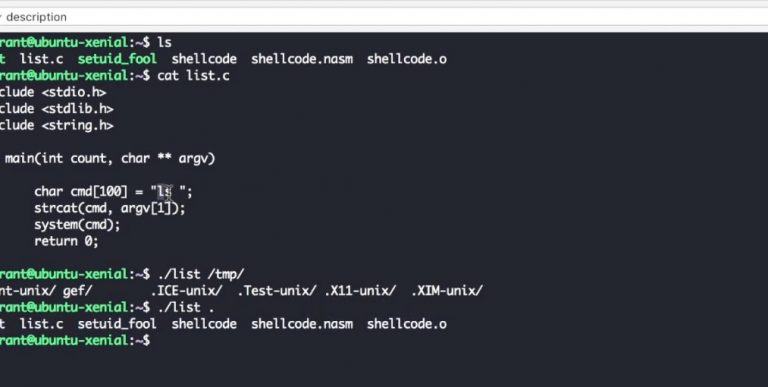
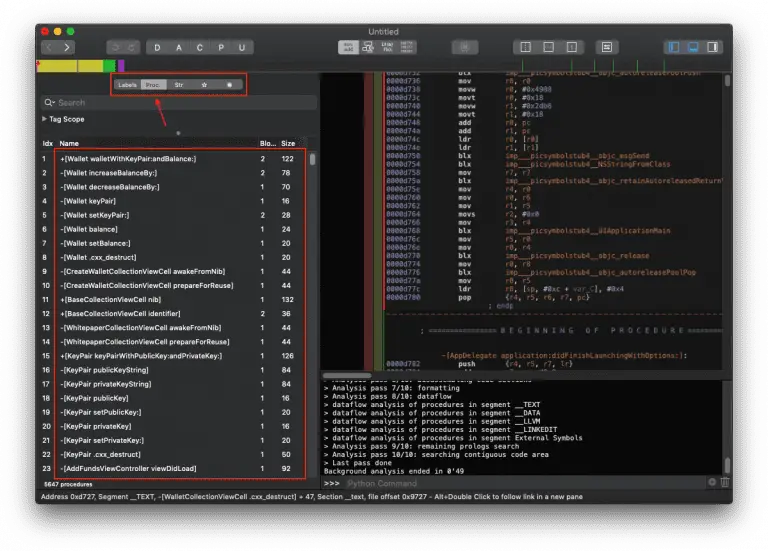
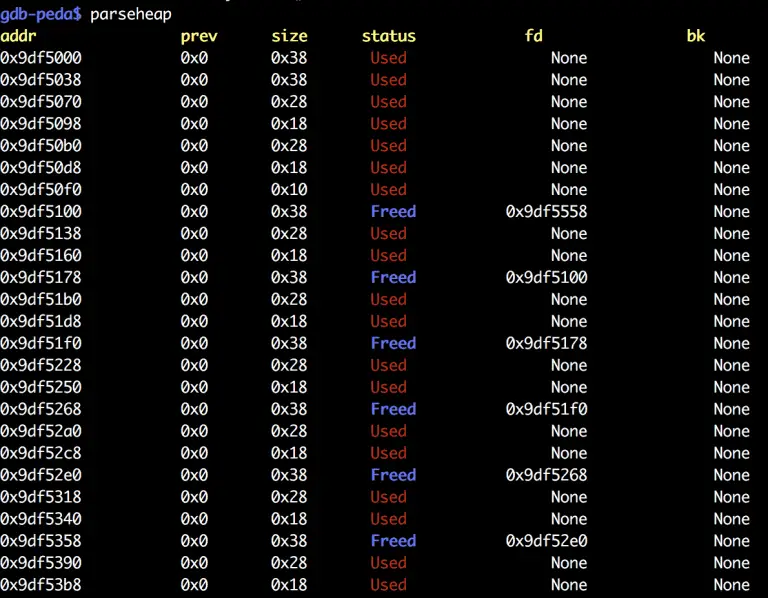
Linux Binary Exploitation Topics Lecture 1. Memory Layout of the C program. ELF binaries. Overview of the...
Reverse Engineering
Reverse Engineering iOS Applications Welcome to my course Reverse Engineering iOS Applications. If you’re here it means...
ReverseAPK Quickly analyze and reverse engineer Android applications. FEATURES: Displays all extracted files for easy reference Automatically...
GEF – GDB Enhanced Features GEF is a kick-ass set of commands for X86, ARM, MIPS, PowerPC...
Pwngdb GDB for pwn. Features libc : Print the base address of libc ld : Print the base address...
The Carnegie Mellon University Binary Analysis Platform (CMU BAP) is a reverse engineering and program analysis platform...
>_ Root the Box Root the Box is a real-time capture the flag (CTF) scoring engine for...
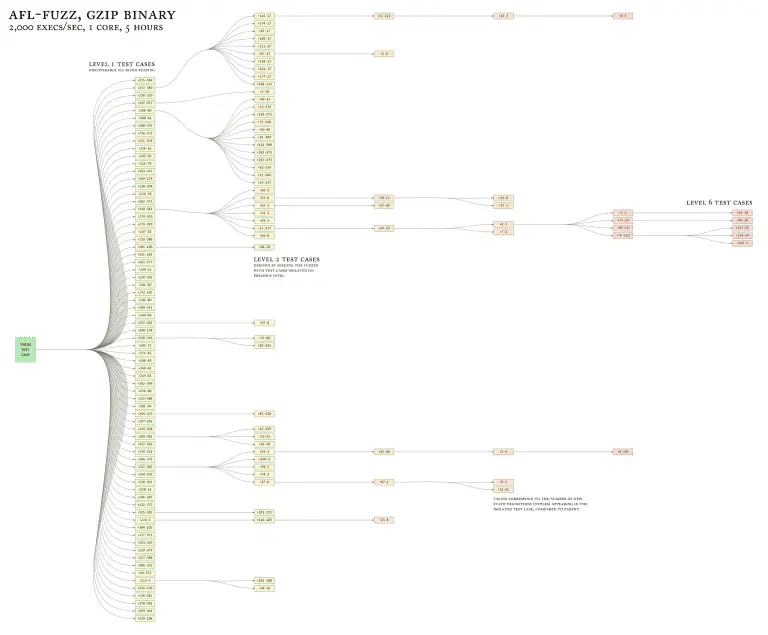
drAFL Original AFL supports black-box coverage-guided fuzzing using QEMU mode. Fuzzing is one of the most powerful...
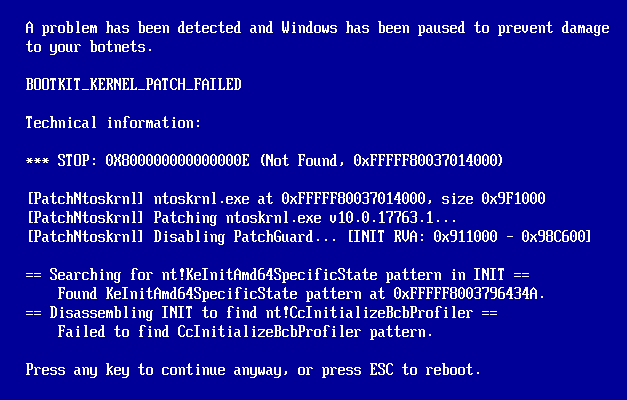
EfiGuard is a portable x64 UEFI bootkit that patches the Windows boot manager, boot loader, and kernel...
Zeratool Automatic Exploit Generation (AEG) and remote flag capture for exploitable CTF problems This tool uses angr to concolically...
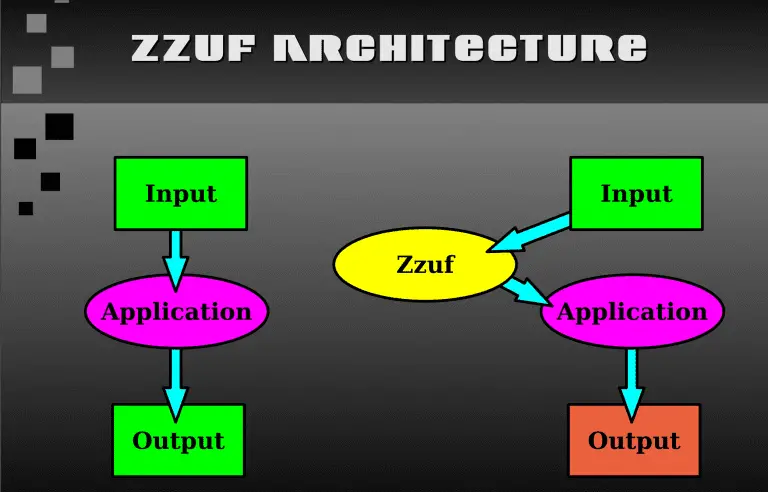
zzuf zzuf is a transparent application input fuzzer. Its purpose is to find bugs in applications by...
RetDec is a retargetable machine-code decompiler based on LLVM. The decompiler is not limited to any particular target architecture,...
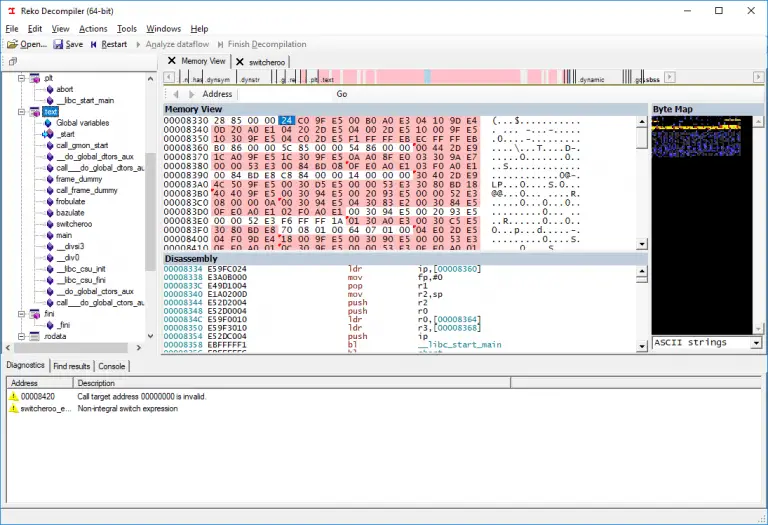
reko Reko (Swedish: “decent, obliging”) is a C# project containing a decompiler for machine code binaries. This project...
Radamsa Radamsa is a test case generator for robustness testing, a.k.a. a fuzzer. It is typically used...
PLASMA PLASMA is an interactive disassembler. It can generate a more readable assembly (pseudo code) with colored...