tactical-exploitation I’ve always been a big proponent of a tactical approach to penetration testing that does not...
Post Exploitation
MIDA-Multitool – Bash script purposed for system enumeration, vulnerability identification, and privilege escalation.MIDA Multitool draws functionality from several...
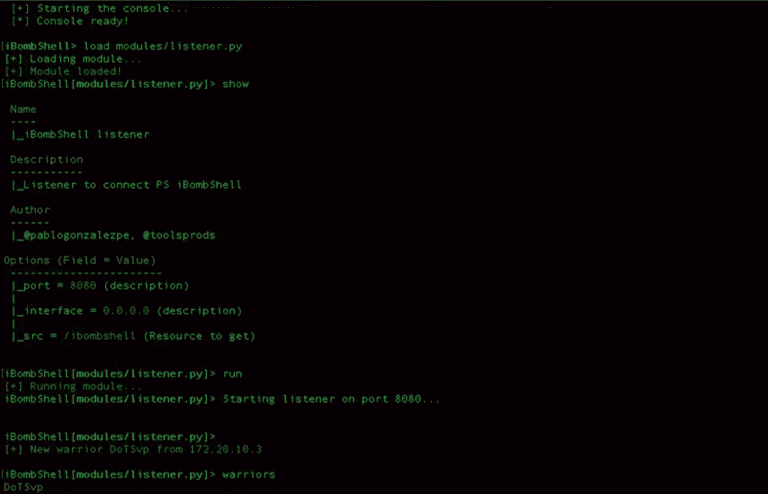
ibombshell – Dynamic Remote Shell ibombshell is a tool written in Powershell that allows you to have a...
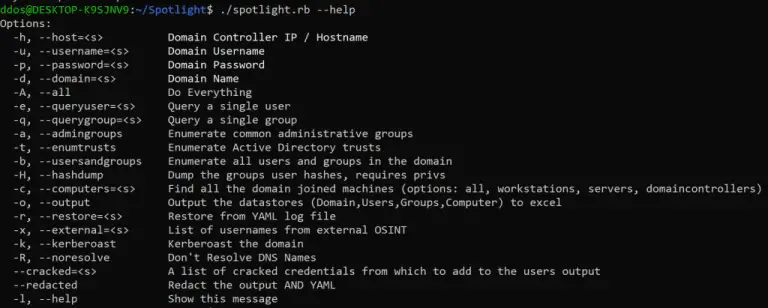
Synopsis This script was created to provide a full LDAP enumeration suite for objects stored in Active...
Invoke-TheHash contains PowerShell functions for performing pass the hash WMI and SMB tasks. WMI and SMB services...
PowerShdll Run PowerShell with dlls only. Does not require access to powershell.exe as it uses powershell automation...
EvilOSX A pure python, post-exploitation, remote administration tool (RAT) for macOS/OS X. Feature Emulate a terminal instance...
Powermad – PowerShell MachineAccountQuota and DNS exploit tools Functions MachineAccountQuota Functions The default Active Directory ms-DS-MachineAccountQuota attribute...
BeRoot Project is a post exploitation tool to check common misconfigurations to find a way to escalate...
EventCleaner A tool mainly to erase specified records from Windows event logs, with additional functionalities. EventCleaner suspend...
yodo proves how easy it is to become root via limited sudo permissions, via dirty COW or...
Extract password from TeamViewer memory using Frida (CVE-2018-14333) TeamViewer automatically authentication A few days ago I worked on...
RPIVOT allows to tunnel traffic into an internal network via socks 4. It works like ssh dynamic...
Invoke-WMILM This is a PoC script for various methods to achieve authenticated remote code execution via WMI,...
Piper Forward local or remote tcp ports through SMB pipes. Download git clone https://github.com/p3nt4/Invoke-Piper.git EXAMPLES Local port forwarding...