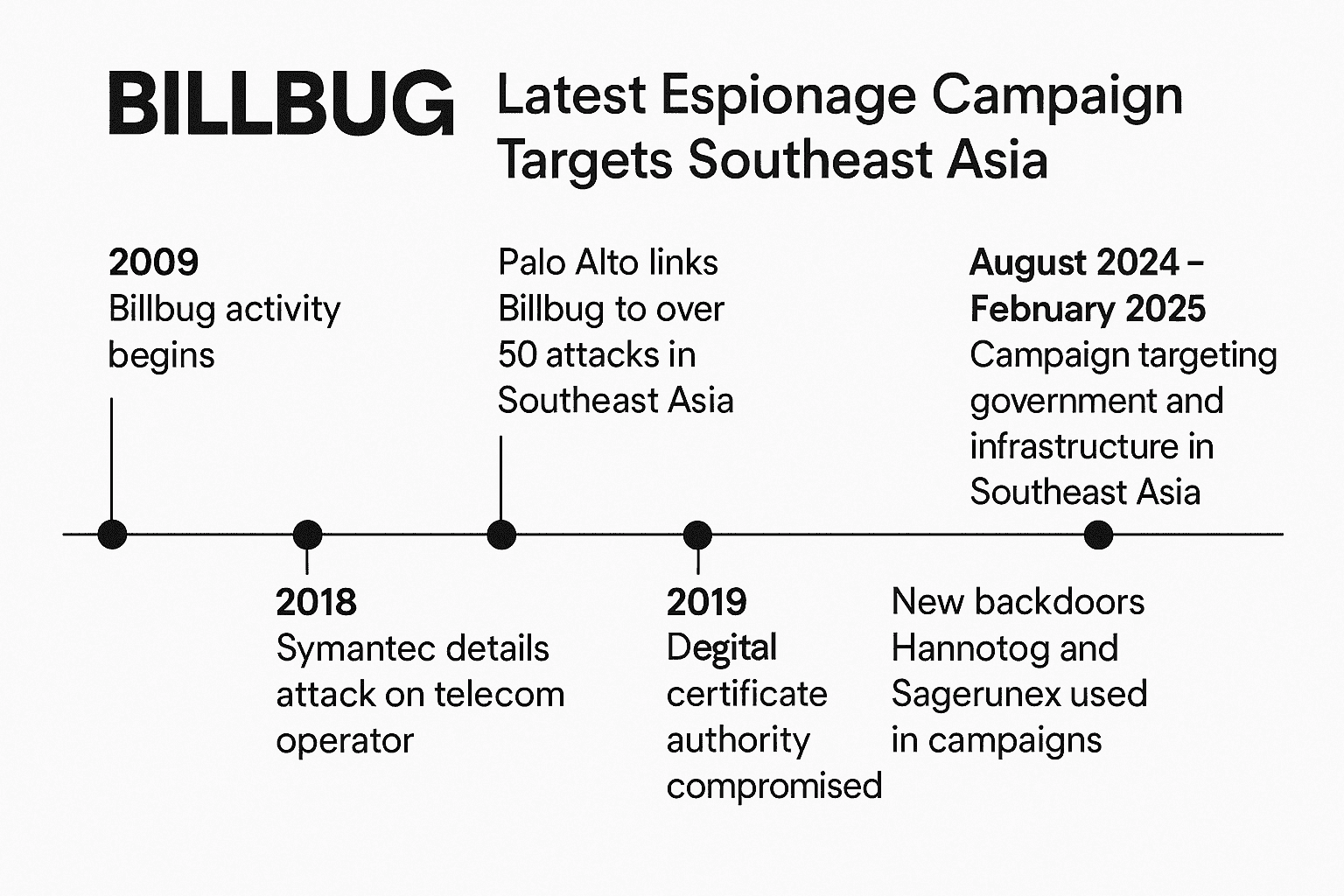
A recent report by Symantec’s Threat Hunter Team has uncovered an extensive espionage campaign orchestrated by the Billbug group, also known as Lotus Blossom, Lotus Panda, or Bronze Elgin. The campaign, which spanned from August 2024 to February 2025, targeted multiple organizations in Southeast Asia, including a government ministry, an air traffic control organization, a telecoms operator, and a construction company. Additionally, the group targeted a news agency and an air freight organization in neighboring Southeast Asian countries.
Billbug has operated since at least 2009 and has a deep history of targeting governments and military organizations across Southeast Asia. First publicized by Palo Alto Networks in 2015 and later tracked by Symantec as “Thrip,” the group has consistently executed advanced, targeted campaigns. These included:
- 2015–2018: Attacks against telecoms and defense sectors using the Trensil Trojan.
- 2019: Introduction of new backdoors like Hannotog and Sagerunex, with targets spanning media, maritime, and education sectors.
- 2022: Compromise of a digital certificate authority, raising concerns over potential misuse of certificates to sign malware or intercept encrypted communications.
While the campaign initially couldn’t be linked to a single actor, indicators of compromise (IOCs) later shared by Cisco Talos aligned with known Billbug operations, helping confirm attribution. These IOCs matched earlier malicious activity documented by Symantec in December 2024.
Billbug’s use of DLL sideloading—abusing legitimate software to launch malicious payloads—remains a cornerstone of its operations. In this campaign, the group misused executables from trusted vendors like Trend Micro and Bitdefender:
- tmdbglog.exe (Trend Micro) was used to sideload a malicious DLL tmdglog.dll, which decrypted and executed payloads from a file named TmDebug.log.
- bds.exe (Bitdefender) sideloaded a DLL called log.dll, which injected code into the system tray process (systray.exe).
“Several variants of log.dll were used in the campaign, but only one was retrieved for analysis,” the report states.
Billbug’s adaptability is further evident in its deployment of new, custom-built tools, including:
- ChromeKatz and CredentialKatz – Two tools designed to extract credentials and cookies from Chrome browsers.
- A reverse SSH tool – Capable of listening for SSH connections on port 22, enabling covert remote access.
- Zrok – An open-source P2P tool used to expose internal services remotely.
- Datechanger.exe – A utility that modifies file timestamps to hinder forensic analysis.
“The attackers deployed the publicly available Zrok peer-to-peer tool… to provide remote access to services that were exposed internally,” Symantec noted.
A new variant of the Sagerunex backdoor—long associated exclusively with Billbug—was also used in the campaign. The malware was configured to achieve persistence by modifying Windows registry keys, allowing it to run as a service. Cisco had similarly documented this variant in February 2025.
Organizations in the region, particularly those in government, telecommunications, and critical infrastructure sectors, should remain vigilant and implement robust cybersecurity measures to defend against these threats.
Related Posts:
- China-Linked Phishing Campaign Exploits Geopolitical Tensions, Ravages Asian Finance Sector
- Python Developers Beware: Attackers Sneak Malware into Popular Package Manager
- Kaspersky Lab Exposes TTPs of Asian Cyber Espionage Groups
- High-Profile Organizations in Southeast Asia Hit by Targeted Cyberattacks
- DLL Sideloading & Proxying: New Campaign Delivers Sliver Implants to German Targets
