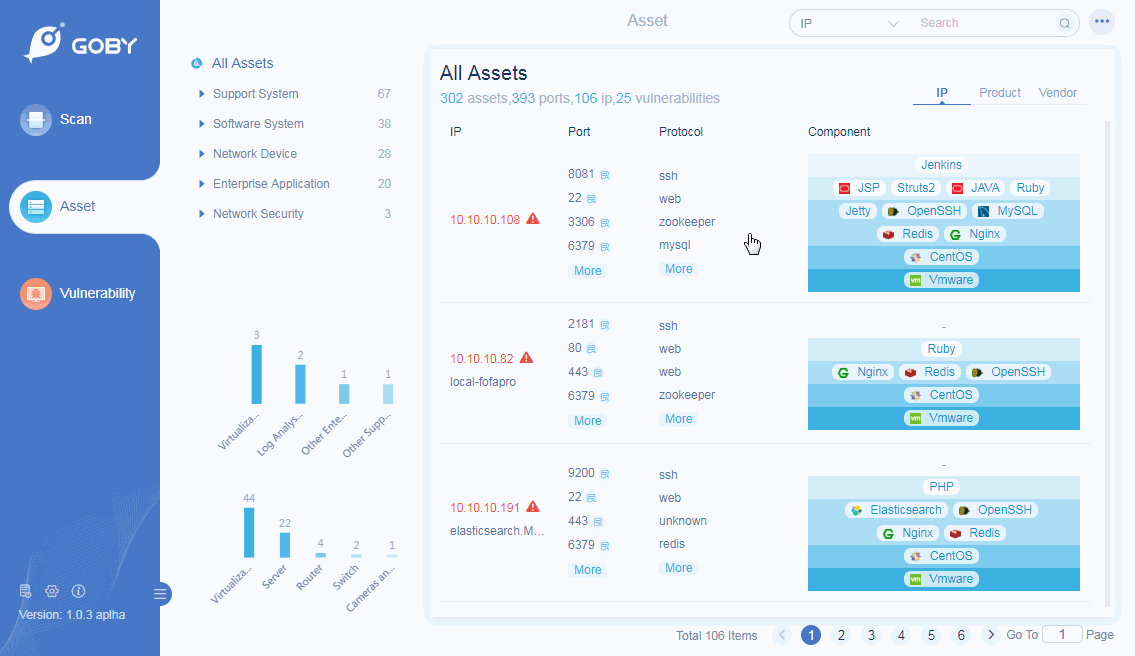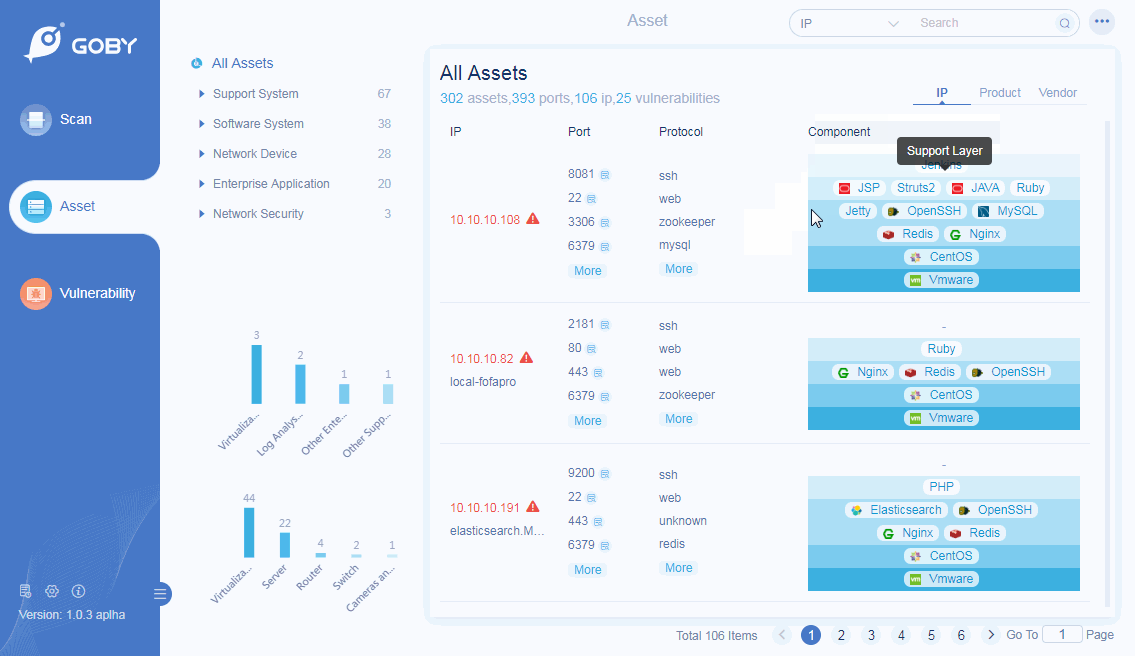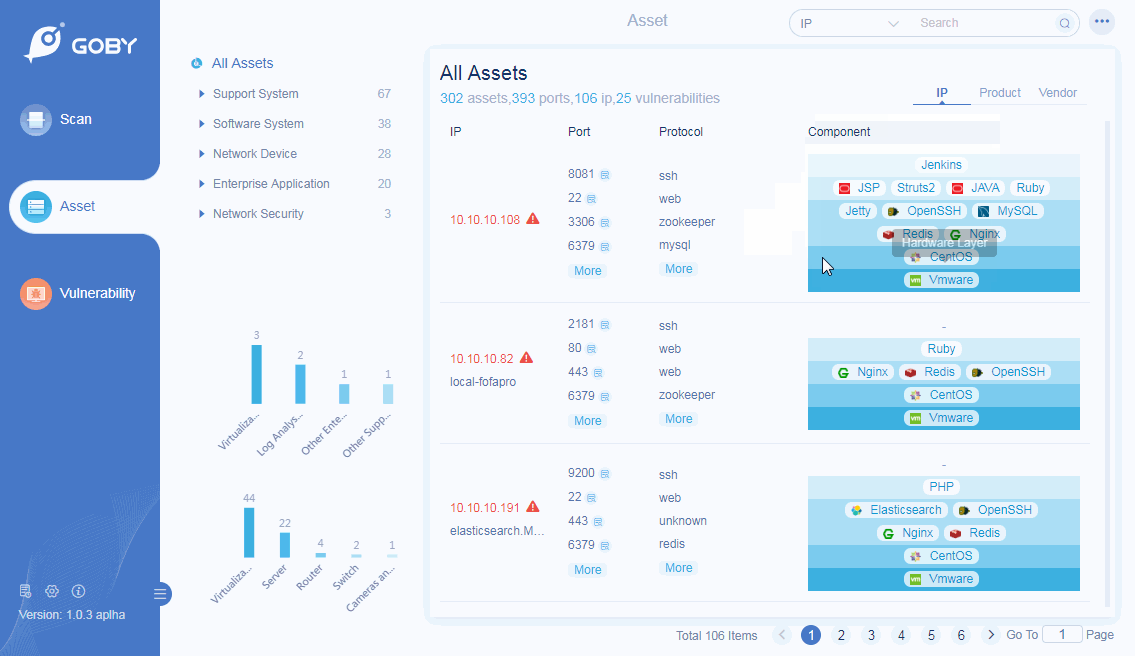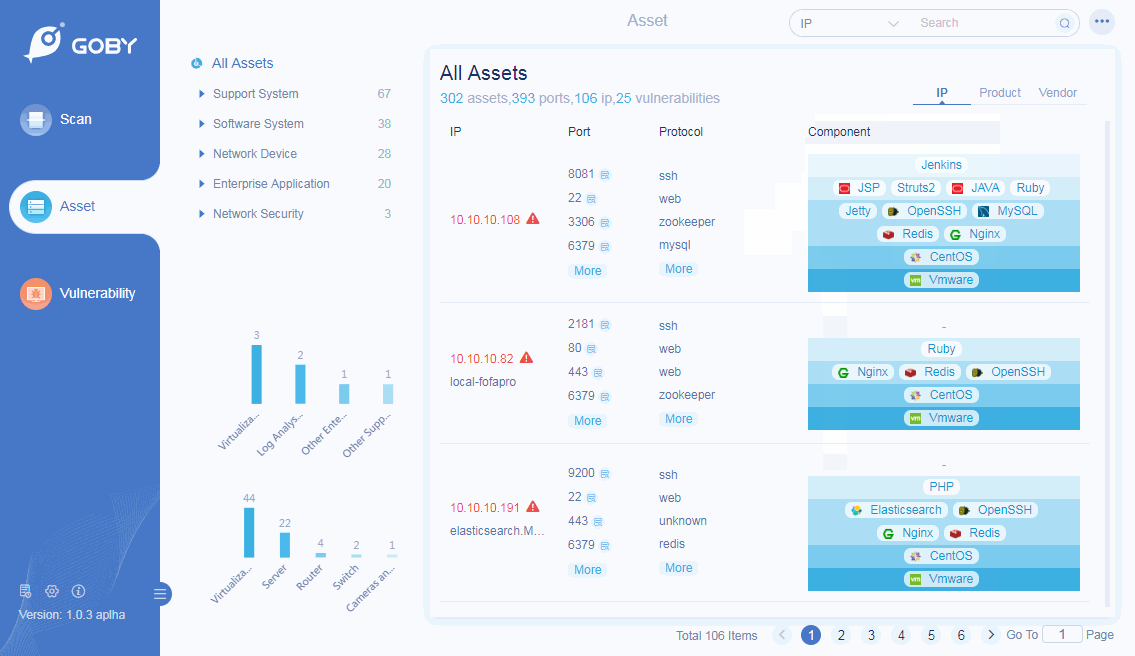
Scan
Asset Scanning
Automatically detect the existing IP in current cyberspace;

Port Scanning
Cover nearly 300 mainstream ports and support port grouping for different scenarios to ensure the most efficient outputs ;
Protocol Identification
Preset more than 200 protocol identification engines, covering network protocol, database protocol, IoT protocol, ICS protocol, etc., which could analyze protocol information corresponding to the port quickly through the very light transmission.
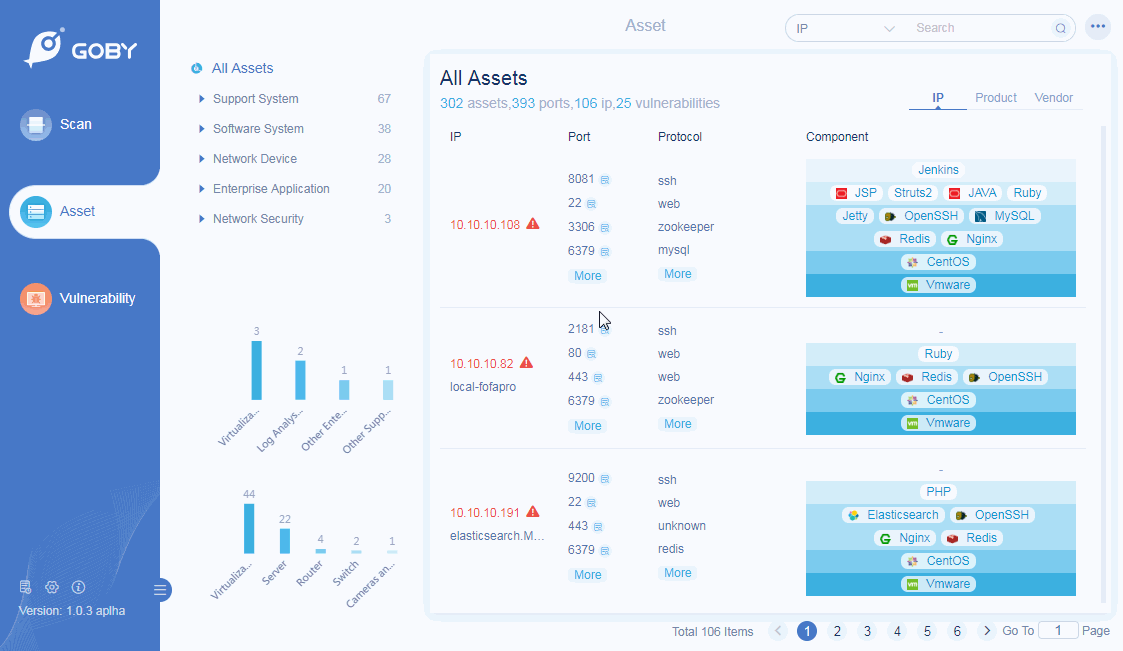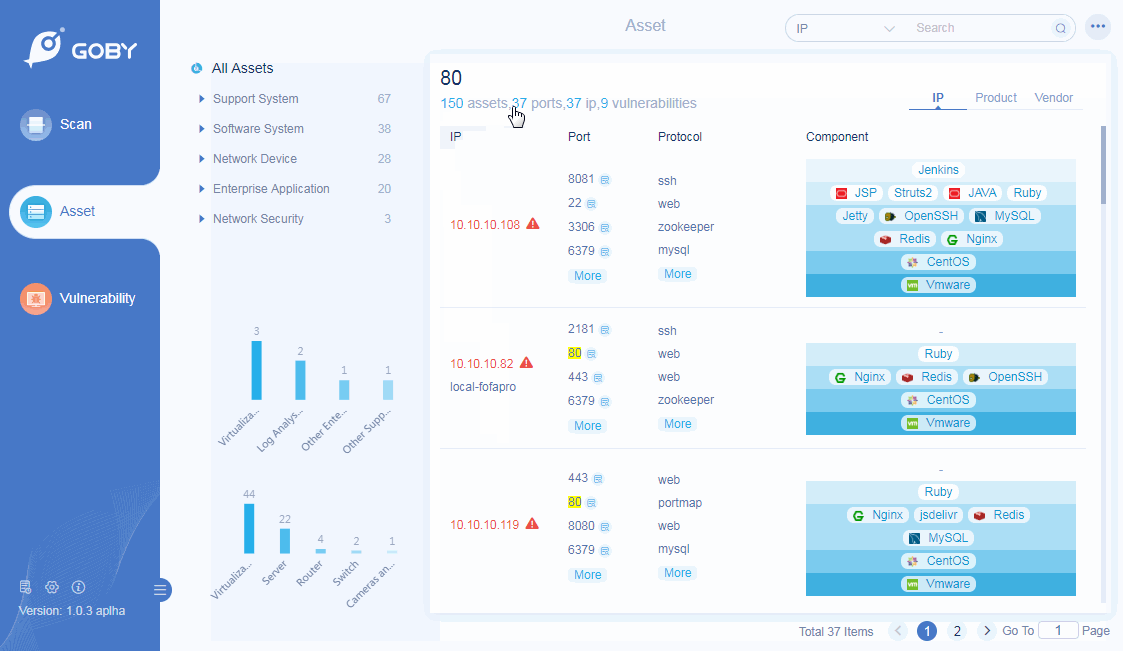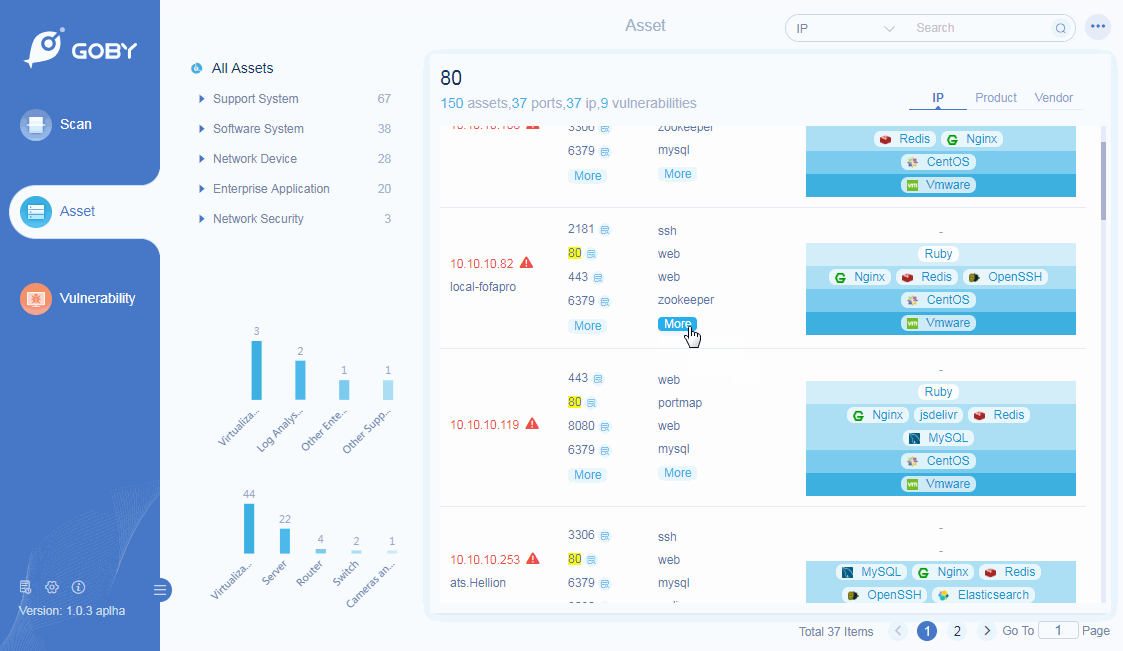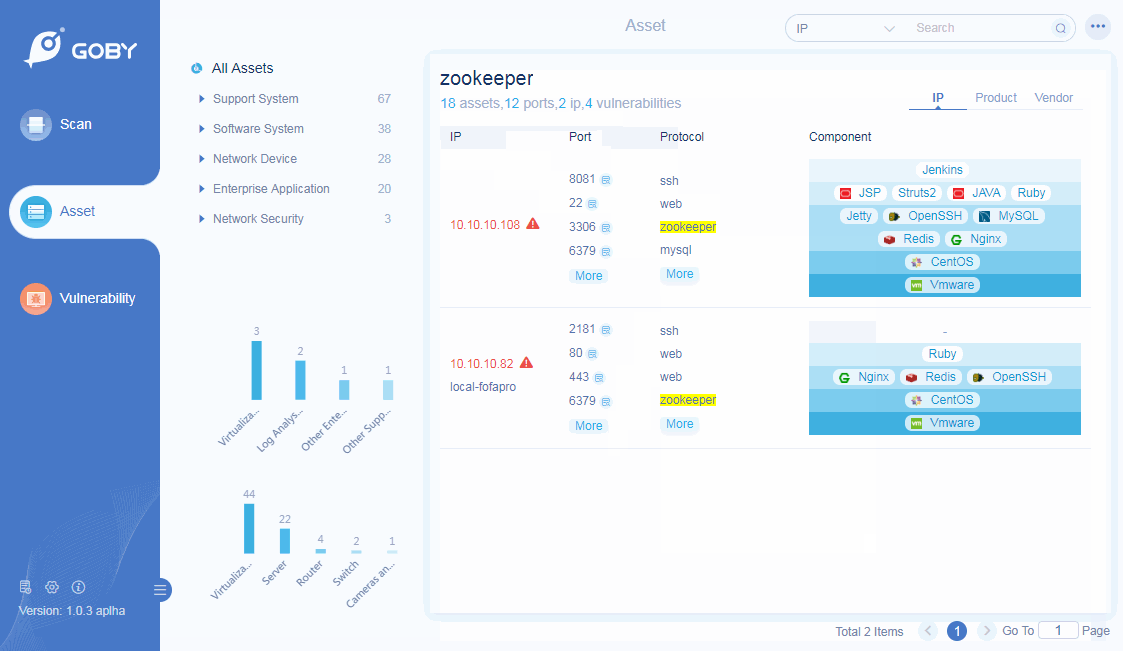
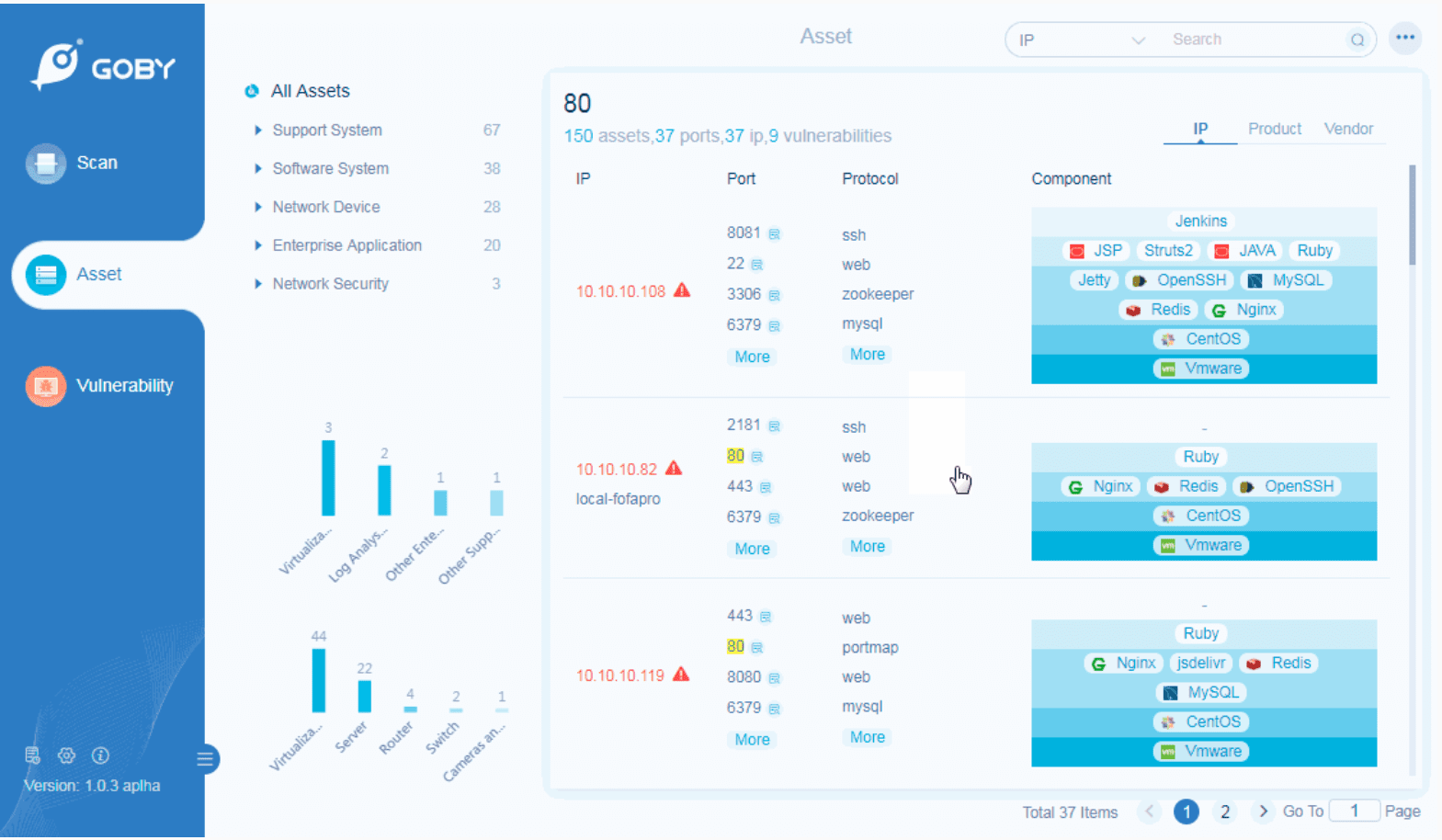
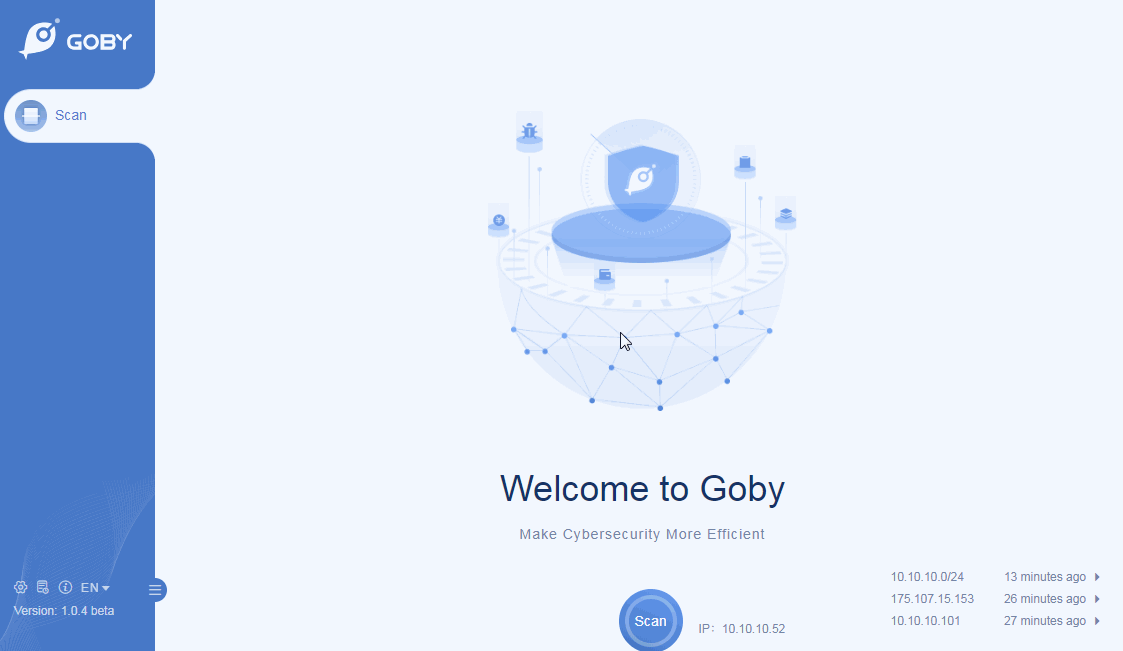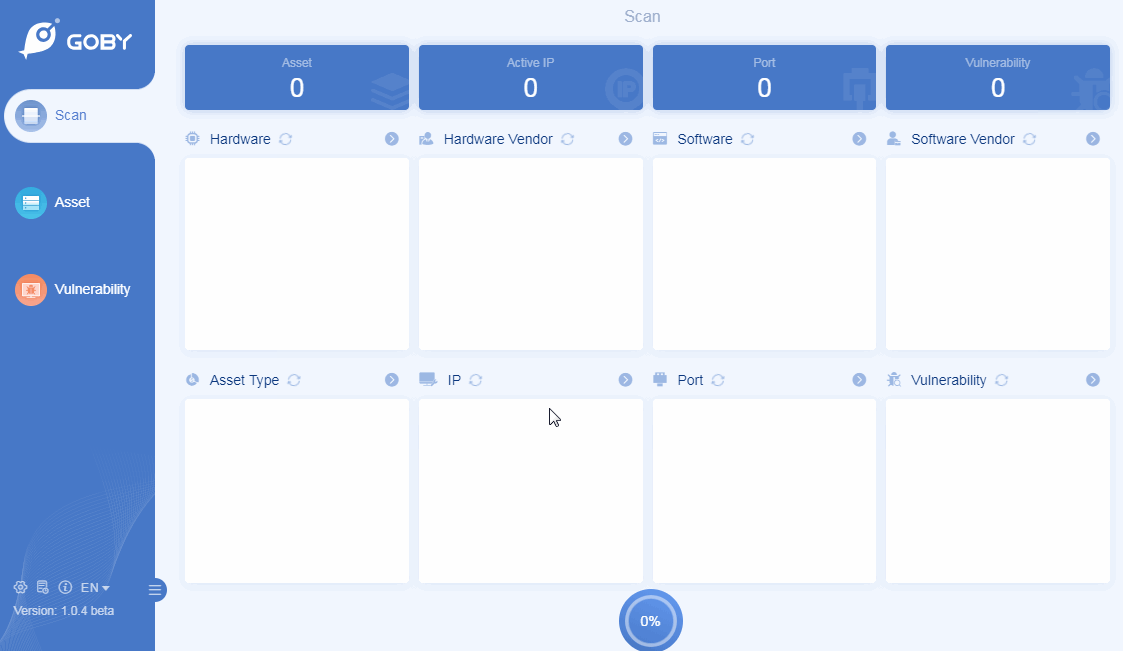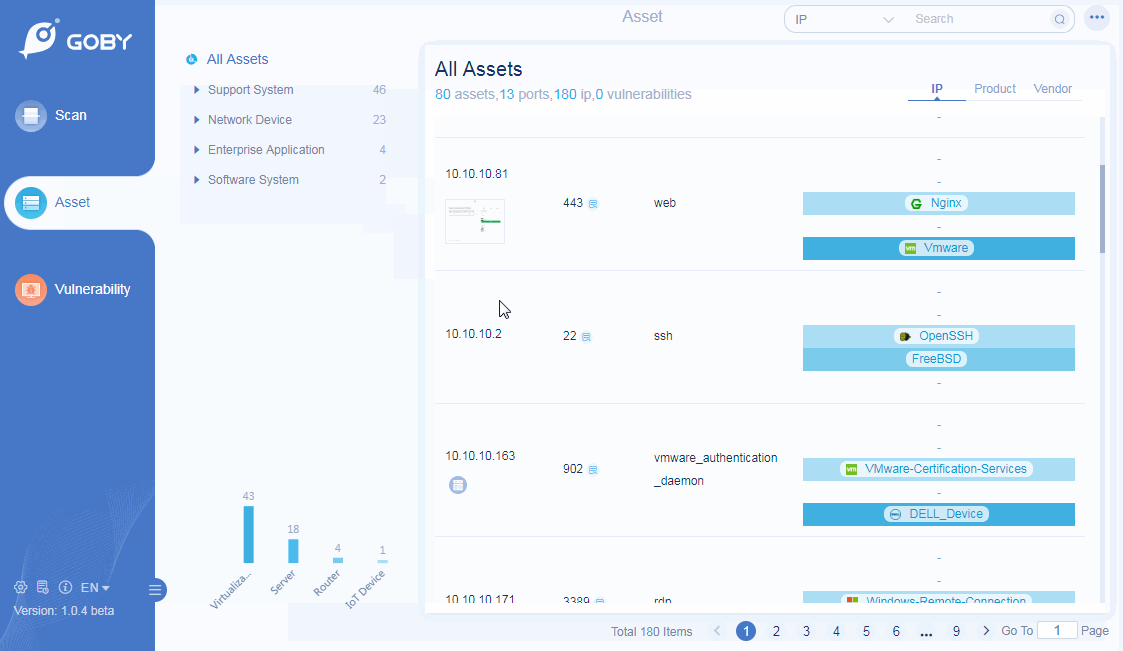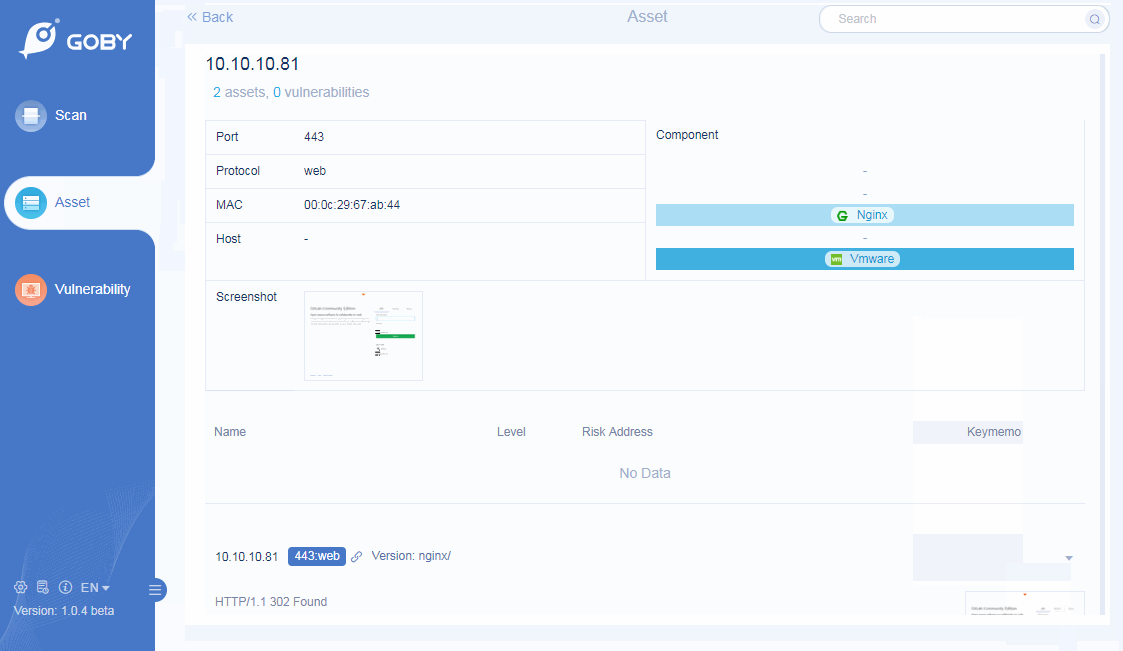
Product Identification
Preset more than 100,000 rule identification engines to automatically identify and classify hardware equipment and software business systems, and comprehensively analyze the business systems that exist in the network.
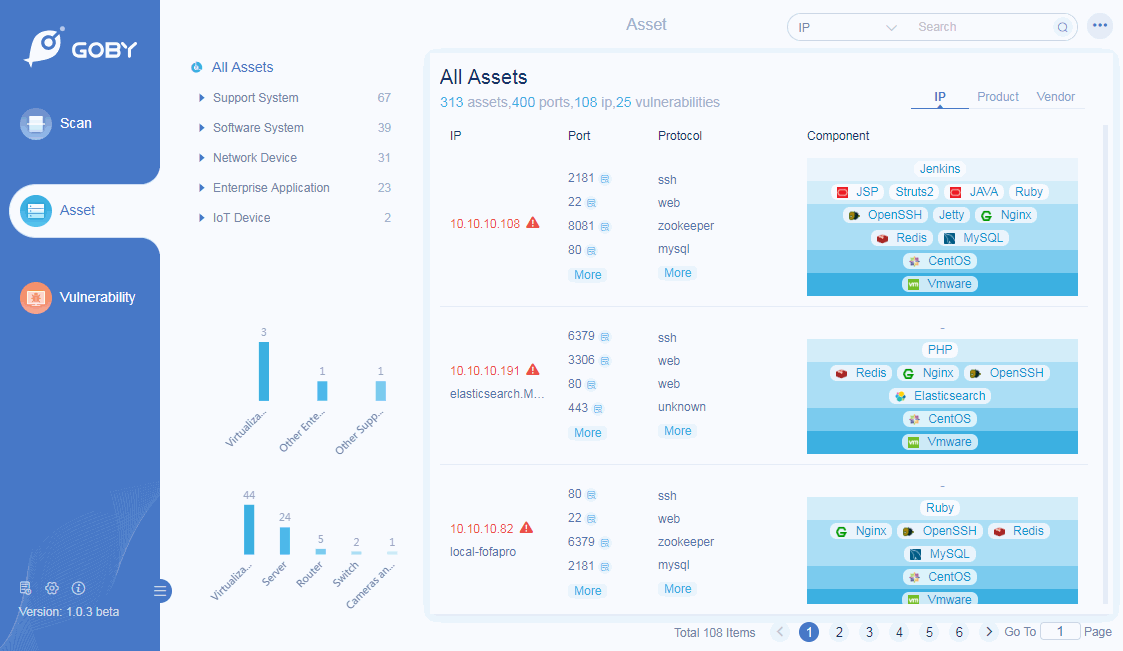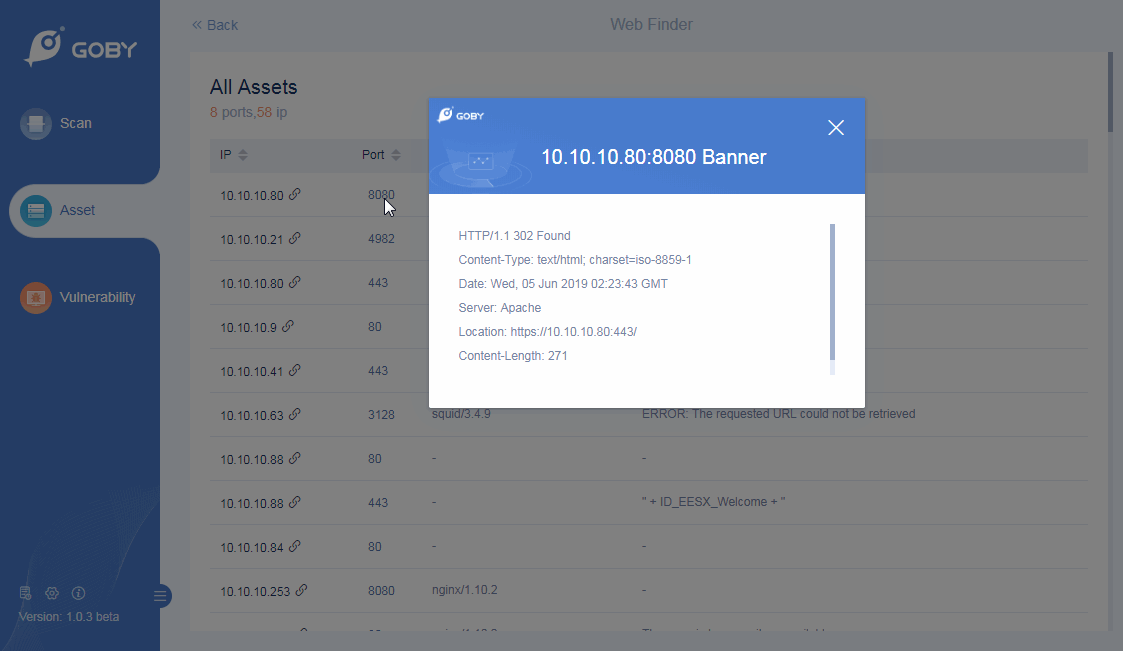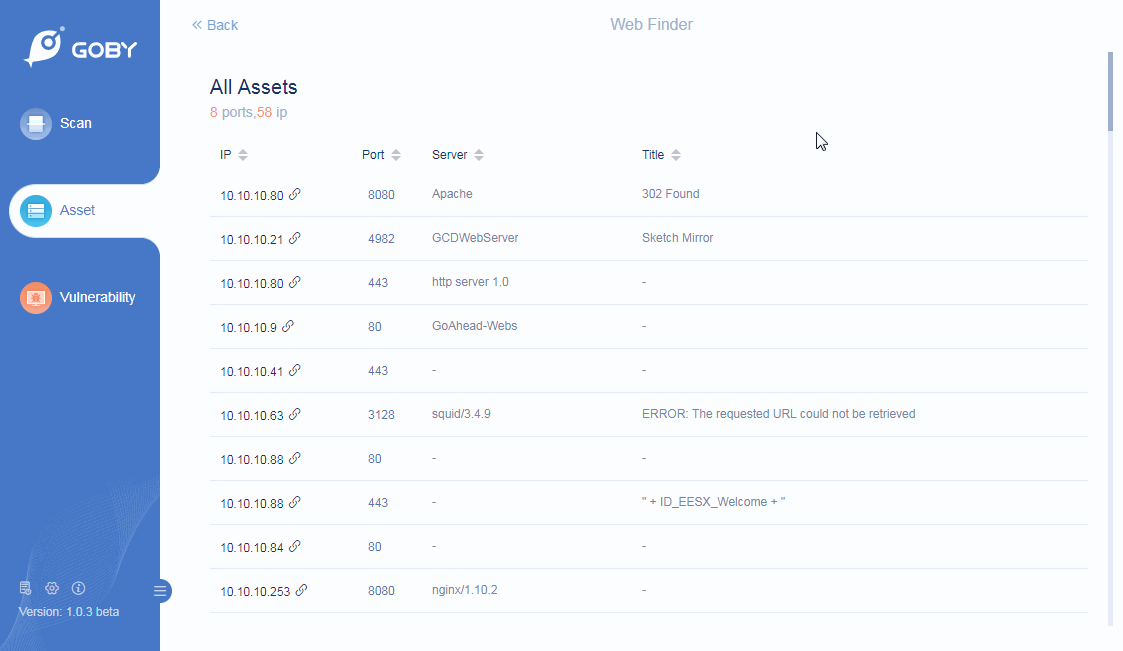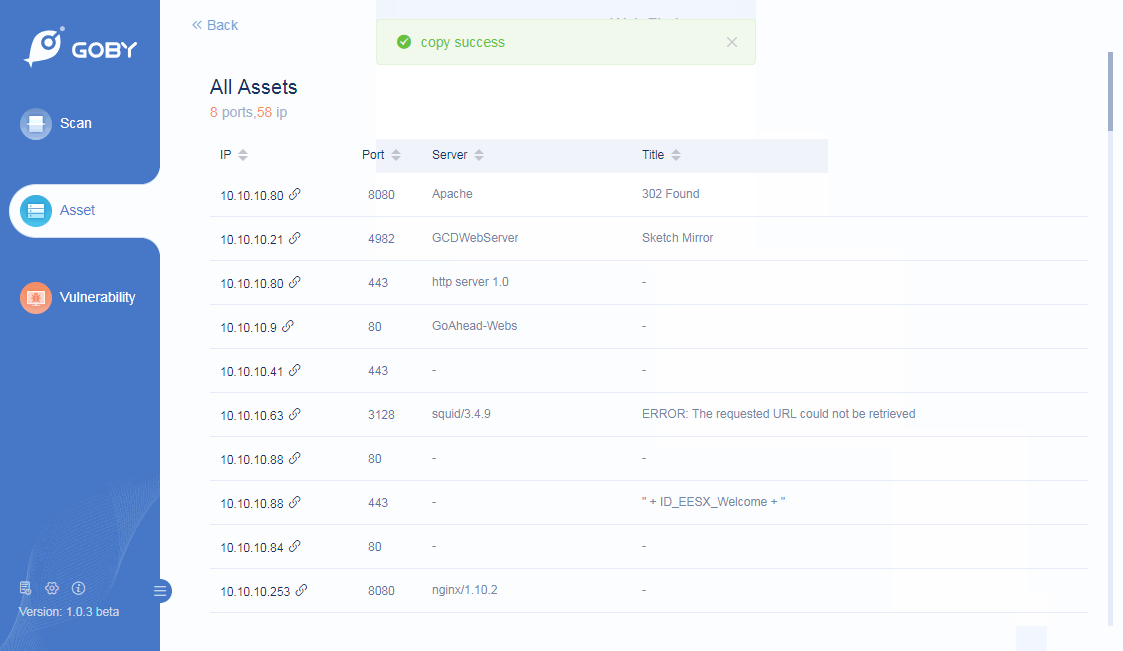
Web Finder
Support important information needed for website penetration: including IP, port, server, title, etc:
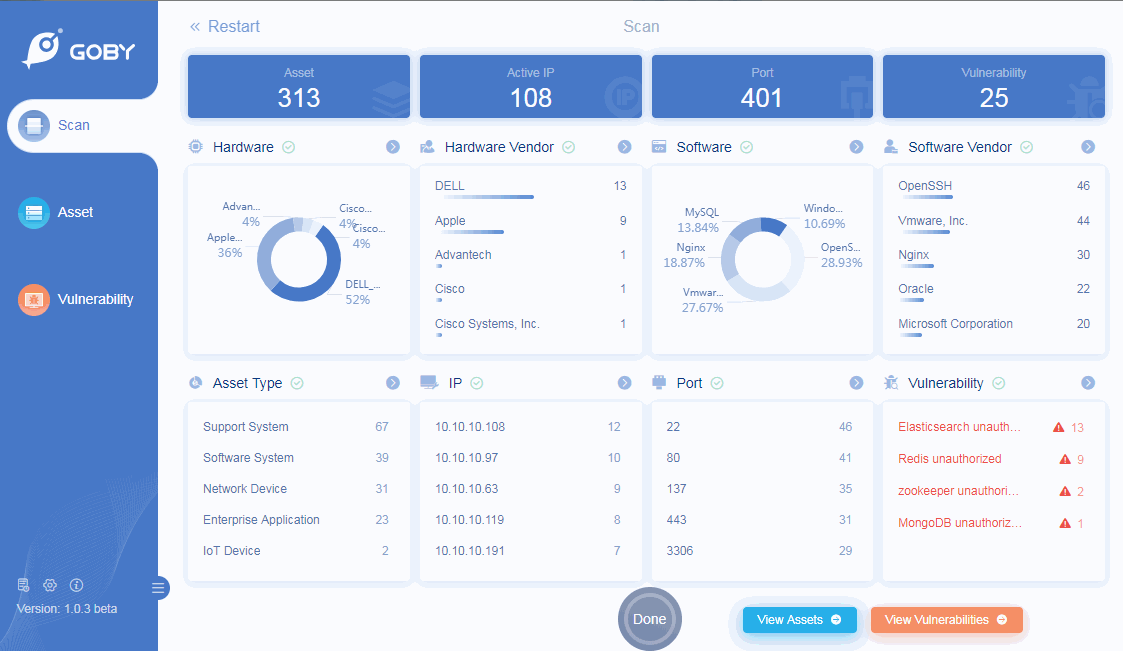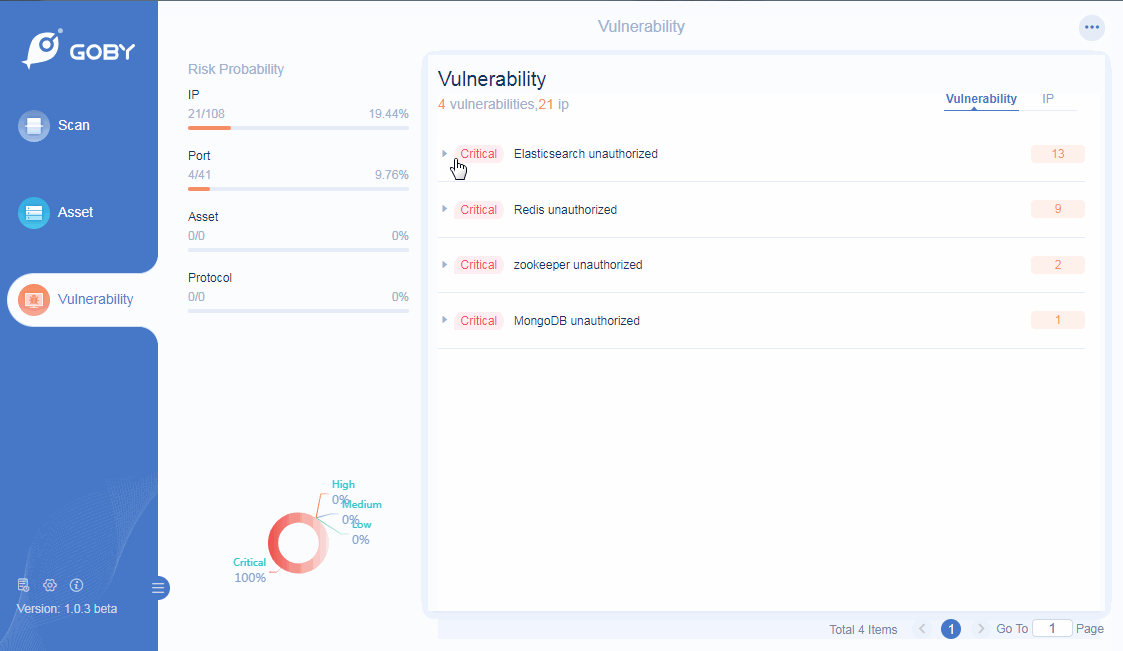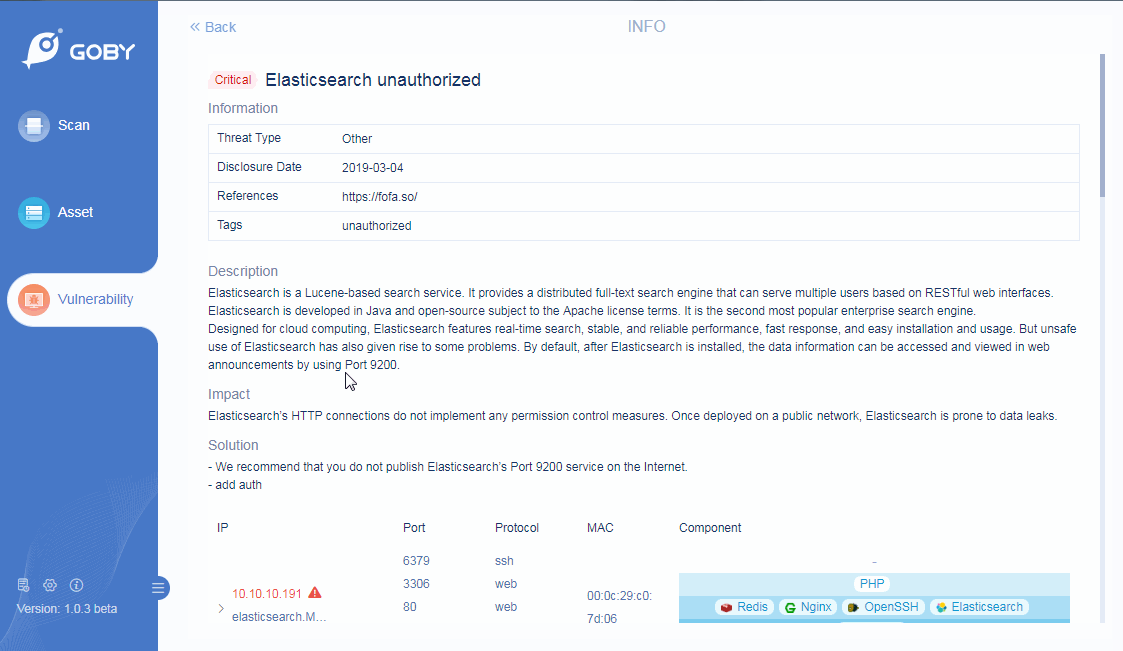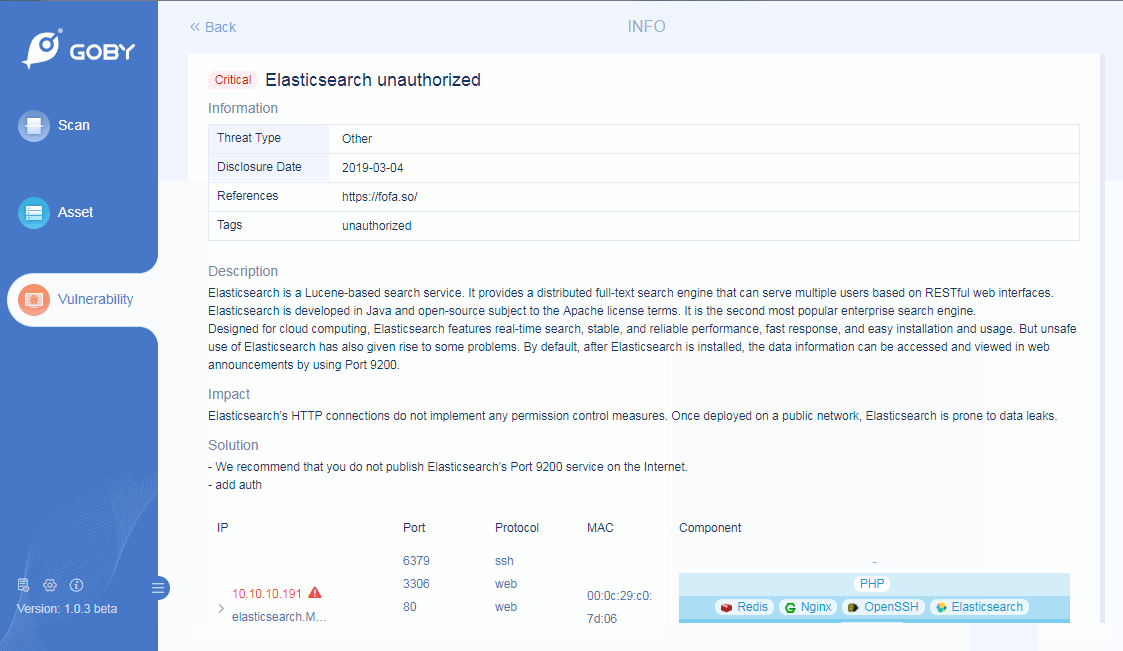
Vulnerability Scanning
Preset the most attacking vulnerability engines, covering the most serious vulnerabilities such as Weblogic and Tomcat.
Website Screenshot
Website screenshots on the server can be obtained and more screenshots can be seen on the detail page.
Domain scanning
Support root domain and subdomain scanning, and support automatic crawling of subdomains.
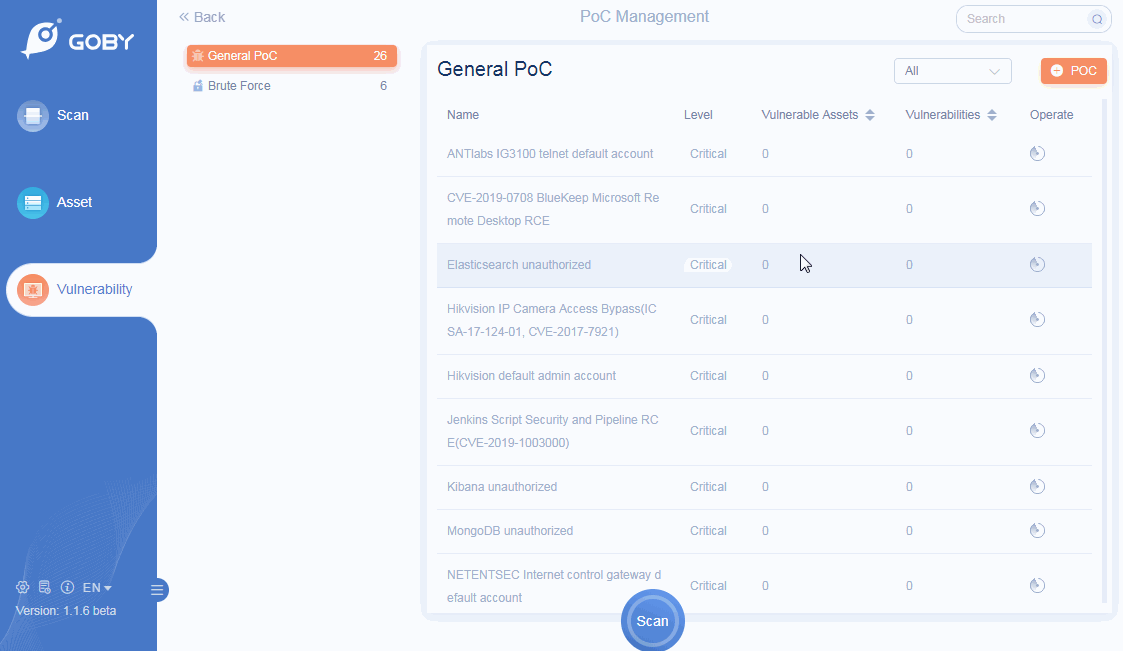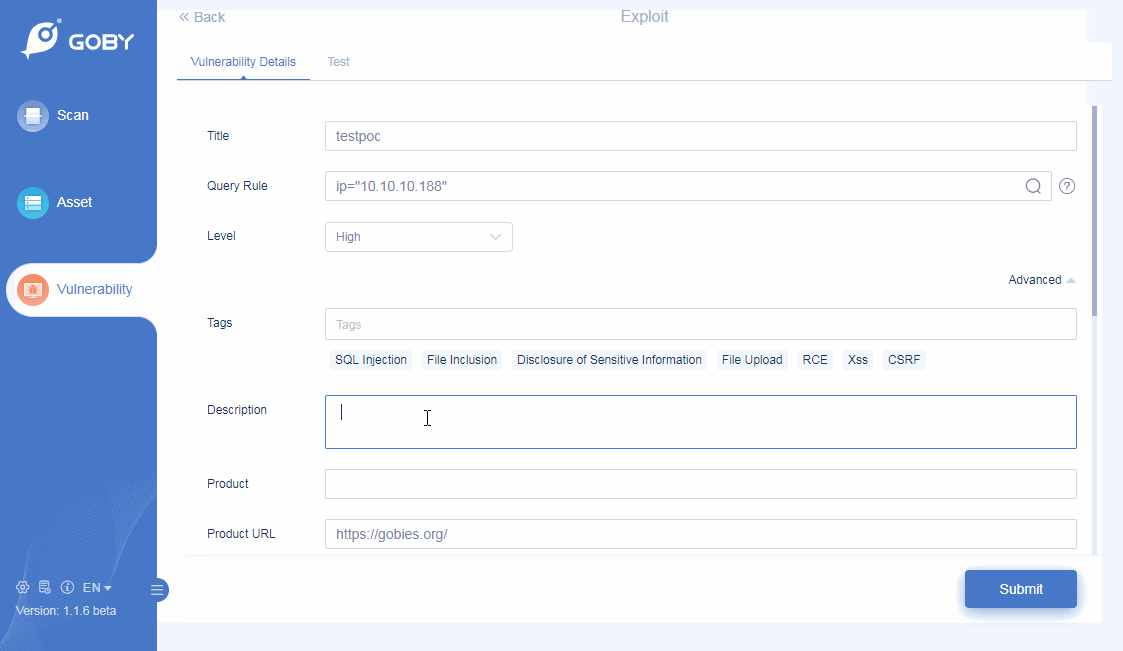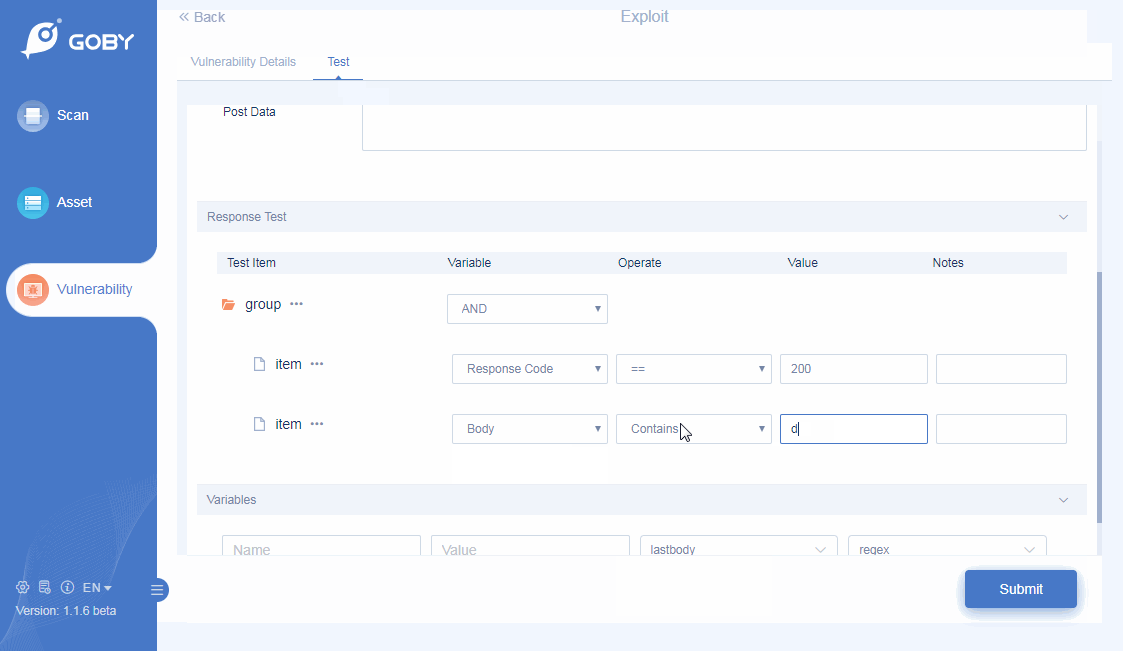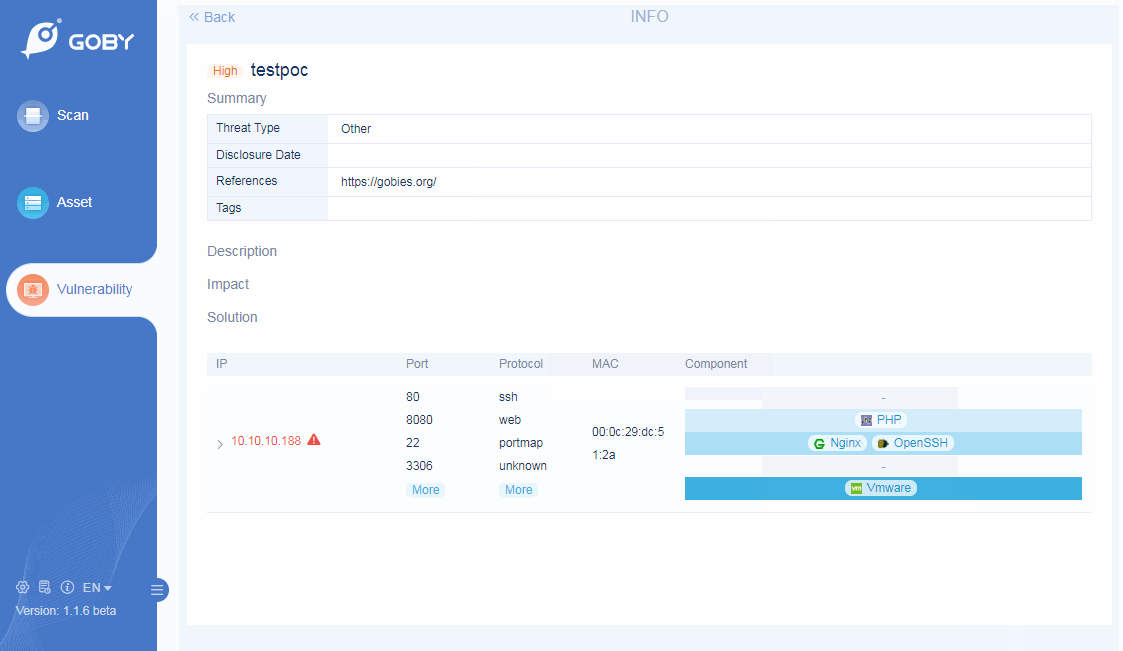
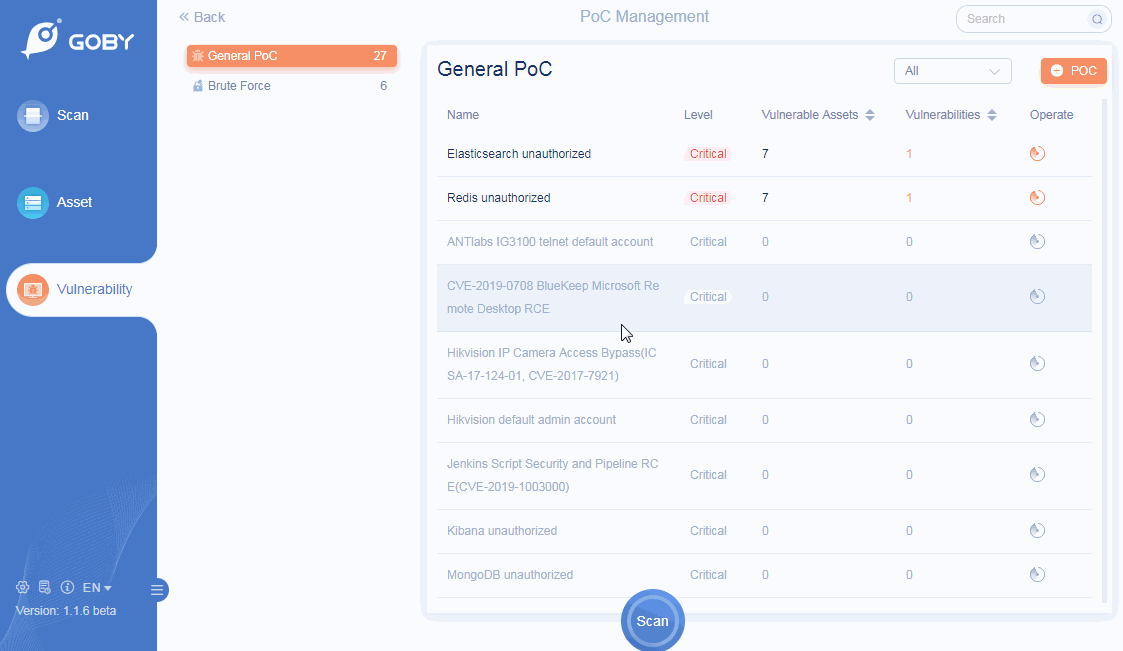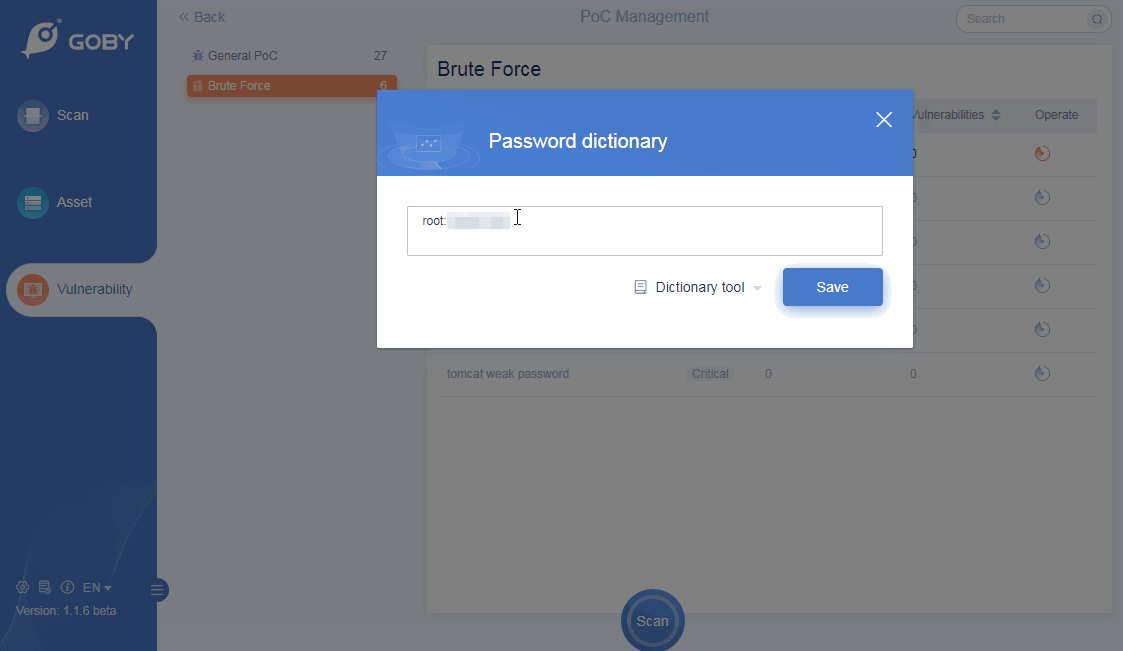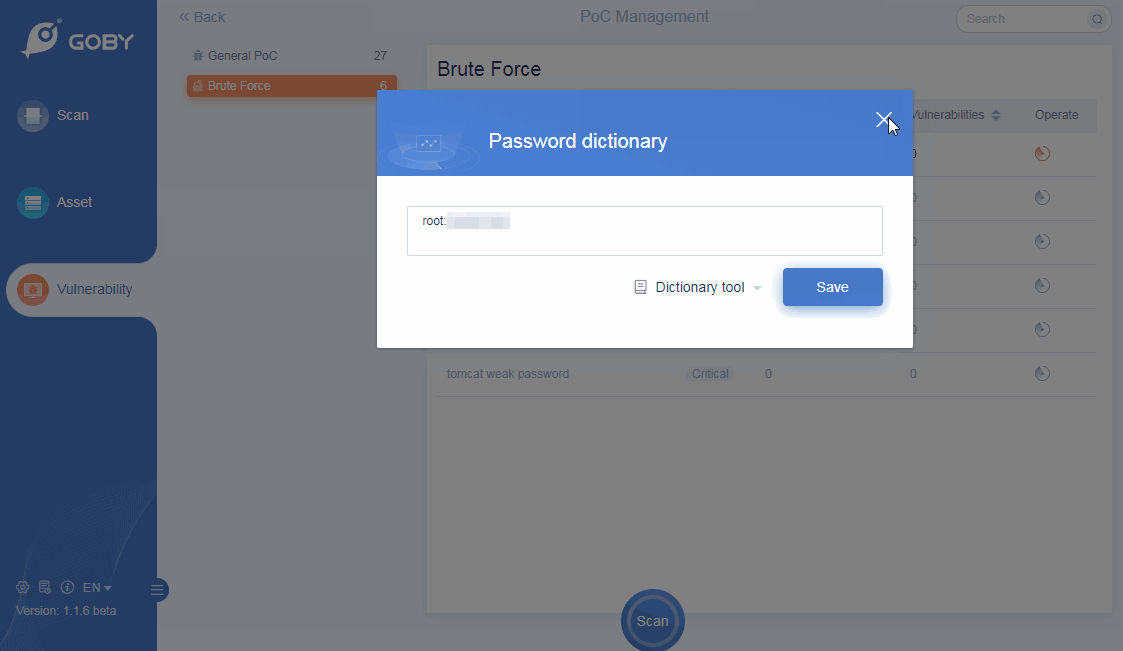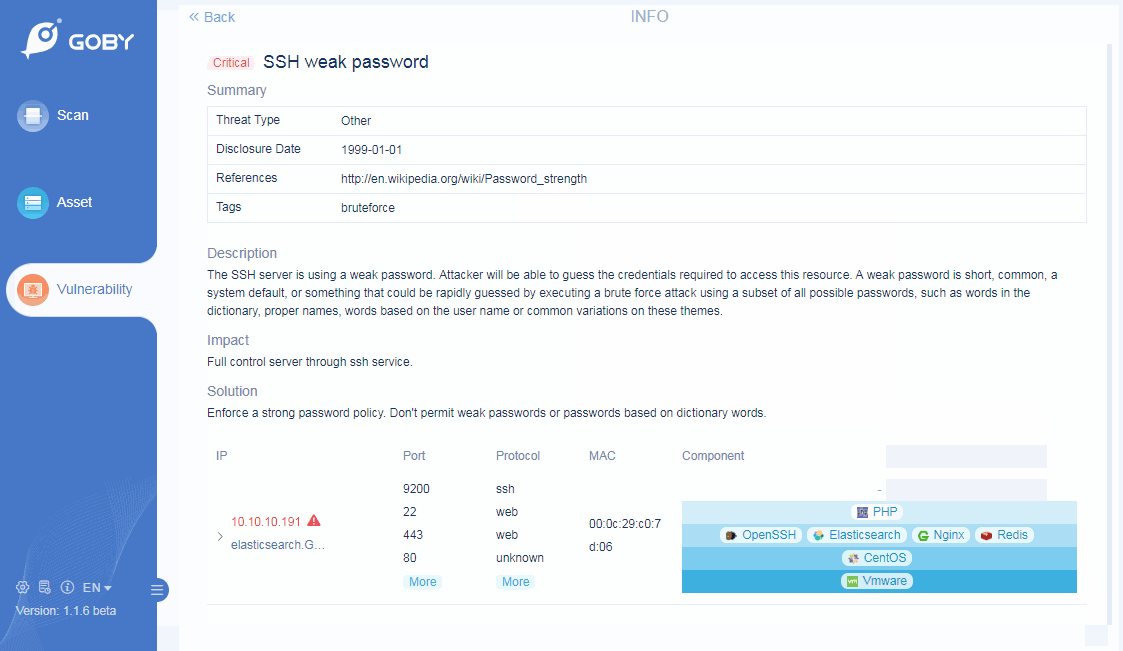
Vulnerability
Custom PoC
Vulnerability scanning is more flexible;
Custom Dictionary
A brute-force attack is easier;
Changelog vBeta2.2
Community version update:
- New memory shell plugin
- ShellHub plugin update
- Vulnerability module added a function to generate deserialization Payload, through the memory shell injection process
- Five Java deserialization vulnerabilities were added, including
- Bonitasoft Platform serverAPI Deserialization Vulnerability
- Liferay Portal Unauthenticated 7.2.1 C3P0 Deserialization Vulnerability (CVE-2020-7961)
- ManageEngine OpManager Deserialization Vulnerability (CVE-2020-28653)
- Zkteco Shiro Deserialization Vulnerability
- ZOHO ManageEngine Password Manager Pro Deserialization Vulnerability
- Fixed the problem that the environment variable http_proxy caused Goby to report errors abnormally
- Goby can now be updated online and vulnerabilities can be updated even if Goby is not in the Mac system Application directory
- Fixed the problem of occasional white horizontal lines in Goby
- remove network error report
Red team/Enterprise version update content
- All update content of 2.2.0 community version
- 20 new deserialization vulnerabilities were added, including
- Apache OFBiz xmlrpc Deserialization Vulnerability (CVE-2020-9496)
- Apereo CAS Before 4.1.7 Deserialization Vulnerability
- Dreamer CMS Shiro Deserialization Vulnerability
- EasyReport Shiro Deserialization Vulnerability
- FEBS Shiro Deserialization Vulnerability
- FH Admin Shiro Deserialization Vulnerability
- FineReport V10 Deserialization RCE Vulnerability
- ForgeRock AM Deserialization Vulnerability (CVE-2021-35464)
- Guns Shiro Deserialization Vulnerability
- J2eeFAST Shiro Deserialization Vulnerability
- JavaWeb_Layui Shiro Deserialization Vulnerability
- Liferay Portal 6.1.1 CE GA2 CB Deserialization Vulnerability
- MCMS Shiro Deserialization Vulnerability (CVE-2022-22928)
- OneBlog Shiro Deserialization Vulnerability
- pb-cms Shiro Deserialization Vulnerability
- QVIS-NVR Camera Management System RCE (CVE-2021-41419)
- RuoYi-plus Shiro Deserialization Vulnerability
- TIMO Shiro Deserialization Vulnerability
- Ysk ERP Shiro Deserialization Vulnerability