Category: Post Exploitation
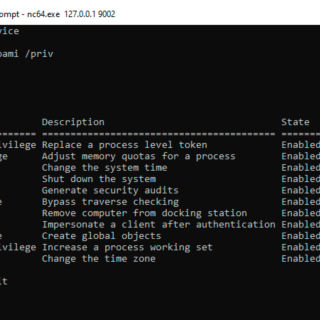
FullPowers FullPowers is a Proof-of-Concept tool I made for automatically recovering the default privilege set of a service account including SeAssignPrimaryToken and SeImpersonate. Rationale On Windows, some services executed as LOCAL SERVICE or NETWORK SERVICE are configured to run with a restricted set of...
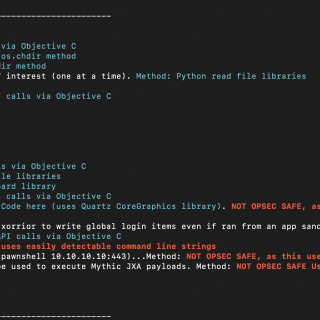
MacC2 MacC2 is a macOS post-exploitation tool written in python that uses Objective C calls or python libraries as opposed to command-line executions. I wrote this tool to aid purple team exercises aimed at...
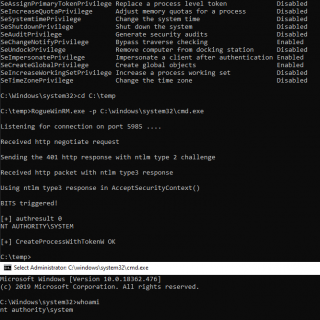
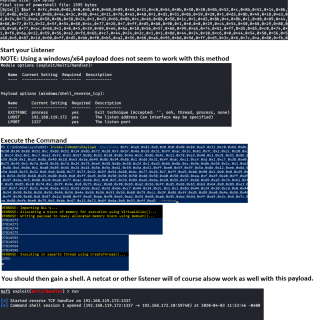
RogueWinRM RogueWinRM is a local privilege escalation exploit that allows to escalate from a Service account (with SeImpersonatePrivilege) to a Local System account if WinRM service is not running (default on Win10 but NOT...
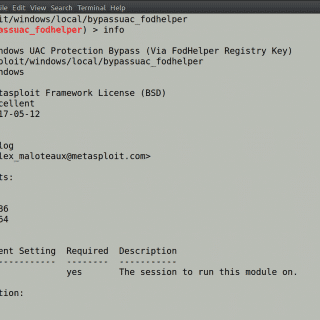
SilentClean UAC bypass via binary planting This project implements a DLL planting technique to bypass UAC Always Notify and execute code in a high integrity process. When the SilentCleanup task is launched, dismhost searches for the...
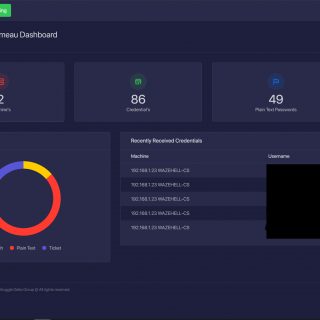
Chalumeau Chalumeau is an automated, extendable and customizable credential dumping tool based on powershell and python. Main Features Write your own Payloads In-Memory execution Extract Password List Dashboard reporting / Web Interface Parsing Mimikatz...
PrintSpoofer From LOCAL/NETWORK SERVICE to SYSTEM by abusing SeImpersonatePrivilege on Windows 10 and Server 2016/2019. For more information. Usage You can check the help message using the -h option. C:\TOOLS>PrintSpoofer.exe -h PrintSpoofer v0.1 (by @itm4n) Provided...
Invoke-AntiVM Invoke-AntiVM is a set of modules to perform VM detection and fingerprinting (with exfiltration) via Powershell. Compatibility Run the script check-compatibility.ps1 to check what modules or functions are compatible with the powershell version....
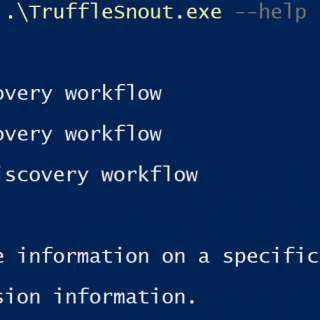
TruffleSnout Iterative AD discovery toolkit for offensive operators. Situational awareness and targeted low noise enumeration. Preference for OpSec. Discover: Forests and Trusts Domains and Trusts GCs/DCs Search and Query AD: For objects and data...
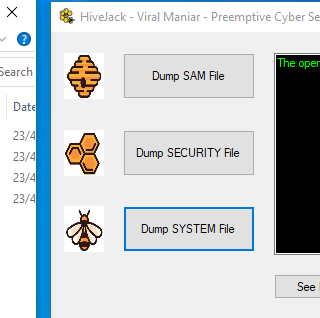
HiveJack This tool can be used during internal penetration testing to dump Windows credentials from an already-compromised host. It allows one to dump SYSTEM, SECURITY, and SAM registry hives and once copied to the...
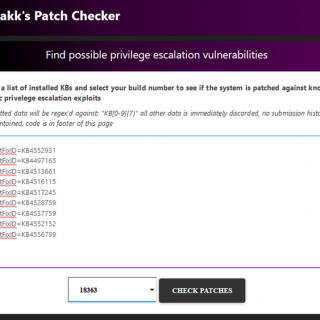
PatchChecker This is the code base for the service running on here. In short, PatchChecker is a web application (running on a flask) that provides output similar to that of Watson. However, by using...
PowerShell Red Team Enum Collection of PowerShell functions a Red Teamer may use to collect data from a machine or gain access to a target. I added ps1 files for the commands that are...
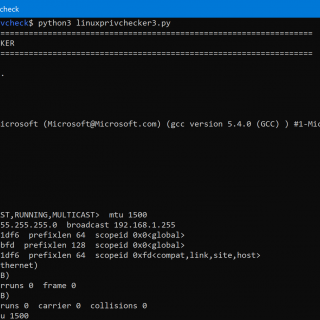
linuxprivcheck Python script for privilege escalation for Linux The original author is Mike Czumak (T_v3rn1x) — @SecuritySift. Scripts old-linuxprivchecker.py: Famous linuxprivchecker.py (Python) with updates – I’ll not update it anymore. linuxprivchecker3.py: Famous linuxprivchecker.py, compatible...
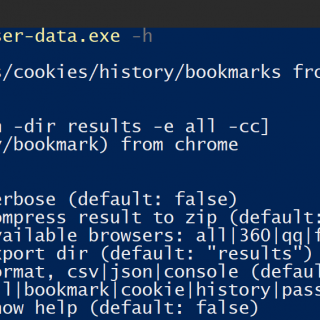
HackBrowserData hack-browser-data is an open-source tool that could help you decrypt data[passwords|bookmarks|cookies|history] from the browser. It supports the most popular browsers on the market and runs on Windows, macOS, and Linux. Supported Browser Windows...
SwiftBelt SwiftBelt is a macOS enumerator inspired by @harmjoy’s Windows-based Seatbelt enumeration tool. It does not utilize any command-line utilities and instead uses Swift code (leveraging the Cocoa Framework, Foundation libraries, OSAKit libraries, etc.)...
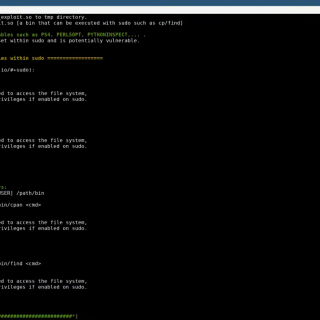
SUDO_KILLER SUDO_KILLER is a tool that can be used for privilege escalation on the Linux environment by abusing SUDO in several ways. The tool helps to identify misconfiguration within sudo rules, vulnerability within the...