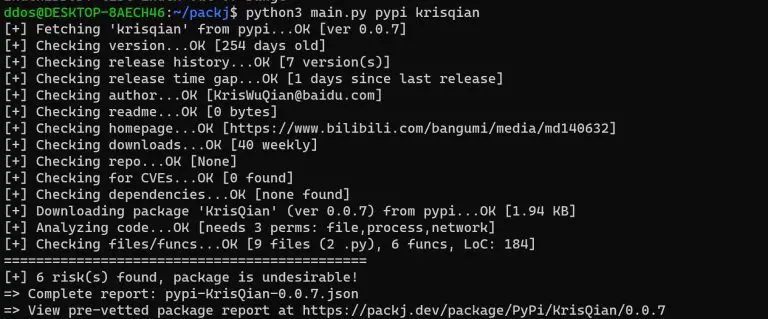
Packj flags malicious/risky open-source packages Packj (pronounced package) is a command-line (CLI) tool to vet open-source software...
Web Vulnerability Analysis
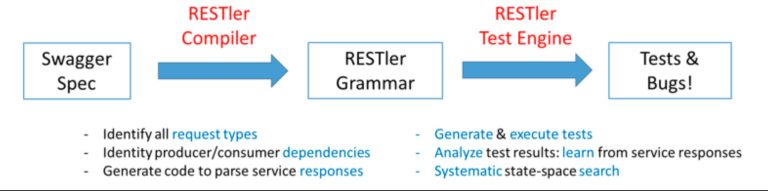
RESTler What is RESTler? RESTler is the first stateful REST API fuzzing tool for automatically testing cloud services through...
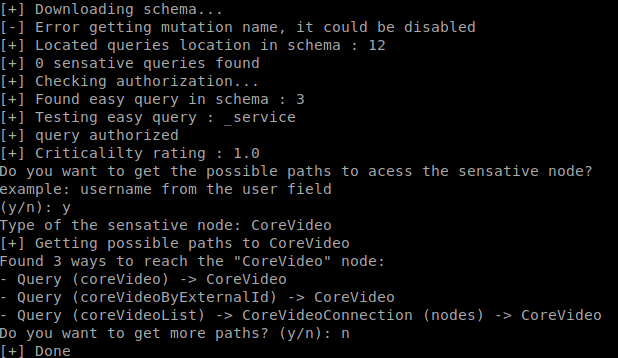
GraphCrawler Graph Crawler is an automated testing toolkit for any GraphQL endpoint. It will run through and...
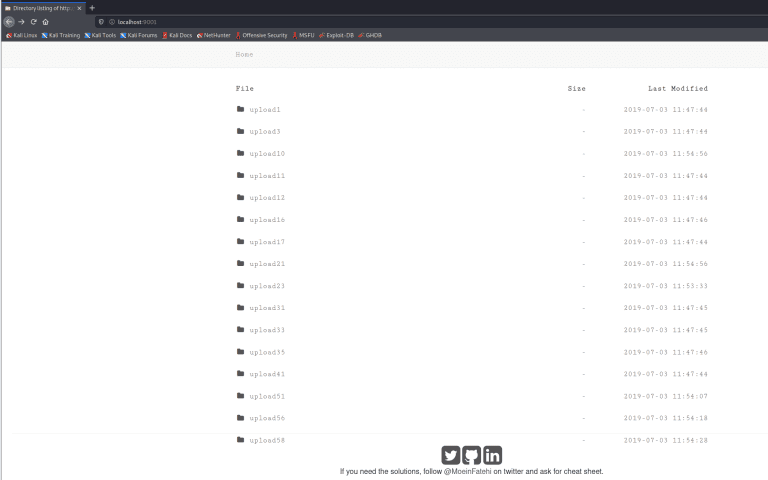
File Upload Vulnerability Scenarios (Challenges) This repository is a dockerized PHP application containing some file upload vulnerability...
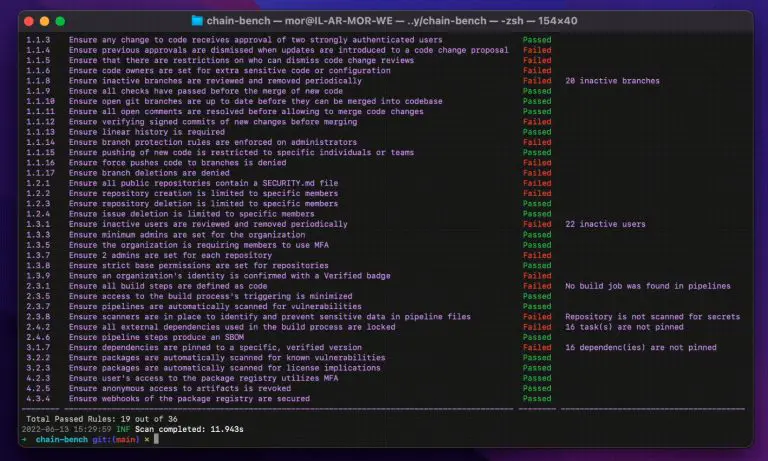
chain-bench Chain-bench is an open-source tool for auditing your software supply chain stack for security compliance based...
XSS Vulnerability Scenarios (challenges) This repository is a Dockerized php application containing some XSS vulnerability challenges. The...
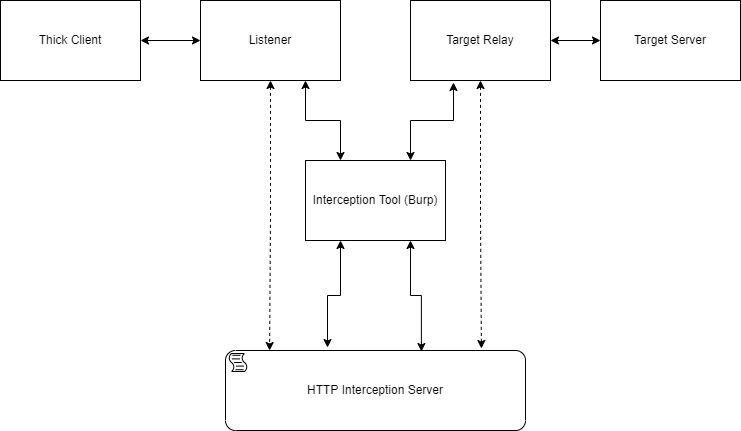
MITM Intercept A little bit less hackish way to intercept and modify non-HTTP protocols through Burp and...
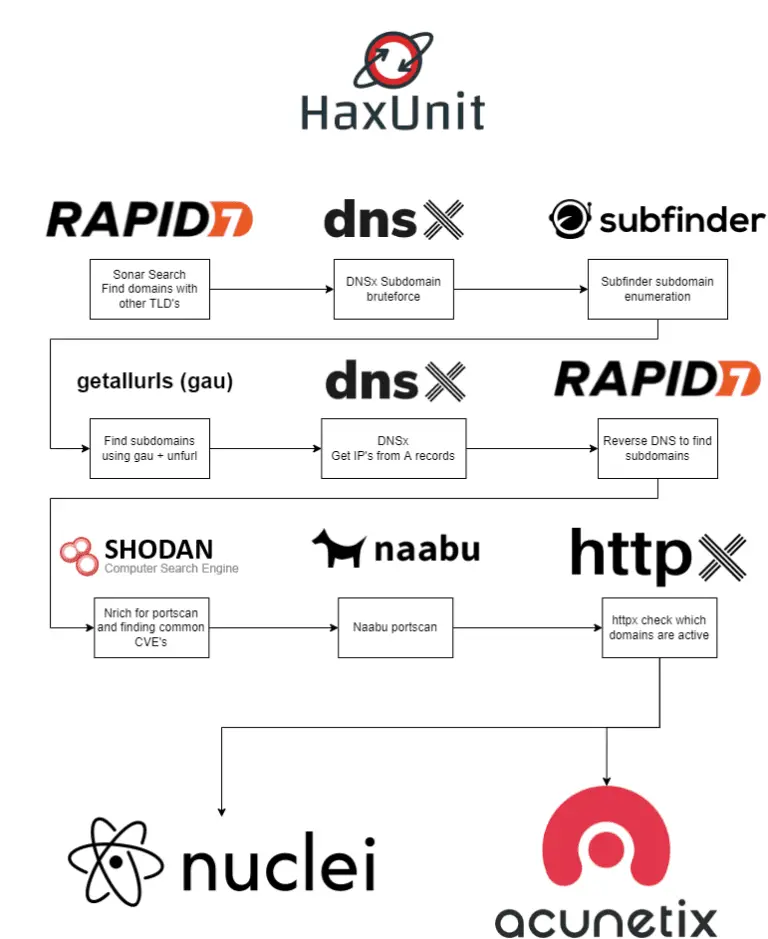
haxunit HaxUnit combines multiple active and passive subdomain enumeration tools and port scanning tools with vulnerability discovery...
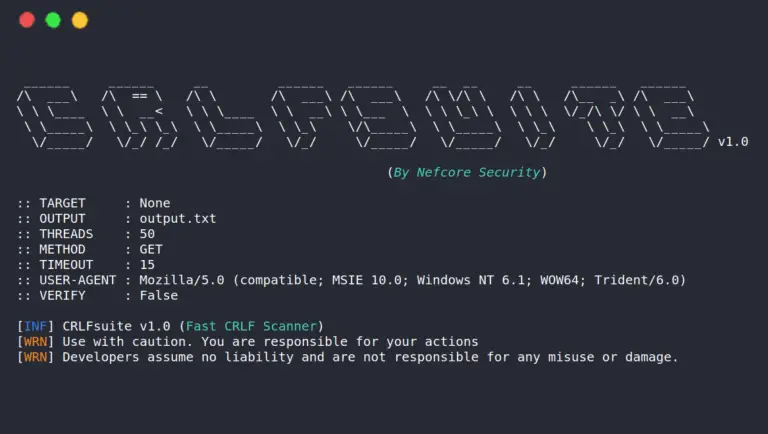
CRLFsuite CRLFsuite is a fast tool specially designed to scan CRLF injection. Features ✔️ Single URL scanning ✔️ Multiple...
Jeeves Jeeves is made for looking to Time-Based Blind SQLInjection through recon. Install > go install github.com/ferreiraklet/Jeeves@latest...
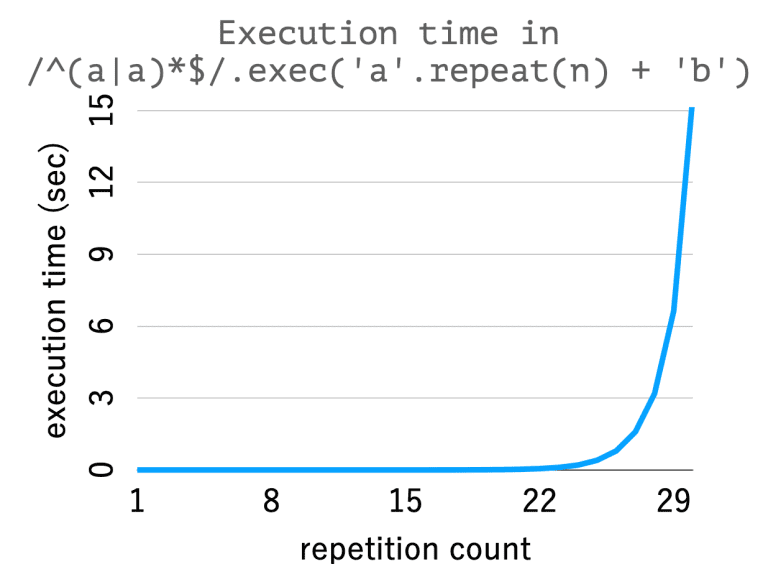
What is ReDoS vulnerability? A regular expression is the most known text processing utility for programmers. There...
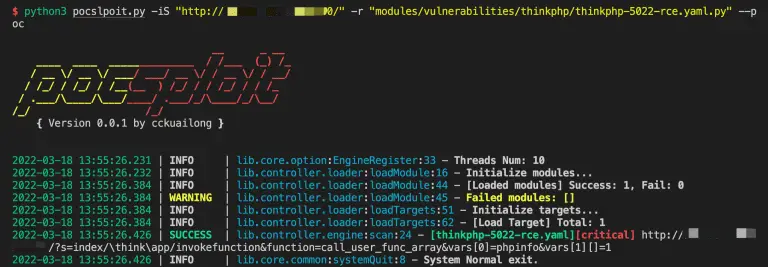
pocsploit pocsploit is a lightweight, flexible, and novel open-source poc verification framework. Pain points of the POC...
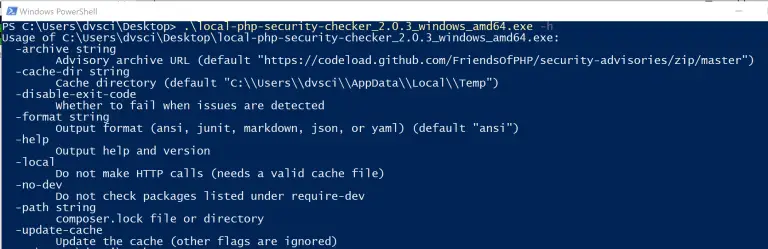
Local PHP Security Checker The Local PHP Security Checker is a command-line tool that checks if your...
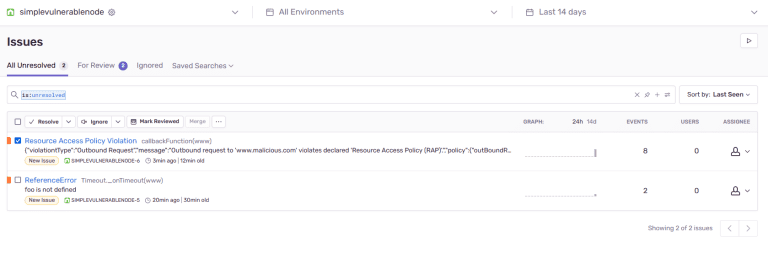
Node Security Shield Node Security Shield (NSS) is a Developer and Security Engineer friendly module for Securing...
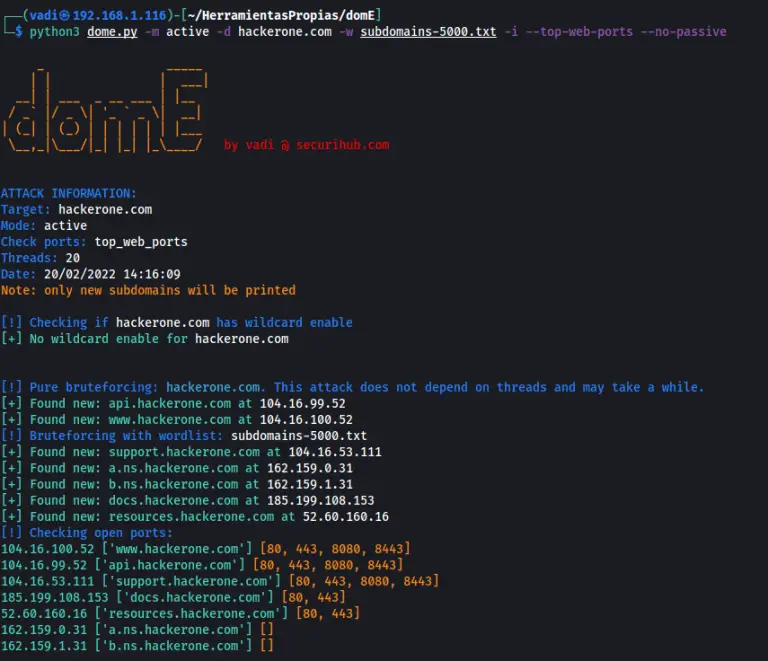
DOME – A subdomain enumeration tool Dome is a fast and reliable python script that makes active...