EDRSandblast-GodFault Integrates GodFault into EDR Sandblast, achieving the same result without the use of any vulnerable drivers. EDRSandBlast is a tool...
Exploitation
Introducing the ROP ROCKET This new, advanced ROP framework made its debut at DEF CON 31 with...
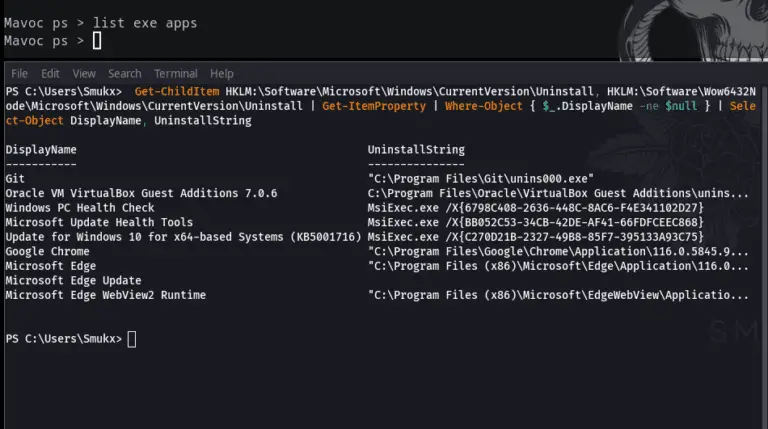
Mavoc C2 Framework Mavoc is a tool used to pentest Windows and Linux machines. This tool mainly...
DllNotificationInjection DllNotificationInection is a POC of a new “threadless” process injection technique that works by utilizing the...
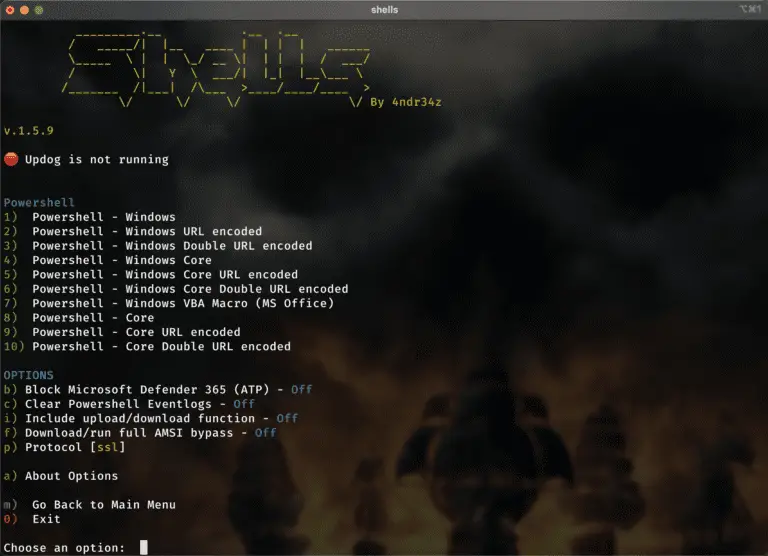
Shellz A script for generating common reverse shells fast and easy. Especially nice when in need of...
HeaderLessPE HeaderLessPE is a memory PE loading technique used by the Icedid Trojan. Based on this technology,...
ContainYourself A PoC of the ContainYourself research, presented on DEFCON 31. This tool abuses the Windows containers framework...
Supernova Supernova is an open-source Golang tool that empowers users to securely encrypt their raw shellcodes. Additionally,...
Electron_shell An increasing number of desktop applications are opting for the Electron framework. Electron provides a method...
OSDP (Open Supervised Device Protocol) Vulnerabilities Attack #1: Encryption is Optional OSDP supports, but doesn’t strictly require, encryption....
SMShell PoC for an SMS-based shell. Send commands and receive responses over SMS from mobile broadband-capable computers....
DropSpawn DropSpawn is a CobaltStrike BOF used to spawn additional Beacons via a relatively unknown method of...
ModuleShifting ModuleShifting is a stealthier variation of Module Stomping and Module overloading injection technique. It is actually...
Chimera While DLL sideloading can be used for legitimate purposes, such as loading necessary libraries for a...
NixImports A .NET malware loader, using API-Hashing and dynamic invoking to evade static analysis. NixImports aims to...