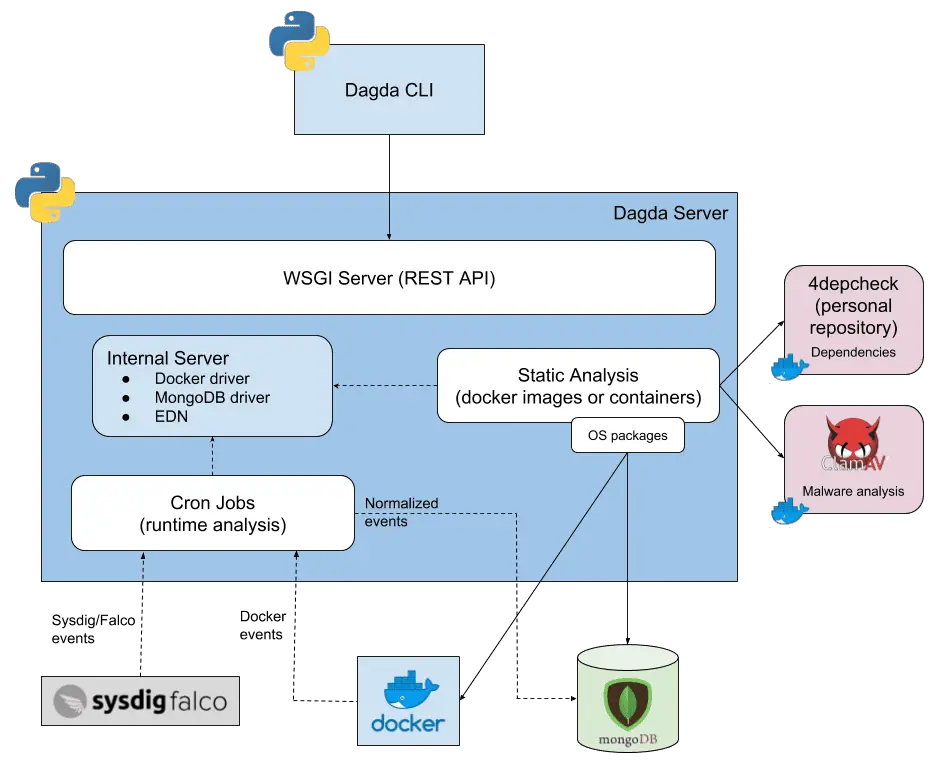
Dagda is a tool to perform static analysis of known vulnerabilities, trojans, viruses, malware & other malicious threats in docker images/containers and to monitor the docker daemon and running Docker containers for detecting anomalous activities.
In order to fulfill its mission, first the known vulnerabilities as CVEs (Common Vulnerabilities and Exposures), BIDs (Bugtraq IDs), RHSAs (Red Hat Security Advisories), and RHBAs (Red Hat Bug Advisories), and the known exploits from the Offensive Security database are imported into a MongoDB to facilitate the search of these vulnerabilities and exploits when your analysis is in progress.
Then, when you run a static analysis of known vulnerabilities, Dagda retrieves information about the software installed into your docker images, such as the OS packages and the dependencies of the programming languages, and verifies for each product and its version if it is free of vulnerabilities against the previously stored information into the MongoDB. Also, Dagdauses ClamAV as an antivirus engine for detecting Trojans, viruses, malware & other malicious threats included within the docker images/containers.
Dagda supports multiple Linux base images:
- Red Hat/CentOS/Fedora
- Debian/Ubuntu
- OpenSUSE
- Alpine
Dagda rests on OWASP dependency check + Retire.js for analyzing multiple dependencies from:
- java
- python
- nodejs
- js
- ruby
- php
On the other hand, Dagda is integrated with Sysdig Falco for monitoring running Docker containers to detect anomalous activities. Also, Dagda includes the gathering of real-time events from the docker daemon.
Finally, each analysis report of a docker image/container, including all static analysis and all runtime monitoring, is stored into the same MongoDB for having available the history of each docker image/container when it is needed.
Copyright 2018 Elías Grande Rubio