Category: Tips and Tricks
Dockernymous is a start script for Docker that runs and configures two individual Linux containers in order act as an anonymization workstation-gateway set up. It’s aimed towards experienced Linux/Docker users,...
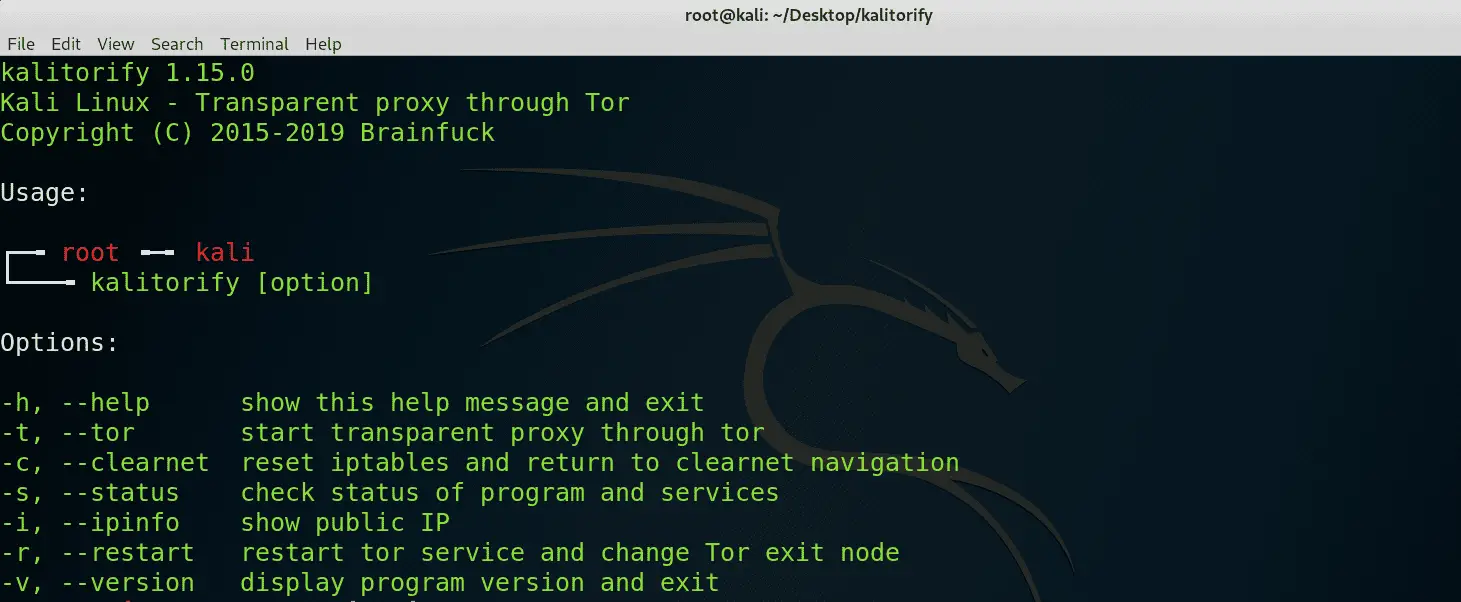
kalitorify kalitorify is a shell script for Kali Linux which use iptables settings to create a transparent proxy through Tor Network, the program also allows you to perform various checks like checking the Tor...
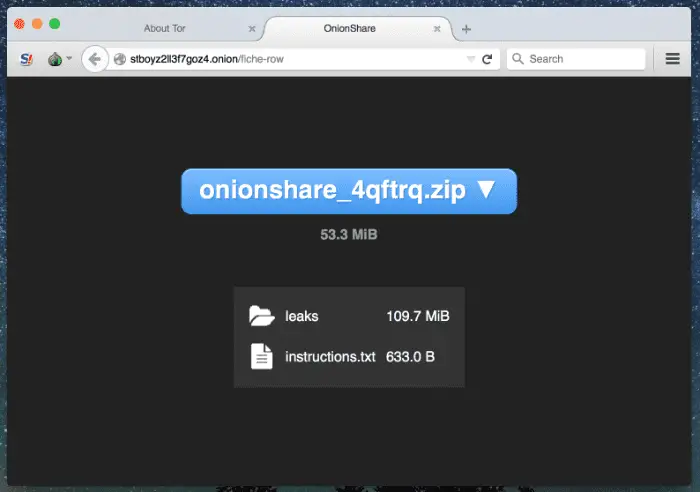
OnionShare OnionShare lets you securely and anonymously share files of any size. It works by starting a web server, making it accessible as a Tor onion service, and generating an...
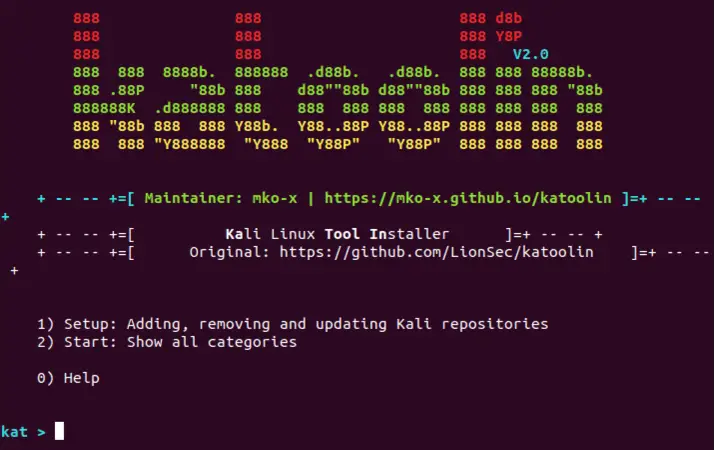
katoolin Command line interface (CLI) to install Kali Linux Tools in your desired distribution. Target Provide Kali Linux Tools to other Linux distributions. Features Install script Uninstall script Bulk install...
fetch-some-proxies Simple Python script for fetching “some” (usable) proxies. It fetches (daily) list of public proxies and automatically finds in a quick manner those usable in that same moment (Note:...
orjail a more secure way to force programs to exclusively use tor network. why? we’ve tried to deanonymize a program executed in torsocks environment and that was not so difficult...
Tor Router Tor Router is a SOCKS5, DNS and HTTP proxy server for distributing traffic across multiple instances of Tor. At startup, Tor Router will run an arbitrary number of instances...
With the development of the Internet, personal information is becoming more and more transparent. Yet, there are measures that are adopted by professional companies. They range from securing personal details...
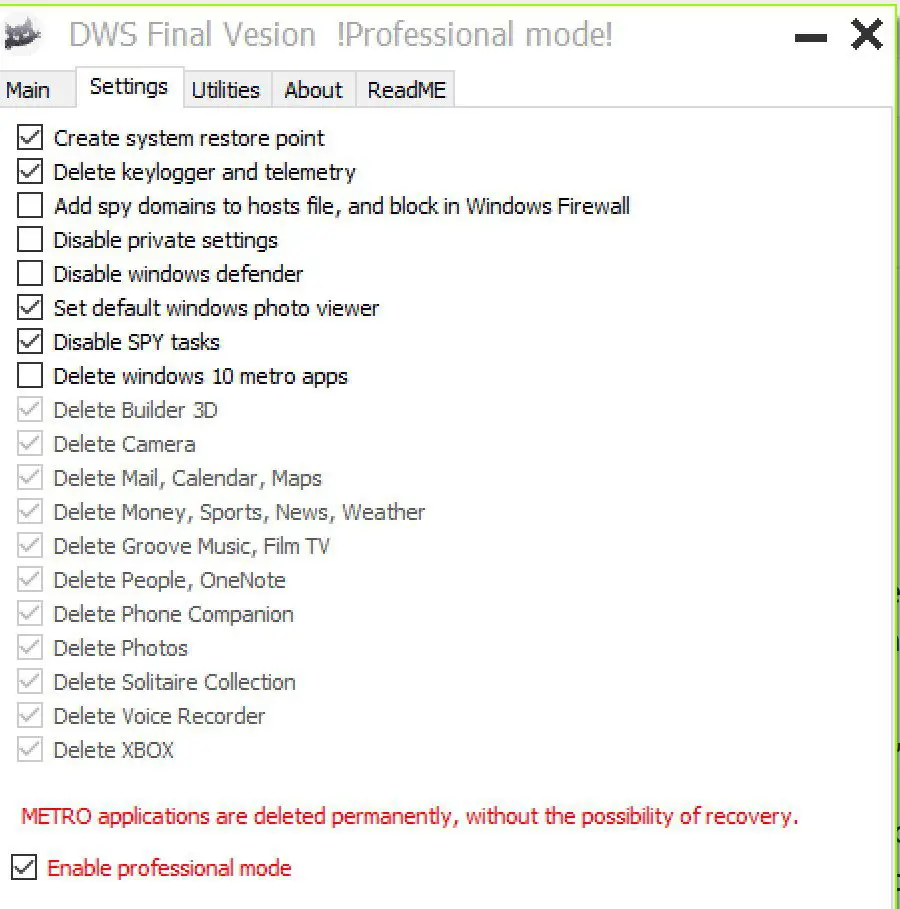
Destroy Windows 10 Spying This program destroys spying on Windows 7/8/8.1/10. This program completely destroys spying. Removes some elements of telemetry and the other turns off, disables Windows Defender, Cortana,...
spoof Easily spoof your MAC address in macOS, Windows, & Linux! Node.js port of the popular SpoofMAC Python utility. Why? I made this because changing your MAC address on macOS is harder...
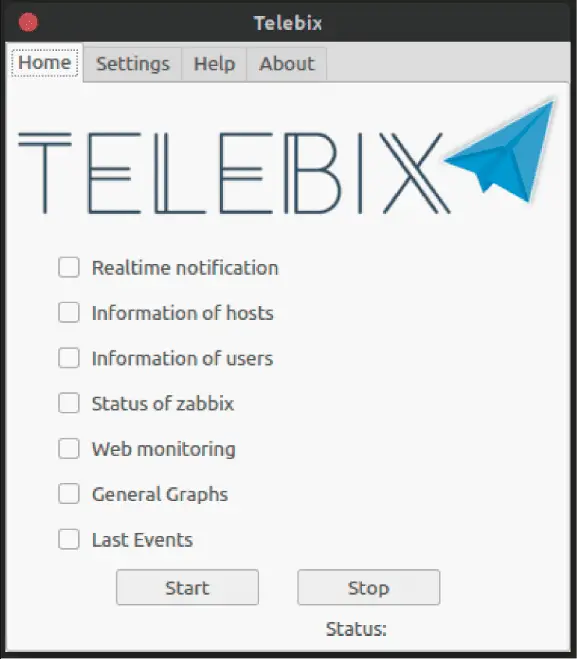
Telebix Telebix is an application that communicates with a Bot on the Telegram to receive commands and send information from an infrastructure monitored by Zabbix, which also sends messages in...
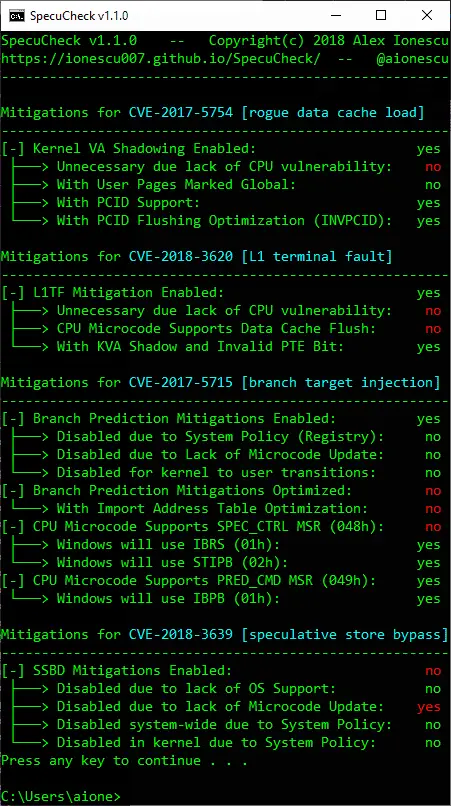
SpecuCheck is a Windows utility for checking the state of the software and hardware mitigations against CVE-2017-5754 (Meltdown), CVE-2017-5715 (Spectre v2), CVE-2018-3260 (Foreshadow), and CVE-2018-3639 (Spectre v4). It uses two...
GhostInTheChaos Chaotic Crypto Stealth VPN for Anonymity and Untraceable Hacking Attacks with Linux and Android. Properties: Protects client from sniffing and tracing Protects server from attacks and scanning Bypasses censorship...
Linux has long been used as an operating system, powering everything from supercomputers to smartphones. For those who have been in the Microsoft or Apple systems for a long time,...
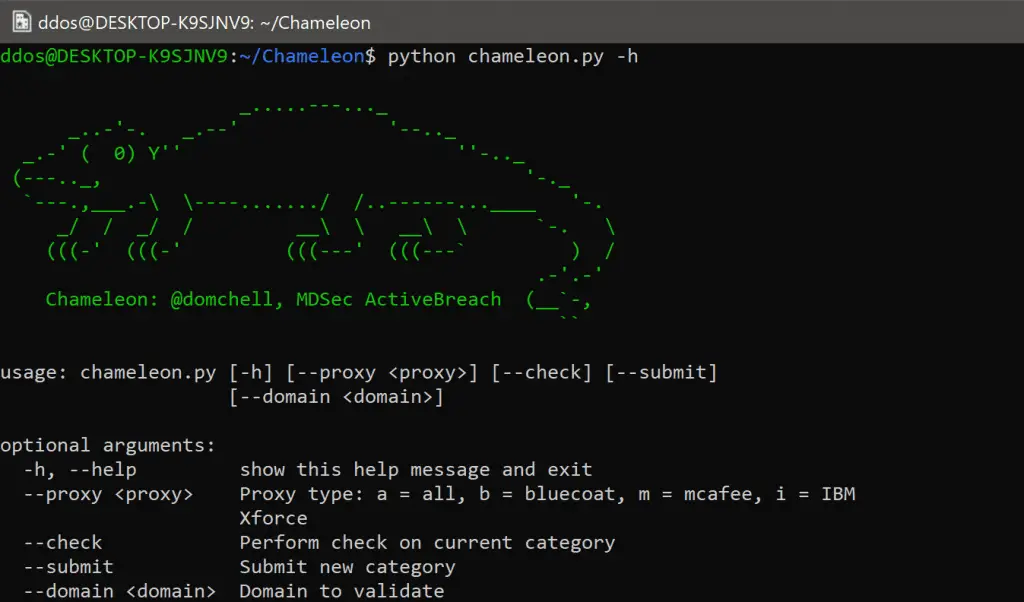
Chameleon is a tool which assists red teams in categorising their infrastructure under arbitrary categories. Currently, the tool supports arbitrary categorisation for Bluecoat, McAfee Trustedsource and IBM X-Force. However, the...