
A recent report from Unit 42, the threat intelligence division of Palo Alto Networks, reveals a sophisticated and evasive phishing campaign discovered in December 2024. This campaign, notable for its multi-layered attack chain, delivers well-known malware such as Agent Tesla, Remcos RAT, and XLoader through a blend of scripting languages, execution paths, and deceptive social engineering.
“Attackers increasingly rely on such complex delivery mechanisms to evade detection, bypass traditional sandboxes, and ensure successful payload delivery and execution,” the report states.
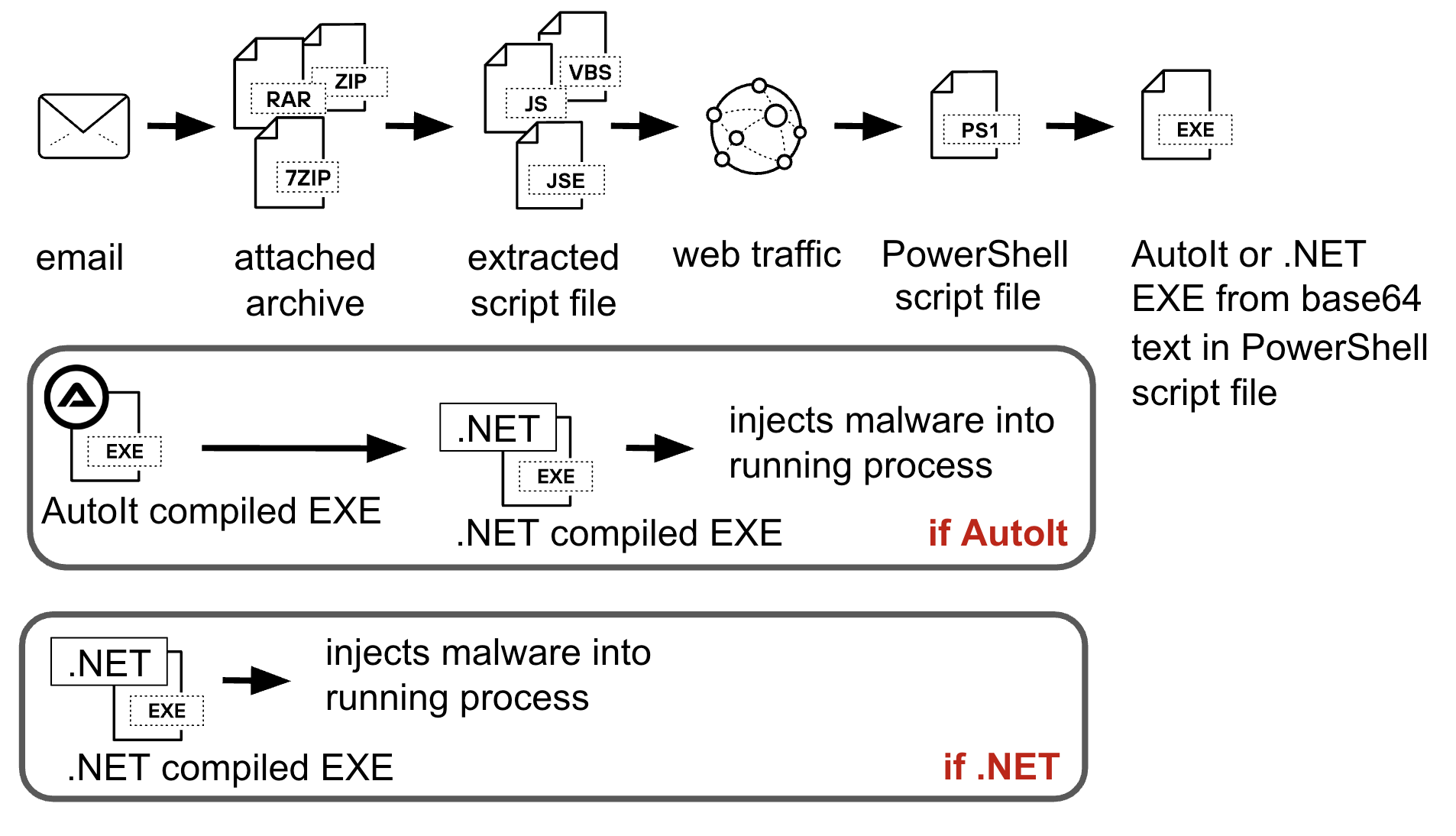
The attack starts with phishing emails disguised as payment confirmations or order release requests, urging recipients to open a malicious attachment. A common lure file name observed was doc00290320092.7z, which contains a .jse (JavaScript Encoded) file—named doc00290320092.jse—to simulate a legitimate document.
Once executed, this .jse script acts as a downloader, initiating the infection chain by retrieving and launching a PowerShell script.
“Notice that both the ZIP filename and the JSE filename start with doc, creating the illusion that the JSE file is a legitimate document.”
The PowerShell script is simple yet potent, containing a Base64-encoded payload. It decodes and executes the payload from the system’s temp directory, maintaining the stealth of the operation.
“The script is not obfuscated, as this attack chain relies on a multi-layered approach rather than heavy obfuscation,” Unit 42 analysts noted.
This method effectively avoids drawing attention from signature-based detection tools and traditional sandboxes.
From this point, the malware delivery branches into two possible paths—.NET-compiled executables or AutoIt-compiled droppers—each leading to a different malware variant.
- .NET Path: Process Injection into RegAsm
The .NET executable contains an AES- or Triple DES-encrypted payload, which is injected into the RegAsm.exe process. Unit 42 observed samples delivering both Agent Tesla and XLoader using this route.
“The .NET samples show process injection patterns that deliver various malware families, reinforcing the multi-layered approach employed by the attacker.”
- AutoIt Path: Shellcode Loader into RegSvcs
Alternatively, the AutoIt executable contains an encrypted payload that decrypts into shellcode, which is injected into the RegSvcs.exe process. This process in turn loads a .NET executable, culminating in the execution of Agent Tesla packed with .NET Reactor.
“One of the key functions in AutoIt for tracing shellcode execution is DLLCALLADDRESS… which ultimately points to the payload execution mechanism,” Unit 42 explains.
This variant of Agent Tesla is a feature-rich infostealer, capable of harvesting credentials, clipboard data, keystrokes, and more.
Unit 42 researchers leveraged tools like IDA Pro and dnSpy to reverse engineer both .NET and AutoIt samples. Through tracing DLL calls and API hooks, they were able to isolate the final malware payloads and identify consistent patterns across variants.
“The dynamically resolved API calls in the shellcode indicate a straightforward execution flow: load → decrypt → inject → execute.”
Despite the attack’s complexity, Palo Alto Networks’ Advanced WildFire detection successfully identified each layer in the infection chain. “Our analysis demonstrates how we can track and mitigate threats that rely on multi-stage delivery mechanisms,” Unit 42 concludes.
Related Posts:
- Xloader Malware Delivered via Sophisticated SharePoint Attack
- New Report Reveals SmokeLoader’s Advanced Tactics in Taiwan Campaign
- Agent Tesla Loader Evolves: New Evasive Techniques Pose Rising Threat
- New Agent Tesla Spyware Variant was spread via Microsoft Word documents
