Category: Penetration Testing
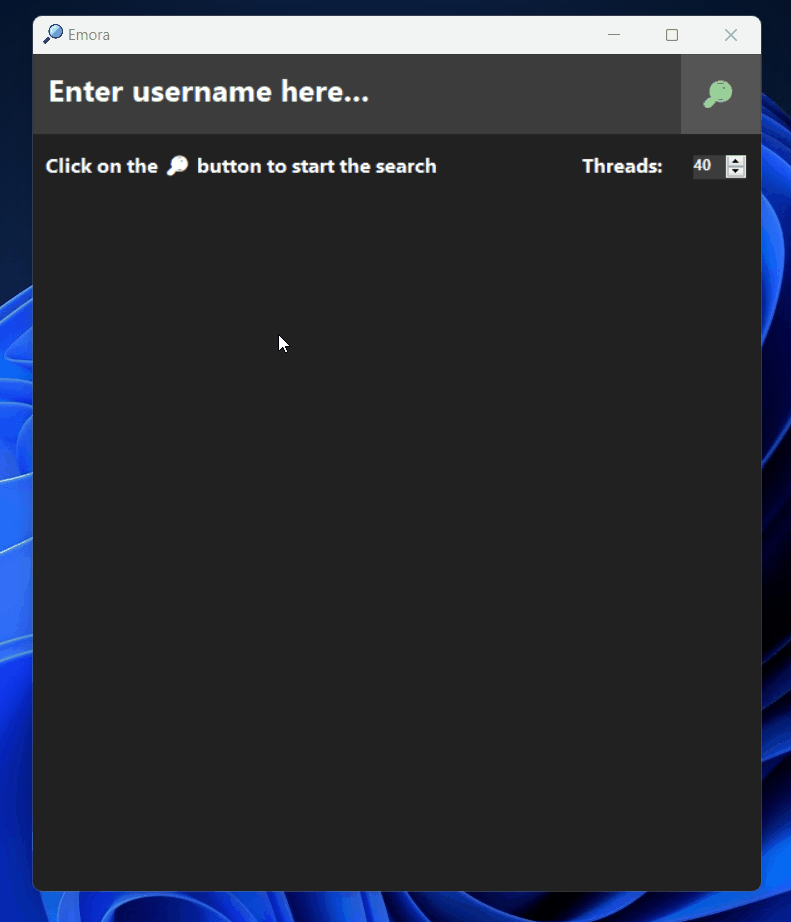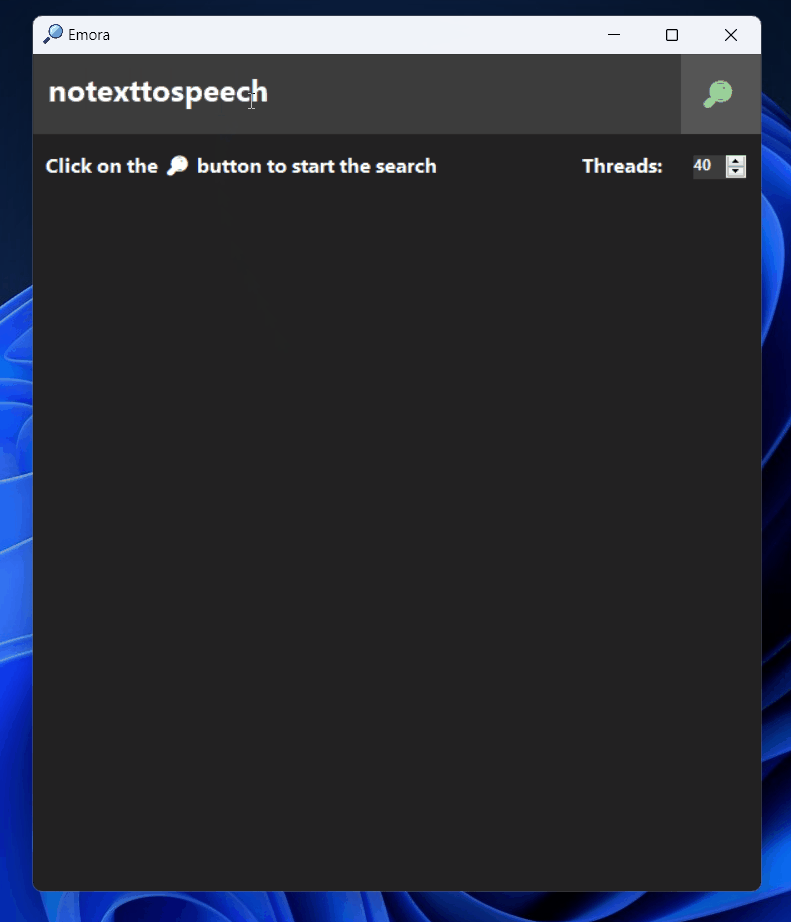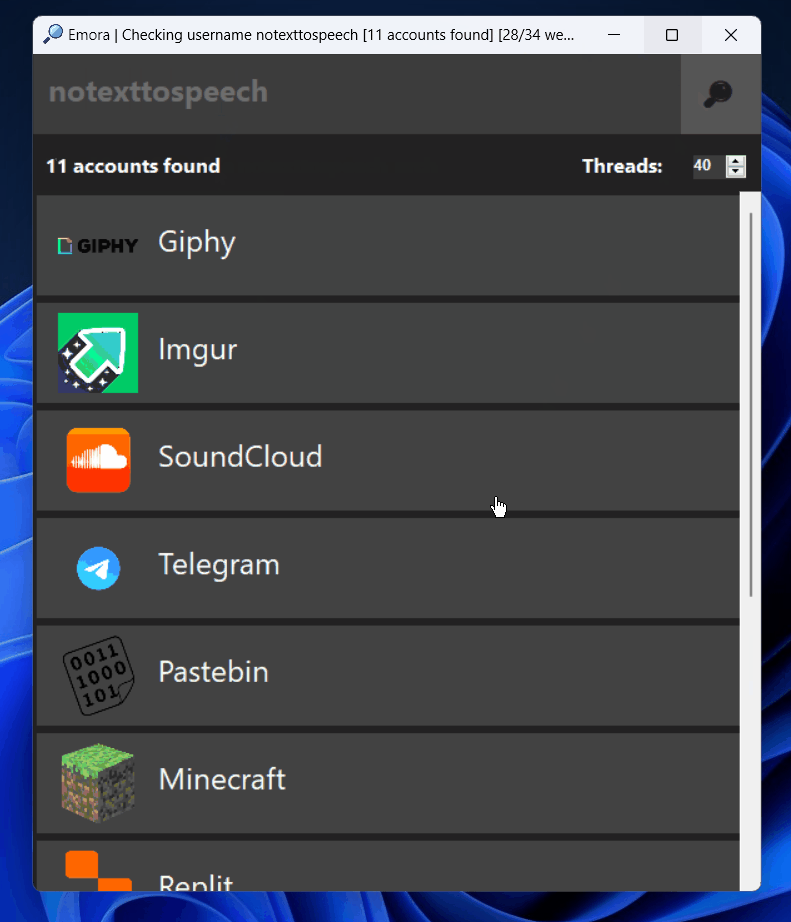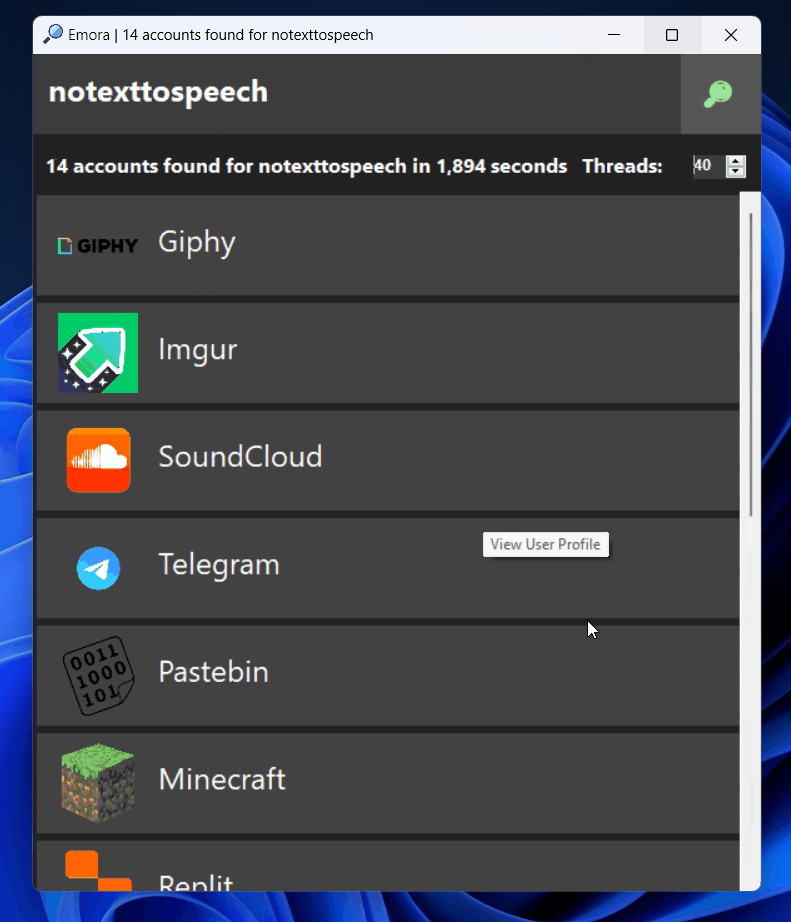
Emora Emora allows you to search for accounts by username across social networks. Inspired by tools like Sherlock, Emora provides a user-friendly graphical interface to ease the usage and navigation through...
NoArgs: Manipulating and Hiding Process Arguments NoArgs is a tool designed to dynamically spoof and conceal process arguments while staying undetected. It achieves this by hooking into Windows APIs to...
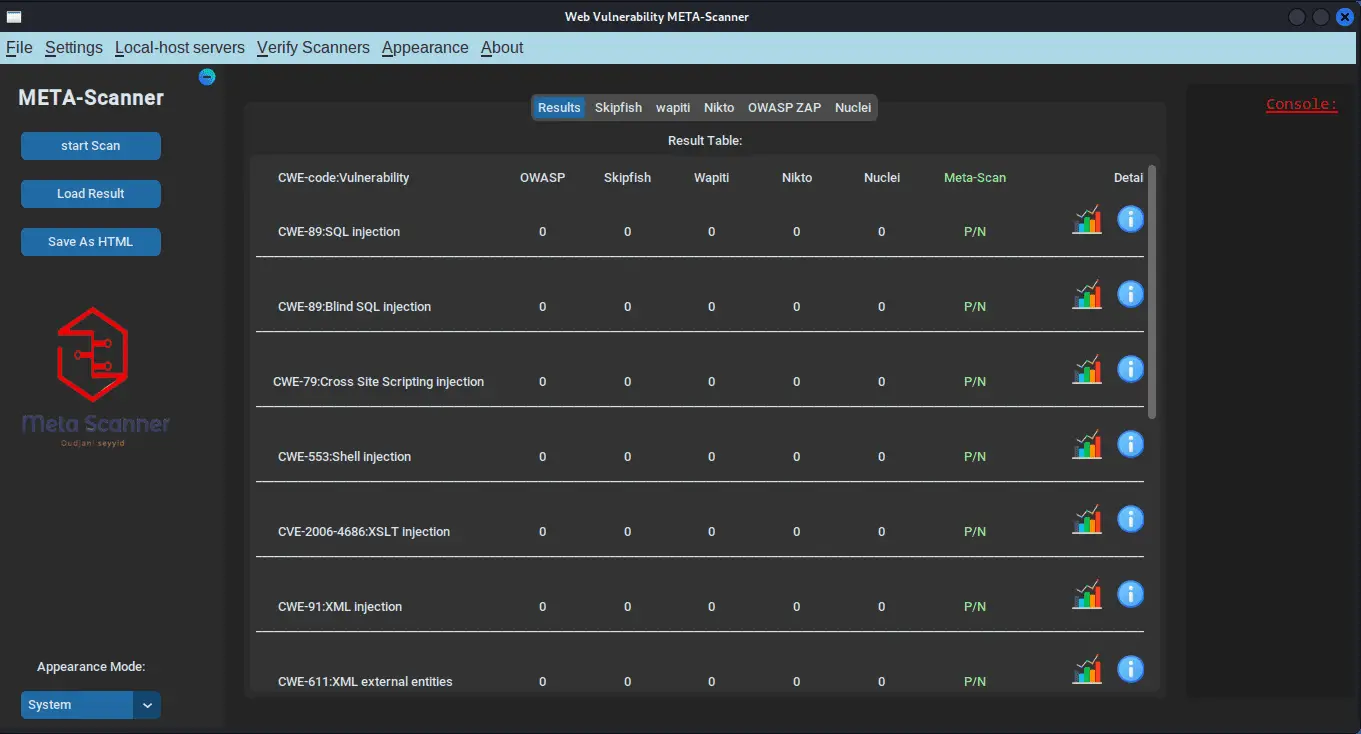
OSTE-Meta-Scanner This project aims to simplify the field of Dynamic Application Security Testing. The OSTE meta scanner is a comprehensive web vulnerability scanner that combines multiple DAST scanners, including Nikto...
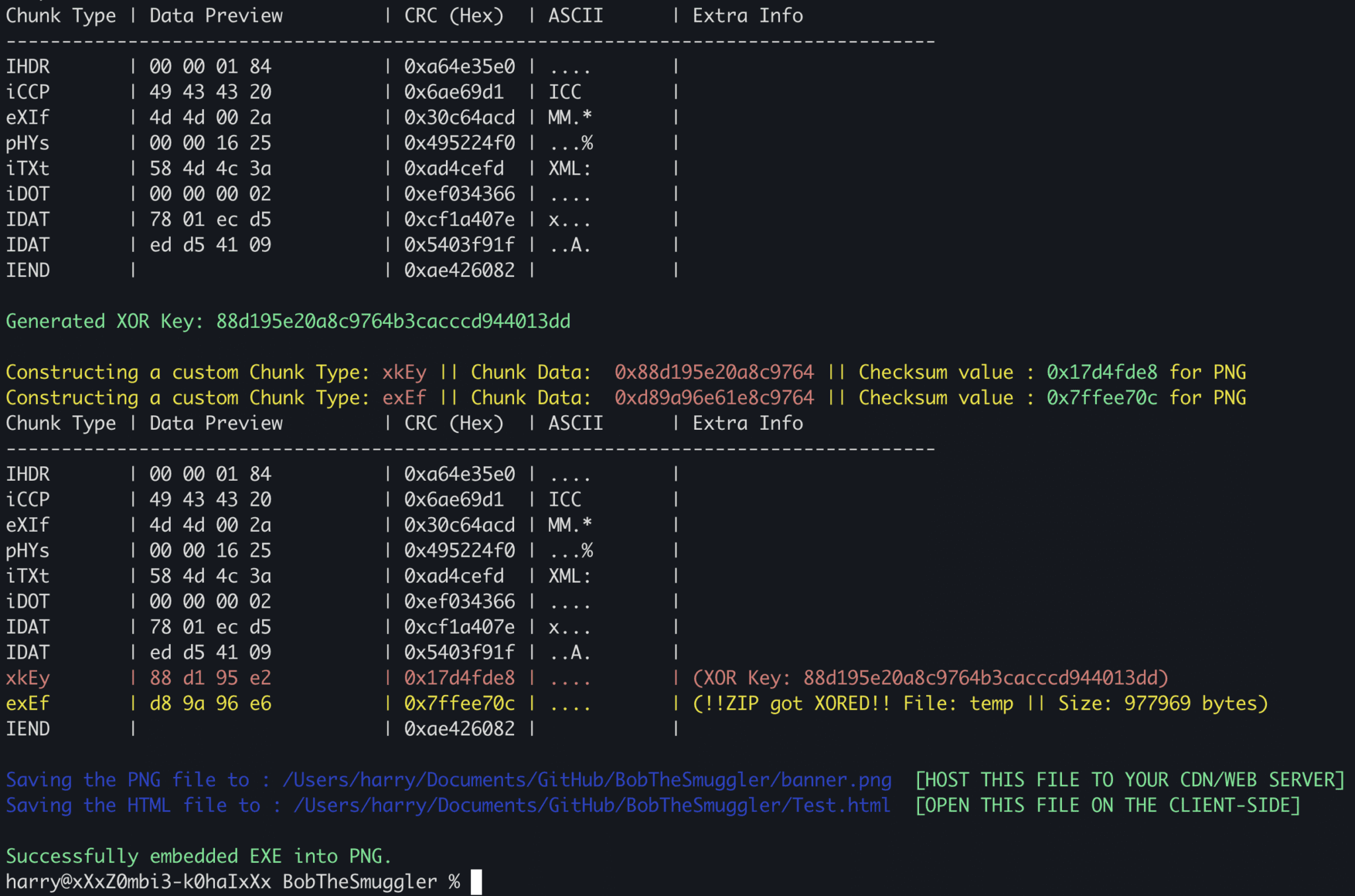
Bob the Smuggler “Bob the Smuggler” is a tool that leverages HTML Smuggling Attack and allows you to create HTML files with embedded 7z/zip archives. The tool would compress your...
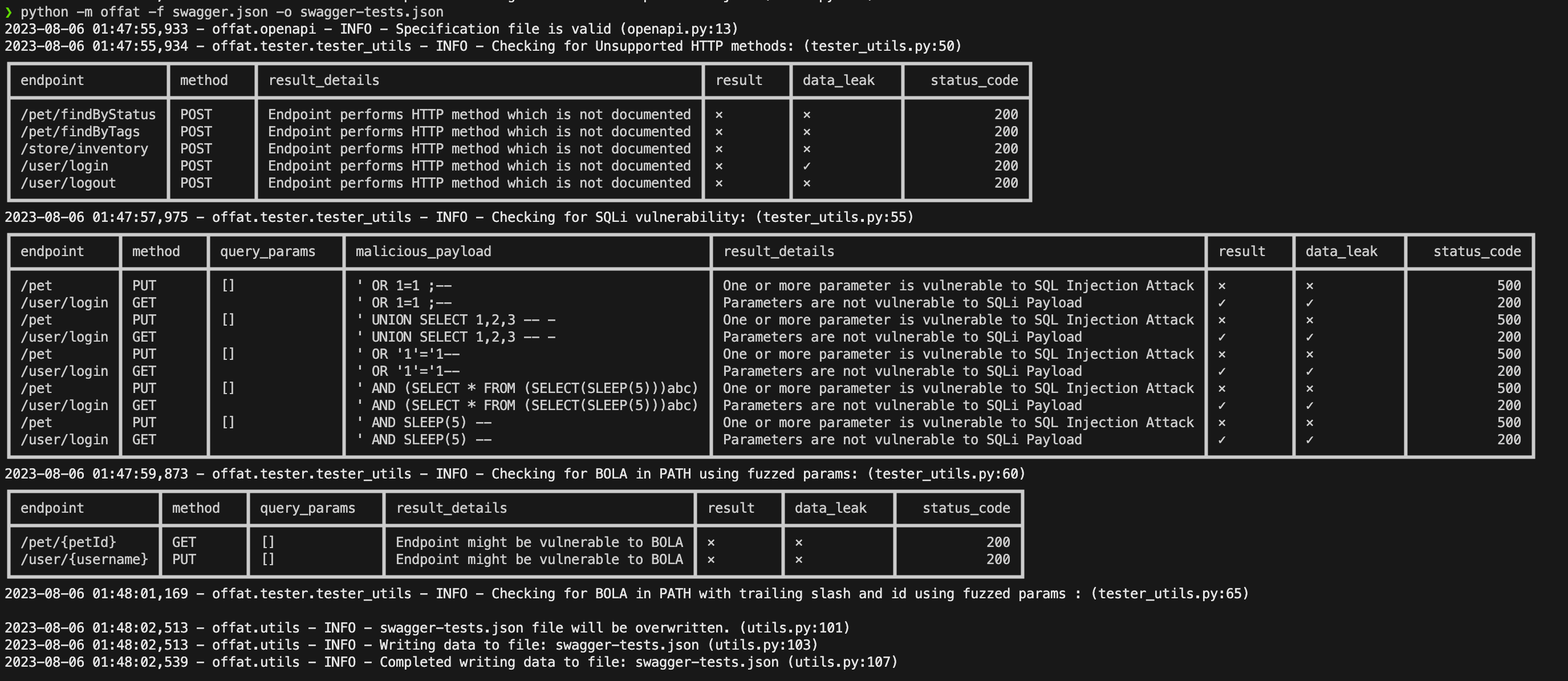
OWASP OFFAT OWASP OFFAT (OFFensive Api Tester) is created to automatically test API for common vulnerabilities after generating tests from the openapi specification file. It provides the feature to automatically...
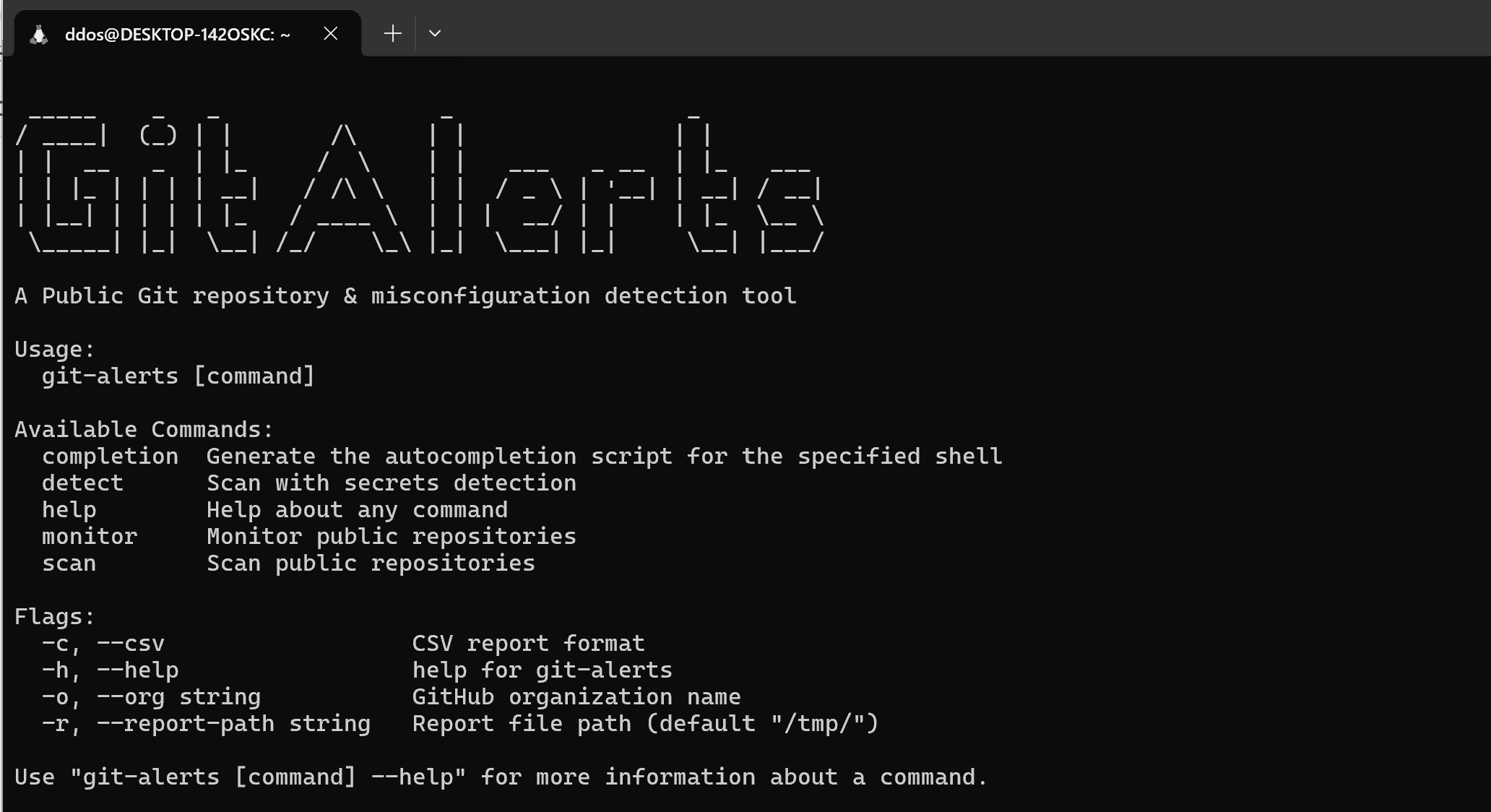
GitAlerts GitHub repositories created under any organization can be controlled by the GitHub administrators. However, any repository created under an organization’s user account is not controllable unless the organization has...
VectorKernel PoCs for Kernelmode rootkit techniques research or education. Currently focusing on Windows OS. All modules support 64-bit OS only. NOTE Some modules use ExAllocatePool2 API to allocate kernel pool...
Shelter Shelter is a completely weaponized sleep obfuscation technique that allows you to fully encrypt your in-memory payload making extensive use of ROP. This crate comes with the following characteristics:...
SiCat – The useful exploit finder SiCat is an advanced exploit search tool designed to identify and gather information about exploits from both open sources and local repositories effectively. With...
APKDeepLens APKDeepLens is a Python-based tool designed to scan Android applications (APK files) for security vulnerabilities. It specifically targets the OWASP Top 10 mobile vulnerabilities, providing an easy and efficient...
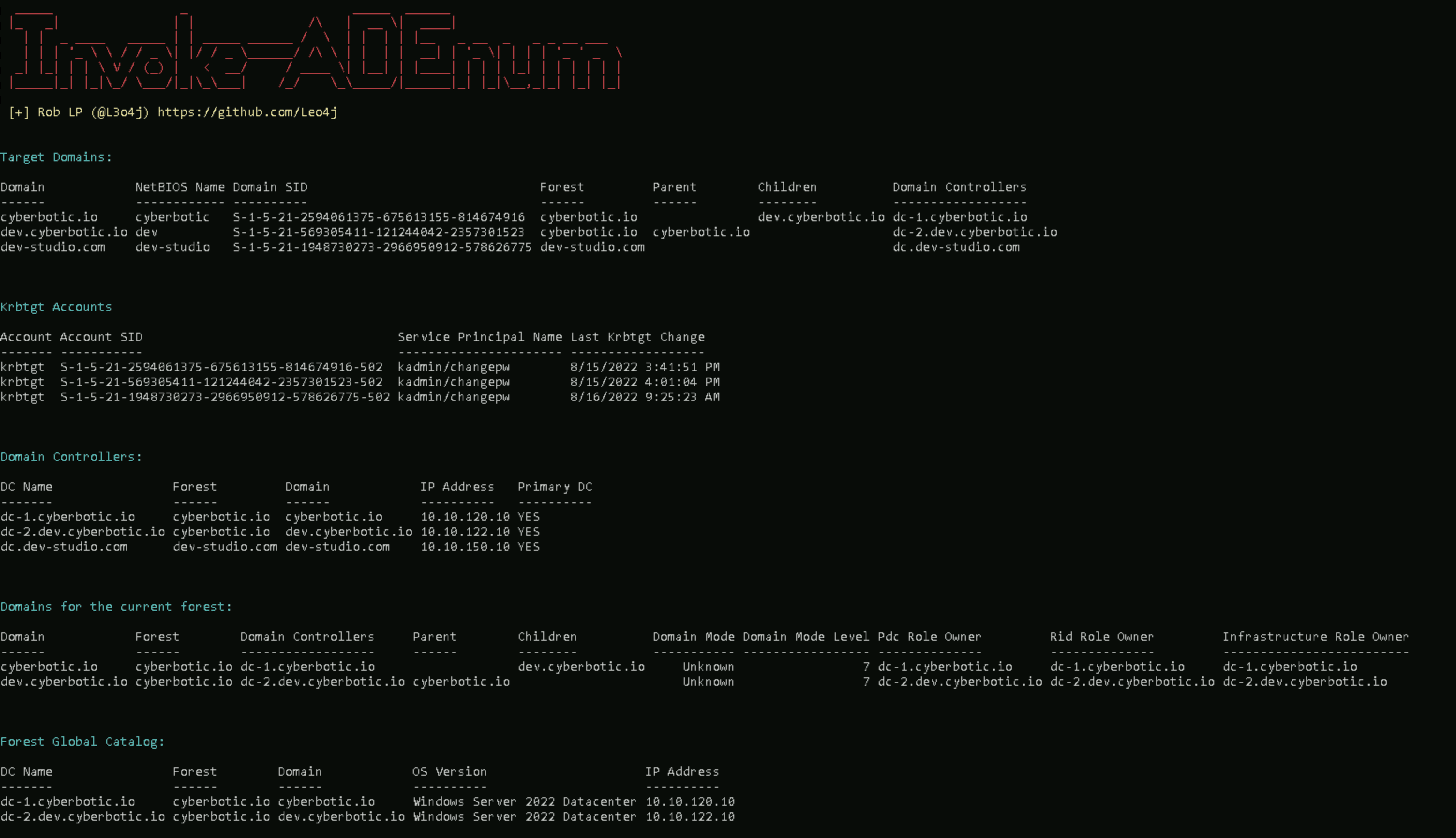
Invoke-ADEnum Active Directory Enumeration Invoke-ADEnum is an Active Directory enumeration tool designed to automate the process of gathering information from an Active Directory environment, leveraging the capabilities of PowerView. With...
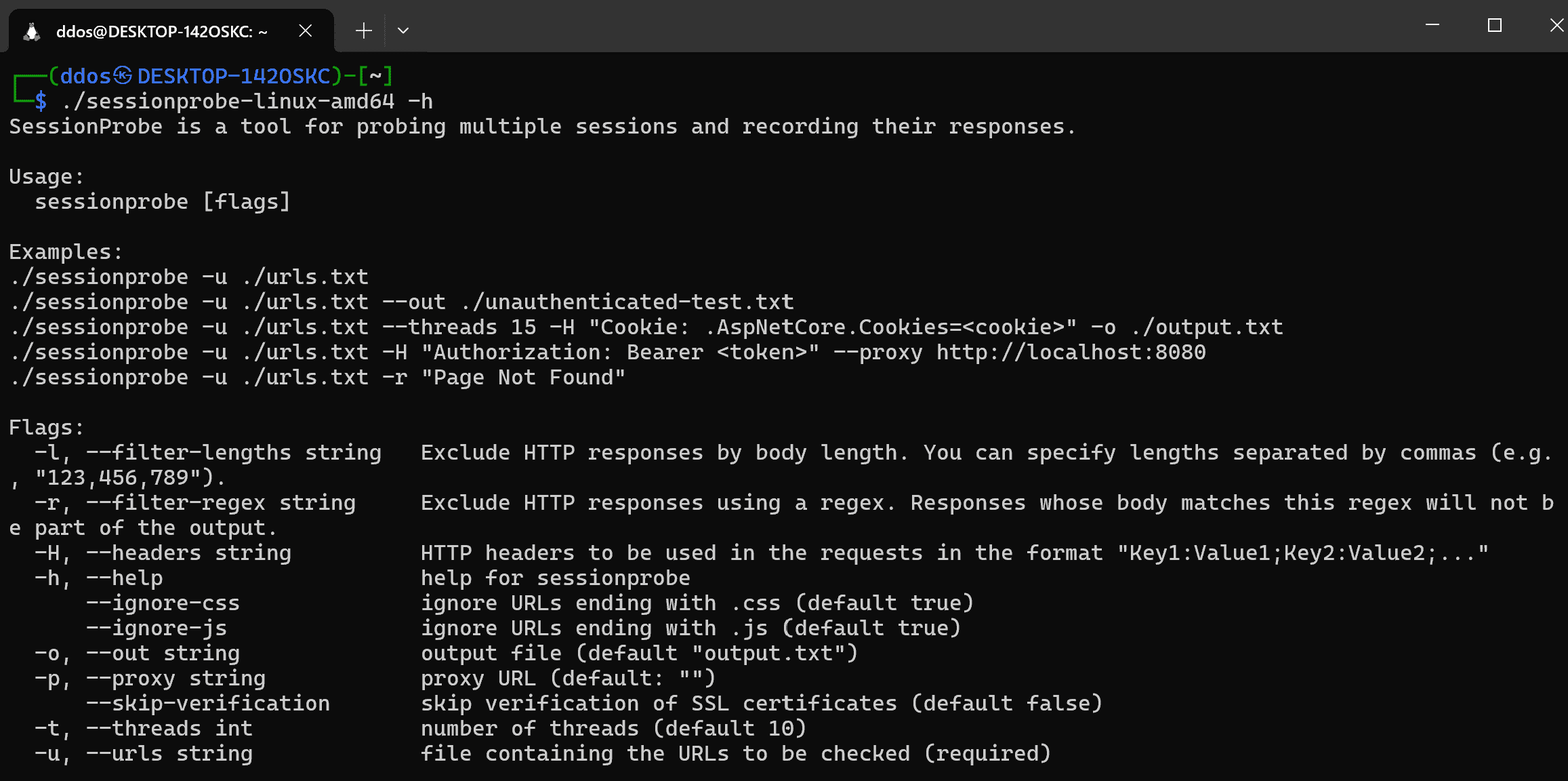
SessionProbe SessionProbe is a multi-threaded pentesting tool designed to assist in evaluating user privileges in web applications. It takes a user’s session token and checks for a list of URLs...
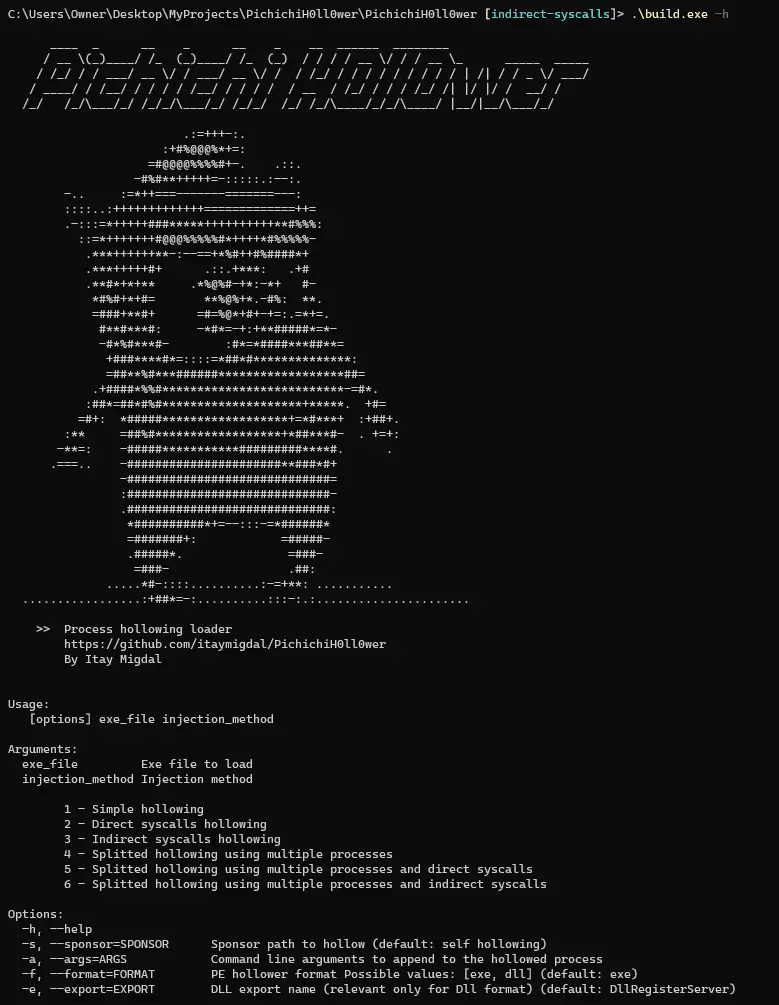
PichichiH0ll0wer Process hollowing loader written in Nim for PEs only PichichiH0ll0wer has some features to protect your payload. Features Configurable builder Payload encrypted and compressed (and optionally splitted) in the...
VMware has released urgent patches addressing multiple critical-severity vulnerabilities in ESXi, Workstation, Fusion, and Cloud Foundation. These flaws center around USB controllers and could allow attackers with local administrative privileges...
EVILRDP – More control over RDP The evil twin of aardwolfgui using the aardwolf RDP client library that gives you extended control over the target and additional scripting capabilities from the command line....