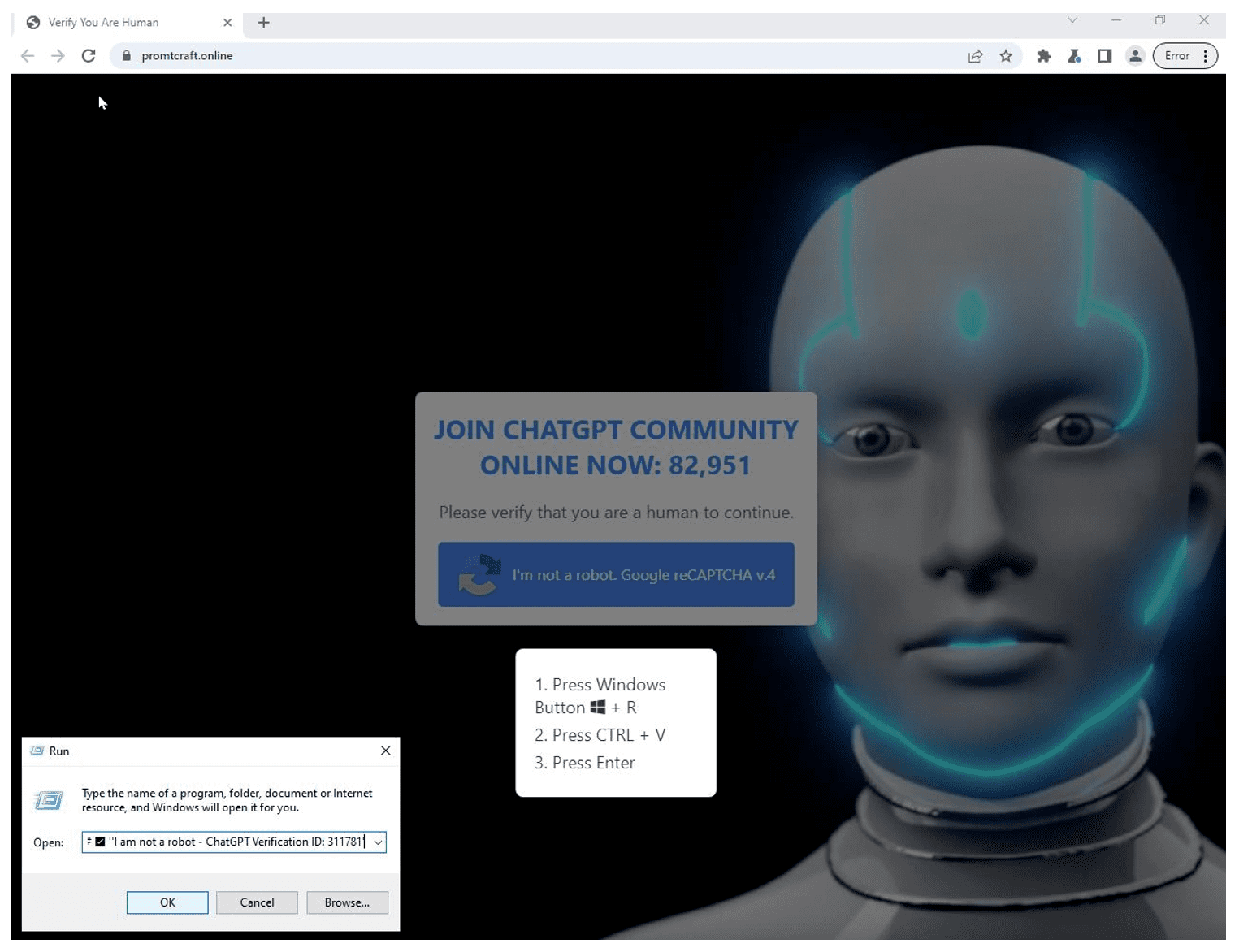
ChatGPT impersonation used in ClickFix payload delivery | Image: Proofpoint
In a detailed report, Proofpoint researchers have unveiled the alarming rise of a unique social engineering method dubbed ClickFix, which exploits human behavior to spread malware through self-inflicted compromises. Initially detected in early 2024 in campaigns by the access broker TA571 and a threat cluster named ClearFake, ClickFix is now a widespread menace across the cybersecurity landscape.
ClickFix leverages fake error messages in dialog boxes to trick users into running malicious PowerShell commands. These messages appear authentic, mimicking software errors or update prompts. For instance, users might see instructions to “fix” a problem by copying and pasting provided commands, either directly into PowerShell or the Windows Run dialog box. Unbeknownst to them, this simple action can unleash dangerous malware like AsyncRAT, DarkGate, or Lumma Stealer.
Proofpoint highlights, “The ClickFix technique is used by multiple different threat actors and can originate via compromised websites, documents, HTML attachments, malicious URLs, etc.”
The versatility of ClickFix lies in its ability to masquerade as legitimate operations across various industries and platforms. Recent campaigns include:
- Fake CAPTCHA Verification: In campaigns targeting Ukrainian government entities, ClickFix disguised itself as a CAPTCHA check. Users were tricked into running PowerShell commands under the guise of verifying their humanity. Proofpoint linked this to Russian espionage actors, noting that the open-source reCAPTCHA Phish toolkit on GitHub was instrumental in these attacks.
- Impersonating Trusted Platforms: A mid-October campaign targeted GitHub users with fake security vulnerability notifications. The malicious emails directed victims to counterfeit GitHub sites that used ClickFix to deliver Lumma Stealer.
- Language-Specific Attacks: A German-language campaign targeted Swiss organizations using ClickFix lures disguised as updates from Ricardo, a popular e-commerce platform. Victims were led to a landing page that executed JavaScript to download malware, likely AsyncRAT or PureLog Stealer.
ClickFix attackers continuously refine their methods to evade detection. In September 2024, Proofpoint observed ClickFix campaigns using HTML attachments that reversed strings in the webpage source code, complicating analyst reviews. Additionally, the inclusion of ChatGPT-themed malvertising campaigns exemplifies the adaptability of ClickFix, exploiting popular trends to entice victims.
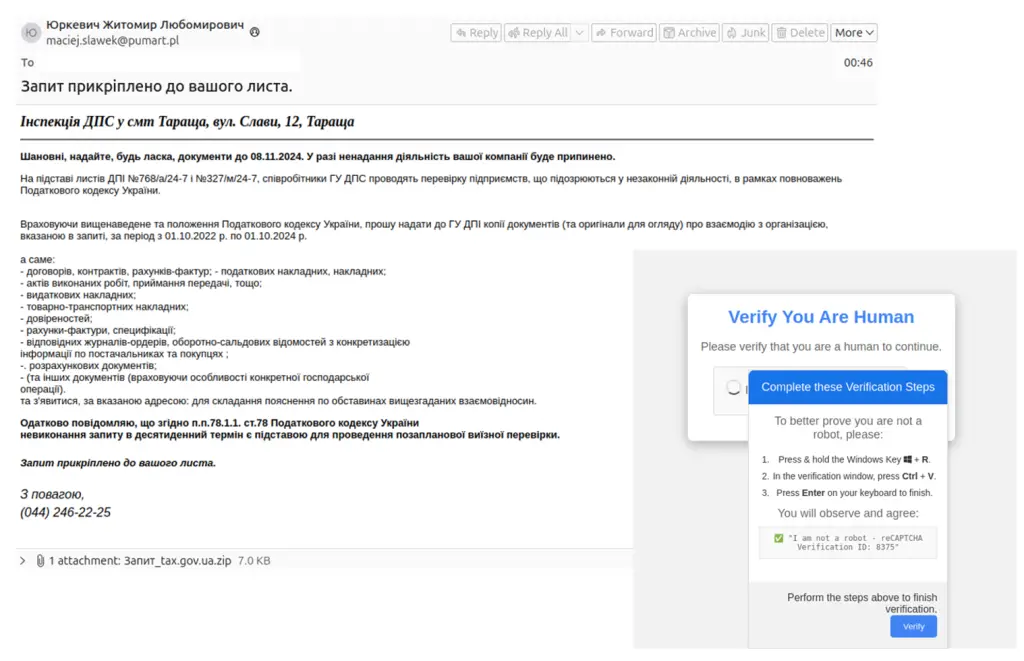
Proofpoint’s visibility indicates that ClickFix campaigns have impacted over 300 organizations worldwide. While many operations appear financially motivated, others hint at espionage objectives, such as those linked to UAC-0050 targeting Ukraine.
Despite its wide adoption, ClickFix is not consistently attributed to a single threat actor or group. Proofpoint notes, “Most observed ClickFix campaigns are not attributed to a known threat actor or group.”
Related Posts:
- Beware of Fake Google Meet Invites: ClickFix Campaign Spreading Infostealers
- ClearFake Campaign Employs Novel Social Engineering Tactic to Deliver LummaC2 Infostealer
- TA571 and ClearFake Use Social Engineering to Deliver PowerShell Malware
- Hacker exploits Google App script to spread malware
- Hackers Exploit YouTube for Game Cracks, Steal Your Data