
A new report by threat intelligence platform Hunt.io has revealed a stealthy and persistent phishing campaign that leverages server-side logic to evade detection and steal credentials from employee and member login portals. The investigation showcases how adversaries are adapting phishing kits to sidestep detection mechanisms—shifting the balance of power in credential-based attacks.
“Credential theft through phishing continues to be one of the most reliable paths into enterprise environments,” the report begins, citing the importance of stolen usernames and passwords for initial access, lateral movement, and account abuse before defenders are even aware of a breach.
Hunt.io analysts uncovered a widespread campaign using a PHP-based phishing kit, originally noted in a Malwarebytes blog post that analyzed a Google Ads malvertising campaign targeting Lowe’s employees. Early variants of the kit relied on client-side redirects to validate stolen credentials. However, recent versions have moved this logic to the server side, making analysis significantly harder.
“By eliminating client-side validation and relocating the decision logic to the server, the actors obscure key detection points defenders previously relied on,” Hunt.io notes.
A more sophisticated variant discovered on hignmarkedmemb[.]com mimics Highmark’s enterprise login system, complete with 2FA prompts. Using JavaScript logic and the function getUpdates2fa(), the page simulates a two-factor authentication experience.
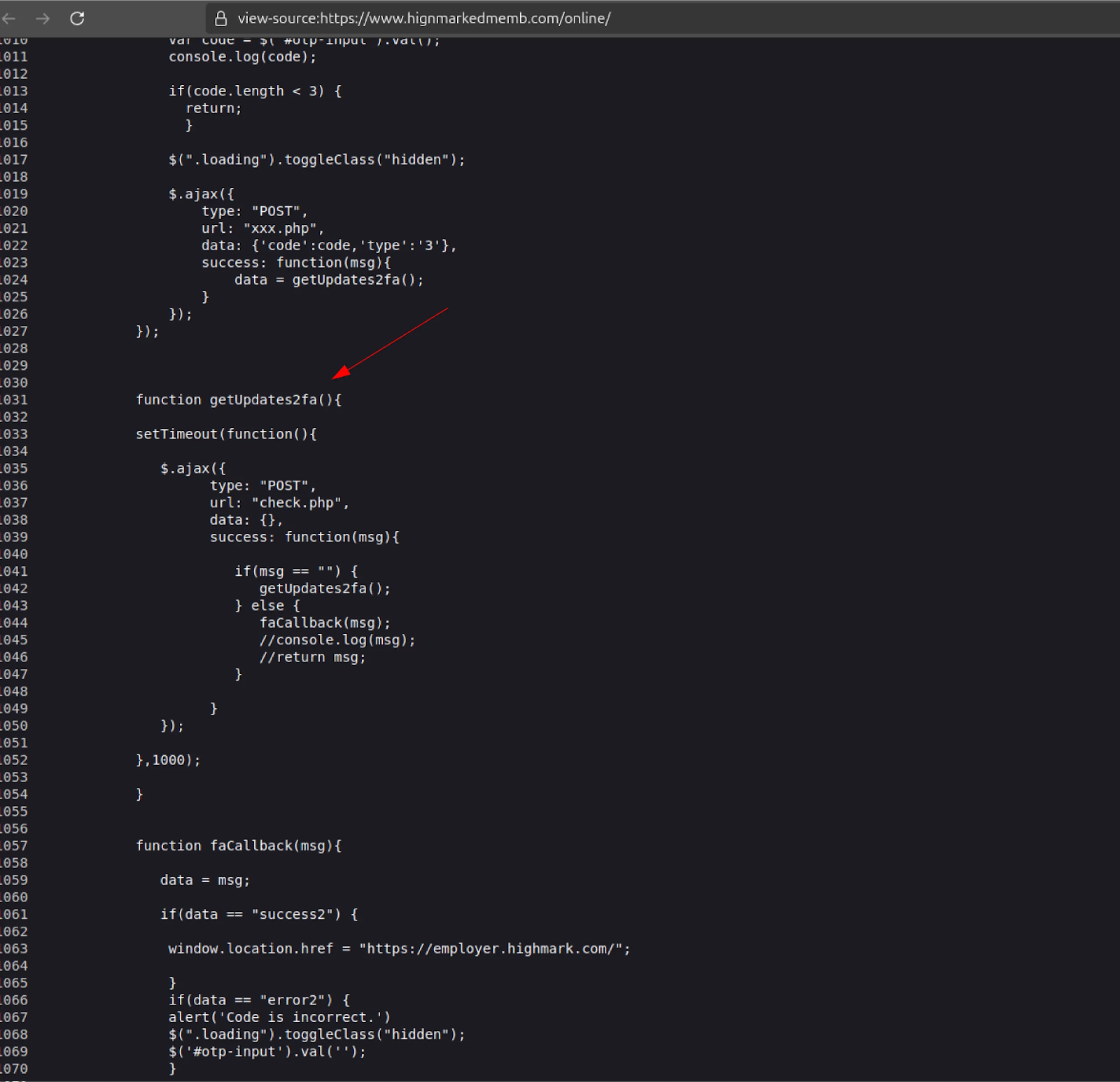
“This version reintroduces the redirect behavior seen in earlier kits but only after a valid OTP is submitted, mimicking typical SSO workflows to avoid suspicion,” the researchers explained.
The phishing kit separates credential and OTP submission via different POST requests—identified by type=3—and only redirects users after receiving a “success2” status from the backend. These enhancements demonstrate a clear intent to bypass MFA-protected environments and prolong persistence.
Hunt.io’s investigation also uncovers the infrastructure used to host these phishing campaigns, tracing it back to specific IP addresses and Autonomous System Numbers (ASNs). The report identifies Chang Way Technologies Co. Limited (AS57523) as the ASN hosting malicious infrastructure and having previous links to malware distribution and other cyberattacks.
“These updates show a deliberate attempt to bypass environments protected by two-factor authentication,” the report concludes, urging defenders to enhance detection rules and monitor backend-driven phishing flows.
Related Posts:
- Search Engine Manipulation Leads to Backdoored App Downloads
- PyPI’s New Rule: 2FA Verification for All Project Maintainers
- Sneaky 2FA: A New Adversary-in-the-Middle Phishing-as-a-Service Threat
- Russian Cybercriminals Impersonate EFF in Targeted Attack on Albion Online Players
