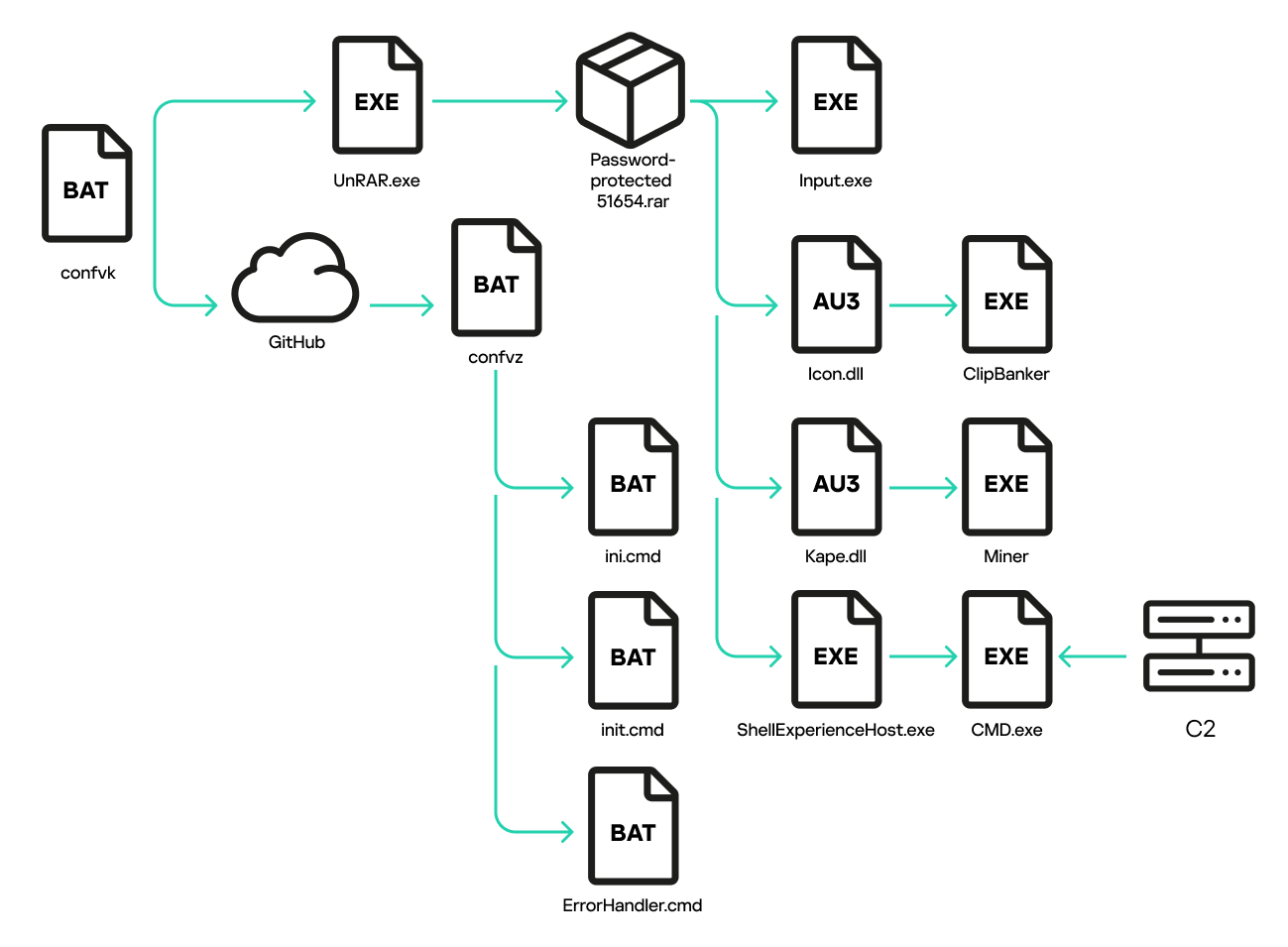
The infection chain: from executing confvk to setting up all the auto-start methods | Image: Kaspersky Labs
For many developers, SourceForge has long been a cornerstone of open-source collaboration — a trusted hub to host and distribute software. But for cybercriminals, it has recently become a platform to stage deception.
In a disturbing discovery by Kaspersky Labs, attackers have been exploiting SourceForge to deliver a sophisticated malware combo: a ClipBanker Trojan and a cryptocurrency miner, hidden behind a project masquerading as a Microsoft Office enhancement suite.
The campaign began with a legitimate-looking project on sourceforge.net, titled “officepackage”, cloned from a GitHub repository of real Microsoft Office add-ins. But behind the scenes, attackers set up a shadow domain — officepackage.sourceforge[.]io — which, unlike the main project page, hosted “an imposing list of office applications complete with version numbers and ‘Download’ buttons.”
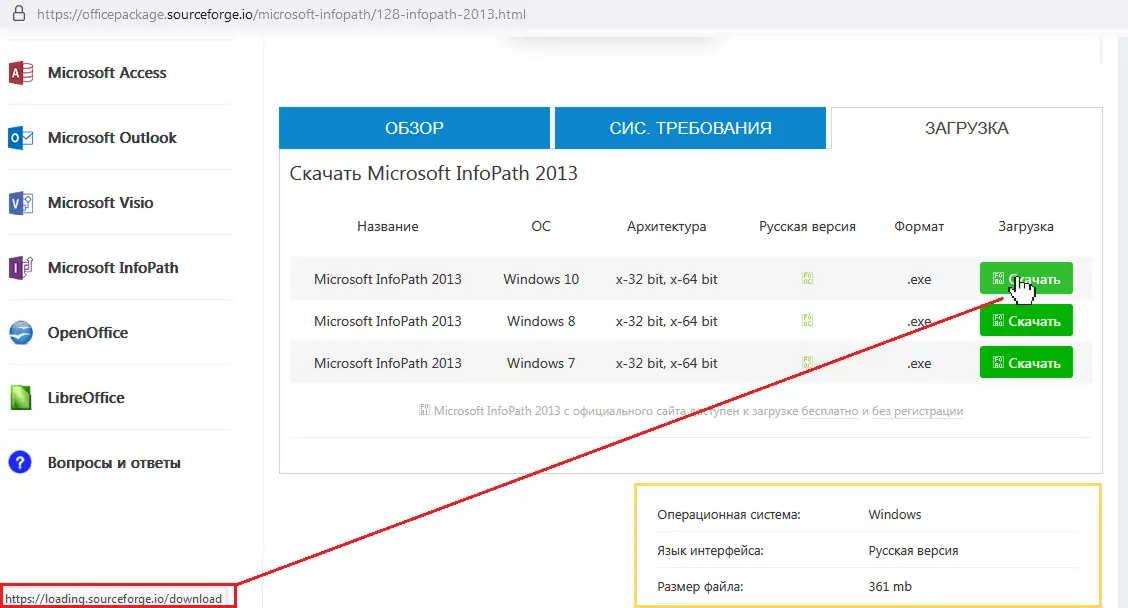
One click initiates a multi-stage infection chain involving inflated installers, embedded scripts, password-protected archives, and PowerShell magic — all carefully designed to fool the user and evade security tools.
“Clicking that button finally downloads a roughly seven-megabyte archive named vinstaller.zip,” Kaspersky reports. “This raises some red flags, as office applications are never that small, even when compressed.”
Once opened, the vinstaller.zip file contains another archive and a Readme.txt with the password. Inside lies a suspiciously large .msi file — over 700MB — its size artificially inflated using file pumping with null bytes.
When executed, the installer deploys a Visual Basic script that downloads a batch file (confvk) from GitHub. This batch file checks for signs of analysis environments or antivirus software, then proceeds to unpack a hidden RAR archive using embedded utilities.
One PowerShell script collects and exfiltrates system data via the Telegram API, while another (confvz) sets the stage for persistent malware execution — and that’s where things get even darker.
The core of the malware lies in two AutoIt scripts wrapped inside DLLs:
- Icon.dll injects a cryptocurrency miner into the system.
- Kape.dll delivers ClipBanker, which silently hijacks clipboard contents to replace copied cryptocurrency wallet addresses with the attacker’s own.
“The key malicious actions… boil down to running two AutoIt scripts,” the report states. “ClipBanker… replaces cryptocurrency wallet addresses in the clipboard with the attackers’ own.”
Alongside these, the RAR archive also included ShellExperienceHost.exe — a renamed Netcat utility used to establish encrypted remote command-line access to the infected system via port 445.
The malware creators ensured longevity through a staggering array of persistence mechanisms:
- Registry hijacks under App Paths to reroute common commands like install.exe to malicious batch scripts.
- Windows Services created under misleading names like NetworkConfiguration and PerformanceMonitor.
- WMIC event filters that retrigger the malware every 80 seconds (and every 300 seconds for backup).
A creative abuse of Windows’ ErrorHandler.cmd — a script meant for OS troubleshooting — is instead used to auto-launch PowerShell-based backdoors.
“This essentially creates a remote command line with apap[.]app:445 as the C2 server,” the researchers note.
While the attack has global implications, most victims appear to be from Russian-speaking regions. The localized interface of the officepackage.sourceforge[.]io site and telemetry from Kaspersky show that “90% of potential victims are in Russia, where 4,604 users encountered the scheme between early January and late March.”
This suggests a deliberate targeting strategy — using search engine optimization, familiar language, and pseudo-legitimate software to increase the likelihood of infection.
Related Posts:
- Cryptocurrency Malware: The Hidden Threat Lurking on YouTube
- Google Messages Rolls Out New Protections Against Scams and Sensitive Content
- NVIDIA Recommended Retailers: Do not sell GeForce graphics to miners