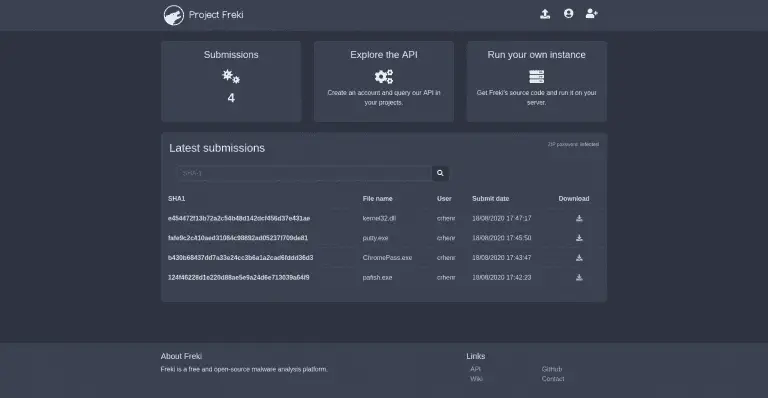
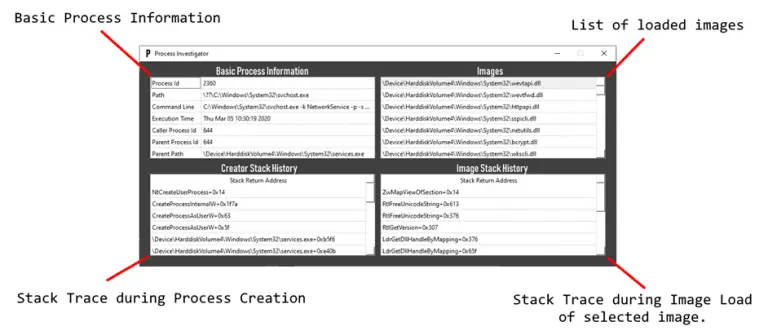
freki Freki is a free and open-source malware analysis platform. Goals Facilitate malware analysis and reverse engineering;...
Malware Analysis
ThreatPursuit-VM Threat Pursuit Virtual Machine (VM): A fully customizable, open-sourced Windows-based distribution focused on threat intelligence analysis...
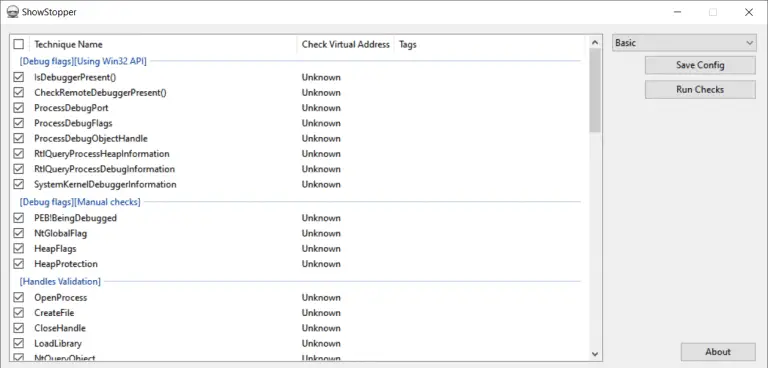
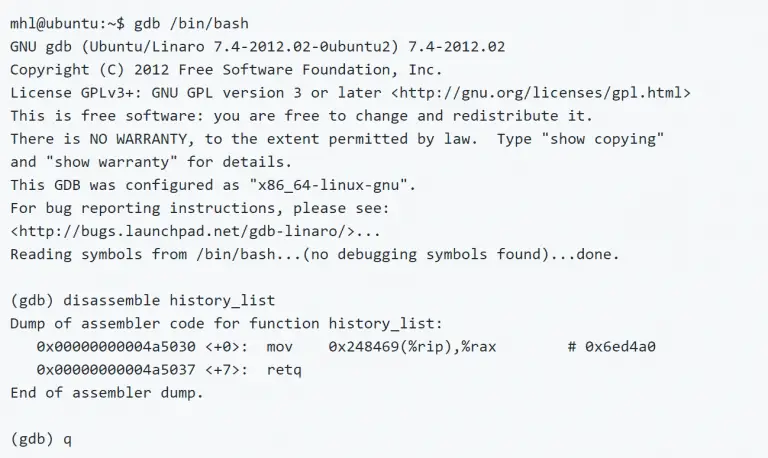
ShowStopper – Anti-Debug tricks exploration tool The ShowStopper project is a tool to help malware researchers explore and test...
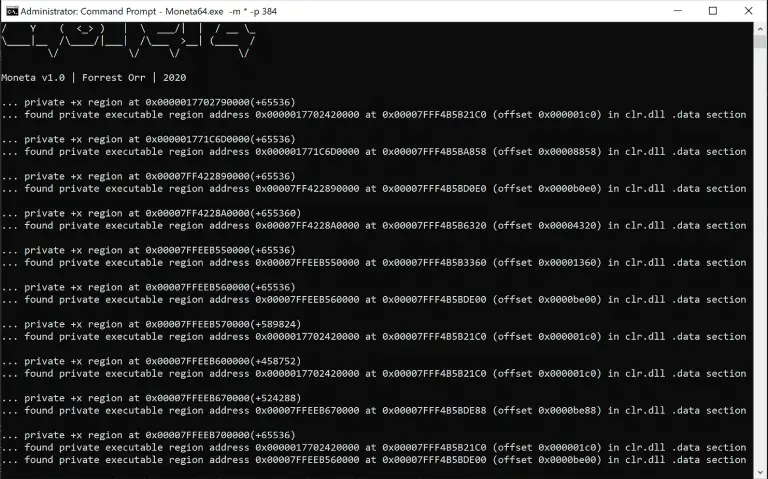
Moneta Moneta is a live usermode memory analysis tool for Windows with the capability to detect malware...
kraken Kraken is a simple cross-platform Yara scanner that can be built for Windows, Mac, FreeBSD, and...
VT Code Similarity Yara Generator Yara rule generator using VirusTotal code similarity feature code-similar-to: This Yara generator is...
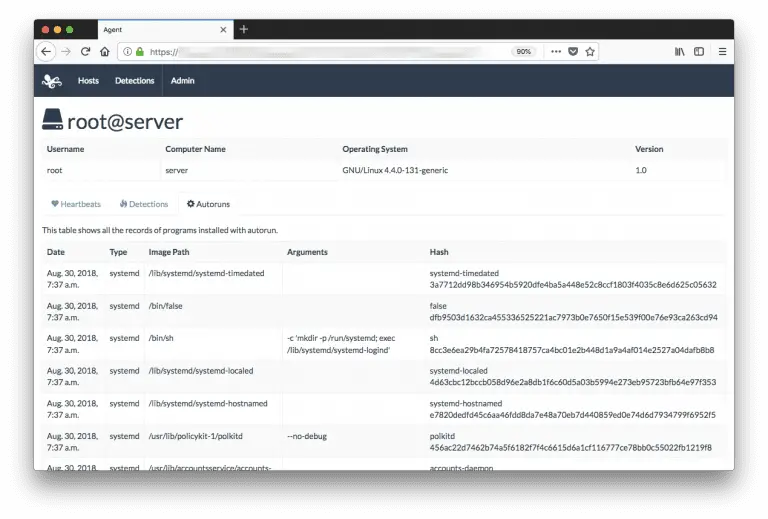
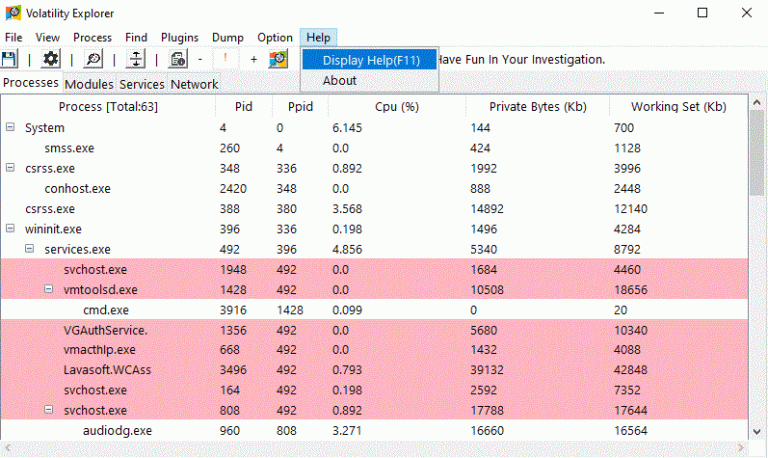
Vol3xp, Volatility 3 Explorer Plugins RAMMap -> Physical Address Mapping (pfn.py) RAMMap (very similar to Rammap [SysInternals]),...
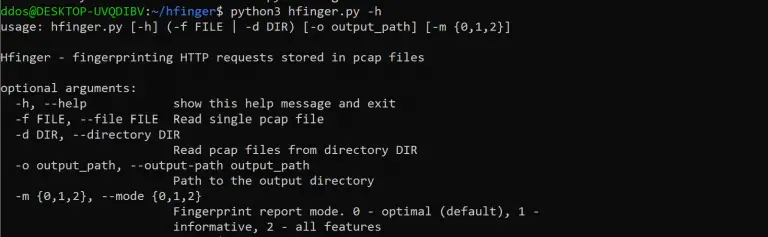
Hfinger – fingerprinting HTTP requests Tool for fingerprinting HTTP requests of malware. Based on Tshark and written...
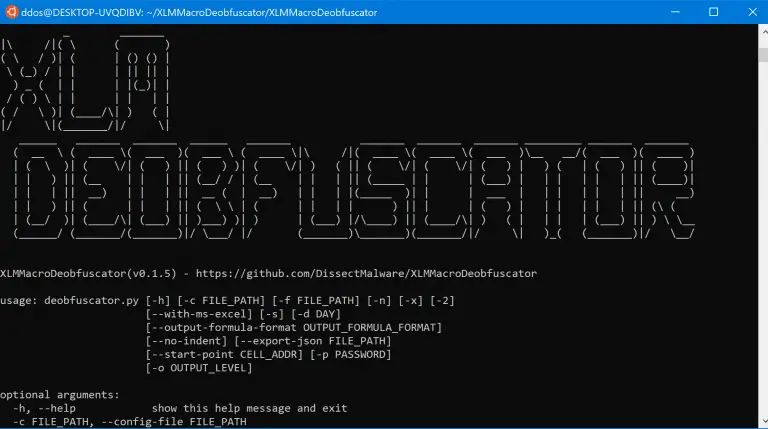
XLM Macro Deobfuscator XLM Macro Deobfuscator can be used to decode obfuscated XLM macros (also known as...
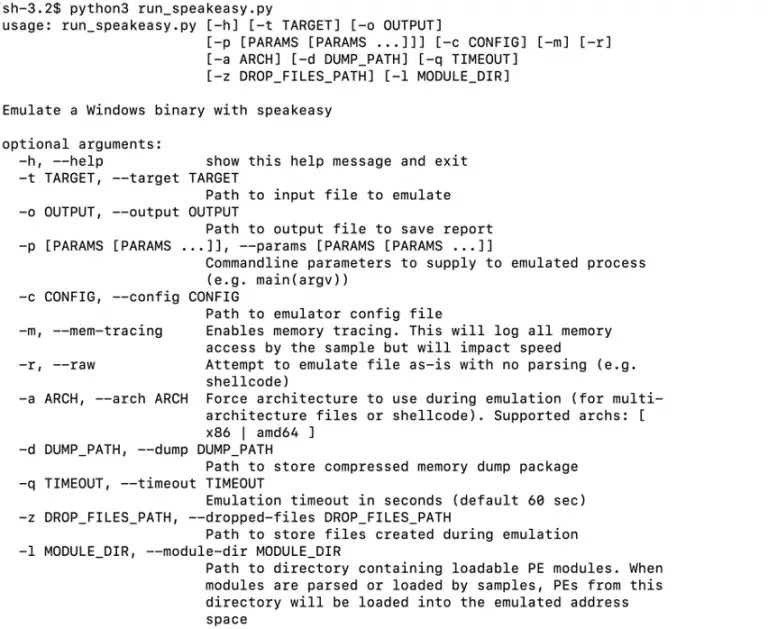
Speakeasy Speakeasy is a portable, modular, binary emulator designed to emulate Windows kernel and user mode malware....
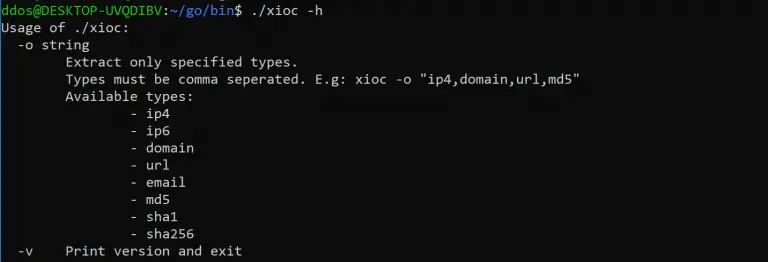
xioc Extract indicators of compromise from the text, including “escaped” ones like hxxp://banana.com, 1.1.1[.]1, and phish at...
PeaceMaker Threat Detection PeaceMaker Threat Detection is a kernel-mode utility designed to detect a variety of methods...
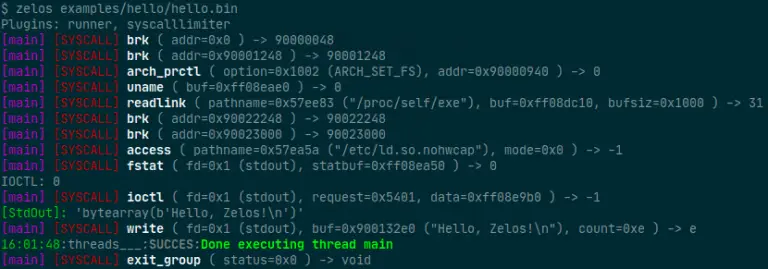
Zelos Zelos (Zeropoint Emulated Lightweight Operating System) is a python-based binary emulation platform. One use of Zelos is to quickly assess...
Linux Memory Grabber A script for dumping Linux memory and creating Volatility(TM) profiles. To analyze Linux memory,...
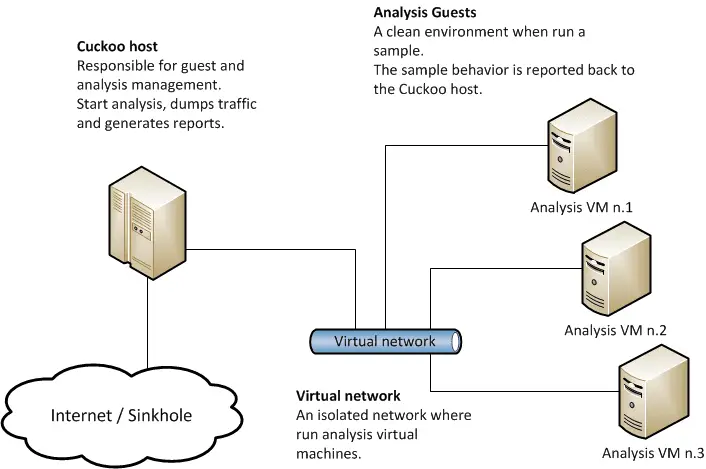
CAPE: Malware Configuration And Payload Extraction CAPE is a malware sandbox. It is derived from Cuckoo and...