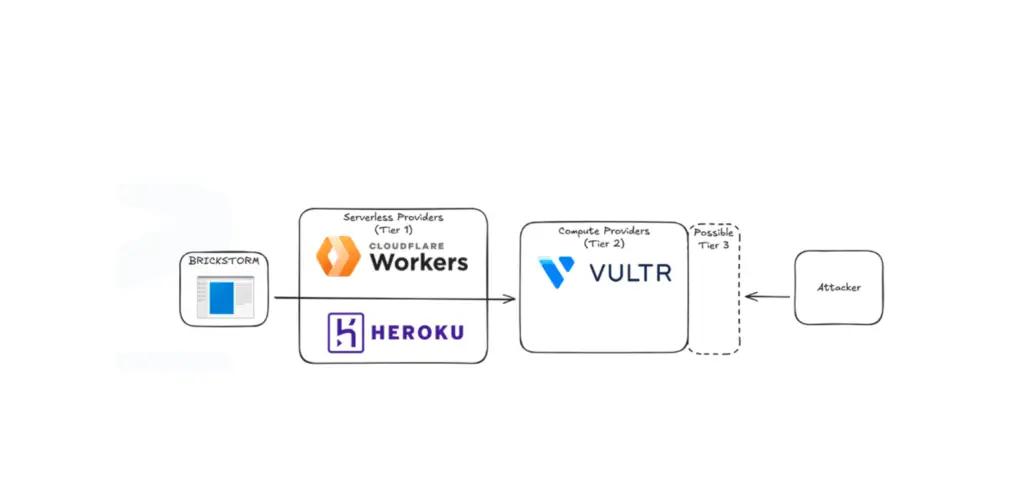
BRICKSTORM's assumed multi-tiered architecture | Image: NISO
In a recent technical expose, NVISO sheds light on BRICKSTORM, a stealthy espionage backdoor attributed to the China-nexus threat cluster UNC5221, which has now evolved to target Windows environments after previously appearing in Linux-based campaigns. According to NVISO, these new BRICKSTORM variants have been active in long-running espionage operations since at least 2022, specifically against European sectors of strategic importance to the People’s Republic of China (PRC).
“Over the past years, the number of persistent intrusions attributed to China-nexus actors has drastically increased… [they] employ a high degree of discretion, enabling the actors to remain undetected for extended duration,” NVISO writes.
The Windows-based samples analyzed were written in Go 1.13.5 and exhibited no export functions, relying instead on scheduled tasks for persistence. They offered two primary capabilities:
- A file manager with a UI and API supporting file uploads, deletions, downloads, renaming, and directory browsing
- Network tunneling using TCP, UDP, and ICMP, enabling lateral movement via protocols like RDP and SMB
Interestingly, NVISO notes that these versions omit direct command execution, instead leveraging tunneling with valid credentials, a design decision likely meant to evade endpoint detection tools that monitor process spawning.
“The avoidance of command execution directly from the backdoor is suspected to be a deliberate choice in order to evade detection…” NVISO explains.
BRICKSTORM employs sophisticated Command & Control (C2) mechanisms, with communications routed through Cloudflare Workers and Heroku apps. It resolves its C2 domains using DNS over HTTPS (DoH) via Quad9, NextDNS, Cloudflare, and Google, effectively bypassing DNS monitoring.
Once connected, BRICKSTORM establishes a three-layered TLS tunnel:
- HTTPS to the reverse proxy (e.g., Cloudflare)
- A nested TLS session inside the WebSocket
- A third TLS session for issuing specific commands
“This TLS-in-TLS approach defeats monitoring opportunities at both victim organizations… and 1st-tier cloud providers,” NVISO states.
The use of Yamux multiplexing allows multiple simultaneous C2 sessions, enabling attackers to manage file transfers and tunneling operations in parallel.
NVISO’s monitoring revealed BRICKSTORM’s multi-tier architecture. Front-end infrastructure like ms-azure.azdatastore.workers.dev proxies traffic to 2nd-tier servers, often hosted on Vultr and obfuscated using nip.io. These systems sometimes reveal default HTTP 404 pages as lures.
“The usage of such providers obfuscates BRICKSTORM’s infrastructure… distinguishing between legitimate and malicious usage poses a challenge.” NVISO notes.
NVISO provides detection and hunting rules using YARA, Suricata, and Microsoft Defender KQL queries. Key recommendations include:
- Blocking DNS over HTTPS providers
- Implementing TLS inspection to detect nested TLS
- Auditing for long-running, rare processes accessing public IPs
Indicators of Compromise (IoCs) and TLS certificates are appended for proactive defense.
BRICKSTORM exemplifies the evolving tactics of Chinese cyber-espionage groups. Its ability to remain undetected, abuse public cloud infrastructure, and adapt across platforms underscores the need for robust threat detection and proactive infrastructure monitoring.
“These recent discoveries… highlight the need for at-risk industries to bolster their security posture and continuously audit their environment,” NVISO concludes.
Related Posts:
- Black Basta Exploits Microsoft Teams for Phishing Attacks
- Stealthy Backdoors: SparkCockpit & SparkTar Remain Undetected
- DNS Tunneling: The Hidden Threat Exploited by Cyberattackers