What is sandfly-filescan? sandfly-filescan is a utility to quickly scan files and report on their entropy (a measure...
Malware Analysis
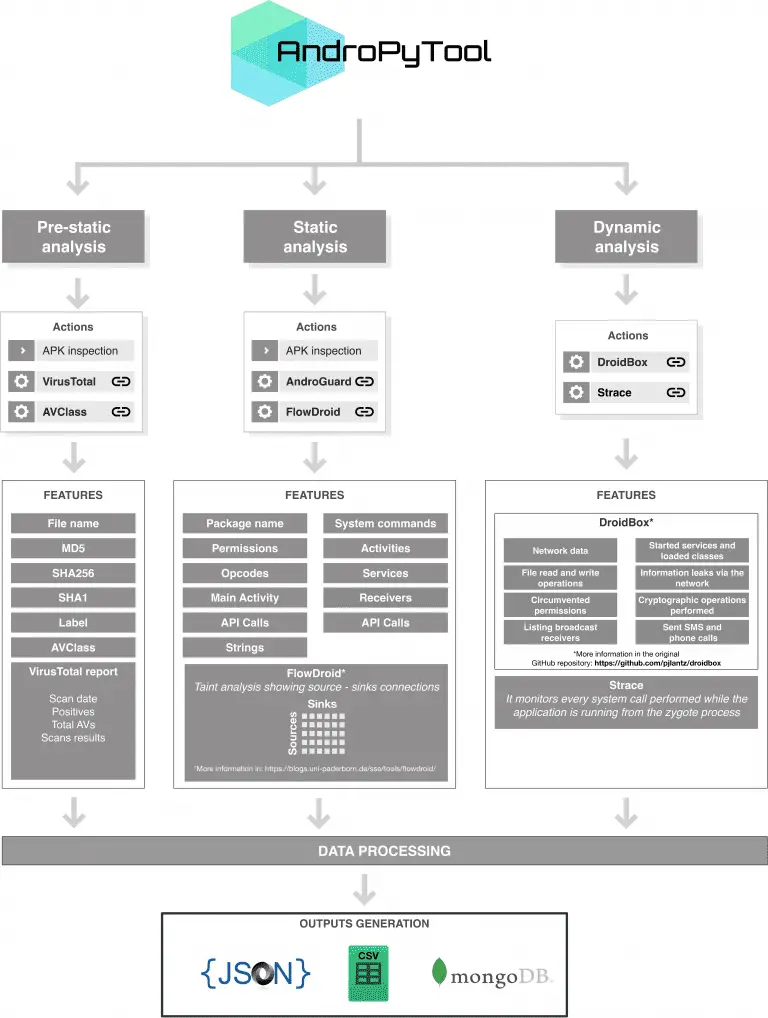
AndroPyTool This is a tool for extracting static and dynamic features from Android APKs. It combines different...
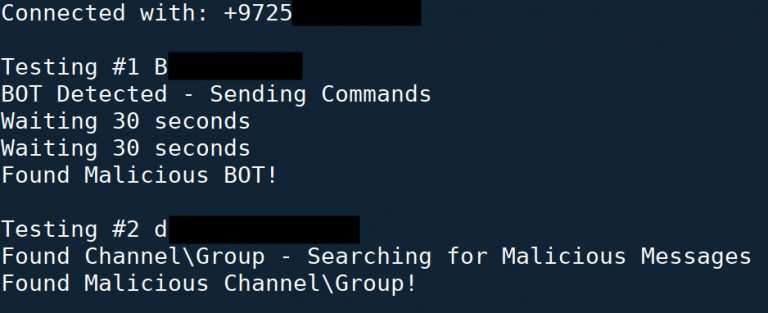
RepoTele – Hunting Abused Telegram Accounts The following is a part of my talk called “Leveraging Yara...
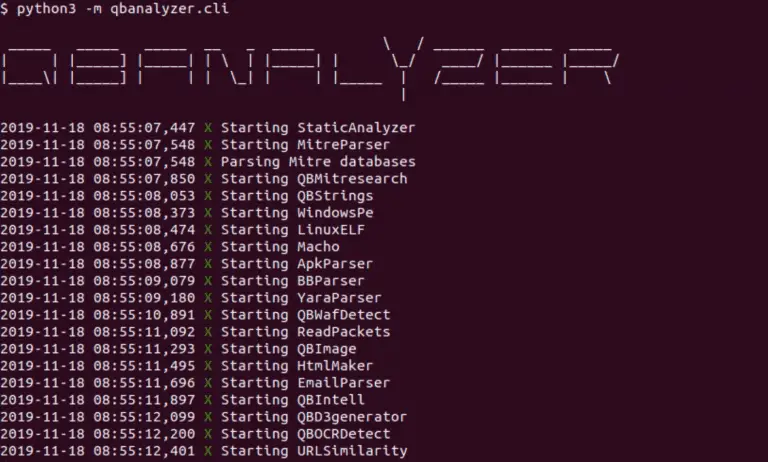
Analyzer Analyzer is an open-source threat intelligence framework that automates extracting artifacts and IOCs from file/dump into...
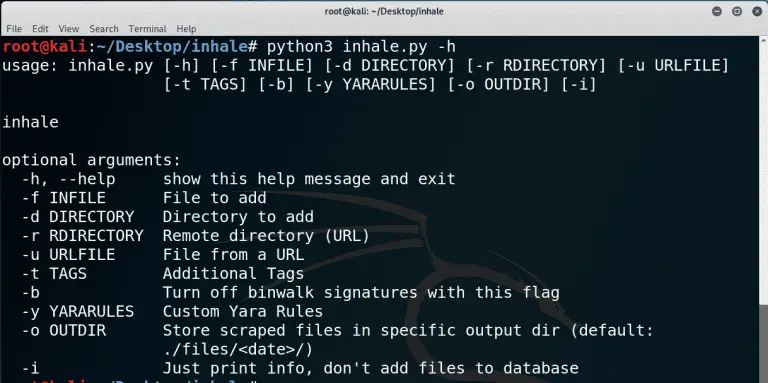
Inhale – Malware Inhaler Inhale is a malware analysis and classification tool that is capable of automating...
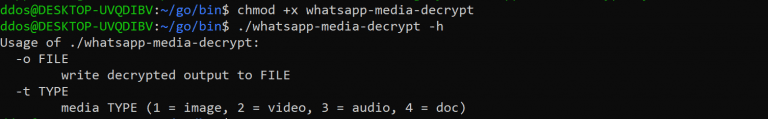
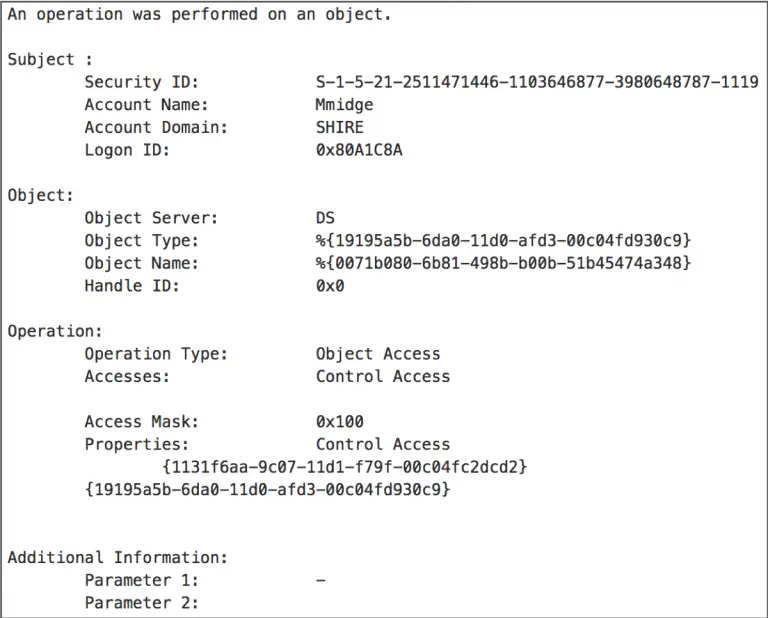
WhatsApp Media Decrypt A recent high-profile forensic investigation reported that “due to end-to-end encryption employed by WhatsApp, it is...
Norimaci “Norimaci” is a simple and lightweight malware analysis sandbox for macOS. This tool was inspired by...
EmoCheck Emotet detection tool for Windows OS. How EmoCheck detects Emotet (v0.0.1) Emotet generates their process name...
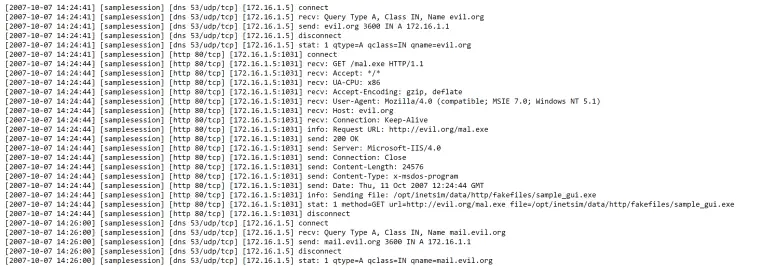
INetSim INetSim is a software suite for simulating common internet services in a lab environment, e.g. for...
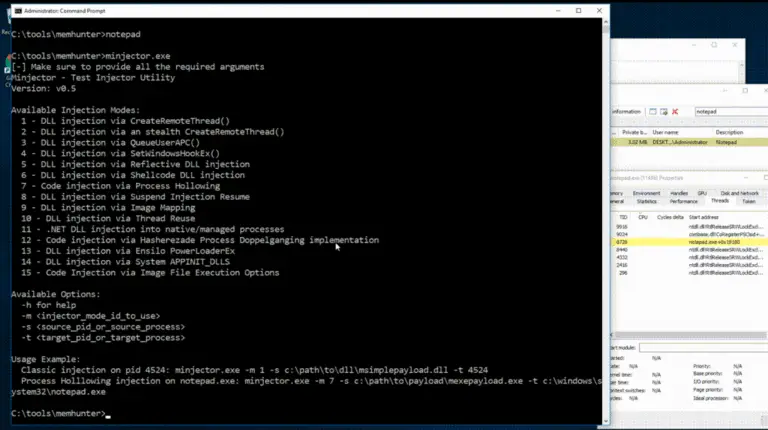
Memhunter Automated hunting of memory-resident malware at scale Overview Memhunter is an endpoint sensor tool that is...
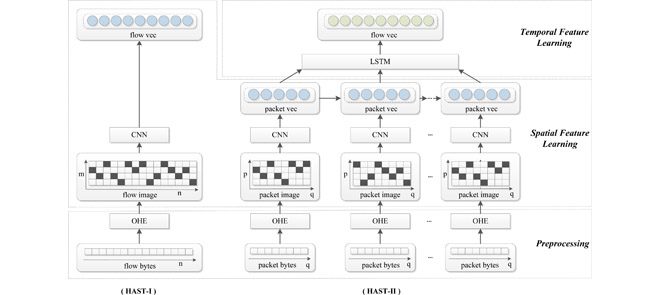
Deep Learning models for network traffic classification The development of an anomaly-based intrusion detection system (IDS) is...
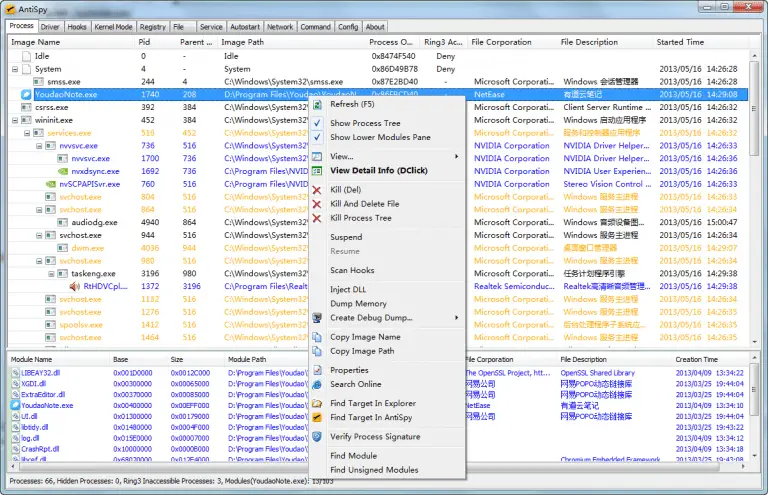
AntiSpy AntiSpy is a free but powerful anti-virus and rootkits toolkit. It offers you the ability with...
Unprotect Malware for the Mass The Unprotect Project is an Open Source project that aims to propose...
Mordor Gates The Mordor project provides pre-recorded security events generated by simulated adversarial techniques in the form...
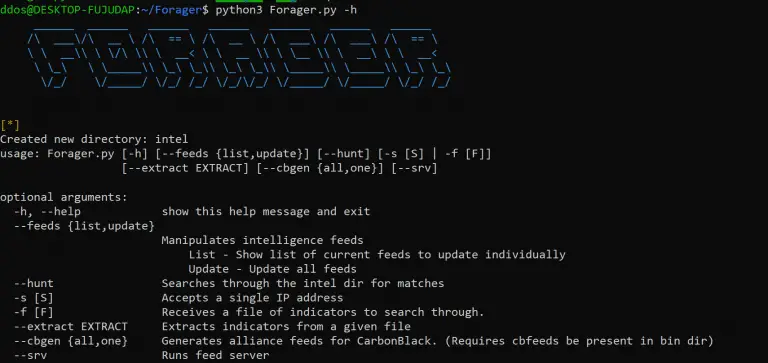
Forager Do you ever wonder if there is an easier way to retrieve, store, and maintain all...