Category: Post Exploitation
SharpRelay SharpRelay is based on the WinDivert driver. According to its description, WinDivert is a kernel driver that allows for user-mode packet interception and modification. The user needs to specify a filter and any packets...
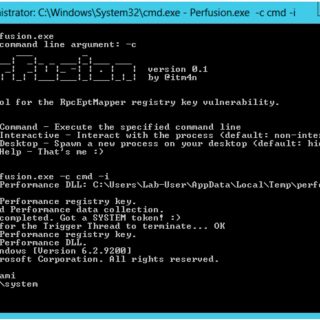
Perfusion On Windows 7, Windows Server 2008R2, Windows 8, and Windows Server 2012, the registry key of the RpcEptMapper and DnsCache (7/2008R2 only) services is configured with weak permissions. Any local user can create a Performance subkey and then leverage...
BlackMamba BlackMamba is a multi-client C2/post-exploitation framework with some spyware features. Powered by Python 3.8.6 and QT Framework. Some of BlackMamba features are: Multi-Client – Supports multiple client connections at the same time. Real-Time Communication...
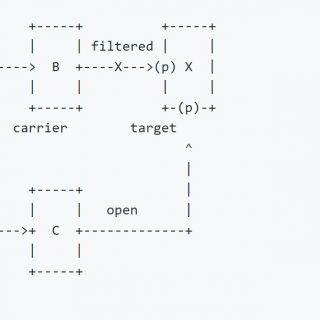
What is CornerShot In warfare, CornerShot is a weapon that allows a soldier to look past a corner (and possibly take a shot), without risking exposure. Similarly, the CornerShot package allows one to look...
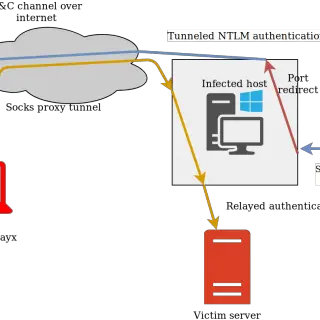
PortShellCrypter PortShellCrypter allows to e2e encrypt shell sessions, single- or multip-hop, being agnostic of the underlying transport, as long as it is reliable and can send/receive Base64 encoded data without modding/filtering. Along with the...
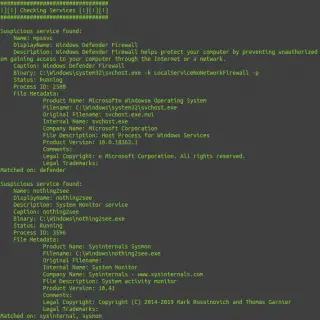
SharpEDRChecker New and improved C# Implementation of Invoke-EDRChecker. Checks running processes, process metadata, Dlls loaded into your current process and each DLLs metadata, common install directories, installed services and each service binaries metadata, installed drivers...
WSuspicious This is a proof of concept program to escalate privileges on a Windows host by abusing WSUS. Details in this blog post. It was inspired by the WSuspect proxy project. WSuspicious is a C#...
MOSE (Master Of SErvers) MOSE is a post-exploitation tool that enables security professionals with little or no experience with configuration management (CM) technologies to leverage them to compromise environments. CM tools, such as Puppet, Chef, Salt,...
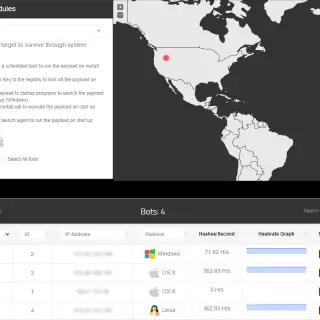
BYOB BYOB is an open-source post-exploitation framework for students, researchers, and developers. It includes features such as: Pre-built C2 server Custom payload generator 12 post-exploitation modules It is designed to allow students and developers...
Apollo Apollo is a Windows agent written in C# using the 4.0 .NET Framework designed to be used in SpecterOps training offerings. Apollo lacks some evasive tradecraft provided by other commercial and open-source tools,...
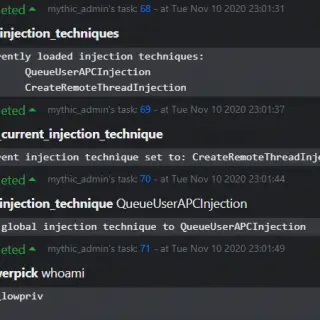
StandIn StandIn is a small AD post-compromise toolkit. StandIn came about because recently at xforcered we needed a .NET native solution to perform resource-based constrained delegation. However, StandIn quickly ballooned to include a number of...
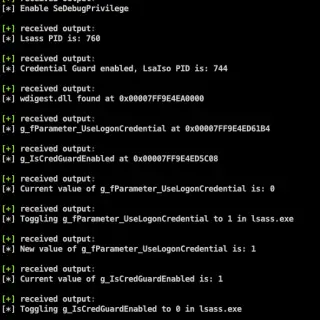
WdToggle A Proof of Concept Cobalt Strike Beacon Object File which uses direct system calls to enable WDigest credential caching and circumvent Credential Guard (if enabled). Additional guidance can be found in this blog post. Background This PoC code is...
Procrustes Procrustes is a bash script that automates the exfiltration of data over dns in case we have blind command execution on a server where all outbound connections except DNS are blocked. The script...
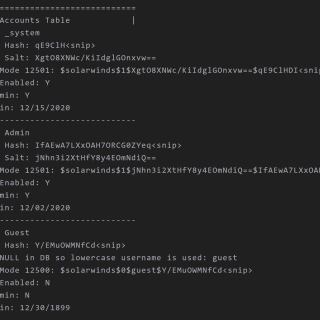
solarflare Credential Dumping Tool for SolarWinds Orion. SolarFlare is a Authentication Audit / Password dumping tool originally designed for Red Team engagements, but can be used to audit the exposure SolarWinds Orion systems pose...
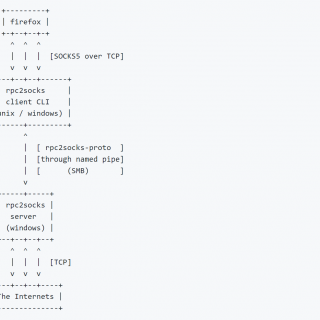
rpc2socks rpc2socks is a client-server solution that allows us to drop and remotely run a custom RPC + SOCKS-through-SMB server application on a Windows target, from a Unix or Windows host. The client-server pair can be used as a regular...