implemented for 32-bit Windows (64-bit Windows on Windows is fine). You must have the following installed: Visual Studio: 2017 Community is tested, but it may...
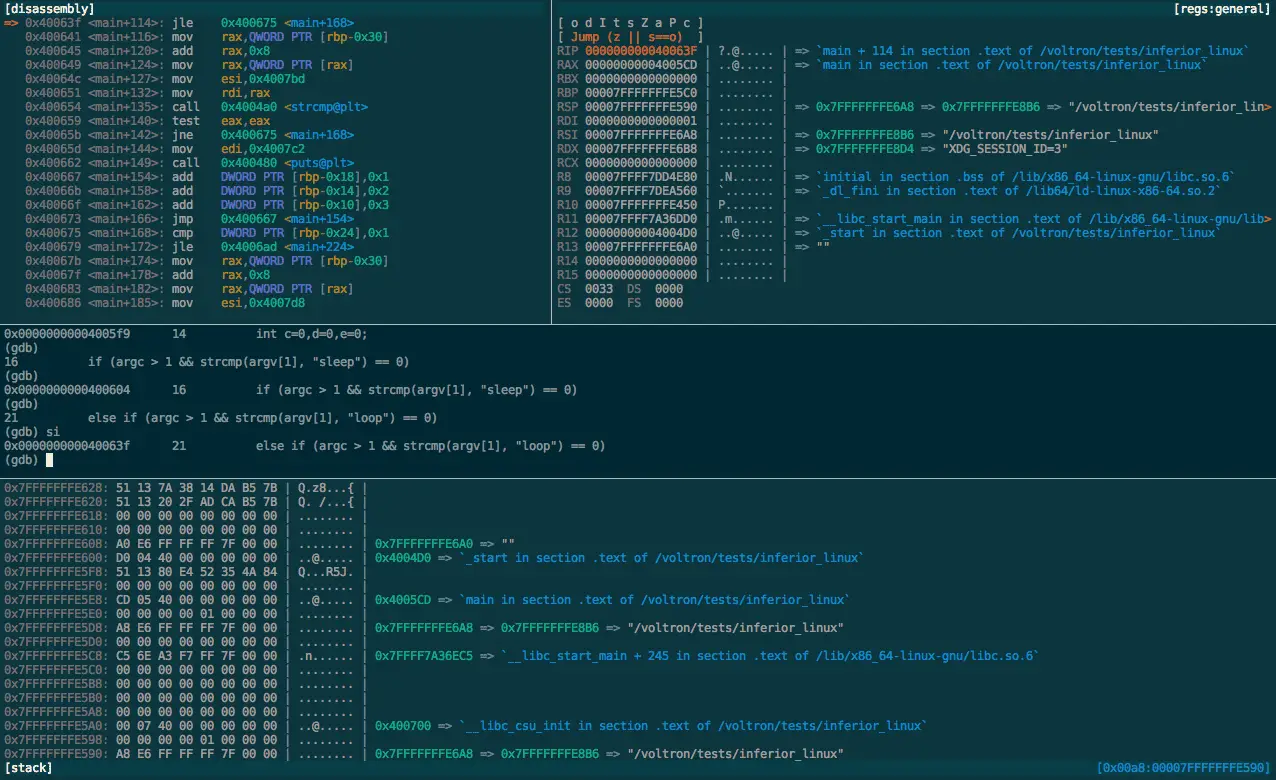
Voltron is an extensible debugger UI toolkit written in Python. It aims to improve the user experience of various debuggers (LLDB, GDB, VDB, and WinDbg) by enabling the attachment of...
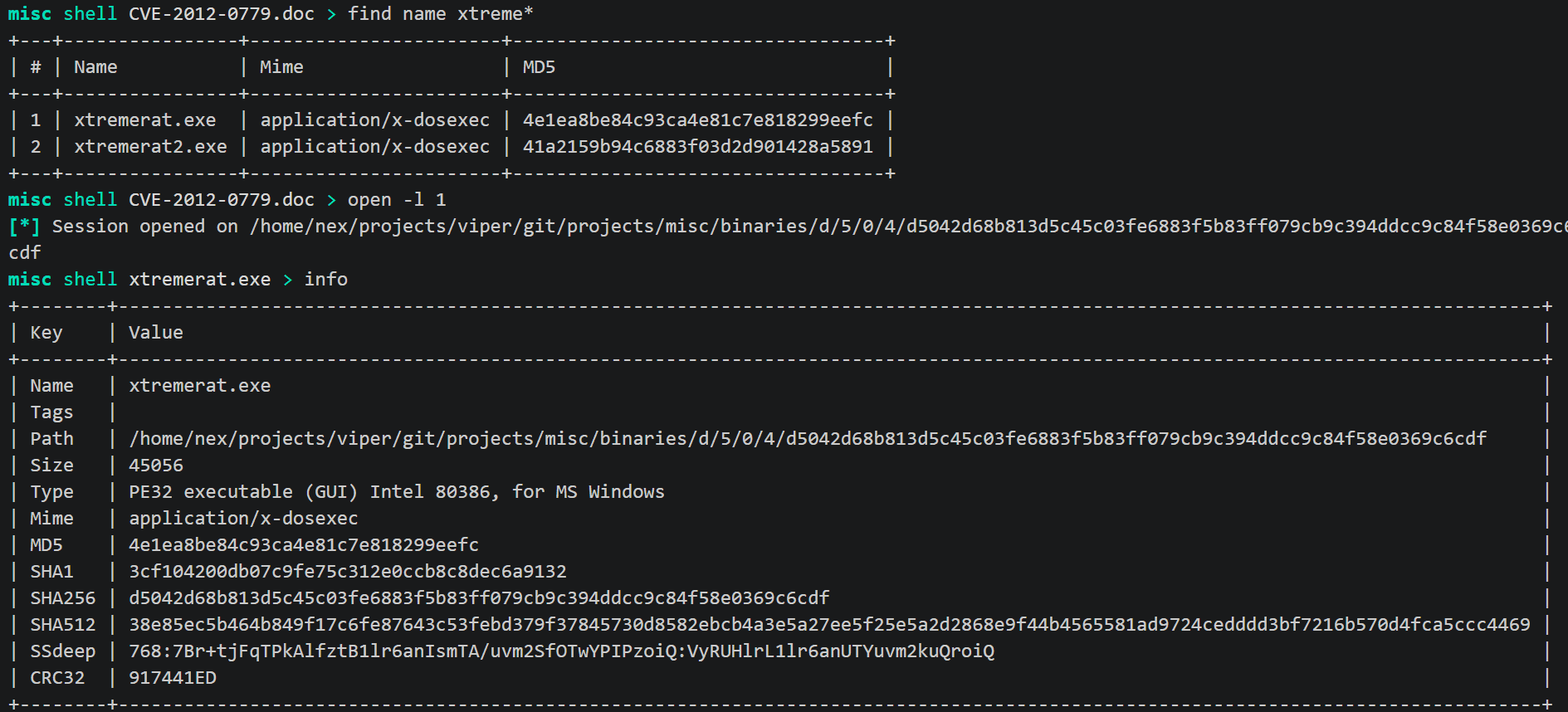
Viper is a binary analysis and management framework. Its fundamental objective is to provide a solution to easily organize your collection of malware and exploit samples as well as your...
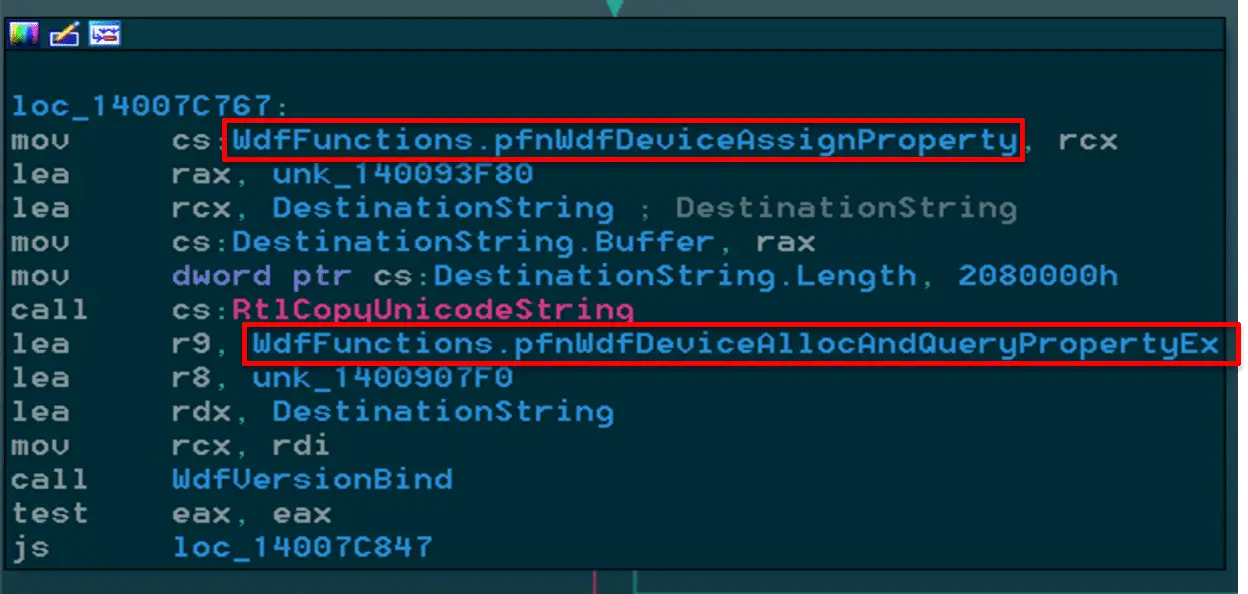
DriverBuddy is an IDAPython plugin that helps automate some of the tedium surrounding the reverse engineering of Windows kernel drivers. Image: NCCGROUP Quickstart DriverBuddy Installation Instructions Clone the repo: git...
PoC code implementing variant 3a of the Meltdown attack for AArch64. This allows reading all (potentially excluding registers whose read has side effects – not verified) system registers from user...
ripr is a tool that helps you rip out functionality from binary code and use it from python. It accomplishes this by pairing the Unicorn-Engine with Binary Ninja. Currently, x86, x64, and arm are supported and work...
What. Usercorn is an analysis and emulator framework, with a base similar to qemu-user. It can run arbitrary binaries on a different host kernel, unlike qemu-user. While recording full system...