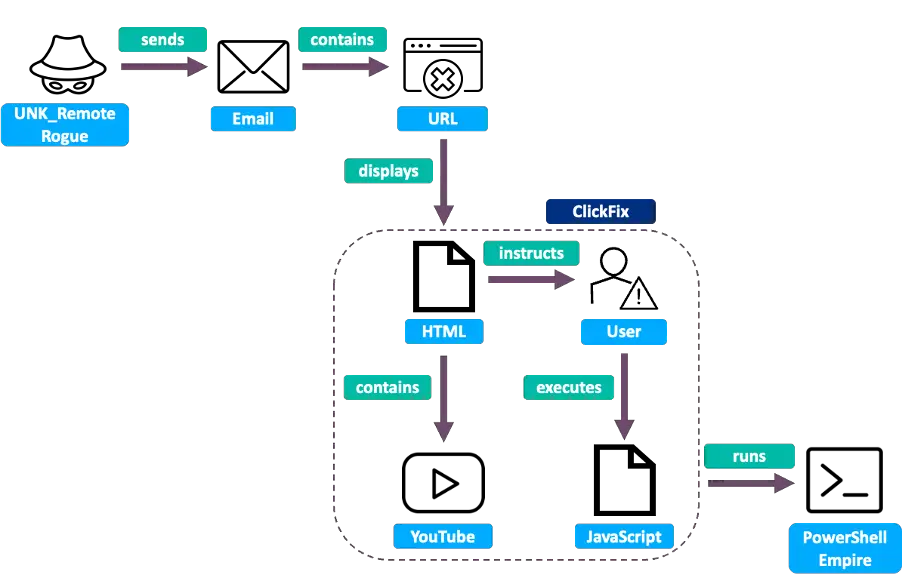
UNK_RemoteRogue ClickFix infection chain | Image: Proofpoint
In a recent cybersecurity report by Proofpoint researchers, a notable trend has emerged: state-sponsored actors are increasingly incorporating social engineering techniques traditionally favored by cybercriminals into their espionage campaigns. The report highlights the adoption of the ClickFix technique by groups from North Korea, Iran, and Russia. This shift underscores the evolving nature of cyber threats and the increasing fluidity of tactics, techniques, and procedures (TTPs) in the threat landscape.
What is ClickFix?
ClickFix is a social engineering technique that employs dialogue boxes with instructions to trick users into copying, pasting, and running malicious commands on their machines. This method often involves the use of fake error messages and authoritative alerts that appear to be coming from the operating system, thus deceiving users into taking harmful actions.
State-Sponsored Actors and ClickFix
Proofpoint’s research indicates that state-sponsored actors have begun to integrate ClickFix into their operations. This adoption is not aimed at revolutionizing existing campaigns but rather at replacing the installation and execution stages in the infection chain. The report emphasizes that this technique, while currently limited to a few state-sponsored groups, is likely to become more widely adopted, given its increasing popularity in both cybercrime and espionage.
- North Korea: TA427
In early 2025, Proofpoint observed the North Korean group TA427 utilizing ClickFix to target individuals in the think tank sector. The attackers used spoofed sender emails to initiate contact, engage targets, and ultimately direct them to an attacker-controlled site where they were persuaded to run a PowerShell command. In one instance, this led to the deployment of QuasarRAT, a commodity malware commonly used in cybercriminal activity.
The report detailed a specific campaign where TA427 operators masqueraded as a Japanese diplomat, sending emails to arrange a meeting with the Japanese ambassador to the U.S. The initial email contained a benign attachment, but subsequent communications led the target to a malicious PDF with a link to a landing page hosting a fake PDF file. This elaborate scheme illustrates the lengths to which state-sponsored actors will go to employ the ClickFix technique.
- Iran: TA450
The Iranian group TA450 was also observed using ClickFix in November 2024. In this case, the attackers sent phishing emails masquerading as security updates from Microsoft, urging targets to run a PowerShell command to address a supposed security vulnerability. The command was designed to install remote management and monitoring (RMM) software, which TA450 operators then used for espionage and data exfiltration.
- Russia: UNK_RemoteRogue and TA422
Russian state actors have also been experimenting with ClickFix. The group UNK_RemoteRogue was seen using it in late 2024 in a campaign targeting the defense industry. Another Russian group, TA422, was observed using ClickFix in October 2024, employing phishing emails with links that mimicked a Google spreadsheet to deceive targets into running a PowerShell command.
Why ClickFix?
The adoption of ClickFix by state-sponsored actors highlights a broader trend in the threat landscape: the convergence of TTPs between cybercriminal and state-sponsored activities. As the report notes, “Threat actors share, copy, steal, adopt, and test TTPs from publicly exposed tradecraft or interaction with other threat groups.” This fluidity makes it challenging to attribute attacks and defend against them, as state-sponsored actors increasingly leverage techniques first developed by cybercriminals.
Looking Ahead
While the use of ClickFix by state-sponsored actors is still emerging, the Proofpoint report suggests that it is likely to increase. The report also points out the absence of ClickFix in Chinese state-sponsored actor campaigns. However, this absence is attributed to visibility rather than a lack of experimentation.
Related Posts:
- ClickFix: The Rising Threat of Clipboard-Based Social Engineering
- Beware of Fake Google Meet Invites: ClickFix Campaign Spreading Infostealers
- Lazarus APT Targets Job Seekers with “Contagious Interview” Campaign Using ClickFix Technique
- com Impersonated in Phishing Campaign Delivering Credential-Stealing Malware
