Security researcher published the technical details and a proof-of-concept exploit for a vulnerability in Linux kernel—CVE-2024-53141, having a CVSS score of 7.8 for a serious out-of-bounds (OOB) access flaw in the netfilter subsystem’s ipset component. Tracked back to a subtle bug in the bitmap_ip_uadt function, this vulnerability provides threat actors with a powerful exploit chain that can ultimately lead to privilege escalation, KASLR bypass, and full kernel-level code execution.
The root cause of CVE-2024-53141 lies in the bitmap_ip_uadt function within the ipset component. The vulnerability occurs due to a missing range check when handling IPSET_ATTR_CIDR parameters.
In certain conditions, specifically when tb[IPSET_ATTR_IP_TO] is not present but tb[IPSET_ATTR_CIDR] exists, the values of ip and ip_to are swapped, and a critical range check for ip is omitted. This oversight can lead to out-of-bounds memory access.
The out-of-bounds access vulnerability can allow attackers to manipulate memory outside of the intended boundaries, potentially leading to various security consequences, including:
- Kernel crashes
- Privilege escalation
- Arbitrary code execution
The report outlines a multi-stage exploitation process, including:
- Heap Leak via OOB Write
By crafting a malicious e.id during a comment initialization path (ip_set_init_comment()), the attacker can leak kernel heap addresses by causing writes into adjacent heap chunks such as socket buffers.
- OOB Write with Arbitrary Values
A second primitive enables an attacker to set crafted values to memory outside valid bounds via manipulated counters (ip_set_init_counter()), allowing attackers to alter control structures on the heap.
- Use-After-Free via msg_msgseg
Through clever memory layout manipulation using msg_msgseg, attackers convert the OOB condition into a use-after-free, reclaiming freed kernel memory and preparing the way for hijacking control flow.
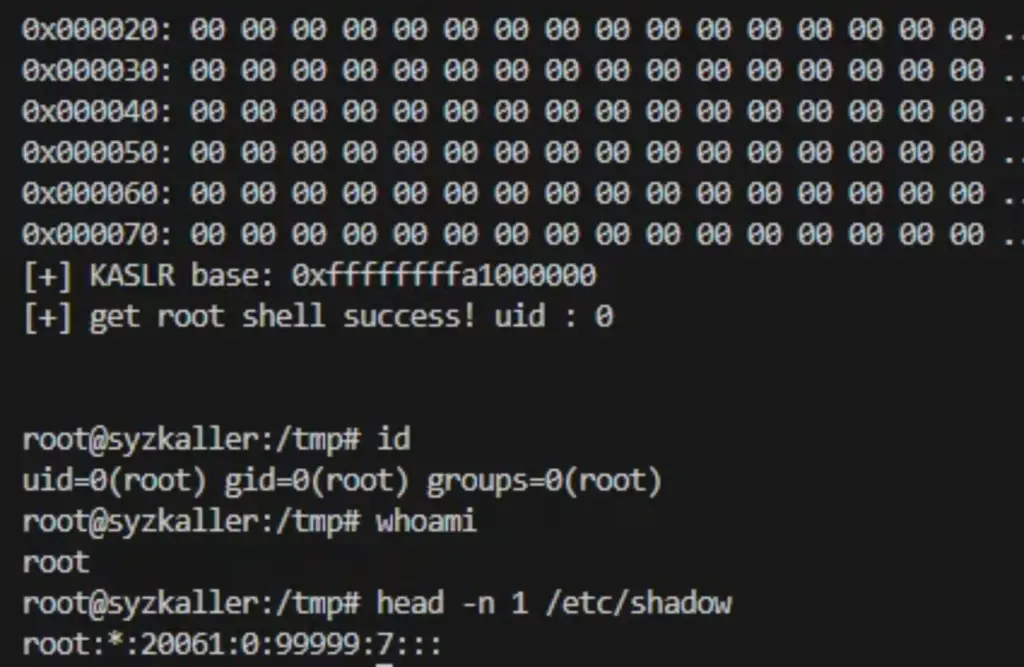
The exploitation doesn’t stop at memory corruption. With the heap leak primitive, attackers calculate the base address of the kernel and overwrite control structures such as pipe_buffer->ops.
The final payload uses a classic core_pattern technique, overwriting the kernel string that determines what gets executed upon a process crash. By pointing core_pattern to a user-controlled binary, the attacker achieves root shell execution.
This vulnerability affects versions v2.7 through v6.12 of the kernel. A working PoC is already available on GitHub.
To address this vulnerability, it is crucial to update the Linux kernel to a patched version where the missing range check has been implemented.
Related Posts:
- Synology Patches Serious Bugs in DiskStation Manager
- Linux Kernel Vulnerability Exposes Local Systems to Privilege Escalation, PoC Published
