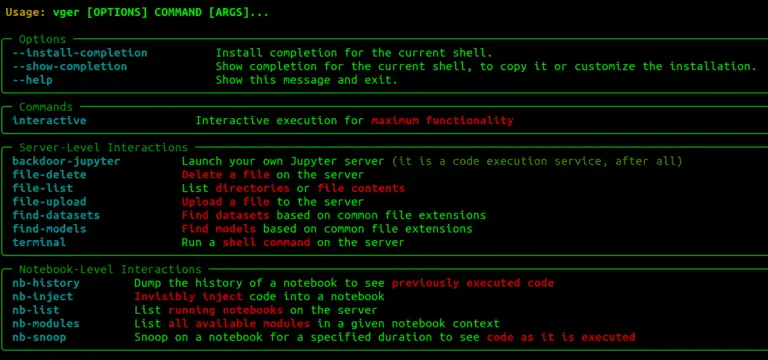
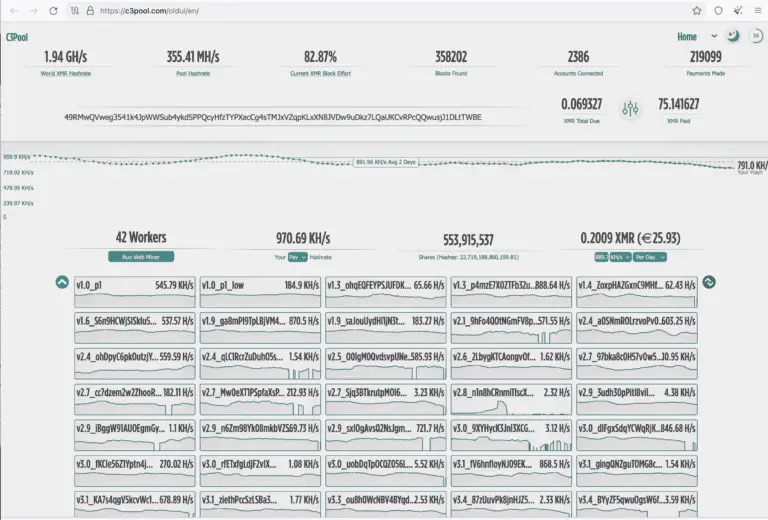
V’ger V’ger is an interactive command-line application for post-exploitation of authenticated Jupyter instances with a focus on...
The United States has formally denounced a series of cyberattacks orchestrated by Russia’s General Staff Main Intelligence...
Hackers are actively exploiting a vulnerability in the LiteSpeed Cache Plugin for WordPress, a tool currently installed...
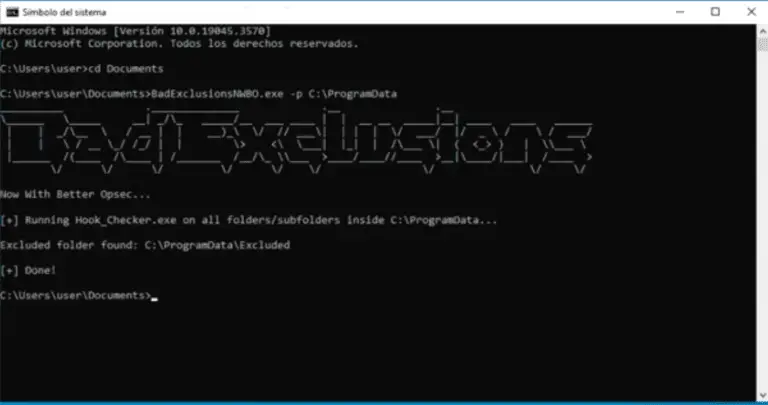
BadExclusions Now With Better Opsec BadExclusionsNWBO is an evolution from BadExclusions to identify folder custom or undocumented...
Nvidia has released a security advisory addressing critical vulnerabilities in its Triton Inference Server, a widely-used platform...
A significant security vulnerability has been identified in WordPress, the world’s most popular content management system, which...
Microsoft’s Senior Security Researcher Vladimir Tokarev will detail a series of critical zero-day vulnerabilities in OpenVPN, the...
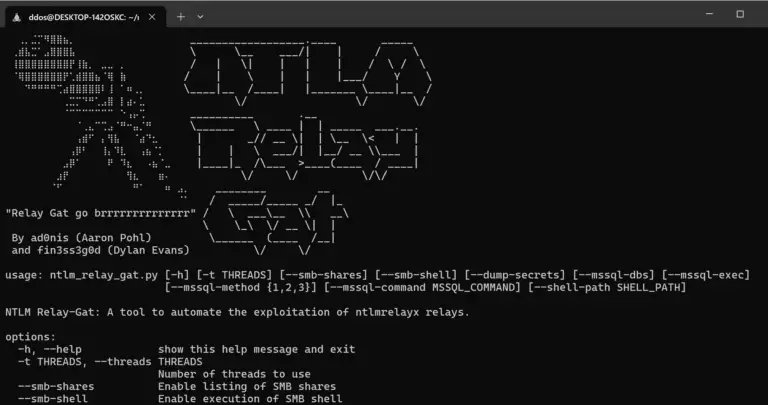
NTLM Relay Gat NTLM Relay Gat is a powerful tool designed to automate the exploitation of NTLM...
A severe security flaw has been identified in aiohttp, the widely used open-source library that enables asynchronous...
A new report by TrendMicro lifts the veil on the shadowy world of router exploitation. Those unassuming...
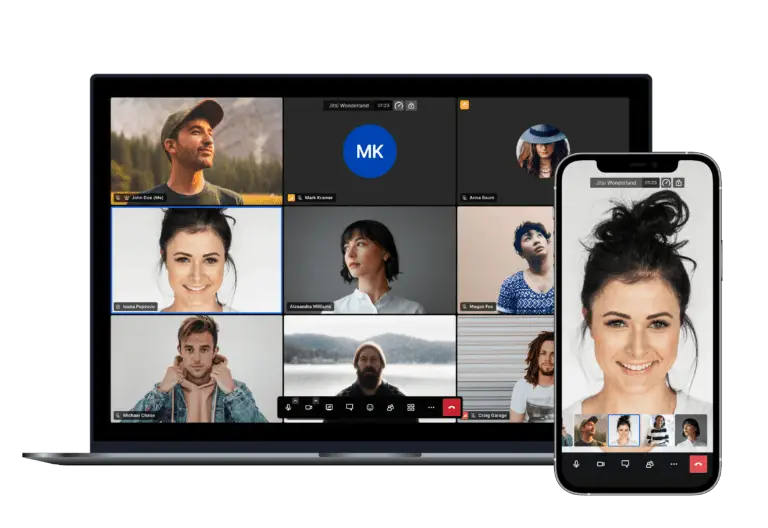
Security researcher Florian Port at Insinuator recently uncovered a critical flaw in Jitsi Meet, the popular open-source...
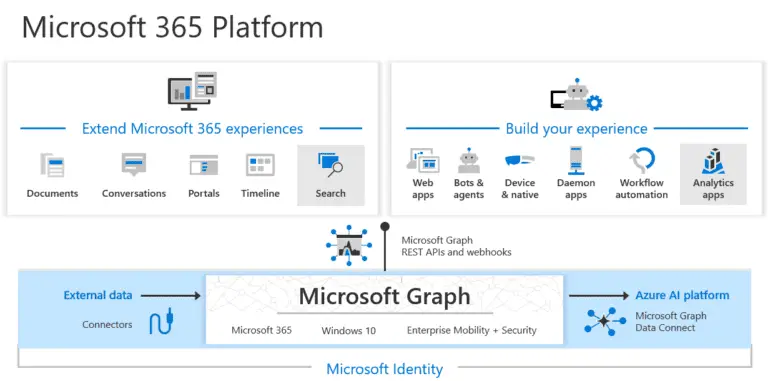
A new trend is gaining momentum among cybercriminals—utilizing Microsoft’s Graph API for sinister purposes. This trend highlights...
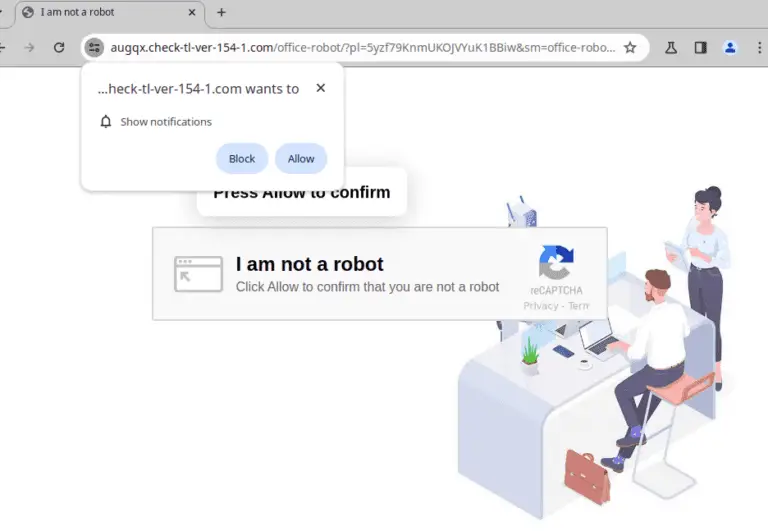
Beware of that seemingly harmless “Verify that you are a human” pop-up window the next time you...
Apache ActiveMQ, widely regarded as the most popular open-source, multi-protocol, Java-based message broker, facilitates communication across a...
Cisco has issued a security advisory highlighting multiple vulnerabilities in the firmware of several IP Phone models...