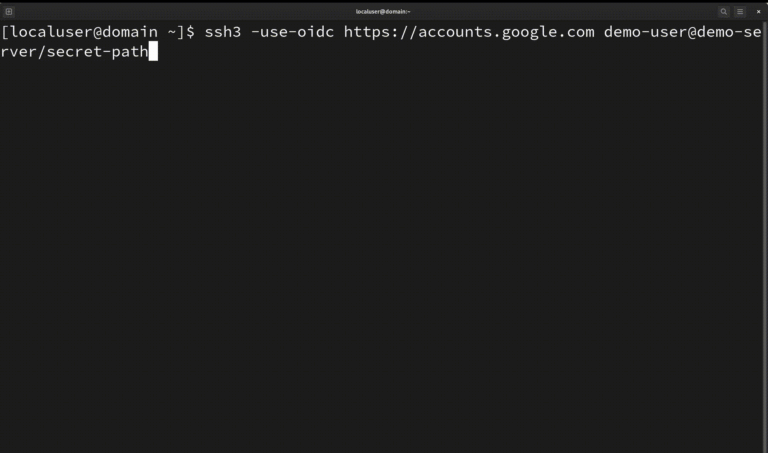
SSH3: faster and rich secure shell using HTTP/3 SSH3 is a complete revisit of the SSH protocol,...
Defense
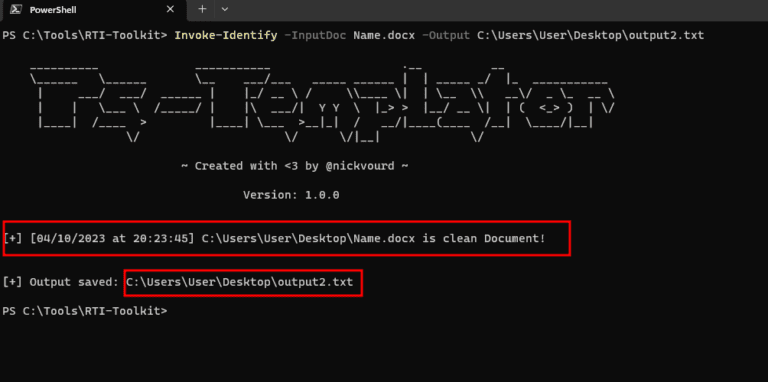
RTI-Toolkit RTI-Toolkit is an open-source PowerShell toolkit for Remote Template Injection attacks. This toolkit includes a PowerShell...
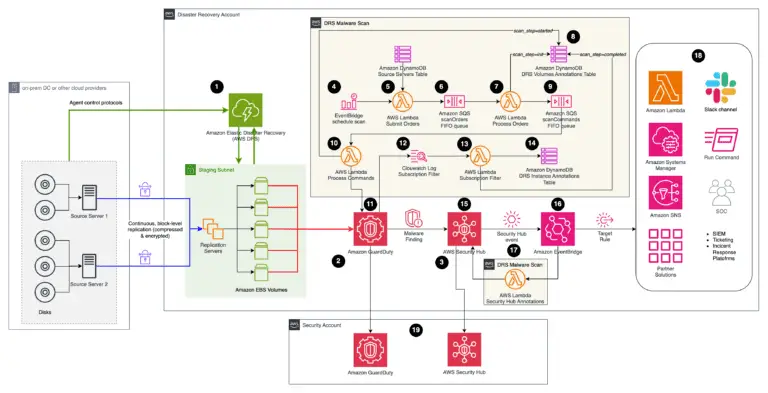
Perform malware scan analysis of on-prem servers using AWS services Challenges with on-premises malware detection It can...
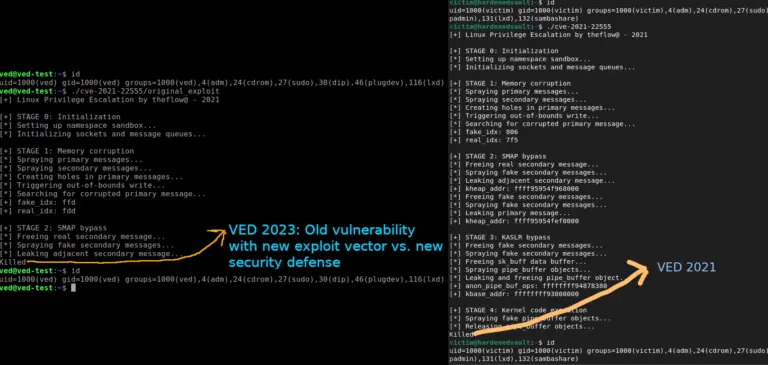
VED-eBPF: Kernel Exploit and Rootkit Detection using eBPF VED (Vault Exploit Defense)-eBPF leverages eBPF (extended Berkeley Packet...
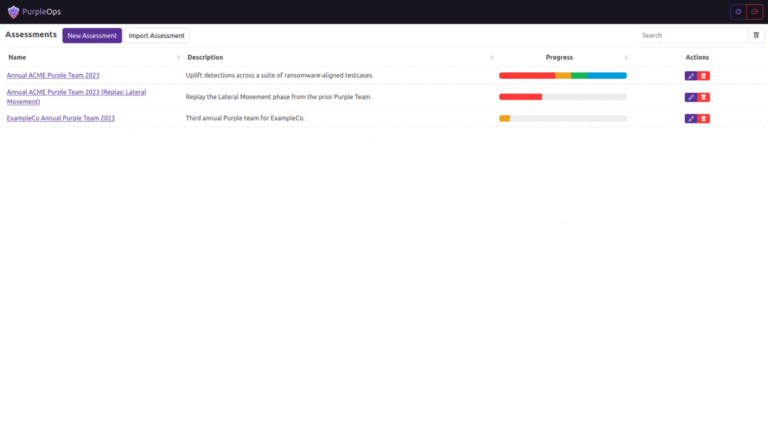
PurpleOps PurpleOps is a free, open-source web app to track Purple Team assessments. Create assessments aligned with...
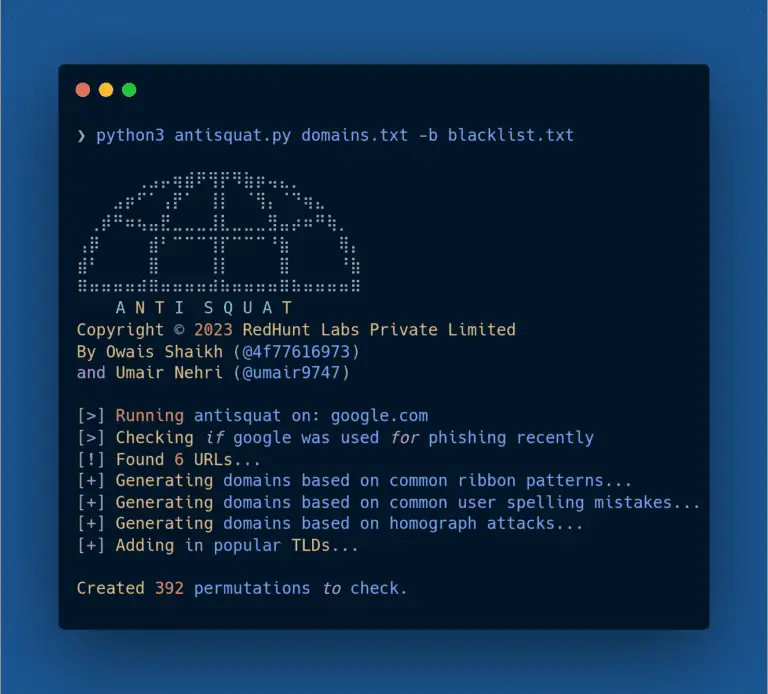
AntiSquat AntiSquat leverages AI techniques such as natural language processing (NLP), large language models (ChatGPT) and more...
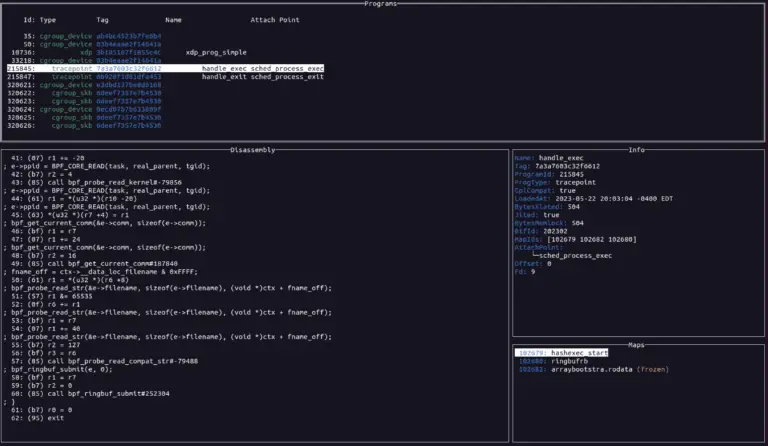
ebpfmon ebpfmon is a tool for monitoring eBPF programs. It is designed to be used with bpftool from the Linux...
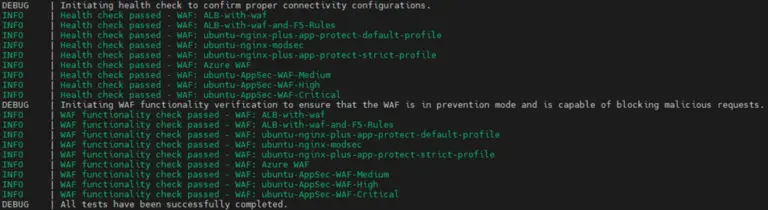
Web Application Firewall (WAF) Comparison Project This project repository contains testing datasets and tools to compare WAF...
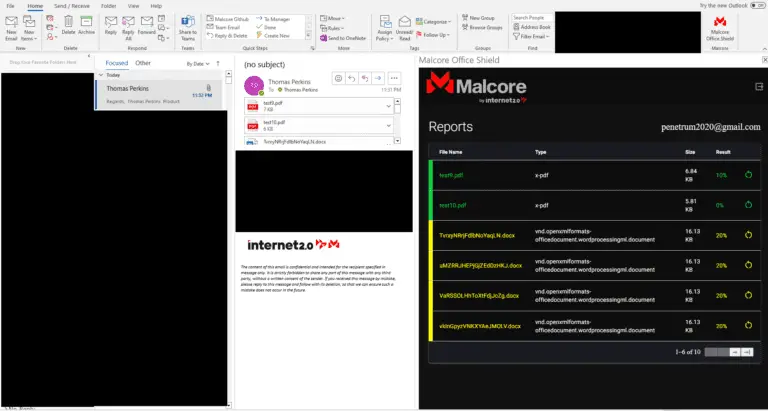
Malcore Office Shield Introducing The Malcore Office Shield imagine having the ability to analyze every attachment that...
MELEE: A Tool to Detect Ransomware Infections in MySQL Instances Attackers are abusing MySQL instances for conducting...
Cybercriminals persistently assail America’s vital infrastructure, exploiting readily accessible and vulnerable operational technology (OT) assets online. In...
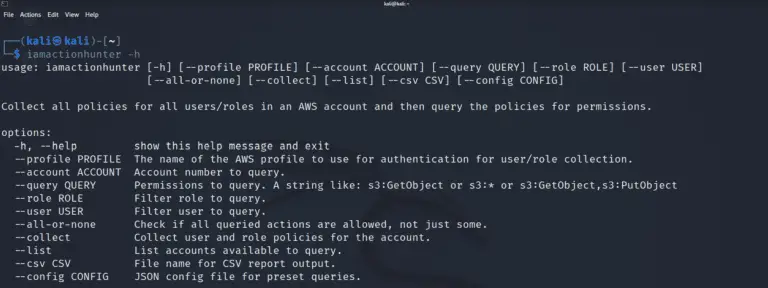
IAMActionHunter IAMActionHunter is an IAM policy statement parser and query tool that aims to simplify the process...
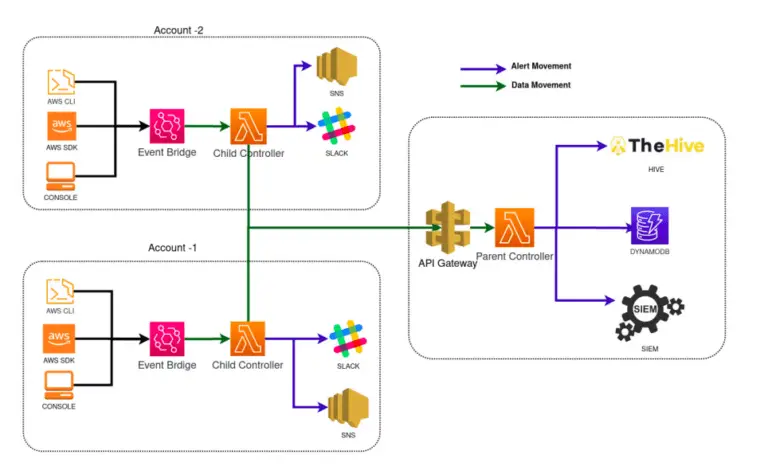
DIAL Workloads on the cloud provide equal opportunities for hackers as much as they do for internal...
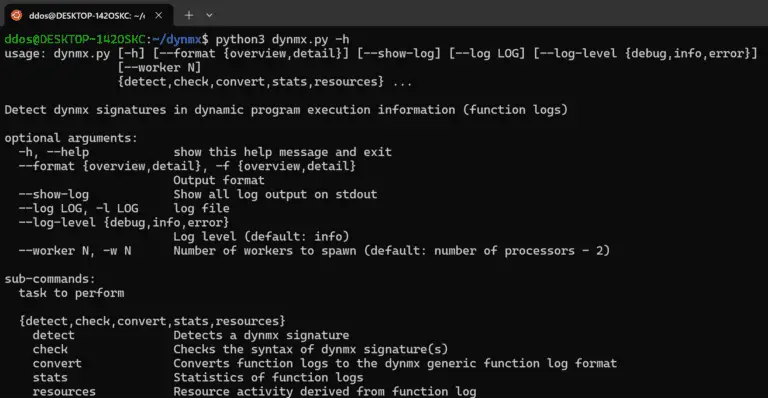
dynmx dynmx (spoken dynamics) is a signature-based detection approach for behavioural malware features based on Windows API call sequences....
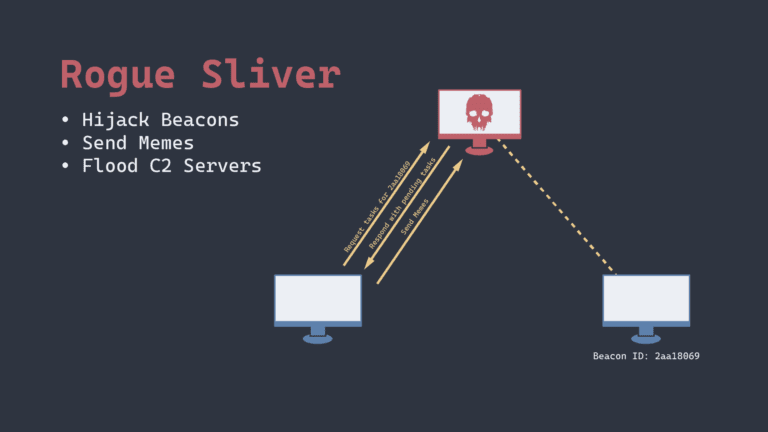
RogueSliver A suite of tools to disrupt campaigns using the Sliver C2 framework. This tool, its uses,...