CimSweep CimSweep is a suite of CIM/WMI-based tools that enable the ability to perform incident response and...
Post Exploitation
mimipenguin A tool to dump the login password from the current Linux desktop user. Adapted from the...
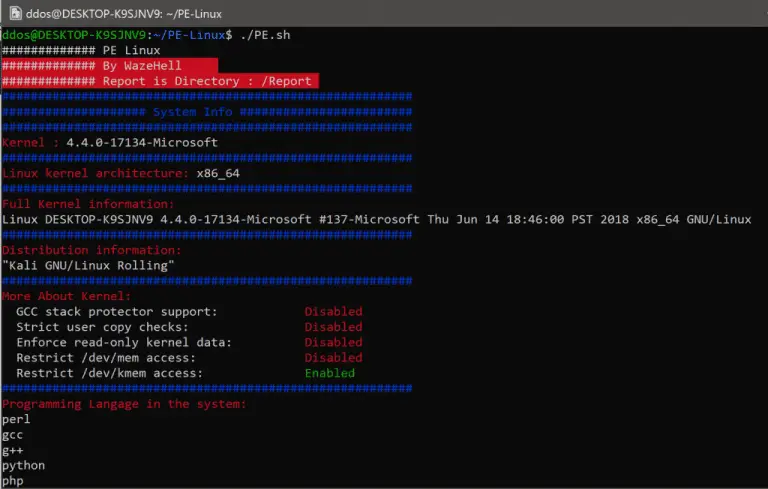
PE-Linux New Linux Privilege Escalation Tool Getting Started System Information Gatherer Kernel Information Gatherer Checking Development environments...
Invoke-LiveResponse The current scope of Invoke-LiveResponse is a live response tool for targeted collection. There are two main modes...
SQLC2 SQLC2 is a PowerShell script for deploying and managing a command and control system that uses...
Sleight Empire HTTP(S) C2 redirector setup script. Download git clone https://github.com/V1V1/Sleight.git Usage: Sleight can be used in...
TeamViewer-dumper Dump TeamViewer ID and password from memory. Works much better than other tools. Tested on TeamViewer...
Fox and the Hound Fox connects to your BloodHound database to perform various queries to generate statistics...
AllTools All reasonably stable tools CpuStres – thread/CPU stress testing app DriverMon – monitor any driver activity GFlagsX – enhanced...
Intro These scripts are a PoC for how to extract unencrypted private SSH keys from Windows when...
Visual Basic GUI (VBG for short) uses an X11 forwarded SSH session to remotely execute commands on...
ProcessHider is a post-exploitation tool designed to hide processes from monitoring tools such as Task Manager and...
Sudohulk This tool change sudo command, hooking the execve syscall using ptrace, tested under bash and zsh...
Internal Monologue Attack: Retrieving NTLM Hashes without Touching LSASS Introduction Mimikatz, developed by Benjamin Delpy (@gentilkiwi), is...
GoFetch GoFetch is a tool to automatically exercise an attack plan generated by the BloodHound application. It first loads...